Docker-配置私有仓库
Docker简介
Docker 仓库是用来包含镜像的位置,Docker提供一个注册服务器
(Register)来保存多个仓库,每个仓库又可以包含多个具备不同tag
的镜像。
Docker运行中使用的默认仓库是 Docker Hub 公共仓库。
2. Registry 工作原理
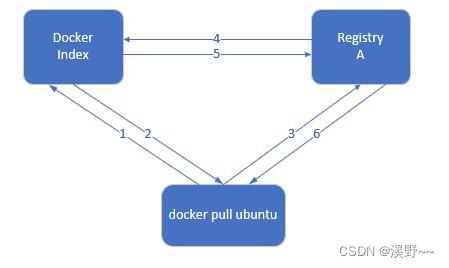
2.1 一次docker pull 或 push背后发生的事情
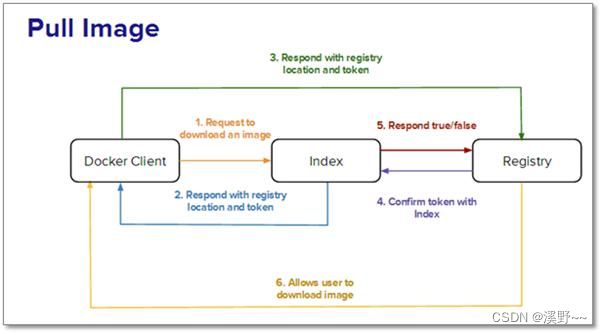
index服务主要提供镜像索引以及用户认证的功能。当下载一个镜像的时候,首先
会去index服务上做认证,然后查找镜像所在的registry的地址并放回给docker客户
端,docker客户端再从registry下载镜像,在下载过程中 registry会去index校验客
户端token的合法性,不同镜像可以保存在不同的registry服务上,其索引信息都放
在index服务上。
2. 2 Docker Registry有三个角色,分别是index、registry和registry client。
index
• 负责并维护有关用户帐户、镜像的校验以及公共命名空间的信息。
• Web UI
• 元数据存储
• 认证服务
• 符号化
registry
• 是镜像和图表的仓库,它不具有本地数据库以及不提供用户认证,通过
Index Auth service的Token的方式进行认证。
• Registry Client
• Docker充当registry客户端来维护推送和拉取,以及客户端的授权。
Registry Client
• Docker充当registry客户端来维护推送和拉取,以及客户端的授权。
2.3 情景A:用户要获取并下载镜像。
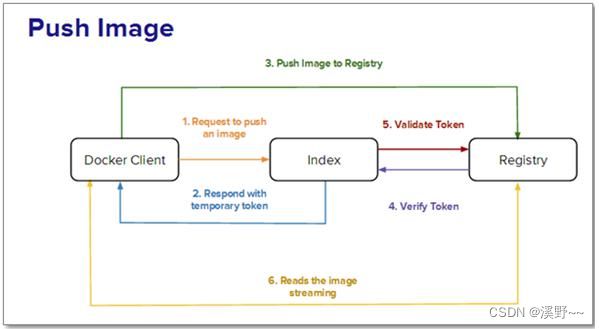
2.4 情景B:用户要推送镜像到registry中。
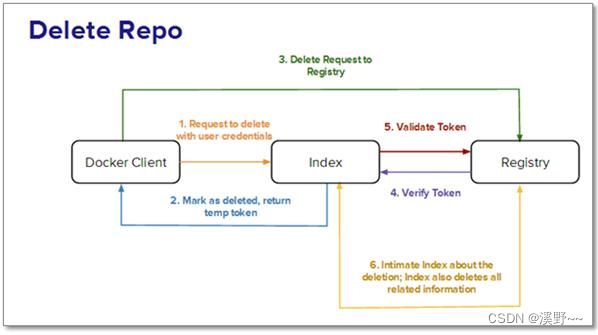
2.5 情景C:用户要从index或registry中删除镜像。
3 . 配置镜像加速器
从docker hub上下载镜像的速度太慢,需要配置镜像加速器,这里以阿里云为例:(需要提前注册阿里云帐号)
3.1 配置docker daemon文件
[root@lnmp0 ~]# cd /etc/docker/
[root@lnmp0 docker]# vim daemon.json
{
"registry-mirrors": ["https://vo5twm71.mirror.aliyuncs.com"]
}
3.2 重载docker服务
[root@lnmp0 ~]# systemctl daemon-reload
[root@lnmp0 ~]# systemctl restart docker.service4. 搭建私有仓库
docker hub虽然方便,但是还是有限制
• 需要internet连接,速度慢
• 所有人都可以访问
• 由于安全原因企业不允许将镜像放到外网
好消息是docker公司已经将registry开源,我们可以快速构建企业私有仓库
官网地址:Deploy a registry server | Docker DocumentationExplains how to deploy a registry![]() https://docs.docker.com/registry/deploying/4.1 下载registry镜像
https://docs.docker.com/registry/deploying/4.1 下载registry镜像
