一、测试环境
1.1 环境准备
lb02服务器(内网:10.0.0.6,外网:172.16.1.6)
web01服务器(内网:10.0.0.7,外网:172.16.1.7)
wen02服务器(内网:10.0.0.8,外网:172.16.1.8)
1.2 配置环境
1>每台服务器配置nginx的yum源
[root@web ~]# vim /etc/yum.repos.d/nginx.repo
[nginx]
name=nginx repo
baseurl=http://nginx.org/packages/centos/7/$basearch/
gpgcheck=0 \\检查模块
enabled=1 \\开启模块
2>每台服务器安装nginx
yum install -y nginx
3>启动nginx服务,并设置开机自启动
启动nginx服务:systemctl start nginx
设置开机自启动:systemctl enable nginx
二、nginx负载均衡的配置
2.1 在web01和web02都配置 www.oldboy.com和 blog.oldboy.com域名
[root@web01 /etc/nginx/conf.d]# vim 01-www.conf
server {
listen 80;
server_name www.oldboy.com;
access_log /var/log/nginx/access_www.log main ;
root /app/www;
location / {
index index.html index.htm;
}
}
[root@web01 /etc/nginx/conf.d]# vim 02-blog.conf
server {
listen 80;
server_name blog.oldboy.com;
access_log /var/log/nginx/access_blog.log main;
root /app/blog;
location / {
index index.php index.html index.htm;
}
}
检查语法,并都平滑重启服务
[root@web01 /etc/nginx/conf.d]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@web01 /etc/nginx/conf.d]# systemctl reload nginx
2.2 在web01和web02创建新的站点目录和index.html文件
[root@web01 ~]# mkdir -p /app/{www,blog}
[root@web01 ~]# for n in www blog ; do echo `hostname` $n.oldboy.com >/app/$n/index.html ;done
[root@web01 ~]# tree /app/
/app/
├── blog
│ └── index.html
└── www
└── index.html
2 directories, 2 files
[root@web01 ~]#
2.3 检查web01和web02的配置是否正常
[root@web01 ~]# curl -H Host:www.oldboy.com 10.0.0.[7-8]
[1/2]: 10.0.0.7 -->
--_curl_--10.0.0.7
web01 www.oldboy.com
[2/2]: 10.0.0.8 -->
--_curl_--10.0.0.8
web02 www.oldboy.com
[root@web01 ~]# curl -H Host:blog.oldboy.com 10.0.0.[7-8]
[1/2]: 10.0.0.7 -->
--_curl_--10.0.0.7
web01 blog.oldboy.com
[2/2]: 10.0.0.8 -->
--_curl_--10.0.0.8
web02 blog.oldboy.com
2.4 在lb02进行反向代理配置
ngx_http_upstream_module----负载均衡
ngx_http_proxy_module-----反向代理 image
image
1>在nginx服务进行以下配置
[root@lb02 /etc/nginx]# cat nginx.conf
……
# include /etc/nginx/conf.d/*.conf;
upstream web_pools{
server 10.0.0.7:80;
server 10.0.0.8:80;
}
server{
listen 80;
server_name www.oldboy.com;
location / {
proxy_pass http://web_pools;
}
}
server{
listen 80;
server_name blog.oldboy.com;
location / {
proxy_pass http://web_pools;
}
}
2>检查语法,平滑重启服务
[root@lb02 /etc/nginx]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@lb02 /etc/nginx]# systemctl reload nginx
3>在命令行用curl进行测试
[root@lb02 /etc/nginx]# curl 10.0.0.6
