计算机网络-自顶向下方法(7th) 第三章 Problems 英文题目+中文答案
P1.
Suppose Client A initiates a Telnet session with Server S. At about the same time, Client B also initiates a Telnet session with Server S. Provide possible source and destination port numbers for
a. The segments sent from A to S.
b. The segments sent from B to S.
c. The segments sent from S to A.
d. The segments sent from S to B.
e. If A and B are different hosts, is it possible that the source port number in the segments from A to S is the same as that from B to S?
f. How about if they are the same host?
| source port numbers | destination port numbers | |
|---|---|---|
| a. A→ S | 467 | 23 |
| b. B→ S | 513 | 23 |
| c. S→ A | 23 | 467 |
| d. S→ B | 23 | 513 |
注:Telnet的端口号是23
e.可以。
f. 不可以。
P2.
Consider Figure 3.5 . What are the source and destination port values in the segments flowing from the server back to the clients’ processes? What are the IP addresses in the network-layer datagrams carrying the transport-layer segments?
P3.
UDP and TCP use 1s complement for their checksums. Suppose you have the following three 8-bit bytes: 01010011, 01100110, 01110100. What is the 1s complement of the sum of these 8-bit bytes? (Note that although UDP and TCP use 16-bit words in computing the checksum, for this problem you are being asked to consider 8-bit sums.) Show all work. Why is it that UDP takes the 1s complement of the sum; that is, why not just use the sum? With the 1s complement scheme, how does the receiver detect errors? Is it possible that a 1-bit error will go undetected? How about a 2-bit error?
1补:11010001
1补只需要把它当成数据的一部分不断加和,判断最后是否是全1。而如果仅使用和sum的话,需要把sum单独存起来。最后把数据的和求出来之后进行比对,单独存储sum需要多用一个寄存器。
当发现加和结果有一位为0,则说明发生了错误。
1位发生错误一定能被检测到,两位发生错误就未必了。
P4.
a. Suppose you have the following 2 bytes: 01011100 and 01100101. What is the 1s complement of the sum of these 2 bytes?
b. Suppose you have the following 2 bytes: 11011010 and 01100101. What is the 1s complement of the sum of these 2 bytes?
c. For the bytes in part (a), give an example where one bit is flipped in each of the 2 bytes and yet the 1s complement doesn’t change.
a 00111110
b 10111111
c 01111100 和 01000101
P5.
Suppose that the UDP receiver computes the Internet checksum for the received UDP segment and finds that it matches the value carried in the checksum field. Can the receiver be absolutely certain that no bit errors have occurred? Explain.
不是。有可能同时出现了两个bits的错误。
P6.
Consider our motivation for correcting protocol rdt2.1. Show that the receiver, shown in Figure 3.57 , when operating with the sender shown in Figure 3.11 , can lead the sender and receiver to enter into a deadlock state, where each is waiting for an event that will never occur.
接收者无法应对ACK损坏的情况。
假如接收者收到了包1,返回ACK,并进入了等待包2的状态。此时发送者收到的若是一个损坏的ACK,就会重发包1。
此时,发送者处于发送包1的状态,接受者处于等待包2的状态,进入死锁。
P7.
In protocol rdt3.0, the ACK packets flowing from the receiver to the sender do not have sequence numbers (although they do have an ACK field that contains the sequence number of the packet they are acknowledging). Why is it that our ACK packets do not require sequence numbers?
不理解该题。
我怀疑是我阅读能力有问题-_-||。
附上官方答案:
To best answer this question, consider why we needed sequence numbers in the first place. We saw that the sender needs sequence numbers so that the receiver can tell if a data packet is a duplicate of an already received data packet. In the case of ACKs, the sender does not need this info (i.e., a sequence number on an ACK) to tell detect a duplicate ACK. A duplicate ACK is obvious to the rdt3.0 receiver, since when it has received the original ACK it transitioned to the next state. The duplicate ACK is not the ACK that the sender needs and hence is ignored by the rdt3.0 sender.
P8.
Draw the FSM for the receiver side of protocol rdt3.0.
使用rdt2.2的接收端状态机就可以。(因为rdt3.0只是在发送端增加了一个超时检测机制,对接收端没有改动)。
P9.
Give a trace of the operation of protocol rdt3.0 when data packets and acknowledgment packets are garbled. Your trace should be similar to that used in Figure 3.16
P10.
