- 机器学习之线性代数
珠峰日记
AI理论与实践机器学习线性代数人工智能
文章目录一、引言:线性代数为何是AI的基石二、向量:AI世界的基本构建块(一)向量的定义(二)向量基础操作(三)重要概念三、矩阵:AI数据的强大容器(一)矩阵的定义(二)矩阵运算(三)矩阵特性(四)矩阵分解(五)Python示例(使用NumPy库)四、线性代数在AI中的应用(一)数据表示(二)降维:PCA(三)线性回归(四)计算机视觉(五)自然语言处理一、引言:线性代数为何是AI的基石在人工智能领
- 鸿蒙ArkUI瀑布流开发实战:WaterFlow组件与LazyForEach高效实现
写雨.0
HarmonyOSNEXTharmonyos华为
前言瀑布流布局(WaterfallFlow)是购物、资讯类应用的核心交互设计,如何在鸿蒙ArkUI中高效实现多列动态加载与滚动优化?本文将以小红书类似的结构为例,手把手教你使用WaterFlow组件与LazyForEach懒加载技术,解决数据量大时的性能瓶颈,并提供多设备适配方案。一、ArkUI瀑布流核心组件1.WaterFlow组件鸿蒙的WaterFlow组件是瀑布流布局的容器,支持以下关键属性
- 《Quick Start Kubernetes》读后感
python
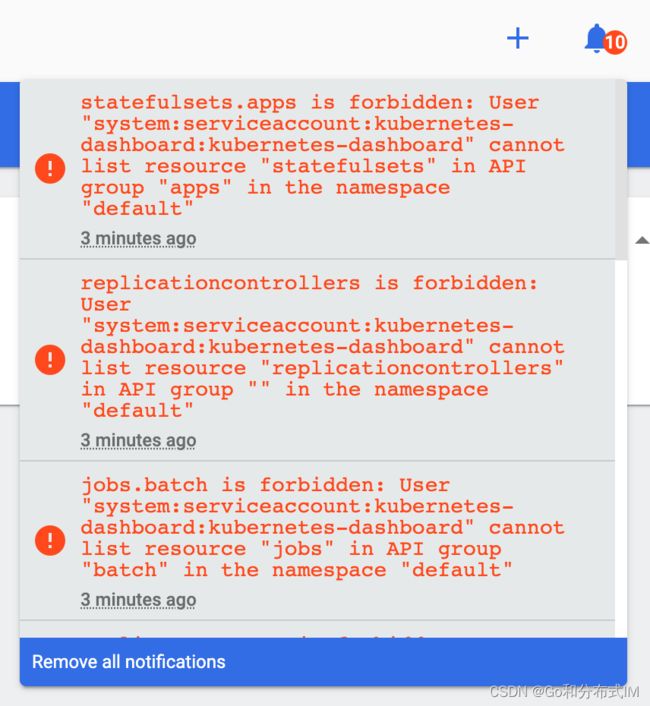
一、为什么选择这本书?面试的时候经常被问到kubernetes(下称k8s),所以打算学习k8s。看到《QuickStartKubernetes》的作者对自己所写的书持续地更新,被这种认真打动了,外加这本书只有100多页,所以选择了这本书作为入门k8s的教材。二、这本书写了什么?这本书介绍了什么是k8s,k8s的组成结构(controlplanenode,workernode),演示了在Windo
- Vue初体验
码上跑步
vue.js前端
Vue基础Vue是什么?Vue是javascript的渐进式框架。Vue初识Vue工作时必须要创建一个Vue的实例,并且传入一个配置对象。root容器里的代码是符合html的语法但是新添加了一些Vue语法,在这些地方Vue会自动进行解析。root容器里的代码称为Vue模版。Vue实例和容器是一一对应的。在实际开发中只有一个Vue,配合组件使用。在vue里的插值{{}}内部只要写js表达式就能正常解
- Spring IOC 容器核心功能解析与优化架构
我不是少爷.
