LXC与Docker介绍
文章目录
- LXC
-
- LUX是什么
- LXC常用命令
- LXC的使用
- Docker
-
- 容器虚拟化和传统虚拟化的区别
- Linux Namespaces
- CGroups
- doeker基本概念
- docker容器编排
LXC
LUX是什么
LXC(LinuX Containers)Linux容器,一种操作系统层虚拟化技术,为Linux内核容器功能的一个用户空间接口。它将应用软件系统打包成一个软件容器(Container),内含应用软件本身的代码,以及所需要的操作系统核心和库。透过统一的名字空间和共享API来分配不同软件容器的可用硬件资源,创造出应用程序的独立沙箱运行环境,使得Linux用户可以容易的创建和管理系统或应用容器。
在Linux内核中,提供了cgroups功能,来达成资源的隔离。它同时也提供了名称空间隔离的功能,使应用程序看到的操作系统环境被区隔成独立区间,包括进程树,网络,用户id,以及挂载的文件系统。但是cgroups并不一定需要启动任何虚拟机。
LXC利用cgroups与名称空间的功能,提供应用软件一个独立的操作系统环境。LXC不需要Hypervisor这个软件层,软件容器(Container)本身极为轻量化,提升了创建虚拟机的速度。
LXC关键技术点:
- chroot,根切换,从容器内的角度来看,仿佛真的有自己的根树
- namespaces:名称空间,负责将资源隔离,比如pid,网络,mnt,user,uts等
- CGroups:控制组,负责控制资源的分配
LXC常用命令
- lxc-checkconfig:检查系统环境是否满足容器使用要求
- lxc-create:创建lxc容器(格式:lxc-create -n NAME -t TEMPLATE_NAME)
- lxc-destory:删除处于停机状态的容器
- lxc-start:启动容器(格式:lxc-start -n NAME -d)
- lxc-stop:停止容器
- lxc-info:查看容器相关的信息(格式:lxc-info -n NAME)
- lxc-console:附加至指定容器的控制台(格式:lxc-console -n NAME -t NUMBER)
- lxc-snapshot:创建和恢复快照
- 退出容器方式:
LXC的使用
- 安装部署LXC
//安装epel源
[root@192 ~]# yum -y install epel-release
//安装依赖包
[root@192 ~]# yum -y install lxc lxc-templates bridge-utils lxc-libs libcgroup libvirt perl debootstrap
//启动服务
[root@192 ~]# systemctl start lxc libvirtd
[root@192 ~]# ss -antl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:111 0.0.0.0:*
LISTEN 0 32 192.168.122.1:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 [::]:111 [::]:*
LISTEN 0 128 [::]:22 [::]:*
//检查系统是否满足容器使用要求
[root@192 ~]# lxc-checkconfig
Kernel configuration not found at /proc/config.gz; searching...
Kernel configuration found at /boot/config-3.10.0-862.el7.x86_64
--- Namespaces ---
Namespaces: enabled
Utsname namespace: enabled
Ipc namespace: enabled
Pid namespace: enabled
User namespace: enabled
newuidmap is not installed
newgidmap is not installed
Network namespace: enabled
Multiple /dev/pts instances: enabled
--- Control groups ---
Cgroup: enabled
Cgroup clone_children flag: enabled
Cgroup device: enabled
Cgroup sched: enabled
Cgroup cpu account: enabled
Cgroup memory controller: enabled
Cgroup cpuset: enabled
--- Misc ---
Veth pair device: enabled
Macvlan: enabled
Vlan: enabled
Bridges: enabled
Advanced netfilter: enabled
CONFIG_NF_NAT_IPV4: enabled
CONFIG_NF_NAT_IPV6: enabled
CONFIG_IP_NF_TARGET_MASQUERADE: enabled
CONFIG_IP6_NF_TARGET_MASQUERADE: enabled
CONFIG_NETFILTER_XT_TARGET_CHECKSUM: enabled
--- Checkpoint/Restore ---
checkpoint restore: enabled
CONFIG_FHANDLE: enabled
CONFIG_EVENTFD: enabled
CONFIG_EPOLL: enabled
CONFIG_UNIX_DIAG: enabled
CONFIG_INET_DIAG: enabled
CONFIG_PACKET_DIAG: enabled
CONFIG_NETLINK_DIAG: enabled
File capabilities: enabled
Note : Before booting a new kernel, you can check its configuration
usage : CONFIG=/path/to/config /usr/bin/lxc-checkconfig
//查看模板
[root@192 ~]# ls /usr/share/lxc/templates/
lxc-alpine lxc-centos lxc-fedora lxc-oracle lxc-ubuntu-cloud
lxc-altlinux lxc-cirros lxc-gentoo lxc-plamo
lxc-archlinux lxc-debian lxc-openmandriva lxc-sshd
lxc-busybox lxc-download lxc-opensuse lxc-ubuntu
- 创建容器
//创建容器lxc-create:
格式:lxc-create -n NAME -t TEMPLATE_NAME
[root@192 ~]# lxc-create -t centos -n watest1
Copy /var/cache/lxc/centos/x86_64/7/rootfs to /var/lib/lxc/watest1/rootfs ...