Consider a channel that can lose packets but has a maximum delay that is known. Modify protocol rdt2.1 to include sender timeout and retransmit. Informally argue why your protocol can communicate correctly over this channel.

把计时器的超时阈值设为已知的最高时延。每次发送新分组后计时器重启。
假如超时,处理策略与收到损坏包/收到NAK相同。
假如超时,有两种情况。
1、发送的包丢失。这样接收方收不到任何包,发送方在超时后重发,接收方便能接收到这个包了。(和对NAK的处理是一致的,因为收不到包和包被损坏差不多是一种情况)。
2、返回的ACK丢失。对于接收方而言,这样相当于ACK被损坏,所以可以采取和ACK损坏一样的策略。
P11.
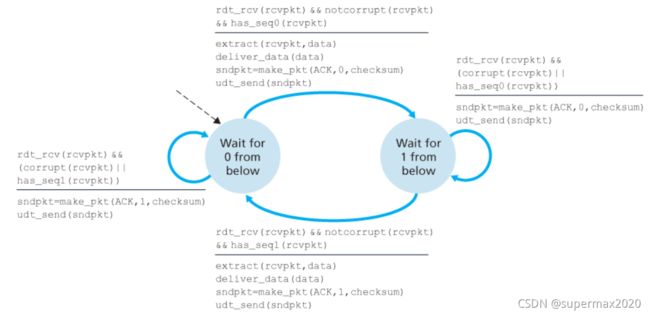
Consider the rdt2.2 receiver in Figure 3.14 , and the creation of a new packet in the self-transition (i.e., the transition from the state back to itself) in the Wait-for-0-from-below and the Wait-for-1-from-below states: sndpkt=make_pkt(ACK, 1, checksum) and sndpkt=make_pkt(ACK, 0, checksum) . Would the protocol work correctly if this action were removed from the self-transition in the Wait-for-1-from-below state? Justify your answer. What if this event were removed from the self-transition in the Wait-for-0-from-below state? [Hint: In this latter case, consider what would happen if the first sender-to-receiver packet were corrupted.]
我猜测题意是:移除sndpkt = make_pkt(ACK,1,checksum);以及udt_send(sndpkt).
不能正确工作。假如去除该动作,可能陷入死锁。
发送方发送了包0,进入等待ACK0的状态。
接收方原本处于等待包0的状态,假如接收方收到损坏的包0,则重新进入等待包0的状态,假设重新进入该状态时什么也不发送,则发送方也不会重发。
此时进入死锁。
P12.
The sender side of rdt3.0 simply ignores (that is, takes no action on) all received packets that are either in error or have the wrong value in the acknum field of anacknowledgment packet. Suppose that in such circumstances, rdt3.0 were simply to retransmit the current data packet. Would the protocol still work? (Hint: Consider what would happen if there were only bit errors; there are no packet losses but premature timeouts can occur. Consider how many times the nth packet is sent, in the limit as n approaches infinity.)
协议仍然能正常工作。这时接收端可以辨别出这是冗余包。
对此题不太理解,附上官方答案:
The protocol would still work, since a retransmission would be what would happen if the packet received with errors has actually been lost (and from the receiver standpoint, it never knows which of these events, if either, will occur).
To get at the more subtle issue behind this question, one has to allow for premature timeouts to occur. In this case, if each extra copy of the packet is ACKed and each received extra ACK causes another extra copy of the current packet to be sent, the number of times packet nis sent will increase without bound as napproaches infinity.
P13.
Consider the rdt 3.0 protocol. Draw a diagram showing that if the network connection between the sender and receiver can reorder messages (that is, that two messages propagating in the medium between the sender and receiver can be reordered), then the alternating-bit protocol will not work correctly (make sure you clearly identify the sense in which it will not work correctly). Your diagram should have the sender on the left and the receiver on the right, with the time axis running down the page, showing data (D) and acknowledgment (A) message exchange. Make sure you indicate the sequence number associated with any data or acknowledgment segment.