Java基础spring架构java
一、IOC容器创建Bean的四种方式1.1普通创建方式使用场景:直接通过类默认构造器创建对象实现步骤:代码说明:id:Bean的唯一标识符class:指定类的全限定名Spring会调用默认无参构造器实例化对象1.2工厂模式创建使用场景:需要工厂类处理复杂初始化逻辑时实现步骤://工厂类publicclassBookFactory{publicBookcreateBook(){returnnewBo
- Docker高级应用-限制容器的cpu和内存
云原生的爱好者
docker容器运维
一、为什么要用docker限制容器的cpu和内存1.资源隔离与公平分配防止资源争用:在多容器环境中,限制CPU和内存可以避免某个容器占用过多资源,影响其他容器的运行。确保公平性:通过限制资源,确保每个容器都能获得所需的计算能力,避免资源被少数容器独占。2.提高系统稳定性防止内存泄漏:限制内存可以避免容器因内存泄漏耗尽主机内存,导致系统崩溃。避免CPU过载:限制CPU使用可以防止容器过度占用CPU,
- docker命令实战运用部署服务
云原生的爱好者
docker容器运维
1.接上篇博文,先讲一下如何利用docker来对容器进行一个守护进程的启动,以及如何进入日期,如下:[root@cjr~]#dockerimagesREPOSITORYTAGIMAGEIDCREATEDSIZEcentoslatest5d0da3dc97643yearsago231MB[root@cjr~]#dockerrun-td--nametestcentos:latest1b0cfe7658
- docker运行容器命令 redis 指定端口
big maom~~
dockerrediseureka容器运维
我整理的一些关于【Docker】的项目学习资料(附讲解~~)和大家一起分享、学习一下:https://edu.51cto.com/surl=QsXoR2使用Docker运行Redis容器并指定端口的详细指南本文旨在帮助初学者理解如何使用Docker来运行Redis容器,并指定端口。Docker是一个开源平台,允许开发者将应用和其依赖打包成一个标准的单元——容器。通过使用Docker,开发者可以确保
- Docker Compose国内镜像一键部署dify
llody_55
GPTdocker容器运维aiAI编程
克隆代码gitclonehttps://github.com/langgenius/dify.git进入docker目录cddocker修改.env部分#将环境模版文件变量重命名cp.env.example.env#修改.env,修改nginx的host和端口,避免端口冲突NGINX_SERVER_NAME=192.168.1.223NGINX_PORT=1880NGINX_SSL_PORT=14
- ARM64环境部署EFK8.15.3收集K8S集群容器日志
llody_55
kubernetes容器云原生运维esjavaelasticsearch
环境规划主机IP系统部署方式ES版本CPU架构用户名密码192.168.1.225Ubuntu22.04.4LTSdockerelasticsearch:8.15.3ARM64elasticllodyi4TMmZDES集群部署创建持久化目录(所有节点)mkdir-p/data/es/{data,certs,logs,plugins}mkdir-p/data/es/certs/{ca,es01}服务
- Qt的QGraphics View的使用
水瓶丫头站住
Qtqt信息可视化开发语言
QGraphicsView框架是Qt中用于管理和渲染大量2D图形对象的强大工具,适合构建绘图软件、游戏编辑器、数据可视化等场景。以下是关键使用步骤和示例:1.核心组件QGraphicsScene:场景容器,管理所有图形项(Item)的层级、坐标和事件。QGraphicsView:视图组件,用于显示场景内容,支持缩放、旋转、滚动等操作。QGraphicsItem:所有图形项的基类(如矩形、椭圆、自定
- 如何在 Dockerfile 中使用 if-else 条件表达式 ?