web02 www.oldboy.com
[root@lb02 /etc/nginx]# curl 10.0.0.6
web01 www.oldboy.com
4>抓包测试
首先在Windows本地hosts文件中配置解析
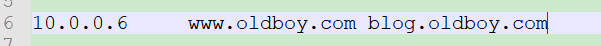 image
image抓包
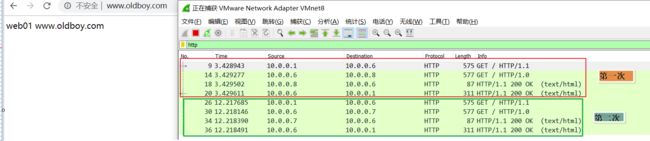 image
image
三、负载均衡相关配置详解
3.1 upstream模块内部server标签参数说明
server :ip或域名,如果端口不写,默认时80端口
weight:权重
max_fails :失败次数
fail_timeout :多久后在检查一遍
backup :如果加上backup 会在池塘中其他机器都挂掉 才会启动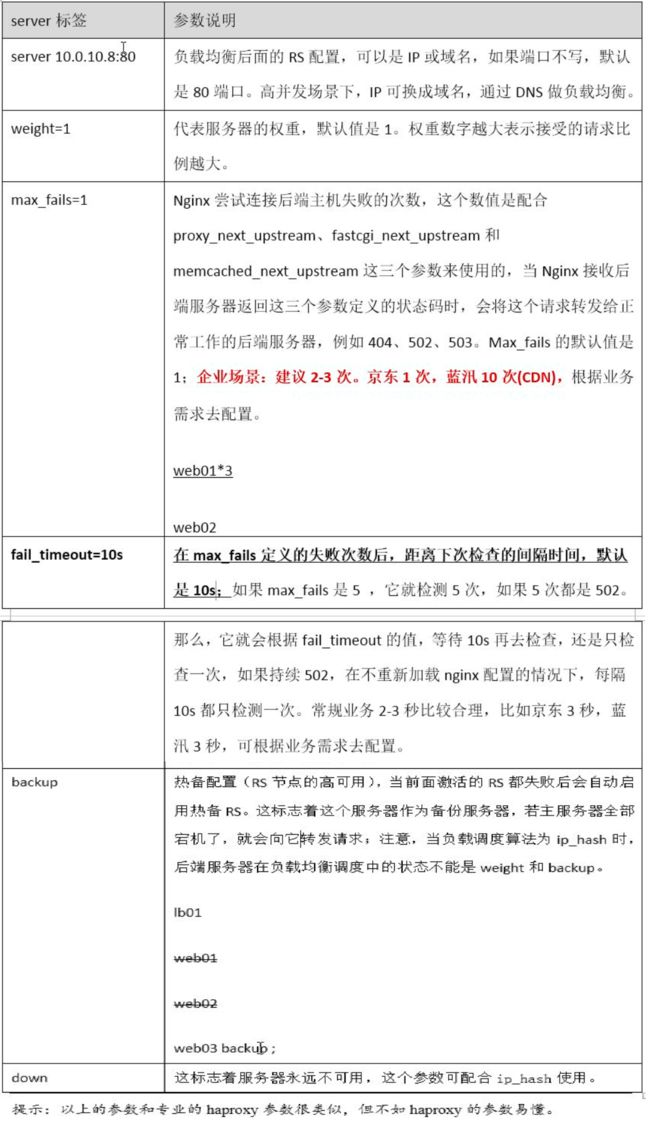 image
image
1>weight权重测试
[root@lb02 /etc/nginx]# cat nginx.conf
……
upstream web_pools{
server 10.0.0.7:80 weight=2;
server 10.0.0.8:80 weight=1;
}
……
[root@lb02 /etc/nginx]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@lb02 /etc/nginx]# systemctl reload nginx
[root@lb02 /etc/nginx]# curl 10.0.0.6
web01 www.oldboy.com
[root@lb02 /etc/nginx]# curl 10.0.0.6
web01 www.oldboy.com
[root@lb02 /etc/nginx]# curl 10.0.0.6
web02 www.oldboy.com
2>fail_timeout(多久后在检查一遍)测试
[root@lb02 /etc/nginx]# cat nginx.conf
……
upstream web_pools{
server 10.0.0.7:80 weight=1 max_fails=1 fail_timeout=4s;
server 10.0.0.8:80 weight=1 max_fails=1 fail_timeout=4s;
}
……
[root@lb02 /etc/nginx]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@lb02 /etc/nginx]# systemctl reload nginx
for n in {1..1000};do curl 10.0.0.5/index.html ;sleep 1;done
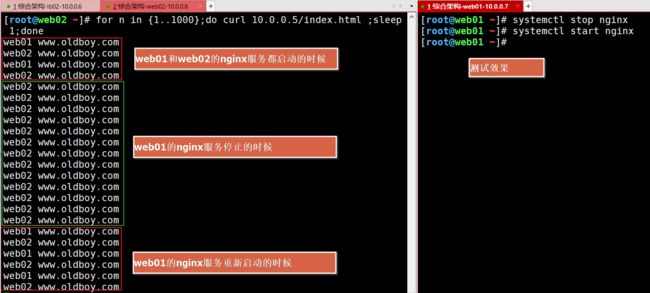 image
image
3.2 用域名访问
3.3 多个域名访问/虚拟主机
多个虚拟主机的通过负载均衡
如:请求访问blog.oldboy.com,但一直显示www的内容
原因:
负载均衡向web服务器发出请求的时候,请求Host 域名时池塘名字(web_pools),web_pools IP地址,所以默认匹配第1个虚拟主机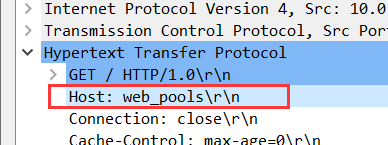 image
image
解决:
用proxy_set_header修改请求头的内容,如:proxy_set_header Host $host;
[root@lb02 /etc/nginx]# cat nginx.conf
……
upstream web_pools{
server 10.0.0.7:80 weight=1 max_fails=1 fail_timeout=4s;
server 10.0.0.8:80 weight=1 max_fails=1 fail_timeout=4s;
}
server{
listen 80;
server_name www.oldboy.com;
location / {
proxy_pass http://web_pools;
proxy_set_header Host $host;
}
}
server{
listen 80;
server_name blog.oldboy.com;
location / {
proxy_pass http://web_pools;
proxy_set_header Host $host;
}
}
[root@lb02 /etc/nginx]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@lb02 /etc/nginx]# systemctl reload nginx
[root@lb02 /etc/nginx]#
3.4 web服务器上面访问日志 记录用户IP
proxy_set_header X-Forwarded-For $remote_addr;
[root@lb02 /etc/nginx]# cat nginx.conf
……
server{
listen 80;
server_name www.oldboy.com;
location / {
proxy_pass http://web_pools;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