Copying rootfs to /var/lib/lxc/watest1/rootfs ...
sed: can't read /var/lib/lxc/watest1/rootfs/etc/init/tty.conf: No such file or directory
Storing root password in '/var/lib/lxc/watest1/tmp_root_pass'
chpasswd: cannot open /etc/passwd
Expiring password for user root.
passwd: Libuser error at line: 425 - Error replacing `/etc/passwd': Permission denied.
passwd: Error
sed: can't read /var/lib/lxc/watest1/rootfs/etc/rc.sysinit: No such file or directory
sed: can't read /var/lib/lxc/watest1/rootfs/etc/rc.d/rc.sysinit: No such file or directory
Container rootfs and config have been created.
Edit the config file to check/enable networking setup.
The temporary root password is stored in:
'/var/lib/lxc/watest1/tmp_root_pass'
The root password is set up as expired and will require it to be changed
at first login, which you should do as soon as possible. If you lose the
root password or wish to change it without starting the container, you
can change it from the host by running the following command (which will
also reset the expired flag):
chroot /var/lib/lxc/watest1/rootfs passwd //修改初始化密码
//新创建的容器密码比较复杂,可以根据自己的需求修改密码
//查看原始密码
[root@192 watest1]# pwd
/var/lib/lxc/watest1
[root@192 watest1]# cat tmp_root_pass
Root-watest1-fVSj3E
//使用命令chroot /var/lib/lxc/watest1/rootfs passwd
更改用户 root 的密码 。
新的 密码:
重新输入新的 密码:
passwd:所有的身份验证令牌已经成功更新
- 启动容器
//启动容器lxc-start
格式:lxc-start -n NAME -d 在启动时添加-d选项可以把主机防止后台有运行
[root@localhost ~]# lxc-start -n watest1 -d
systemd 219 running in system mode. (+PAM +AUDIT +SELINUX +IMA -APPARMOR +SMACK +SYSVINIT +UTMP +LIBCRYPTSETUP +GCRYPT +GNUTLS +ACL +XZ +LZ4 -SECCOMP +BLKID +ELFUTILS +KMOD +IDN)
Detected virtualization lxc.
Detected architecture x86-64.
Welcome to CentOS Linux 7 (Core)!
Running in a container, ignoring fstab device entry for /dev/root.
Cannot add dependency job for unit display-manager.service, ignoring: Unit not found.
[ OK ] Started Dispatch Password Requests to Console Directory Watch.
[ OK ] Reached target Local Encrypted Volumes.
[ OK ] Reached target Swap.
[ OK ] Created slice Root Slice.
[ OK ] Created slice User and Session Slice.
[ OK ] Listening on /dev/initctl Compatibility Named Pipe.
[ OK ] Listening on Journal Socket.
[ OK ] Started Forward Password Requests to Wall Directory Watch.
[ OK ] Reached target Paths.
[ OK ] Created slice System Slice.
Mounting POSIX Message Queue File System...
[ OK ] Created slice system-getty.slice.
Mounting Huge Pages File System...
Starting Journal Service...
Starting Read and set NIS domainname from /etc/sysconfig/network...
[ OK ] Reached target Slices.
Starting Remount Root and Kernel File Systems...
[ OK ] Reached target Remote File Systems.
[ OK ] Listening on Delayed Shutdown Socket.