docker
Docker是容器化应用程序的必要工具,使它们可移植和隔离。Dockerfile是Docker生态系统中的一个关键组件,它允许开发人员指定他们的应用程序应该如何被容器化。通常在Dockerfiles中需要条件逻辑,就像您在编程脚本中发现的那样。但是Dockerfile语法不直接支持if-else条件表达式。在本文中,我们将探讨如何在Dockerfiles中有效地使用条件逻辑,特别是使用外部参数。A
- Spring 多实例注入
m0_74825172
面试学习路线阿里巴巴springjava后端
文章目录1.Spring多实例注入的应用场景2.Spring多实例注入的使用2.1通过ApplicationContext获取多实例2.2配置@Scope的proxyMode属性获取多实例1.Spring多实例注入的应用场景Spring容器中保存的bean默认是单例的,通常来说这样做可以降低bean对象创建的频率,在某些访问量大的场景下可以节省对象创建消耗的时间,提高响应性能。但在一些其他场景,比
- 统信uos20:利用docker部署python+jupyterlab开发环境
阆遤
dockerpythonjupytergithubactionsworkflow统信uos20
很多统信uos20计算机没有联网安装python开发环境的条件,但是工作中需要对数据进行分析处理,因而产生了离线部署python开发环境的想法。我首先下载了python3.11的源代码包,在uos中编译居然正常通过。但后续的麻烦来了:需要安装的库没法安装。尝试了一天,最终放弃。改用Docker方式部署,理由就不多解释了。一、在uos中安装docker。我的系统是uos20linux4.19.0-a
- 系统架构设计师【第14章】: 云原生架构设计理论与实践 (核心总结)
数据知道
系统架构云原生软考高级系统架构设计师
文章目录14.1云原生架构产生背景14.2云原生架构内涵14.2.1云原生架构定义14.2.2云原生架构原则14.2.3主要架构模式14.2.4典型的云原生架构反模式14.3云原生架构相关技术14.3.1容器技术14.3.2云原生微服务14.3.3无服务器技术14.3.4服务网格14.4云原生架构案例分析14.4.1某旅行公司云原生改造14.4.2云原生技术助力某汽车公司数字化转型实践14.4.3
- Docker部署SVN服务器并使用:从基础到高级
ivwdcwso
运维SVN代码管理运维
目录引言Docker部署SVN服务器SVN基础使用SVN高级使用最佳实践和注意事项结语1.引言Subversion(SVN)是一个开源的版本控制系统,广泛用于管理和追踪软件项目的源代码。本文将详细介绍如何使用Docker快速部署SVN服务器,以及SVN的基础和高级使用方法。无论你是SVN新手还是有经验的用户,本文都将为你提供有价值的信息。2.Docker部署SVN服务器2.1安装Docker如果你
- 使用docker安装elk
吴传逞
dockerelk运维
配置要求:一台Linux服务器,内存不少于2g,centos7以上系统1.安装docker安装教程:CentOSDocker安装|菜鸟教程分以下几个步骤(我只写我使用过的方式):curl-fsSLhttps://get.docker.com|bash-sdocker--mirrorAliyun安装DockerEngine-Communityyuminstall-yyum-utils\device-
- 基于Linux环境部署和使用ElasticSearch搜索引擎
探模之翼
数据库搜索引擎linuxelasticsearch向量数据库多模态检索
目录一.Elasticsearch基础介绍二.Docker部署单节点ElasticSearch1.环境配置2.创建数据目录3.创建ES自定义配置文件4.启动ElasticSearch服务5.验证服务三.DockerCompose部署单节点ElasticSearch1.环境配置2.创建docker-compose.yml3.创建配置文件elasticsearch.yml4.启动ElasticSear
- Java常用集合与映射的线程安全问题深度解析
yang789022
编程学习java安全python
Java常用集合与映射的线程安全问题深度解析一、线程安全基础认知二、典型非线程安全集合问题分析1.ArrayList的并发陷阱2.HashMap的并发灾难3.HashSet的隐藏风险三、线程安全解决方案对比1.同步包装方案2.传统线程安全集合3.现代并发容器(java.util.concurrent包)3.1CopyOnWriteArrayList3.2ConcurrentHashMap3.3Co
- 【DeepSeek问答】Qt布局和控件的关系
CSUC
qt
在Qt中,布局管理器(Layout)与控件(Widget)的关系是容器与内容的关系。布局负责自动管理控件的排列、尺寸调整和自适应,确保界面在不同窗口尺寸下保持美观和功能。以下是详细说明及用法示例:一、布局与控件的关系容器与内容:布局(如QVBoxLayout、QHBoxLayout)作为容器,管理其内部控件的位置和大小。控件(如QPushButton、QLabel)是布局中的内容,通过addWid
- docker和kubectl客户端安装Linux
yyytucj
dockerlinux容器
在现代软件开发和运维领域,Docker和Kubernetes已成为不可或缺的工具。Docker是一个开源的应用容器引擎,允许开发者打包应用及其依赖包到一个可移植的容器中,然后发布到任何流行的Linux机器或者Windows机器上。Kubernetes(简称K8s)是一个开源的容器编排工具,用于自动化容器的部署、扩展和管理。在Linux环境中安装Docker和Kubernetes客户端(kubect