[root@lnmp0 ~]# docker pull registry
Using default tag: latest
latest: Pulling from library/registry
2408cc74d12b: Pull complete
ea60b727a1ce: Pull complete
c87369050336: Pull complete
e69d20d3dd20: Pull complete
fc30d7061437: Pull complete
Digest: sha256:bedef0f1d248508fe0a16d2cacea1d2e68e899b2220e2258f1b604e1f327d475
Status: Downloaded newer image for registry:latest
docker.io/library/registry:latest
4.2 运行registry容器
[root@lnmp0 ~]# docker run -d --name registry -p 5000:5000 registry
176a6d135ca800390cc61c3c114934259ae64d204f3de3e781e343a61db5a316
[root@lnmp0 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
176a6d135ca8 registry "/entrypoint.sh /etc…" 12 seconds ago Up 11 seconds 0.0.0.0:5000->5000/tcp, :::5000->5000/tcp registry
4.3 上传镜像到本地仓库
本地镜像在命名时需要加上仓库的ip和端口
[root@lnmp0 ~]# docker tag nginx:latest localhost:5000/nginx:latest
[root@lnmp0 ~]# docker push localhost:5000/nginx
Using default tag: latest
The push refers to repository [localhost:5000/nginx]
33e3df466e11: Pushed
747b7a567071: Pushed
57d3fc88cb3f: Pushed
53ae81198b64: Pushed
58354abe5f0e: Pushed
ad6562704f37: Pushed
latest: digest: sha256:25dedae0aceb6b4fe5837a0acbacc6580453717f126a095aa05a3c6fcea14dd4 size: 1570
[root@lnmp0 ~]# curl localhost:5000/v2/_catalog
{"repositories":["nginx"]}
5 . 为Docker仓库添加证书加密功能
[root@lnmp0 ~]# yum install openssl11-1.1.1k-2.el7.x86_64.rpm openssl11-libs-1.1.1k-2.el7.x86_64.rpm -y
Loaded plugins: langpacks, product-id, search-disabled-repos, subscription-manager
This system is not registered with an entitlement server. You can use subscription-manager to register.
