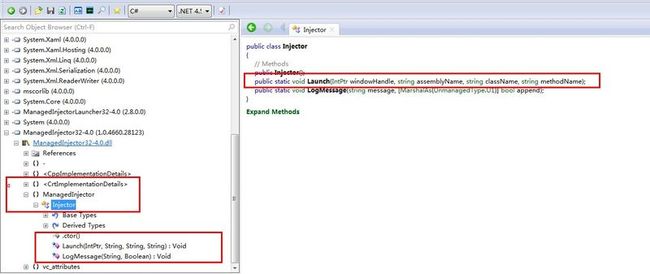
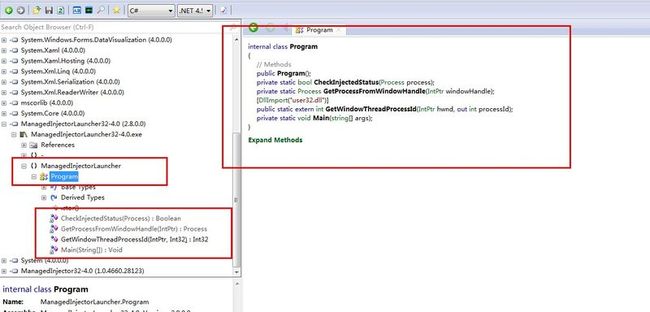
Snoop工具抓取Wpf应用程序的核心code
1.所需组件:(1)ManagedInjector32-4.0.dll
(2)ManagedInjectorLauncher32-4.0.exe
(3)Snoop.exe
2.核心算法介绍:
2.1 ManagedInjector32-4.0.dll:
public static unsafe void Launch(IntPtr windowHandle, string assemblyName, string className, string methodName) { HINSTANCE__* hinstance__Ptr; string str2 = "$"; string str = (assemblyName + str2 + className) + str2 + methodName; ref byte modopt(IsExplicitlyDereferenced) numRef = (ref byte modopt(IsExplicitlyDereferenced)) str; if (numRef != null) { numRef = ((ref byte modopt(IsExplicitlyDereferenced)) RuntimeHelpers.OffsetToStringData) + numRef; } ref char modopt(IsConst) modopt(IsExplicitlyDereferenced) pinned chRef = numRef; int num3 = (int) __unep@?MessageHookProc@@$$FYGJHIJ@Z; if (GetModuleHandleExW(4, (char modopt(IsConst)*) num3, &hinstance__Ptr) != 0) { LogMessage("GetModuleHandleEx successful", true); uint modopt(IsLong) num2 = 0; uint modopt(IsLong) windowThreadProcessId = GetWindowThreadProcessId((HWND__*) windowHandle.ToPointer(), &num2); if (num2 != null) { LogMessage("Got process id", true); void* voidPtr = OpenProcess(0x1f0fff, 0, num2); if (voidPtr != null) { LogMessage("Got process handle", true); int num = (str.Length * 2) + 2; void* voidPtr2 = VirtualAllocEx(voidPtr, null, (uint modopt(IsLong)) num, 0x1000, 4); if (voidPtr2 != null) { LogMessage("VirtualAllocEx successful", true); WriteProcessMemory(voidPtr, voidPtr2, chRef, (uint modopt(IsLong)) num, null); ?A0x7cab18b3._messageHookHandle = SetWindowsHookExW(4, (int modopt(IsLong) modopt(CallConvStdcall) *(int, uint, int modopt(IsLong))) num3, hinstance__Ptr, windowThreadProcessId); if (?A0x7cab18b3._messageHookHandle != null) { LogMessage("SetWindowsHookEx successful", true); uint num4 = ?A0x7cab18b3.WM_GOBABYGO; SendMessageW((HWND__*) windowHandle.ToPointer(), num4, (uint) voidPtr2, 0); UnhookWindowsHookEx(?A0x7cab18b3._messageHookHandle); } VirtualFreeEx(voidPtr, voidPtr2, 0, 0x8000); } CloseHandle(voidPtr); } } FreeLibrary(hinstance__Ptr); } }
2.2 ManagedInjectorLauncher32-4.0.exe:
private static void Main(string[] args) { Injector.LogMessage("Starting the injection process...", false); IntPtr windowHandle = (IntPtr) long.Parse(args[0]); string assemblyName = args[1]; string className = args[2]; string methodName = args[3]; Injector.Launch(windowHandle, assemblyName, className, methodName); Process processFromWindowHandle = GetProcessFromWindowHandle(windowHandle); if (((processFromWindowHandle != null) && !CheckInjectedStatus(processFromWindowHandle)) && (processFromWindowHandle.MainWindowHandle != windowHandle)) { Injector.LogMessage("Could not inject with current handle... retrying with MainWindowHandle", true); Injector.Launch(processFromWindowHandle.MainWindowHandle, assemblyName, className, methodName); CheckInjectedStatus(processFromWindowHandle); } }
private static bool CheckInjectedStatus(Process process) { bool flag = false; process.Refresh(); foreach (ProcessModule module in process.Modules) { if (module.FileName.Contains("ManagedInjector")) { flag = true; } } if (flag) { Injector.LogMessage(string.Format("Successfully injected Snoop for process {0} (PID = {1})", process.ProcessName, process.Id), true); return flag; } Injector.LogMessage(string.Format("Failed to inject for process {0} (PID = {1})", process.ProcessName, process.Id), true); return flag; }
private static Process GetProcessFromWindowHandle(IntPtr windowHandle) { int num; GetWindowThreadProcessId(windowHandle, out num); if (num == 0) { Injector.LogMessage(string.Format("could not get process for window handle {0}", windowHandle), true); return null; } Process processById = Process.GetProcessById(num); if (processById == null) { Injector.LogMessage(string.Format("could not get process for PID = {0}", num), true); return null; } return processById; }