- CICD系列之k8s
john137724
DEV-OPSk8s
k8s安装操作系统配置主机规划hosts配置(所有主机都要配置)防火墙配置(所有主机都要配置)内核配置参数(所有主机都要配置)selinux和swap配置(所有主机都要配置)ipvs配置(所有主机都要配置)安装docker安装k8s组件配置k8s组件安装yum源安装kubelet,kubeadm,kubectl(所有节点都要安装,工作节点不用安装kubectl)设置kubelet开机自启动初始化集
- CICD系列之jenkins
john137724
DEV-OPSdockerjenkins
jenkins专题安装docker&docker-compose安装jenkins编写docker-compose.yml脚本配置jenkins安装常用插件记录jenkins安装、配置、使用的常用操作linux物理机安装安装docker&docker-composedocker安装与配置安装jenkins#创建docker桥接网络dockernetworkcreatejohn-net#新建数据目录
- CICD系列之harbor
john137724
DEV-OPSharbor
镜像仓库专题安装docker&docker-compose安装harbor下载并解压安装文件修改配置文件安装、管理harbor访问harbor重点提示记录镜像仓库的常用操作。安装docker&docker-composedocker&docker-compose安装与配置安装harbor下载并解压安装文件#下载到指定目录并进入该目录wgethttps://github.com/goharbor/h
- docker 安装ELK 8.17.3
离开水的飞鱼
dockerelk容器
ELK是指Elasticsearch、Logstash和Kibana这三个开源软件的组合。Elasticsearch是一个分布式的搜索和分析引擎,用于日志的存储,搜索,分析,查询。Logstash是一个数据收集、转换和传输工具,用于收集过滤和转换数据,然后将其发送到Elasticsearch或其他目标存储中。Kibana是一个数据可视化平台,通过与Elasticsearch的集成,提供了强大的数据
- C++中map和set的详解
jiajia651304
c++算法开发语言
C++中map和set的介绍与使用一、map的介绍与使用二、set的介绍与使用三、总结在C++编程中,map和set是标准模板库(STL)中两种非常重要的关联容器。它们基于平衡二叉搜索树(通常是红黑树)的数据结构来实现,提供了高效的数据存储和检索功能。本文将详细介绍map和set的特点、用法以及一些常见的操作示例。一、map的介绍与使用1.map的基本概念map是一个键值对容器,其中每个键都是唯一
- Qt基础之四十一:记一次QVector的bad alloc问题追踪
草上爬
Qt那些事儿qtQVectorvectorbadalloc
目录一.QVector的特点二.QVector的内存分配策略三.badalloc问题追踪一.QVector的特点QVector是Qt容器类库中的一个重要组成部分,它提供了类似于C++标准库中的std::vector的功能,但同时拥有Qt独特的优势。QVector是一个动态数组,支持添加、插入和删除元素。与其他容器相比,QVector在随机访问元素时具有出色的性能,同时在尾部添加和删除元素时依然高效
- 在vue3中使用Mermaid创建可动态生成的时序图
充气大锤
前端组件javascript开发语言前端流程图vuevue.js
有手就行的:用Mermaid创建自己的时序图一、Mermaid的安装在vue3中使用Mermaid时,需要npm一下npminstallmermaid完事之后这样引用importmermaidfrom'mermaid'引用之后就可以开始整活了二、承载Mermaid的容器Mermaid不同于其他的流程图组件,这玩意用标签来承载数据,所以我们在vue文件中这样创建{{message}}*类名不能错,类
- python基础——元组【特点,创建,常见操作方法:index,len,count】
愚润泽
python入门基础python开发语言学习方法笔记经验分享
前言:上一篇文章python基础——列表讲解了关于列表的先关知识,还介绍了很多列表的常见操作方法,这篇文章我们就基于上篇文章带大家认识的有关序列的知识,继续讲解python中另一种常见的数据容器——元组:1,元组的特点2,元组的定义3,元组的常见操作方法个人简介:努力学习ing个人专栏:C语言入门基础以及python入门基础CSDN主页愚润求学每日鸡汤:日日行不怕千万里,时时做不惧千万事文章目录一
- C++之list删除元素
csdn_zhangchunfeng
C++VS技术管理索引列表c++
C++之list删除元素对容器list存储的元素执行删除操作的时候,一般都是使用其成员函数实现的:(1)clear():删除list容器中的所有元素(2)remove(value):删除容器中所有为value的元素(3)remove_if():删除容器中满足条件的元素(4)unique():删除容器中相邻的重复元素,只留下一个(5)erase():删除list容器中指定位置处的元素,也可以删除容器
- 书其实只有三类
西蜀石兰
类
一个人一辈子其实只读三种书,知识类、技能类、修心类。
知识类的书可以让我们活得更明白。类似十万个为什么这种书籍,我一直不太乐意去读,因为单纯的知识是没法做事的,就像知道地球转速是多少一样(我肯定不知道),这种所谓的知识,除非用到,普通人掌握了完全是一种负担,维基百科能找到的东西,为什么去记忆?