官方答案:
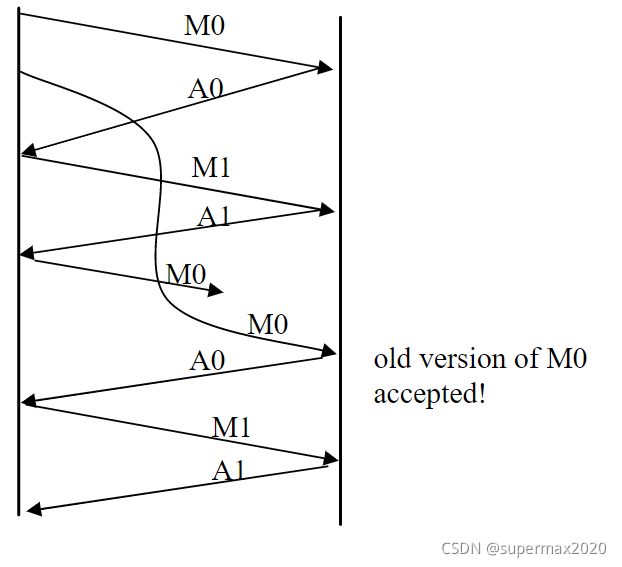
答案这张图我有很多疑问,为什么一开始M0会连续发送两次(第一次已经被成功接收了)?为什么在旧的M0到达之前,新的M0恰好丢失?
P14.
Consider a reliable data transfer protocol that uses only negative acknowledgments. Suppose the sender sends data only infrequently. Would a NAK-only protocol be preferable to a protocol that uses ACKs? Why? Now suppose the sender has a lot of data to send and the end-to-end connection experiences few losses. In this second case, would a NAK-only protocol be preferable to a protocol that uses ACKs? Why?
第一种情况:假如发送方发送数据的频率不高,不应该使用仅发送NAK的协议。
因为对仅发送NAK的协议而言,第x号分组的丢失只有在发送x+1号分组之后才能被检测到。(比如收到了x-1以及x+1,这时候就能推测x丢失了)。假如发送方发送频率不高,需要很长时间之后才能得知发送失败。
第二种情况,使用仅发送NAK的协议更好。
因为有很多数据需要发送,意味着发送的频率很高,分组的缺失很快就能做出反应。并且不发送NAK,节省了很多NAK导致的带宽。
P15.
Consider the cross-country example shown in Figure 3.17 . How big would the window size have to be for the channel utilization to be greater than 98 percent? Suppose that the size of a packet is 1,500 bytes, including both header fields and data.
注意,此题的中译本中利用率为90%,应为译者笔误(偶然发现的,其他地方有没有翻译错误我不清楚)
设窗口大小为n,一次发送n个分组。
一个RTT为30ms,传输时延为L/R,在此时间内,总时间为(RTT+L/R)
假如利用率超过98%,则传输的数据总量为:
( R T T + L / R ) × 0.98 × R (RTT+L/R)\times 0.98\times R (RTT+L/R)×0.98×R
已知传输是数据总量是nL,故可列出等式:
( R T T + L / R ) × 0.98 × R = n L (RTT+L/R)\times 0.98\times R=nL (RTT+L/R)×0.98×R=nL
解得 n=2451
一定要注意这里的传输时延是L/R(每个分组的平均时延)而不是nL/R(n个分组的总时延),在这儿犯错误很多次了QAQ
R15. (暂无答案)
Suppose Host A sends two TCP segments back to back to Host B over a TCP connection. The first segment has sequence number 90; the second has sequence number 110.
a. How much data is in the first segment?
b. Suppose that the first segment is lost but the second segment arrives at B. In the acknowledgment that Host B sends to Host A, what will be the acknowledgment number?
P16.
Suppose an application uses rdt 3.0 as its transport layer protocol. As the stop-and-wait protocol has very low channel utilization (shown in the cross-country example), the designers of this application let the receiver keep sending back a number (more than two) of alternating ACK 0 and ACK 1 even if the corresponding data have not arrived at the receiver. Would this application design increase the channel utilization? Why? Are there any potential problems with this approach? Explain.
会提高利用率。但是会产生各种问题:
1)分组丢失/损坏。由于不知道丢失的分组的序列号,接收端只能重新申请整个文件。
2)分组乱序。也很难处理,只能在应用层进行处理,但也需要发送方和接收方对包的信息有着一致的设定。
P17. (暂无答案)
Consider two network entities, A and B, which are connected by a perfect bi-directional channel (i.e., any message sent will be received correctly; the channel will not corrupt, lose, or re-order packets). A and B are to deliver data messages to each other in an alternating manner: First, A must deliver a message to B, then B must deliver a message to A, then A must deliver a message to B and so on. If an entity is in a state where it should not attempt to deliver a message to the other side, and there is an event like rdt_send(data) call from above that attempts to pass data down for transmission to the other side, this call from above can simply be ignored with a call to rdt_unable_to_send(data), which informs the higher layer that it is currently not able to send data. [Note: This simplifying assumption is made so you don’t have to worry about buffering data.] Draw a FSM specification for this protocol (one FSM for A, and one FSM for B!). Note that you do not have to worry about a reliability mechanism here; the main point of this question is to create a FSM specification that reflects the synchronized behavior of the two entities. You should use the following events and actions that have the same meaning as protocol rdt1.0 in Figure 3.9 : rdt_send(data), packet = make_pkt(data) , udt_send(packet), rdt_rcv(packet), extract (packet, data), deliver_data(data) . Make sure your protocol reflects the strict alternation of sending between A and B. Also, make sure to indicate the initial states for A and B in your FSM descriptions.
