国密算法 ZUC流密码 祖冲之密码 python代码完整实现
此前发布了包含SM2公钥密码、SM3杂凑算法和SM4分组密码的国密算法完整工具包,其实还是有些不完整,因为没有流密码。今天把我们国家自己的流密码——ZUC祖冲之密码算法补充上。介绍其他国密算法的链接如下:
SM2:国密算法 SM2 公钥加密 非对称加密 数字签名 密钥协商 python实现完整代码_qq_43339242的博客-CSDN博客_python国密sm2
SM3:国密算法 SM3 消息摘要 杂凑算法 哈希函数 散列函数 python实现完整代码_qq_43339242的博客-CSDN博客
SM4:国密算法 SM4 对称加密 分组密码 python实现完整代码_qq_43339242的博客-CSDN博客_sm4代码python
对上述几个算法和实现不了解的,建议点进去看看。下面这篇文章是对上述的汇总:
国密算法 SM2公钥密码 SM3杂凑算法 SM4分组密码 python代码完整实现
所有代码托管在码云:hggm - 国密算法 SM2 SM3 SM4 python实现完整代码: 国密算法 SM2公钥密码 SM3杂凑算法 SM4分组密码 python代码完整实现 效率高于所有公开的python国密算法库 (gitee.com)
废话多了。上ZUC的代码:
from array import array
_ZUC_D = [0x44D700, 0x26BC00, 0x626B00, 0x135E00, 0x578900, 0x35E200, 0x713500, 0x09AF00,
0x4D7800, 0x2F1300, 0x6BC400, 0x1AF100, 0x5E2600, 0x3C4D00, 0x789A00, 0x47AC00]
_ZUC_S0 = bytes([
0x3E, 0x72, 0x5B, 0x47, 0xCA, 0xE0, 0x00, 0x33, 0x04, 0xD1, 0x54, 0x98, 0x09, 0xB9, 0x6D, 0xCB,
0x7B, 0x1B, 0xF9, 0x32, 0xAF, 0x9D, 0x6A, 0xA5, 0xB8, 0x2D, 0xFC, 0x1D, 0x08, 0x53, 0x03, 0x90,
0x4D, 0x4E, 0x84, 0x99, 0xE4, 0xCE, 0xD9, 0x91, 0xDD, 0xB6, 0x85, 0x48, 0x8B, 0x29, 0x6E, 0xAC,
0xCD, 0xC1, 0xF8, 0x1E, 0x73, 0x43, 0x69, 0xC6, 0xB5, 0xBD, 0xFD, 0x39, 0x63, 0x20, 0xD4, 0x38,
0x76, 0x7D, 0xB2, 0xA7, 0xCF, 0xED, 0x57, 0xC5, 0xF3, 0x2C, 0xBB, 0x14, 0x21, 0x06, 0x55, 0x9B,
0xE3, 0xEF, 0x5E, 0x31, 0x4F, 0x7F, 0x5A, 0xA4, 0x0D, 0x82, 0x51, 0x49, 0x5F, 0xBA, 0x58, 0x1C,
0x4A, 0x16, 0xD5, 0x17, 0xA8, 0x92, 0x24, 0x1F, 0x8C, 0xFF, 0xD8, 0xAE, 0x2E, 0x01, 0xD3, 0xAD,
0x3B, 0x4B, 0xDA, 0x46, 0xEB, 0xC9, 0xDE, 0x9A, 0x8F, 0x87, 0xD7, 0x3A, 0x80, 0x6F, 0x2F, 0xC8,
0xB1, 0xB4, 0x37, 0xF7, 0x0A, 0x22, 0x13, 0x28, 0x7C, 0xCC, 0x3C, 0x89, 0xC7, 0xC3, 0x96, 0x56,
0x07, 0xBF, 0x7E, 0xF0, 0x0B, 0x2B, 0x97, 0x52, 0x35, 0x41, 0x79, 0x61, 0xA6, 0x4C, 0x10, 0xFE,
0xBC, 0x26, 0x95, 0x88, 0x8A, 0xB0, 0xA3, 0xFB, 0xC0, 0x18, 0x94, 0xF2, 0xE1, 0xE5, 0xE9, 0x5D,
0xD0, 0xDC, 0x11, 0x66, 0x64, 0x5C, 0xEC, 0x59, 0x42, 0x75, 0x12, 0xF5, 0x74, 0x9C, 0xAA, 0x23,
0x0E, 0x86, 0xAB, 0xBE, 0x2A, 0x02, 0xE7, 0x67, 0xE6, 0x44, 0xA2, 0x6C, 0xC2, 0x93, 0x9F, 0xF1,
0xF6, 0xFA, 0x36, 0xD2, 0x50, 0x68, 0x9E, 0x62, 0x71, 0x15, 0x3D, 0xD6, 0x40, 0xC4, 0xE2, 0x0F,
0x8E, 0x83, 0x77, 0x6B, 0x25, 0x05, 0x3F, 0x0C, 0x30, 0xEA, 0x70, 0xB7, 0xA1, 0xE8, 0xA9, 0x65,
0x8D, 0x27, 0x1A, 0xDB, 0x81, 0xB3, 0xA0, 0xF4, 0x45, 0x7A, 0x19, 0xDF, 0xEE, 0x78, 0x34, 0x60])
_ZUC_S1 = bytes([