知识类的书,每个方面都涉及些,让自己显得不那么没文化,仅此而已。社会认为的学识渊博,肯定不是站在
- 《TCP/IP 详解,卷1:协议》学习笔记、吐槽及其他
bylijinnan
tcp
《TCP/IP 详解,卷1:协议》是经典,但不适合初学者。它更像是一本字典,适合学过网络的人温习和查阅一些记不清的概念。
这本书,我看的版本是机械工业出版社、范建华等译的。这本书在我看来,翻译得一般,甚至有明显的错误。如果英文熟练,看原版更好:
http://pcvr.nl/tcpip/
下面是我的一些笔记,包括我看书时有疑问的地方,也有对该书的吐槽,有不对的地方请指正:
1.
- Linux—— 静态IP跟动态IP设置
eksliang
linuxIP
一.在终端输入
vi /etc/sysconfig/network-scripts/ifcfg-eth0
静态ip模板如下:
DEVICE="eth0" #网卡名称
BOOTPROTO="static" #静态IP(必须)
HWADDR="00:0C:29:B5:65:CA" #网卡mac地址
IPV6INIT=&q
- Informatica update strategy transformation
18289753290
更新策略组件: 标记你的数据进入target里面做什么操作,一般会和lookup配合使用,有时候用0,1,1代表 forward rejected rows被选中,rejected row是输出在错误文件里,不想看到reject输出,将错误输出到文件,因为有时候数据库原因导致某些column不能update,reject就会output到错误文件里面供查看,在workflow的
- 使用Scrapy时出现虽然队列里有很多Request但是却不下载,造成假死状态
酷的飞上天空
request
现象就是:
程序运行一段时间,可能是几十分钟或者几个小时,然后后台日志里面就不出现下载页面的信息,一直显示上一分钟抓取了0个网页的信息。
刚开始已经猜到是某些下载线程没有正常执行回调方法引起程序一直以为线程还未下载完成,但是水平有限研究源码未果。
经过不停的google终于发现一个有价值的信息,是给twisted提出的一个bugfix
连接地址如下http://twistedmatrix.
- 利用预测分析技术来进行辅助医疗
蓝儿唯美
医疗
2014年,克利夫兰诊所(Cleveland Clinic)想要更有效地控制其手术中心做膝关节置换手术的费用。整个系统每年大约进行2600例此类手术,所以,即使降低很少一部分成本,都可以为诊 所和病人节约大量的资金。为了找到适合的解决方案,供应商将视野投向了预测分析技术和工具,但其分析团队还必须花时间向医生解释基于数据的治疗方案意味着 什么。
克利夫兰诊所负责企业信息管理和分析的医疗
- java 线程(一):基础篇
DavidIsOK
java多线程线程
&nbs
- Tomcat服务器框架之Servlet开发分析
aijuans
servlet
最近使用Tomcat做web服务器,使用Servlet技术做开发时,对Tomcat的框架的简易分析:
疑问: 为什么我们在继承HttpServlet类之后,覆盖doGet(HttpServletRequest req, HttpServetResponse rep)方法后,该方法会自动被Tomcat服务器调用,doGet方法的参数有谁传递过来?怎样传递?