P18. (暂无答案)
In the generic SR protocol that we studied in Section 3.4.4 , the sender transmits a message as soon as it is available (if it is in the window) without waiting for an acknowledgment. Suppose now that we want an SR protocol that sends messages two at a time. That is, the sender will send a pair of messages and will send the next pair of messages only when it knows that both messages in the first pair have been received correctly. Suppose that the channel may lose messages but will not corrupt or reorder messages. Design an error-control protocol for the unidirectional reliable transfer of messages. Give an FSM description of the sender and receiver. Describe the format of the packets sent between sender and receiver, and vice versa. If you use any procedure calls other than those in Section 3.4 (for example, udt_send(), start_timer(), rdt_rcv(), and so on), clearly state their actions. Give an example (a timeline trace of sender and receiver) showing how your protocol recovers from a lost packet.
P19. (暂无答案)
Consider a scenario in which Host A wants to simultaneously send packets to Hosts B and C. A is connected to B and C via a broadcast channel—a packet sent by A is carried by the channel to both B and C. Suppose that the broadcast channel connecting A, B, and C can independently lose and corrupt packets (and so, for example, a packet sent from A might be correctly received by B, but not by C). Design a stop-and-wait-like error-control protocol for reliably transferring packets from A to B and C, such that A will not get new data from the upper layer until it knows that both B and C have correctly received the current packet. Give FSM descriptions of A and C. (Hint: The FSM for B should be essentially the same as for C.) Also, give a description of the packet format(s) used.
P20. (暂无答案)
Consider a scenario in which Host A and Host B want to send messages to Host C. Hosts A and C are connected by a channel that can lose and corrupt (but not reorder) messages. Hosts B and C are connected by another channel (independent of the channel connecting A and C) with the same properties. The transport layer at Host C should alternate in delivering messages from A and B to the layer above (that is, it should first deliver the data from a packet from A, then the data from a packet from B, and so on). Design a stop-and-wait-like error-control protocol for reliably transferring packets from A and B to C, with alternating delivery at C as described above. Give FSM descriptions of A and C. (Hint: The FSM for B should be essentially the same as for A.) Also, give a description of the packet format(s) used.
P21. (暂无答案)
Suppose we have two network entities, A and B. B has a supply of data messages that will be sent to A according to the following conventions. When A gets a request from the layer above to get the next data (D) message from B, A must send a request ® message to B on the A-to-B channel. Only when B receives an R message can it send a data (D) message back to A on the B-to-A channel. A should deliver exactly one copy of each D message to the layer above. R messages can be lost (but not corrupted) in the A-to-B channel; D messages, once sent, are always delivered correctly. The delay along both channels is unknown and variable. Design (give an FSM description of) a protocol that incorporates the appropriate mechanisms to compensate for the loss-prone A-to-B channel and implements message passing to the layer above at entity A, as discussed above. Use only those mechanisms that are absolutely necessary.
P22.
Consider the GBN protocol with a sender window size of 4 and a sequence number range of 1,024. Suppose that at time t, the next in-order packet that the receiver is expecting has a sequence number of k. Assume that the medium does not reorder messages. Answer the following questions:
a. What are the possible sets of sequence numbers inside the sender’s window at time t? Justify your answer.
b. What are all possible values of the ACK field in all possible messages currently propagating back to the sender at time t? Justify your answer.
a,可能有
k-4,k-3,k-2,k-1// 这四个分组都已经被接收端收到,只是ACK还未抵达发送端。
k-3,k-2,k-1,k/
k-2,k-1,k,k+1/
k-1,k,k+1,k+2/
k,k+1,k+2,k+3//k之前的所有分组,发送端都已经收到了ACK
因为接收端在请求k,则k之前的分组一定已经成功发送,所以发送窗口一定发送过k-1,所以序号最小的情况是[k-4,k-1],
因为接收端在请求k,则k分组一定没有得到ACK,所以序号最大的情况一定有k,该情况是[k,k+3].