Examining openssl11-1.1.1k-2.el7.x86_64.rpm: 1:openssl11-1.1.1k-2.el7.x86_64
Marking openssl11-1.1.1k-2.el7.x86_64.rpm to be installed
Resolving Dependencies
--> Running transaction check
---> Package openssl11.x86_64 1:1.1.1k-2.el7 will be installed
--> Finished Dependency Resolution
.......[root@lnmp0 ~]# mkdir certs ##存放证书的目录
[root@lnmp0 ~]# openssl11 req -newkey rsa:4096 -nodes -sha256 -keyout certs/westos.org.key -addext "subjectAltName = DNS:reg.westos.org" -x509 -days 365 -out certs/westos.org.crt ##生成证书
Generating a RSA private key
..++++
........................++++
writing new private key to 'certs/westos.org.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Shaanxi
Locality Name (eg, city) [Default City]:Xi'an
Organization Name (eg, company) [Default Company Ltd]:westos
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:reg.westos.org
Email Address []:[email protected]
##这里的Common Name (eg, your name or your server's hostname) []:reg.westos.org,域名一定要和"subjectAltName = DNS:reg.westos.org"的域名一样,否则无法解析
6 . 重建registry容器
6.1 先删除容器和容器创建的卷
[root@lnmp0 docker]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
176a6d135ca8 registry "/entrypoint.sh /etc…" 28 minutes ago Up 28 minutes 0.0.0.0:5000->5000/tcp, :::5000->5000/tcp registry
[root@lnmp0 docker]# docker rm -f 176a6d135ca8
176a6d135ca8
[root@lnmp0 docker]# docker volume prune
WARNING! This will remove all local volumes not used by at least one container.
Are you sure you want to continue? [y/N] y
Deleted Volumes:
766c4987441e379c4890e6e3acd000774e7a388581f50219faeecc068e791401
5216f00b72a6fdeefa98f484ba6c294385b09de715c26f22b3e87c2e931873f0
ad58e70a93475ca724b9316356dc79504502bc3e81b8a16c971399574c9bc056
7db19d4105051add9fd884b488a3b2078f39590668a17c6a42f85fa0d50daf83
c822caf78106b2db18b2b64748ddbe73ce22b52a21b374a5774805a2b5f519c1
6.2 添加解析,重新运行容器
[root@lnmp0 ~]# vim /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.155.100 lnmp0 reg.westos.org
[root@lnmp0 ~]# docker run -d --restart=always --name registry -v /root/certs:/certs -v /opt/registry:/var/lib/registry -v /root/auth:/auth -e "REGISTRY_AUTH=htpasswd" -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd -e REGISTRY_HTTP_ADDR=0.0.0.0:443 -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt -e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key -p 443:443 registry
0dce86653079cd51b40c29b78e74bd5a639007e6b4f668d59509f6cf70ccf20c
[root@lnmp0 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
0dce86653079 registry "/entrypoint.sh /etc…" 20 seconds ago Up 19 seconds 0.0.0.0:443->443/tcp, :::443->443/tcp, 5000/tcp registry
[root@lnmp0 ~]# curl -k https://reg.westos.org/v2/_catalog -u admin:westos
{"repositories":["nginx"]}
6.2.1 重新运行容器的参数详解
docker run -d #后台运行
--restart=always #跟随docker启动
--name registry #容器名称
-v /root/certs:/certs #目录映射关系——宿主机目录:容器内目录
-v /opt/registry:/var/lib/registry #目录映射
-e REGISTRY_HTTP_ADDR=0.0.0.0:443 #允许端口
-e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt #证书名称及域名
-e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key #证书名称及域名
-p 443:443 #端口映射——宿主机端口:容器端口
registry #镜像名称6.3 拷贝证书到docker主机
[root@lnmp0 certs]# mkdir -p /etc/docker/certs.d/reg.westos.org ##建立的目录名字和域名“reg.westos.org”保持一致,docker会自动识别
[root@lnmp0 certs]# cp westos.org.crt /etc/docker/certs.d/reg.westos.org/ca.crt ##拷贝到这个固定目录后,docker会自动识别
6.4 测试上传镜像
[root@lnmp0 certs]# docker tag nginx:latest reg.westos.org/nginx:latest ##更改成私有仓库的标签
[root@lnmp0 certs]# docker push reg.westos.org/nginx:latest ##上传镜像
The push refers to repository [reg.westos.org/nginx]
33e3df466e11: Pushed
747b7a567071: Pushed
57d3fc88cb3f: Pushed
53ae81198b64: Pushed
58354abe5f0e: Pushed
ad6562704f37: Pushed
latest: digest: sha256:25dedae0aceb6b4fe5837a0acbacc6580453717f126a095aa05a3c6fcea14dd4 size: 15707. 为Docker仓库添加用户认证功能
7. 1 下载创建密钥所要用的工具,删除运行的registry容器
[root@lnmp0 ~]# mkdir auth ##创建存储信息的目录
[root@lnmp0 ~]# yum install httpd-tools -y ##下载创建密钥所要用的工具
Loaded plugins: langpacks, product-id, search-disabled-repos, subscription-manager
This system is not registered with an entitlement server. You can use subscription-manager to register.