分析之我见: doGet方法的
- 揭秘玖富的粉丝营销之谜 与小米粉丝社区类似
aoyouzi
揭秘玖富的粉丝营销之谜
玖富旗下悟空理财凭借着一个微信公众号上线当天成交量即破百万,第七天成交量单日破了1000万;第23天时,累计成交量超1个亿……至今成立不到10个月,粉丝已经超过500万,月交易额突破10亿,而玖富平台目前的总用户数也已经超过了1800万,位居P2P平台第一位。很多互联网金融创业者慕名前来学习效仿,但是却鲜有成功者,玖富的粉丝营销对外至今仍然是个谜。
近日,一直坚持微信粉丝营销
- Java web的会话跟踪技术
百合不是茶
url会话Cookie会话Seession会话Java Web隐藏域会话
会话跟踪主要是用在用户页面点击不同的页面时,需要用到的技术点
会话:多次请求与响应的过程
1,url地址传递参数,实现页面跟踪技术
格式:传一个参数的
url?名=值
传两个参数的
url?名=值 &名=值
关键代码
- web.xml之Servlet配置
bijian1013
javaweb.xmlServlet配置
定义:
<servlet>
<servlet-name>myservlet</servlet-name>
<servlet-class>com.myapp.controller.MyFirstServlet</servlet-class>
<init-param>
<param-name>
- 利用svnsync实现SVN同步备份
sunjing
SVN同步E000022svnsync镜像
1. 在备份SVN服务器上建立版本库
svnadmin create test
2. 创建pre-revprop-change文件
cd test/hooks/
cp pre-revprop-change.tmpl pre-revprop-change
3. 修改pre-revprop-
- 【分布式数据一致性三】MongoDB读写一致性
bit1129
mongodb
本系列文章结合MongoDB,探讨分布式数据库的数据一致性,这个系列文章包括:
数据一致性概述与CAP
最终一致性(Eventually Consistency)
网络分裂(Network Partition)问题
多数据中心(Multi Data Center)
多个写者(Multi Writer)最终一致性
一致性图表(Consistency Chart)
数据
- Anychart图表组件-Flash图转IMG普通图的方法
白糖_
Flash
问题背景:项目使用的是Anychart图表组件,渲染出来的图是Flash的,往往一个页面有时候会有多个flash图,而需求是让我们做一个打印预览和打印功能,让多个Flash图在一个页面上打印出来。
那么我们打印预览的思路是获取页面的body元素,然后在打印预览界面通过$("body").append(html)的形式显示预览效果,结果让人大跌眼镜:Flash是
- Window 80端口被占用 WHY?
bozch
端口占用window
平时在启动一些可能使用80端口软件的时候,会提示80端口已经被其他软件占用,那一般又会有那些软件占用这些端口呢?
下面坐下总结:
1、web服务器是最经常见的占用80端口的,例如:tomcat , apache , IIS , Php等等;
2
- 编程之美-数组的最大值和最小值-分治法(两种形式)
bylijinnan
编程之美
import java.util.Arrays;
public class MinMaxInArray {
/**
* 编程之美 数组的最大值和最小值 分治法
* 两种形式
*/
public static void main(String[] args) {
int[] t={11,23,34,4,6,7,8,1,2,23};
int[]
- Perl正则表达式
chenbowen00
正则表达式perl
首先我们应该知道 Perl 程序中,正则表达式有三种存在形式,他们分别是:
匹配:m/<regexp>;/ (还可以简写为 /<regexp>;/ ,略去 m)
替换:s/<pattern>;/<replacement>;/
转化:tr/<pattern>;/<replacemnt>;
- [宇宙与天文]行星议会是否具有本行星大气层以外的权力呢?
comsci
举个例子: 地球,地球上由200多个国家选举出一个代表地球联合体的议会,那么现在地球联合体遇到一个问题,地球这颗星球上面的矿产资源快要采掘完了....那么地球议会全体投票,一致通过一项带有法律性质的议案,既批准地球上的国家用各种技术手段在地球以外开采矿产资源和其它资源........
&
- Oracle Profile 使用详解
daizj
oracleprofile资源限制
Oracle Profile 使用详解 转
一、目的:
Oracle系统中的profile可以用来对用户所能使用的数据库资源进行限制,使用Create Profile命令创建一个Profile,用它来实现对数据库资源的限制使用,如果把该profile分配给用户,则该用户所能使用的数据库资源都在该profile的限制之内。
二、条件:
创建profile必须要有CREATE PROFIL
- How HipChat Stores And Indexes Billions Of Messages Using ElasticSearch & Redis
dengkane
elasticsearchLucene
This article is from an interview with Zuhaib Siddique, a production engineer at HipChat, makers of group chat and IM for teams.