0x55, 0xC2, 0x63, 0x71, 0x3B, 0xC8, 0x47, 0x86, 0x9F, 0x3C, 0xDA, 0x5B, 0x29, 0xAA, 0xFD, 0x77,
0x8C, 0xC5, 0x94, 0x0C, 0xA6, 0x1A, 0x13, 0x00, 0xE3, 0xA8, 0x16, 0x72, 0x40, 0xF9, 0xF8, 0x42,
0x44, 0x26, 0x68, 0x96, 0x81, 0xD9, 0x45, 0x3E, 0x10, 0x76, 0xC6, 0xA7, 0x8B, 0x39, 0x43, 0xE1,
0x3A, 0xB5, 0x56, 0x2A, 0xC0, 0x6D, 0xB3, 0x05, 0x22, 0x66, 0xBF, 0xDC, 0x0B, 0xFA, 0x62, 0x48,
0xDD, 0x20, 0x11, 0x06, 0x36, 0xC9, 0xC1, 0xCF, 0xF6, 0x27, 0x52, 0xBB, 0x69, 0xF5, 0xD4, 0x87,
0x7F, 0x84, 0x4C, 0xD2, 0x9C, 0x57, 0xA4, 0xBC, 0x4F, 0x9A, 0xDF, 0xFE, 0xD6, 0x8D, 0x7A, 0xEB,
0x2B, 0x53, 0xD8, 0x5C, 0xA1, 0x14, 0x17, 0xFB, 0x23, 0xD5, 0x7D, 0x30, 0x67, 0x73, 0x08, 0x09,
0xEE, 0xB7, 0x70, 0x3F, 0x61, 0xB2, 0x19, 0x8E, 0x4E, 0xE5, 0x4B, 0x93, 0x8F, 0x5D, 0xDB, 0xA9,
0xAD, 0xF1, 0xAE, 0x2E, 0xCB, 0x0D, 0xFC, 0xF4, 0x2D, 0x46, 0x6E, 0x1D, 0x97, 0xE8, 0xD1, 0xE9,
0x4D, 0x37, 0xA5, 0x75, 0x5E, 0x83, 0x9E, 0xAB, 0x82, 0x9D, 0xB9, 0x1C, 0xE0, 0xCD, 0x49, 0x89,
0x01, 0xB6, 0xBD, 0x58, 0x24, 0xA2, 0x5F, 0x38, 0x78, 0x99, 0x15, 0x90, 0x50, 0xB8, 0x95, 0xE4,
0xD0, 0x91, 0xC7, 0xCE, 0xED, 0x0F, 0xB4, 0x6F, 0xA0, 0xCC, 0xF0, 0x02, 0x4A, 0x79, 0xC3, 0xDE,
0xA3, 0xEF, 0xEA, 0x51, 0xE6, 0x6B, 0x18, 0xEC, 0x1B, 0x2C, 0x80, 0xF7, 0x74, 0xE7, 0xFF, 0x21,
0x5A, 0x6A, 0x54, 0x1E, 0x41, 0x31, 0x92, 0x35, 0xC4, 0x33, 0x07, 0x0A, 0xBA, 0x7E, 0x0E, 0x34,
0x88, 0xB1, 0x98, 0x7C, 0xF3, 0x3D, 0x60, 0x6C, 0x7B, 0xCA, 0xD3, 0x1F, 0x32, 0x65, 0x04, 0x28,
0x64, 0xBE, 0x85, 0x9B, 0x2F, 0x59, 0x8A, 0xD7, 0xB0, 0x25, 0xAC, 0xAF, 0x12, 0x03, 0xE2, 0xF2])
_ZUC_S = array('H')
for byte1 in _ZUC_S0: # 构造两字节的S盒变换表
byte1 <<= 8
_ZUC_S.extend(byte1 | byte2 for byte2 in _ZUC_S1)
class ZUC:
def __init__(self, key, iv):
lfsr = self.lfsr = [_ZUC_D[i] | key[i] << 23 | iv[i] for i in range(16)]
self.r = 0, 0
for i in range(32):
c = (((lfsr[15] << 1 & 0xFFFF0000 | lfsr[14] & 0xFFFF) ^ self.r[0]) + self.r[1] >> 1 & 0x7FFFFFFF)\
+ self.lfsr_next()
self.lfsr_shift((c & 0x7FFFFFFF) + (c >> 31))
def lfsr_next(self):
lfsr, r = self.lfsr, self.r
W1, W2 = r[0] + (lfsr[11] << 16 | lfsr[9] >> 15) & 0xFFFFFFFF, r[1] ^ ((lfsr[7] & 0xFFFF) << 16 | lfsr[5] >> 15)
x, y = (W1 & 0xFFFF) << 16 | W2 >> 16, (W2 & 0xFFFF) << 16 | W1 >> 16 # L线性变换
u = (x ^ (x << 2 | x >> 30) ^ (x << 10 | x >> 22) ^ (x << 18 | x >> 14) ^ (x << 24 | x >> 8)) & 0xFFFFFFFF
