Tryhackme-Threat and Vulnerability Management
Threat and Vulnerability Management
文章目录
- Threat and Vulnerability Management
-
- Nessus
-
- task1 Introduction
- task2 Installation
- task3 Navigation and Scans
- task4 Scanning!
- task5 Scanning a Web Application!
- MIRE
-
- Task1 Introduction to MITRE
- Task2 Basic Terminology
- Task3 ATT&CK® Framework
- Task4 CAR Knowledge Base
- Task5 Shield Active Defense
- Task6 ATT&CK® Emulation Plans
- Task7 ATT&CK® and Threat Intelligence
- Task8 Conclusion
- Yara
-
- Task1 Introduction
- Task2 What is Yara?
- Task3 Installing Yara (Ubuntu/Debian & Windows)
- Task4 Deploy
- Task5 Introduction to Yara Rules
- Task6 Expanding on Yara Rules
- Task7 Yara Modules
- Task8 Other tools and Yara
- Task9 Using LOKI and its Yara rule set
- Task10 Creating Yara rules with yarGen
- Task11 Valhalla
- Task12 Conclusion
- OpenVAS
-
- Task1 Introduction
- Task2 GVM Framework Architecture
- Task3 Installing OpenVAS
- Task4 Initial Configuration
- Task5 Scanning Infrastructure
- Task6 Reporting and Continuous Monitoring
- Task7 Practical Vulnerability Management
- Task8 Conclusion
Nessus
task1 Introduction
I have read the description!
task2 Installation
1.Goto https://www.tenable.com/products/nessus/nessus-essentials and register an account.
You will need to do this for an activation code.
2.We will then download the Nessus-#.##.#-debian6_**amd64.**deb file
Save it to your /Downloads/ folder
3.In the terminal we will navigate to that folder and run the following command:
sudo dpkg -i package_file.deb
Remember to replace package_file.deb with the file name you downloaded.
4.We will now start the Nessus Service with the command:
sudo /bin/systemctl start nessusd.service
5.Open up Firefox and goto the following URL:
https://localhost:8834/
You may be prompted with a security risk alert.
Click Advanced… -> Accept the Risk and Continue’’
6.Next, we will set up the scanner.
Select the option Nessus Essentials
Clicking the Skip button will bring us to a page, which we will input that code we got in the email from Nessus.
7.Fill out the Username and Password fields. Make sure to use a strong password!
8.Nessus will now install the plugins required for it to function.
This will take some time, which will depend on your internet connection and the hardware attached to your VM.
If the progress bar appears to be not moving, it means you do not have enough space on the VM to install.
9.Log in with the account credentials you made earlier.
10.You have now successfully installed Nessus!
task3 Navigation and Scans
1.What is the name of the button which is used to launch a scan?
New Scan
2.What side menu option allows us to create custom templates?
Policies
3.What menu allows us to change plugin properties such as hiding them or changing their severity?
Plugin Rules
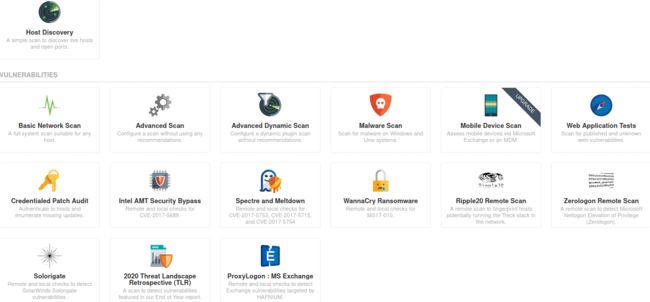
4.In the ‘Scan Templates’ section after clicking on ‘New Scan’, what scan allows us to see simply what hosts are alive?
Host Discovery
5.One of the most useful scan types, which is considered to be ‘suitable for any host’?
Basic Network Scan
6.What scan allows you to ‘Authenticate to hosts and enumerate missing updates’?
Credentialed Patch Audit
7.What scan is specifically used for scanning Web Applications?
Web Application Tests
task4 Scanning!
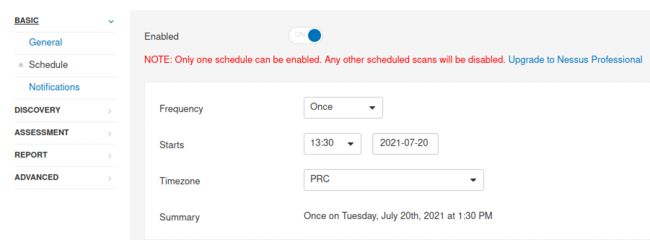
1.Create a new ‘Basic Network Scan’ targeting the deployed VM. What option can we set under ‘BASIC’ (on the left) to set a time for this scan to run? This can be very useful when network congestion is an issue.
Schedule
2.Under ‘DISCOVERY’ (on the left) set the ‘Scan Type’ to cover ports 1-65535. What is this type called?
Port scan(all ports)
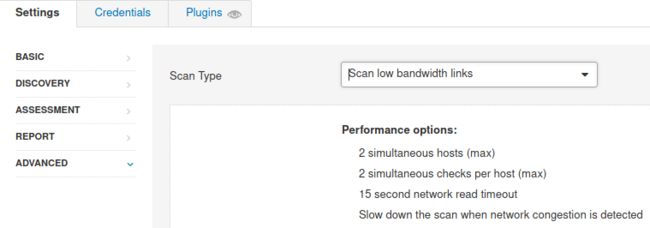
3.What ‘Scan Type’ can we change to under ‘ADVANCED’ for lower bandwidth connection?