Resolving Dependencies
--> Running transaction check
---> Package httpd-tools.x86_64 0:2.4.6-88.el7 will be updated
..............
[root@lnmp0 ]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
0300e39e8acb registry "/entrypoint.sh /etc…" 42 minutes ago Up 13 minutes 0.0.0.0:443->443/tcp, :::443->443/tcp, 5000/tcp registry
[root@lnmp0 ]# docker rm -f 0300e39e8acb ##删除运行的registry容器
0300e39e8acb
7.2 创建用户,生成文件
[root@lnmp0 ~]# htpasswd -cB auth/htpasswd admin ##第一次创建admin用户,要用到参数-cB
New password:
Re-type new password:
Adding password for user admin
[root@lnmp0 ~]# htpasswd -B auth/htpasswd westos ##第二次创建用户时不能添加参数-c只用到-B,否则会覆盖第一次所创建的文件
New password:
Re-type new password:
Adding password for user westos
[root@lnmp0 ~]# cat auth/htpasswd ##生成的证书文件
admin:$2y$05$5Eh751dZlXKD/NFggCKlW.1gFaNeOlYaUhleZTXmlMEeHPrqgjkHu
westos:$2y$05$Vb0aCA5RcxEuUWRwPbEt/uJ4.mmBXVzmkr5XxKjWY2uj26ipcoDk6
7.3 重新运行容器registry
[root@lnmp0 ~]# docker run -d --restart=always --name registry -v /root/certs:/certs -v /opt/registry:/var/lib/registry -v /root/auth:/auth -e "REGISTRY_AUTH=htpasswd" -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd -e REGISTRY_HTTP_ADDR=0.0.0.0:443 -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/westos.org.crt -e REGISTRY_HTTP_TLS_KEY=/certs/westos.org.key -p 443:443 registry
0dce86653079cd51b40c29b78e74bd5a639007e6b4f668d59509f6cf70ccf20c
[root@lnmp0 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
0dce86653079 registry "/entrypoint.sh /etc…" 20 seconds ago Up 19 seconds 0.0.0.0:443->443/tcp, :::443->443/tcp, 5000/tcp registry
[root@lnmp0 ~]# curl -k https://reg.westos.org/v2/_catalog -u admin:westos ##查看私有仓库的镜像
{"repositories":["nginx"]} [root@lnmp0 ~]# docker login reg.westos.org ##用之前创建的用户密码登录私有仓库
Username: admin
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[root@lnmp0 ~]# docker yakexi007/busyboxplus reg.westos.org/yakexi007/busyboxplus
[root@lnmp0 ~]# docker push reg.westos.org/yakexi007/busyboxplus ##测试上传镜像至私有仓库
Using default tag: latest
The push refers to repository [reg.westos.org/yakexi007/busyboxplus]
5f70bf18a086: Pushed
774600fa57ae: Pushed
075a34aac01b: Pushed
latest: digest: sha256:9d1c242c1fd588a1b8ec4461d33a9ba08071f0cc5bb2d50d4ca49e430014ab06 size: 1353
[root@lnmp0 ~]# curl -k https://reg.westos.org/v2/_catalog -u admin:westos
{"repositories":["nginx","yakexi007/busyboxplus"]} ##上传成功