v = (y ^ (y << 8 | y >> 24) ^ (y << 14 | y >> 18) ^ (y << 22 | y >> 10) ^ (y << 30 | y >> 2)) & 0xFFFFFFFF
self.r = _ZUC_S[u >> 16] << 16 | _ZUC_S[u & 0xFFFF], _ZUC_S[v >> 16] << 16 | _ZUC_S[v & 0xFFFF] # S盒变换
v_0, v_4, v_10, v_13, v_15 = lfsr[0], lfsr[4], lfsr[10], lfsr[13], lfsr[15]
c = v_0 + ((v_0 << 8 | v_0 >> 23) & 0x7FFFFFFF)
c = (c & 0x7FFFFFFF) + (c >> 31) + ((v_4 << 20 | v_4 >> 11) & 0x7FFFFFFF)
c = (c & 0x7FFFFFFF) + (c >> 31) + ((v_10 << 21 | v_10 >> 10) & 0x7FFFFFFF)
c = (c & 0x7FFFFFFF) + (c >> 31) + ((v_13 << 17 | v_13 >> 14) & 0x7FFFFFFF)
c = (c & 0x7FFFFFFF) + (c >> 31) + ((v_15 << 15 | v_15 >> 16) & 0x7FFFFFFF)
return (c & 0x7FFFFFFF) + (c >> 31)
def lfsr_shift(self, x):
self.lfsr.pop(0)
self.lfsr.append(x)
def enc(self, data):
res, lfsr = [], self.lfsr
for i in data:
self.lfsr_shift(self.lfsr_next())
res.append(i ^ ((lfsr[15] << 1 & 0xFFFF0000 | lfsr[14] & 0xFFFF) ^ self.r[0]) + self.r[1] & 0xFFFFFFFF
^ ((lfsr[2] & 0xFFFF) << 16 | lfsr[0] >> 15))
self.lfsr_shift(self.lfsr_next())
return res
这是未加速的版本,numba加速版本和测试代码请到码云下载。本代码的使用方法请参考测试代码。以下是从国密算法工具包的完整测试代码中截取的一部分和ZUC相关的:
import os
import random
import time
import numpy as np
from Crypto.Cipher import ARC4
from pysmx.ZUC import ZUC as ZUC_pysmx
from hggm.ZUC import ZUC as ZUC_my_fast
from hggm.slow.ZUC import ZUC as ZUC_my
def zuc_compare_test():
# 随机生成128位的密钥和初始向量
key, iv = os.urandom(16), os.urandom(16)
test_data = os.urandom(128)
test_num = 50 # 测试次数
# 随机生成消息
short_data = [os.urandom(random.randint(16, 48)) for _ in range(test_num)] # 短消息列表
long_data = [os.urandom(random.randint(1000, 2000)) for _ in range(test_num)] # 长消息列表
enc_data_arc4 = [b''] * test_num
enc_data_pysmx = [b''] * test_num
enc_data_my = [b''] * test_num
enc_data_my_fast = [b''] * test_num
enc_data_arc4_2 = [b''] * test_num
enc_data_pysmx2 = [b''] * test_num
enc_data_my2 = [b''] * test_num
enc_data_my_fast2 = [b''] * test_num
dec_data = [b''] * test_num
dec_data2 = [b''] * test_num
print('\n———————————————————————————————————————————流密码测试———————————————————————————————————————————')
print('前两次加密消息长度:%dB\n后两项为连续加密——短消息平均长度:%.1fB 长消息平均长度:%.1fB 测试次数:%d' %
(len(test_data), np.mean(list(map(len, short_data))), np.mean(list(map(len, long_data))), test_num))
print('算法库名\t\t\t首次初始化(μs)\t再次初始化(μs)\t首次加密(μs)\t再次加密(μs)\t处理短消息(ms)\t处理长消息(ms)')
# Crypto - ARC4
time_1 = time.perf_counter()
arc4 = ARC4.new(key)
time_2 = time.perf_counter()