在以上两种极端情况之间的都有可能。
b,所有[k-4,k-1]的分组一定是ACK。k号分组的返回消息(假如有)中一定是NAK,k之后的分组则不一定。
因为请求k,所以k之前的分组一定被成功接收,假如这些返回信息正在链路上,一定是ACK,同样的,k分组一定没有被成功接收,所以k分组对应的返回信息一定是NAK,k之后的分组是否是NAK对题目没有影响。
P23. (暂无答案)
Consider the GBN and SR protocols. Suppose the sequence number space is of size k. What is the largest allowable sender window that will avoid the occurrence of problems such as that in Figure 3.27 for each of these protocols?
P24.
Answer true or false to the following questions and briefly justify your answer:
a. With the SR protocol, it is possible for the sender to receive an ACK for a packet that falls outside of its current window.
b. With GBN, it is possible for the sender to receive an ACK for a packet that falls outside of its current window.
c. The alternating-bit protocol is the same as the SR protocol with a sender and receiver window size of 1.
d. The alternating-bit protocol is the same as the GBN protocol with a sender and receiver window size of 1.
a,对。考虑超时重发的情况。分组由于超时可能被重发了多次,这样也能得到多个ACK,超时的ACK可能在之后被发送方收到,也许抵达之时,窗口中已经没有该序列号了。
b,对。同a。
c,对。窗口为1则每个分组都要等待接收ACK,也就是停等协议。
d,对。同c。
P25.(暂无答案)
We have said that an application may choose UDP for a transport protocol because UDP offers finer application control (than TCP) of what data is sent in a segment and when.
a. Why does an application have more control of what data is sent in a segment?
b. Why does an application have more control on when the segment is sent?
P26. (暂无答案)
Consider transferring an enormous file of L bytes from Host A to Host B. Assume an MSS of 536 bytes.
a. What is the maximum value of L such that TCP sequence numbers are not exhausted? Recall that the TCP sequence number field has 4 bytes.
b. For the L you obtain in (a), find how long it takes to transmit the file. Assume that a total of 66 bytes of transport, network, and data-link header are added to each segment before the resulting packet is sent out over a 155 Mbps link. Ignore flow control and congestion control so A can pump out the segments back to back and continuously.
P27.
Host A and B are communicating over a TCP connection, and Host B has already received from A all bytes up through byte 126. Suppose Host A then sends two segments to Host B back-to-back. The first and second segments contain 80 and 40 bytes of data, respectively. In the first segment, the sequence number is 127, the source port number is 302, and the destination port number is 80. Host B sends an acknowledgment whenever it receives a segment from Host A.
a. In the second segment sent from Host A to B, what are the sequence number, source port number, and destination port number?
b. If the first segment arrives before the second segment, in the acknowledgment of the first arriving segment, what is the acknowledgment number, the source port number, and the destination port number?
c. If the second segment arrives before the first segment, in the acknowledgment of the first arriving segment, what is the acknowledgment number?
d. Suppose the two segments sent by A arrive in order at B. The first acknowledgment is lost and the second acknowledgment arrives after the first timeout interval. Draw a timing diagram, showing these segments and all other segments and acknowledgments sent. (Assume there is no additional packet loss.) For each segment in your figure, provide the sequence number and the number of bytes of data; for each acknowledgment that you add, provide the acknowledgment number.
a, 序号:207 源端口号:302 目的端口号:80
b,确认号:207, 源端口号:80, 目的端口号:302
c, 127
d,

P28.
Host A and B are directly connected with a 100 Mbps link. There is one TCP connection between the two hosts, and Host A is sending to Host B an enormous file over this connection. Host A can send its application data into its TCP socket at a rate as high as 120 Mbps but Host B can read out of its TCP receive buffer at a maximum rate of 50 Mbps. Describe the effect of TCP flow control.