HipChat started in an unusual space, one you might not
- 循环小示例,菲波拉契序列,循环解一元二次方程以及switch示例程序
dcj3sjt126com
c算法
# include <stdio.h>
int main(void)
{
int n;
int i;
int f1, f2, f3;
f1 = 1;
f2 = 1;
printf("请输入您需要求的想的序列:");
scanf("%d", &n);
for (i=3; i<n; i
- macbook的lamp环境
dcj3sjt126com
lamp
sudo vim /etc/apache2/httpd.conf
/Library/WebServer/Documents
是默认的网站根目录
重启Mac上的Apache服务
这个命令很早以前就查过了,但是每次使用的时候还是要在网上查:
停止服务:sudo /usr/sbin/apachectl stop
开启服务:s
- java ArrayList源码 下
shuizhaosi888
ArrayList源码
版本 jdk-7u71-windows-x64
JavaSE7 ArrayList源码上:http://flyouwith.iteye.com/blog/2166890
/**
* 从这个列表中移除所有c中包含元素
*/
public boolean removeAll(Collection<?> c) {
- Spring Security(08)——intercept-url配置
234390216
Spring Securityintercept-url访问权限访问协议请求方法
intercept-url配置
目录
1.1 指定拦截的url
1.2 指定访问权限
1.3 指定访问协议
1.4 指定请求方法
1.1 &n
- Linux环境下的oracle安装
jayung
oracle
linux系统下的oracle安装
本文档是Linux(redhat6.x、centos6.x、redhat7.x) 64位操作系统安装Oracle 11g(Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production),本文基于各种网络资料精心整理而成,共享给有需要的朋友。如有问题可联系:QQ:52-7
- hotspot虚拟机
leichenlei
javaHotSpotjvm虚拟机文档
JVM参数
http://docs.oracle.com/javase/6/docs/technotes/guides/vm/index.html
JVM工具
http://docs.oracle.com/javase/6/docs/technotes/tools/index.html
JVM垃圾回收
http://www.oracle.com
- 读《Node.js项目实践:构建可扩展的Web应用》 ——引编程慢慢变成系统化的“砌砖活”
noaighost
Webnode.js
读《Node.js项目实践:构建可扩展的Web应用》
——引编程慢慢变成系统化的“砌砖活”
眼里的Node.JS
初初接触node是一年前的事,那时候年少不更事。还在纠结什么语言可以编写出牛逼的程序,想必每个码农都会经历这个月经性的问题:微信用什么语言写的?facebook为什么推荐系统这么智能,用什么语言写的?dota2的外挂这么牛逼,用什么语言写的?……用什么语言写这句话,困扰人也是阻碍
- 快速开发Android应用
rensanning
android
Android应用开发过程中,经常会遇到很多常见的类似问题,解决这些问题需要花时间,其实很多问题已经有了成熟的解决方案,比如很多第三方的开源lib,参考
Android Libraries 和
Android UI/UX Libraries。
编码越少,Bug越少,效率自然会高。
但可能由于 根本没听说过、听说过但没用过、特殊原因不能用、自己已经有了解决方案等等原因,这些成熟的解决
- 理解Java中的弱引用
tomcat_oracle
java工作面试
不久之前,我
面试了一些求职Java高级开发工程师的应聘者。我常常会面试他们说,“你能给我介绍一些Java中得弱引用吗?”,如果面试者这样说,“嗯,是不是垃圾回收有关的?”,我就会基本满意了,我并不期待回答是一篇诘究本末的论文描述。 然而事与愿违,我很吃惊的发现,在将近20多个有着平均5年开发经验和高学历背景的应聘者中,居然只有两个人知道弱引用的存在,但是在这两个人之中只有一个人真正了
- 标签输出html标签" target="_blank">关于标签输出html标签
xshdch
jsp
http://back-888888.iteye.com/blog/1181202
关于<c:out value=""/>标签的使用,其中有一个属性是escapeXml默认是true(将html标签当做转移字符,直接显示不在浏览器上面进行解析),当设置escapeXml属性值为false的时候就是不过滤xml,这样就能在浏览器上解析html标签,
&nb