arc4_2 = ARC4.new(key)
time_3 = time.perf_counter()
arc4.encrypt(test_data)
time_4 = time.perf_counter()
arc4_2.encrypt(test_data)
time_5 = time.perf_counter()
for i in range(test_num):
enc_data_arc4[i] = arc4.encrypt(short_data[i]) # 加密短消息
time_6 = time.perf_counter()
for i in range(test_num):
enc_data_arc4_2[i] = arc4.encrypt(long_data[i]) # 加密长消息
time_7 = time.perf_counter()
print('Crypto-ARC4\t\t%.2f\t\t\t%.2f\t\t\t%.2f\t\t%.2f\t\t%.2f\t\t\t%.2f' %
((time_2 - time_1) * 1000000, (time_3 - time_2) * 1000000, (time_4 - time_3) * 1000000,
(time_5 - time_4) * 1000000, (time_6 - time_5) * 1000, (time_7 - time_6) * 1000))
# pysmx - ZUC
time_1 = time.perf_counter()
zuc_smx = ZUC_pysmx(key, iv)
time_2 = time.perf_counter()
zuc_smx2 = ZUC_pysmx(key, iv)
time_3 = time.perf_counter()
zuc_smx.zuc_encrypt(test_data)
time_4 = time.perf_counter()
zuc_smx2.zuc_encrypt(test_data)
time_5 = time.perf_counter()
for i in range(test_num):
enc_data_pysmx[i] = zuc_smx.zuc_encrypt(short_data[i]) # 加密短消息
time_6 = time.perf_counter()
for i in range(test_num):
enc_data_pysmx2[i] = zuc_smx.zuc_encrypt(long_data[i]) # 加密长消息
time_7 = time.perf_counter()
print('pysmx-ZUC\t\t%.2f\t\t\t%.2f\t\t\t%.2f\t\t%.2f\t\t%.2f\t\t\t%.2f' %
((time_2 - time_1) * 1000000, (time_3 - time_2) * 1000000, (time_4 - time_3) * 1000000,
(time_5 - time_4) * 1000000, (time_6 - time_5) * 1000, (time_7 - time_6) * 1000))
time_aim = time_7 - time_5
# my - ZUC
time_1 = time.perf_counter()
zuc_my = ZUC_my(key, iv)
time_2 = time.perf_counter()
zuc_my2 = ZUC_my(key, iv)
time_3 = time.perf_counter()
zuc_my.enc(test_data)
time_4 = time.perf_counter()
zuc_my2.enc(test_data)
time_5 = time.perf_counter()
for i in range(test_num):
enc_data_my[i] = zuc_my.enc(short_data[i]) # 加密短消息
time_6 = time.perf_counter()
for i in range(test_num):
enc_data_my2[i] = zuc_my.enc(long_data[i]) # 加密长消息
time_7 = time.perf_counter()
print('my-ZUC\t\t\t%.2f\t\t\t%.2f\t\t\t%.2f\t\t%.2f\t\t%.2f\t\t\t%.2f' %
((time_2 - time_1) * 1000000, (time_3 - time_2) * 1000000, (time_4 - time_3) * 1000000,
(time_5 - time_4) * 1000000, (time_6 - time_5) * 1000, (time_7 - time_6) * 1000))
time_my = time_7 - time_5
# my - ZUC(fast)
time_1 = time.perf_counter()
zuc_my_fast = ZUC_my_fast(key, iv)
time_2 = time.perf_counter()
zuc_my_fast2 = ZUC_my_fast(key, iv)
time_3 = time.perf_counter()
zuc_my_fast.enc(test_data)