由于链路传输速率限制加上TCP的拥塞控制影响,主机A发送数据的最大速率小于100 Mbps。
接收方的接收速率为50 Mbps,则当主机发送速率大于50 Mbps时,接收方的窗口逐渐被填满,直至剩余窗口为0,提示发送方停止发送,此后发送方发送试探信号,探测接收方是否有空闲窗口。如此不断往复,最终的传输速率最多为50 Mbps
官方答案有些不同,我不太理解是如何推出最终速率是60 Mbps的,在这里附上,供参考:Since the link capacity is only 100 Mbps, so host A’s sending rate can be at most 100Mbps. Still, host A sends data into the receive buffer faster than Host B can remove data from the buffer. The receive buffer fills up at a rate of roughly 40Mbps. When the buffer is full, Host B signals to Host A to stop sending data by setting RcvWindow = 0. Host A then stops sending until it receives a TCP segment with RcvWindow > 0. Host A will thus repeatedly stop and start sending as a function of the RcvWindow values itreceives from Host B. On average, the long-term rate at which Host A sends data to Host B as part of this connection is no more than 60Mbps.
P29. (暂无答案)
SYN cookies were discussed in Section 3.5.6 .
a. Why is it necessary for the server to use a special initial sequence number in the SYNACK?
b. Suppose an attacker knows that a target host uses SYN cookies. Can the attacker create half-open or fully open connections by simply sending an ACK packet to the target? Why or why not?
c. Suppose an attacker collects a large amount of initial sequence numbers sent by the server. Can the attacker cause the server to create many fully open connections by sending ACKs with those initial sequence numbers? Why?
P30. (暂无答案)
Consider the network shown in Scenario 2 in Section 3.6.1 . Suppose both sending hosts A and B have some fixed timeout values.
a. Argue that increasing the size of the finite buffer of the router might possibly decrease the throughput (λ ).
b. Now suppose both hosts dynamically adjust their timeout values (like what TCP does) based on the buffering delay at the router. Would increasing the buffer size help to increase the throughput? Why?
P31.
Suppose that the five measured SampleRTT values (see Section 3.5.3 ) are 106 ms, 120ms, 140 ms, 90 ms, and 115 ms. Compute the EstimatedRTT after each of these SampleRTT values is obtained, using a value of α = 0.125 \alpha=0.125 α=0.125 and assuming that the value of EstimatedRTT was 100 ms just before the first of these five samples were obtained. Compute also the DevRTT after each sample is obtained, assuming a value of β = 0.25 \beta=0.25 β=0.25 and assuming the value of DevRTT was 5 ms just before the first of these five samples was obtained. Last, compute the TCP
TimeoutInterval after each of these samples is obtained.
初始: EstimatedRTT为100ms, DevRTT为5ms
根据以下公式进行迭代:
D e v R T T = ( 1 − β ) D e v R T T + β × ∣ s a m p l e R T T − D e v R T T ∣ DevRTT=(1-\beta)DevRTT+\beta\times|sampleRTT-DevRTT| DevRTT=(1−β)DevRTT+β×∣sampleRTT−DevRTT∣
E s t i m a t e d R T T = ( 1 − α ) × E s t i m a t e d R T T + α × s a m p l e R T T EstimatedRTT=(1-\alpha)\times EstimatedRTT+\alpha\times sampleRTT EstimatedRTT=(1−α)×EstimatedRTT+α×sampleRTT
计算结果:
测得第一个sampleRTT后:
DevRTT = 0.755 + 0.25 * | 106 - 100 | = 5.25ms
EstimatedRTT = 0.875 * 100 + 0.125 * 106 = 100.75 ms
TimeoutInterval = 100.75+45.25 = 121.75 ms
测得第二个sampleRTT后:
DevRTT = 0.755.25 + 0.25 * | 120 – 100.75 | = 8.75 ms
EstimatedRTT = 0.875 * 100.75 + 0.125 * 120 = 103.16 ms
TimeoutInterval = 103.16+48.75 = 138.16 ms
测得第三个sampleRTT后:
DevRTT = 0.758.75 + 0.25 * | 140 – 103.16 | = 15.77 ms
EstimatedRTT = 0.875 * 103.16 + 0.125 * 140 = 107.76 ms
TimeoutInterval = 107.76+415.77 = 170.84 ms
测得第四个sampleRTT后:
DevRTT = 0.7515.77 + 0.25 * | 90 – 107.76 | = 16.27 ms
EstimatedRTT = 0.875 * 107.76 + 0.125 * 90 = 105.54 ms
TimeoutInterval = 105.54+416.27 =170.62 ms
测得第五个sampleRTT后:
DevRTT = 0.7516.27 + 0.25 * | 115 – 105.54 | = 14.57 ms
EstimatedRTT = 0.875 * 105.54 + 0.125 * 115 = 106.72 ms
TimeoutInterval = 106.72+414.57 =165 ms
P32.