[ OK ] Mounted POSIX Message Queue File System.
[ OK ] Mounted Huge Pages File System.
[ OK ] Started Journal Service.
[ OK ] Started Read and set NIS domainname from /etc/sysconfig/network.
[ OK ] Started Remount Root and Kernel File Systems.
Starting Configure read-only root support...
Starting Flush Journal to Persistent Storage...
Starting Rebuild Hardware Database...
[ OK ] Reached target Local File Systems (Pre).
<46>systemd-journald[16]: Received request to flush runtime journal from PID 1
[ OK ] Started Flush Journal to Persistent Storage.
[ OK ] Started Configure read-only root support.
[ OK ] Reached target Local File Systems.
Starting Rebuild Journal Catalog...
Starting Mark the need to relabel after reboot...
Starting Create Volatile Files and Directories...
Starting Load/Save Random Seed...
[ OK ] Started Mark the need to relabel after reboot.
[ OK ] Started Load/Save Random Seed.
[ OK ] Started Rebuild Journal Catalog.
[ OK ] Started Create Volatile Files and Directories.
Starting Update UTMP about System Boot/Shutdown...
[ OK ] Started Update UTMP about System Boot/Shutdown.
[ OK ] Started Rebuild Hardware Database.
Starting Update is Completed...
[ OK ] Started Update is Completed.
[ OK ] Reached target System Initialization.
[ OK ] Started Daily Cleanup of Temporary Directories.
[ OK ] Reached target Timers.
[ OK ] Listening on D-Bus System Message Bus Socket.
[ OK ] Reached target Sockets.
[ OK ] Reached target Basic System.
[ OK ] Started D-Bus System Message Bus.
Starting OpenSSH Server Key Generation...
Starting Permit User Sessions...
Starting LSB: Bring up/down networking...
Starting Login Service...
Starting Cleanup of Temporary Directories...
[ OK ] Started Permit User Sessions.
[ OK ] Started Console Getty.
[ OK ] Reached target Login Prompts.
[ OK ] Started Command Scheduler.
[ OK ] Started Cleanup of Temporary Directories.
[ OK ] Started Login Service.
[ OK ] Started OpenSSH Server Key Generation.
CentOS Linux 7 (Core)
Kernel 3.10.0-862.el7.x86_64 on an x86_64
mytest1 login: root #使用root用户登陆
Password: #输入设置的root密码
<28>systemd-sysctl[296]: Failed to write '1' to '/proc/sys/fs/protected_symlinks': Read-only file system