server{
listen 80;
server_name blog.oldboy.com;
location / {
proxy_pass http://web_pools;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
……
[root@lb02 /etc/nginx]#
[root@lb02 /etc/nginx]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@lb02 /etc/nginx]# systemctl reload nginx
四、添加访问控制
如果某些网段访问量成千上万,特别高的话,可能是被入侵了
需要给这个网址做限制访问
server {
listen 80;
server_name www.oldboy.com;
location / {
if ($remote_addr ~ "^192.168.22.") { \\指定禁止访问的网段
return 403 "biedaoluan"; \\定义的是指定网段中,客户访问后返回的内容
}
proxy_pass http://web_pools;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $remote_addr;
}
五、iptables命令的详解
详细介绍:http://man.linuxde.net/iptables
iptables命令是Linux上常用的防火墙软件,是netfilter项目的一部分。可以直接配置,也可以通过许多前端和图形界面配置。
语法:iptables(选项)(参数)
如:iptables -A INPUT -p tcp -s 192.168.22.0/24 -j DROP
-A:向规则链中添加条目;
-P:定义规则链中的默认目标;
-s:指定要匹配的数据包源
-j<目标>:指定要跳转的目标;
INPUT链:处理输入数据包。
DROP:丢弃数据包
5.1 清除已有iptables规则
iptables -F
iptables -X
iptables -Z
5.2 开放指定的端口
iptables -A INPUT -s 127.0.0.1 -d 127.0.0.1 -j ACCEPT #允许本地回环接口(即运行本机访问本机)
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT #允许已建立的或相关连的通行
iptables -A OUTPUT -j ACCEPT #允许所有本机向外的访问
iptables -A INPUT -p tcp --dport 22 -j ACCEPT #允许访问22端口
iptables -A INPUT -p tcp --dport 80 -j ACCEPT #允许访问80端口
iptables -A INPUT -p tcp --dport 21 -j ACCEPT #允许ftp服务的21端口
iptables -A INPUT -p tcp --dport 20 -j ACCEPT #允许FTP服务的20端口
iptables -A INPUT -j reject #禁止其他未允许的规则访问
iptables -A FORWARD -j REJECT #禁止其他未允许的规则访问
5.3 屏蔽IP
iptables -I INPUT -s 123.45.6.7 -j DROP #屏蔽单个IP的命令
iptables -I INPUT -s 123.0.0.0/8 -j DROP #封整个段即从123.0.0.1到123.255.255.254的命令
iptables -I INPUT -s 124.45.0.0/16 -j DROP #封IP段即从123.45.0.1到123.45.255.254的命令
iptables -I INPUT -s 123.45.6.0/24 -j DROP #封IP段即从123.45.6.1到123.45.6.254的命令是
5.4 查看已添加的iptables规则
iptables -L -n -v
Chain INPUT (policy DROP 48106 packets, 2690K bytes)
pkts bytes target prot opt in out source destination
5075 589K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
191K 90M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
1499K 133M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4364K 6351M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
6256 327K ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3382K packets, 1819M bytes)
pkts bytes target prot opt in out source destination
5075 589K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0