time_4 = time.perf_counter()
zuc_my_fast2.enc(test_data)
time_5 = time.perf_counter()
for i in range(test_num):
enc_data_my_fast[i] = zuc_my_fast.enc(short_data[i]) # 加密短消息
time_6 = time.perf_counter()
for i in range(test_num):
enc_data_my_fast2[i] = zuc_my_fast.enc(long_data[i]) # 加密长消息
time_7 = time.perf_counter()
print('my-ZUC(fast)\t%.2f\t\t\t%.2f\t\t\t%.2f\t\t%.2f\t\t%.2f\t\t\t%.2f' %
((time_2 - time_1) * 1000000, (time_3 - time_2) * 1000000, (time_4 - time_3) * 1000000,
(time_5 - time_4) * 1000000, (time_6 - time_5) * 1000, (time_7 - time_6) * 1000))
time_my_fast = time_7 - time_5
print('连续加密时,未加速时总耗时为pysmx的%.2f%%' % (time_my / time_aim * 100))
print('加速以后总耗时为pysmx的%.2f%%、未加速的%.2f%%' % (time_my_fast / time_aim * 100, time_my_fast / time_my * 100))
assert enc_data_pysmx == enc_data_my == list(map(list, enc_data_my_fast)) # 短消息加密生成的列表
assert enc_data_pysmx2 == enc_data_my2 == list(map(list, enc_data_my_fast2)) # 长消息加密生成的列表
# ARC4解密
for i in range(test_num): # 解密短消息
dec_data[i] = arc4_2.decrypt(enc_data_arc4[i])
for i in range(test_num): # 解密长消息
dec_data2[i] = arc4_2.decrypt(enc_data_arc4_2[i])
assert dec_data == short_data and dec_data2 == long_data
# ZUC解密
for i in range(test_num): # 解密短消息
dec_data[i] = bytes(zuc_my2.enc(enc_data_my[i]))
dec_data2[i] = zuc_my_fast2.dec(enc_data_my_fast[i]).astype(np.uint8).tobytes()
assert dec_data == dec_data2 == short_data
for i in range(test_num): # 解密长消息(因为是流密码,从始至终加密和解密的顺序必须完全一致)
dec_data[i] = bytes(zuc_my2.enc(enc_data_my2[i]))
dec_data2[i] = zuc_my_fast2.dec(enc_data_my_fast2[i]).astype(np.uint8).tobytes()
assert dec_data == dec_data2 == long_data
if __name__ == "__main__":
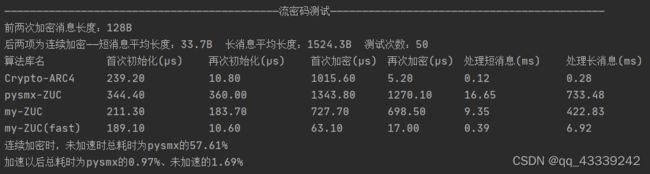
zuc_compare_test()测试结果如下图:
效果还行,未加速版本的耗时约为pysmx库的60%,加速以后耗时约为其1%。未加速时能比pysmx库快一点,是因为采用了双字节S盒表,减少了函数调用和冗余计算(代码比pysmx库的实现短了很多,可能对可读性有些影响)。
需要注意的是,解密流密码密文时,必须保证解密顺序与加密时完全对应。本代码的解密方法可参考上面测试代码的最后一段,未加速版本统一用"enc"方法实现加密和解密,加速版本用"dec"方法实现解密。加密和解密后,我没有去转输出类型,未加速版本输出的是list,加速版本输出的是np数组,个人认为这个留给使用者自己转会更好,免得画蛇添足(上面解密的代码把输出类型转化为bytes后再与原始数据比较)
为了更好地进行对比,引入了Crypto(PyCryptodome)库的流密码算法ARC4(好像是RC4算法的非官方实现),可见ARC4连续加密长消息时性能是很强劲的(国外成熟密码算法库会调用编译好的C语言动态链接库),但ZUC的复杂度和安全性高于RC4。如果运行测试代码时Crypto库的部分报类似“ARC4_stream_init' not found in library”的错误,可以尝试一下老版本Crypto库,我用的3.8版本是没问题的,在cmd命令行中输入下面两行即可换版本:
pip uninstall pycryptodome
pip install pycryptodome==3.8.0
网络安全,人人有责!