- 查看容器运行状态
//查看运行状态语法: lxc-info
格式:lxc-info -n NAME
[root@192 ~]# lxc-info -n watest1
Name: watest1 //主机名
State: RUNNING //当前状态,RUNNING表示启动,STOPPED表示关闭。
PID: 4257 //lxc主机当前在物理机上的进程号
IP: 192.168.218.145 //主机的IP地址
CPU use: 0.09 seconds //cpu占用时间
BlkIO use: 17.44 MiB //占用BLKIO资源的大小
Memory use: 9.14 MiB //占用物理内存大小
KMem use: 0 bytes //内核虚拟内存
Link: vethHPG9WI
TX bytes: 1.23 KiB //流量相关的信息
RX bytes: 2.68 KiB
Total bytes: 4.11 KiB
- 停止lxc容器
停止容器语法:lxc-stop
[root@192~]# lxc-stop -n watest1
- 删除容器
//删除容器语法:lxc-destory
[root@192 ~]# lxc-destroy -n watest1
Docker
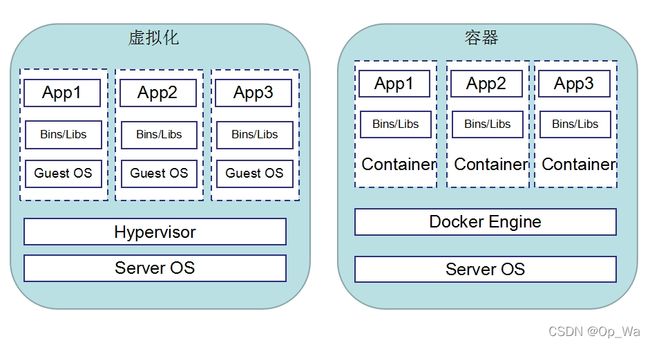
容器虚拟化和传统虚拟化的区别
传统虚拟化:通过虚拟化技术模拟真实的硬件从而创建出来的一台拥有完整功能的逻辑计算机。
容器虚拟化:Docker容器也是一种虚拟化技术,和传统虚拟化不一样的是Docker只模拟一个程序最核心的运行环境,所以十分小巧,启动更快。
虚拟化分为以下两类:
- 主机级虚拟化
- 全虚拟化
- 半虚拟化
- 容器级虚拟化
容器分离开的资源:
- UTS(主机名与域名)
- Mount(文件系统挂载树)
- IPC
- PID进程树
- User
- Network(tcp/ip协议栈)
Linux Namespaces
命名空间(Namespaces)是Linux内核针对实现容器虚拟化而引入的一个强大特性。
每个容器都可以拥有自己独立的命名空间,运行其中的应用都像是在独立的操作系统中运行一样。命名空间保证了容器间彼此互不影响。
| namespaces | 系统调用参数 | 隔离内容 | 内核版本 |
|---|---|---|---|
| UTS | CLONE_NEWUTS | 主机名和域名 | 2.6.19 |
| IPC | CLONE_NEWIPC | 信号量、消息队列和共享内存 | 2.6.19 |
| PID | CLONE_NEWPID | 进程编号 | 2.6.24 |
| Network | CLONE_NEWNET | 网络设备、网络栈、端口等 | 2.6.29 |
| Mount | CLONE_NEWNS | 挂载点(文件系统) | 2.4.19 |
| User | CLONE_NEWUSER | 用户和用户组 | 3.8 |
CGroups
控制组(CGroups)是Linux内核的一个特性,用来对共享资源进行隔离、限制、审计等。只有能控制分配到容器的资源,Docker才能避免多个容器同时运行时的系统资源竞争。
控制组可以提供对容器的内存、CPU、磁盘IO等资源进行限制。
CGroups能够限制的资源有:
- blkio:块设备IO
- cpu:CPU
- cpuacct:CPU资源使用报告
- cpuset:多处理器平台上的CPU集合
- devices:设备访问
- freezer:挂起或恢复任务
- memory:内存用量及报告
- perf_event:对cgroup中的任务进行统一性能测试
- net_cls:cgroup中的任务创建的数据报文的类别标识符
具体来看,控制组提供如下功能:
- 资源限制(Resource Limitting)组可以设置为不超过设定的内存限制。比如:内存子系统可以为进行组设定一个内存使用上限,一旦进程组使用的内存达到限额再申请内存,就会发出Out of Memory警告
- 优先级(Prioritization)通过优先级让一些组优先得到更多的CPU等资源
- 资源审计(Accounting)用来统计系统实际上把多少资源用到合适的目的上,可以使用cpuacct子系统记录某个进程组使用的CPU时间
- 隔离(Isolation)为组隔离命名空间,这样一个组不会看到另一个组的进程、网络连接和文件系统
- 控制(Control)挂起、恢复和重启等操作
安装Docker后,用户可以在/sys/fs/cgroup/memory/docker/目录下看到对Docker组应用的各种限制项,包括
[root@localhost ~]# cd /sys/fs/cgroup/memory/
[root@localhost memory]# ls