Consider the TCP procedure for estimating RTT. Suppose that α = 0.1 \alpha=0.1 α=0.1. Let S a m p l e R T T 1 {SampleRTT}_1 SampleRTT1 be the most recent sample RTT, let S a m p l e R T T 2 {SampleRTT}_2 SampleRTT2 be the next most recent sample RTT, and so on.
a. For a given TCP connection, suppose four acknowledgments have been returned with corresponding sample RTTs: S a m p l e R T T 4 {SampleRTT}_4 SampleRTT4 , S a m p l e R T T 3 {SampleRTT}_3 SampleRTT3 , S a m p l e R T T 2 {SampleRTT}_2 SampleRTT2 , and S a m p l e R T T 1 {SampleRTT}_1 SampleRTT1 . Express E s t i m a t e d R T T EstimatedRTT EstimatedRTT in terms of the four sample RTTs.
b. Generalize your formula for n sample RTTs.
c. For the formula in part (b) let n approach infinity. Comment on why this averaging procedure is called an exponential moving average.
a,
设 E s t i m a t e d R T T n 是 S a m p l e R T T n 被 接 收 后 得 到 的 EstimatedRTT_n是SampleRTT_n被接收后得到的 EstimatedRTTn是SampleRTTn被接收后得到的
E s t i m a t e d R T T 4 = s a m p l e R T T 4 EstimatedRTT_4=sampleRTT_4 EstimatedRTT4=sampleRTT4
E s t i m a t e d R T T 3 = E s t i m a t e d R T T 4 × ( 1 − α ) + s a m p l e R T T 3 × α = s a m p l e R T T 4 × ( 1 − α ) + s a m p l e R T T 3 × α \begin{aligned} EstimatedRTT_3&=EstimatedRTT_4\times (1-\alpha)+sampleRTT_3\times \alpha\\ &=sampleRTT_4\times (1-\alpha)+sampleRTT_3\times \alpha\end{aligned} EstimatedRTT3=EstimatedRTT4×(1−α)+sampleRTT3×α=sampleRTT4×(1−α)+sampleRTT3×α
E s t i m a t e d R T T 2 = E s t i m a t e d R T T 3 × ( 1 − α ) + s a m p l e R T T 2 × α = ( s a m p l e R T T 4 × ( 1 − α ) + s a m p l e R T T 3 × α ) × ( 1 − α ) + s a m p l e R T T 2 × α = s a m p l e R T T 4 × ( 1 − α ) 2 + s a m p l e R T T 3 × α ( 1 − α ) + s a m p l e R T T 2 × α \begin{aligned} EstimatedRTT_2&=EstimatedRTT_3\times (1-\alpha)+sampleRTT_2\times \alpha\\ &=(sampleRTT_4\times (1-\alpha)+sampleRTT_3\times \alpha)\times (1-\alpha)+sampleRTT_2\times \alpha\\ &=sampleRTT_4\times (1-\alpha)^2+sampleRTT_3\times\alpha(1-\alpha)+sampleRTT_2\times \alpha\end{aligned} EstimatedRTT2=EstimatedRTT3×(1−α)+sampleRTT2×α=(sampleRTT4×(1−α)+sampleRTT3×α)×(1−α)+sampleRTT2×α=sampleRTT4×(1−α)2+sampleRTT3×α(1−α)+sampleRTT2×α
最终结果为:
E s t i m a t e d R T T 1 = α × s a m p l e R T T 1 + ( 1 − α ) α × s a m p l e R T T 2 + ( 1 − α ) 2 α × s a m p l e R T T 3 + ( 1 − α ) 3 s a m p l e R T T 4 EstimatedRTT_1=\alpha\times sampleRTT_1+(1-\alpha)\alpha\times sampleRTT_2+\\(1-\alpha)^2\alpha\times sampleRTT_3+(1-\alpha)^3sampleRTT_4 EstimatedRTT1=α×sampleRTT1+(1−α)α×sampleRTT2+(1−α)2α×sampleRTT3+(1−α)3sampleRTT4
b,
E s t i m a t e d R T T 1 = ∑ k = 1 n − 1 ( 1 − α ) k − 1 α × s a m p l e R T T k + ( 1 − α ) n − 1 s a m p l e R T T n EstimatedRTT_1=\sum^{n-1}_{k=1}(1-\alpha)^{k-1}\alpha \times sampleRTT_k+(1-\alpha)^{n-1}sampleRTT_n EstimatedRTT1=∑k=1n−1(1−α)k−1α×sampleRTTk+(1−α)n−1sampleRTTn
c,n趋于无穷,则:
E s t i m a t e d R T T 1 = ∑ k = 1 ∞ ( 1 − α ) k − 1 α × s a m p l e R T T k = 0.1 ∑ k = 1 ∞ ( 0.9 ) k − 1 × s a m p l e R T T k = 1 9 ∑ k = 1 ∞ ( 0.9 ) k × s a m p l e R T T k \begin{aligned}EstimatedRTT_1&=\sum^{\infty}_{k=1}(1-\alpha)^{k-1}\alpha \times sampleRTT_k\\ &=0.1\sum^{\infty}_{k=1}(0.9)^{k-1} \times sampleRTT_k\\ &=\frac{1}{9}\sum^{\infty}_{k=1}(0.9)^{k} \times sampleRTT_k\end{aligned} EstimatedRTT1=k=1∑∞(1−α)k−1α×sampleRTTk=0.1k=1∑∞(0.9)k−1×sampleRTTk=91k=1∑∞(0.9)k×sampleRTTk
可以看出,每一个sampleRTT的权重是呈指数分布的。
P33. (暂无答案)
In Section 3.5.3 , we discussed TCP’s estimation of RTT. Why do you think TCP avoids measuring the SampleRTT for retransmitted segments?
P34. (暂无答案)
What is the relationship between the variable SendBase in Section 3.5.4 and the variable LastByteRcvd in Section 3.5.5 ?
P35. (暂无答案)
What is the relationship between the variable LastByteRcvd in Section 3.5.5 and the variable y in Section 3.5.4?
P36. (暂无答案)
In Section 3.5.4 , we saw that TCP waits until it has received three duplicate ACKs before performing a fast retransmit. Why do you think the TCP designers chose not to perform a fast retransmit after the first duplicate ACK for a segment is received?
P37. (暂无答案)
Compare GBN, SR, and TCP (no delayed ACK). Assume that the timeout values for all three protocols are sufficiently long such that 5 consecutive data segments and their corresponding ACKs can be received (if not lost in the channel) by the receiving host (Host B) and the sending host (Host A) respectively. Suppose Host A sends 5 data segments to Host B, and the 2nd segment (sent from A) is lost. In the end, all 5 data segments have been correctly received by Host B.
a. How many segments has Host A sent in total and how many ACKs has Host B sent in total? What are their sequence numbers? Answer this question for all three protocols.
b. If the timeout values for all three protocol are much longer than 5 RTT, then which protocol successfully delivers all five data segments in shortest time interval?
P38. (暂无答案)
In our description of TCP in Figure 3.53 , the value of the threshold, ssthresh, is set as ssthresh=cwnd/2 in several places and ssthresh value is referred to as being set to half the window size when a loss event occurred. Must the rate at which the sender is sending when the loss event occurred be approximately equal to cwnd segments per RTT? Explain your answer. If your answer is no, can you suggest a different manner in which ssthresh should be set?
P39.
Consider Figure 3.46(b) . If λ i n ′ λ'_{in} λin′ increases beyond R/2, can λ o u t λ_{out} λout increase beyond R/3? Explain. Now consider Figure 3.46(c) . If λ i n ′ λ'_{in} λin′ increases beyond R/2, can λ o u t λ_{out} λout increase beyond R/4 under the assumption that a packet will be forwarded twice on average from the router to the receiver? Explain.

- 由于链路只能提供给主机A R/2的吞吐量,若 λ i n ′ λ'_{in} λin′超过R/2, 则进入发送链路的速率最高为R/2,多余的数据会被直接丢失,与 λ i n ′ = R / 2 λ'_{in}=R/2 λin′=R/2的情况相比,传如发送链路的数据没有增加,并且由于丢包增多,重发会有更多的负荷,实际的 λ o u t λ_{out} λout反而会降低。
故 λ o u t λ_{out} λout会小于R/3
2)基于与1)同样的理由,即可用吞吐量有限,当 λ i n ′ λ'_{in} λin′超过R/2,实际的 λ o u t λ_{out} λout已达到最大,即R/4.继续增大 λ i n ′ λ'_{in} λin′不会使得 λ o u t λ_{out} λout增加。