cgroup.clone_children memory.kmem.slabinfo memory.memsw.limit_in_bytes memory.swappiness
cgroup.event_control memory.kmem.tcp.failcnt memory.memsw.max_usage_in_bytes memory.usage_in_bytes
cgroup.procs memory.kmem.tcp.limit_in_bytes memory.memsw.usage_in_bytes memory.use_hierarchy
cgroup.sane_behavior memory.kmem.tcp.max_usage_in_bytes memory.move_charge_at_immigrate notify_on_release
memory.failcnt memory.kmem.tcp.usage_in_bytes memory.numa_stat release_agent
memory.force_empty memory.kmem.usage_in_bytes memory.oom_control system.slice
memory.kmem.failcnt memory.limit_in_bytes memory.pressure_level tasks
memory.kmem.limit_in_bytes memory.max_usage_in_bytes memory.soft_limit_in_bytes user.slice
memory.kmem.max_usage_in_bytes memory.memsw.failcnt memory.stat
用户可以通过修改这些文件值来控制组限制Docker应用资源。
doeker基本概念
- docker是容器技术的一个前端工具,容器是内核的一项技术,docker只是把这一项技术的使用得以简化,使之普及而已
- docker早期的版本其核心就是一个LXC,docker对其进行了二次封装,功能的实现是通过LXC做容器管理引擎,但是在创建容器时,不再是像LXC一样用模板去现场安装,而是事先通过一种类似镜像技术,就像在KVM中一样,将一个操作系统打包成一个镜像,然后将这个镜像拷贝到目标主机上直接部署启动
- 尝试着把一个操作系统用户空间需要用到的所有组件,事先准备、编排好,编排好以后整体打包成一个文件,这个文件我们称其为镜像文件(image)
- docker底层依赖的核心技术主要包括Linux操作系统的命名空间、控制组、联合文件系统和Linux虚拟网络支持
- docker的镜像文件是放在一个集中统一的互联网仓库中的,把一些人们常用的镜像文件放在互联网仓库中,当人们想启动一个容器的时候,docker会到这个互联网仓库中去下载我们需要的镜像到本地,并基于镜像来启动容器。
- 自docker 0.9版本起,docker除了继续支持LXC外,还开始引入自家的libcontainer,试图打造更通用的底层容器虚拟化库。如今的docker基本上都已经是使用libcontainer而非LXC了。
docker工作方式:
为了使容器的使用更加易于管理,docker采取一个用户空间只跑一个业务进程的方式,在一个容器内只运行一个进程,比如我们要在一台主机上安装一个nginx和一个tomcat,那么nginx就运行在nginx的容器中,tomcat运行在tomcat的容器中,二者用容器间的通信逻辑来进行通信。
使用docker的优劣:
- 删除一个容器不会影响其他容器
- 分发容易,真正意义上一次编写到处运行,比java的跨平台更彻底
- 部署容易,无论底层系统是什么,只要有docker,直接run就可以了
- 分层构建,联合挂载
- 调试不便,占空间(每个容器中都必须自带调试工具,比如ps命令)
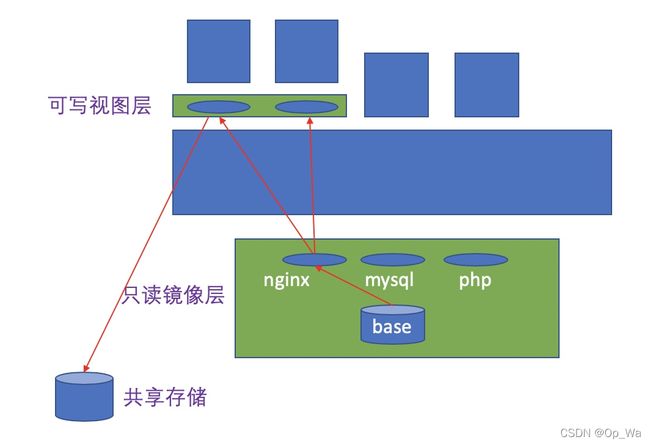
在容器中有数据称作有状态,没有数据称作无状态。在容器的使用中,我们应以有状态为耻,以无状态为荣。数据不应该放在容器中,而应放置于外部存储中,通过挂载到容器中从而进行数据的存储。
docker容器编排
当我们要去构建一个lnmp架构的时候,它们之间会有依赖关系,哪个应用应该在什么时候启动,在谁之前或之后启动,这种依赖关系我们应该要事先定义好,最好是按照一定的次序实现,而docker自身没有这个功能,所以我们需要一个在docker的基础上,能够把这种应用程序之间的依赖关系、从属关系、隶属关系等等反映在启动、关闭时的次序和管理逻辑中,这种功能被称为容器编排。
有了docker以后,运维的发布工作必须通过编排工具来实现容器的编排,如果没有编排工具,运维人员想去管理容器其实比直接管理程序要更加麻烦,增加了运维环境管理的复杂度。
常见的容器编排工具:
- machine+swarm(把N个docker主机当一个主机来管理)+compose(单机编排)
- mesos(实现统一资源调度和分配)+marathon
- kubernetes --> k8s