Scan low bandwidth links
4.With these options set, launch the scan.
5.After the scan completes, which ‘Vulnerability’ in the ‘Port scanners’ family can we view the details of to see the open ports on this host?
Nessus SYN Scanner
6.What Apache HTTP Server Version is reported by Nessus?
2.4.99
task5 Scanning a Web Application!
1.What is the plugin id of the plugin that determines the HTTP server type and version?
10107
2.What authentication page is discovered by the scanner that transmits credentials in cleartext?
login.php
3.What is the file extension of the config backup?
.bak
4.Which directory contains example documents? (This will be in a php directory)
/external/phpids/0.6/docs/examples/
5.What vulnerability is this application susceptible to that is associated with X-Frame-Options?
Clickjacking
MIRE
Task1 Introduction to MITRE
Read the above
https://www.mitre.org/about/corporate-overview
Task2 Basic Terminology
Read the above
APT(Advanced Persistent Threat)高级可持续威胁攻击
TTP(Tactics, Techniques, and Procedures)战术、技术、程序
Task3 ATT&CK® Framework
Phishing, Technique T1566 - Enterprise | MITRE ATT&CK®
1.Only blue teamers will use the ATT&CK Matrix? (Yay/Nay)
Nay
2.What is the ID for this technique?
T1566
3.Based on this technique, what mitigation covers identifying social engineering techniques?
User Training
4.There are other possible areas for detection for this technique, which occurs after what other technique?
User Execution
5.What group has used spear phishing in their campaigns?
Dragonfly
6.Based on the information for this group, what are their associated groups?
TG-4192,Crouching Yeti,IRON LIBERTY,Energetic Bear
7.What tool is attributed to this group to transfer tools or files from one host to another within a compromised environment?
PsExec
8.Based on the information about this tool, what group used a customized version of it?
FIN5
9.This group has been active since what year?
2008
10.Instead of Mimikatz, what OS Credential Dumping tool is does this group use?
Windows Credential Editor
Task4 CAR Knowledge Base
Analytics | MITRE Cyber Analytics Repository
1.For the above analytic, what is the pseudocode a representation of?
Splunk Search
2.What tactic has an ID of TA0003?
Persistence
3.What is the name of the library that is a collection of Zeek (BRO) scripts?
BZAR
4.What is the name of the technique for running executables with the same hash and different names?
Masquerading
5.Examine CAR-2013-05-004, what additional information is provided to analysts to ensure coverage for this technique?
Unit Tests
Task5 Shield Active Defense
Shield Home (mitre.org)
1.Which Shield tactic has the most techniques?
Detect
2.Is the technique ‘Decoy Credentials’ listed under the tactic from question #1? (Yay/Nay)
Yay
3.Explore DTE0011, what is the ID for the use case where a defender can plant artifacts on a system to make it look like a virtual machine to the adversary?
DUC0234
4.Based on the above use case, what is its ATT&CK® Technique mapping?
T1497
5.Continuing from the previous question, look at the information for this ATT&CK® Technique, what 2 programs are listed that adversary’s will check for?
Sysinternals and Wireshark
Task6 ATT&CK® Emulation Plans
https://mitre-engenuity.org/attackevaluations/
1.How many phases does APT3 Emulation Plan consists of?
3
2.Under Persistence, what binary was replaced with cmd.exe?
sethc.exe
3.Examining APT29, what 2 tools were used to execute the first scenario?
Pupy and Metasploit
4.What tool was used to execute the second scenario?
PoshC2
5.Where can you find step-by-step instructions to execute both scenarios?
ATT&CK Arsenal
Task7 ATT&CK® and Threat Intelligence
1.What is a group that targets your sector who has been in operation since at least 2013?
APT33
2.Does this group use Stuxnet? (Yay/Nay)
Nay
3.As your organization is migrating to the cloud, is there anything attributed to this APT group that you should focus on? If so, what is it?
Cloud Accounts
4.What tool is associated with this technique?
Ruler
5.Per the detection tip, what should you be detecting?
abnormal or malicious behavior
6.What platforms does this affect?
Azure AD, Google Workspace, IaaS, Office 365, SaaS
Task8 Conclusion
Read the above
参考链接:Mitre on Tryhackme - The Dutch Hacker
Yara
Task1 Introduction
Let’s get started
Task2 What is Yara?
1.What is the name of the base-16 numbering system that Yara can detect?
HEX
With such a fitting quote, Yara can identify information based on both binary and textual patterns, such as hexadecimal and strings contained within a file.
2.Would the text “Enter your Name” be a string in an application? (Yay/Nay)
Yay
Task3 Installing Yara (Ubuntu/Debian & Windows)
I’ve installed Yara and/or are using the attached VM!
Releases · VirusTotal/yara (github.com)
Task4 Deploy
Username: cmnatic
Password: yararules!
SSH Port: 22
I’ve either connected to my instance or installed Yara on my own operating system!
Task5 Introduction to Yara Rules
One rule to - well - rule them all.
Task6 Expanding on Yara Rules
Upwards and onwards…
Task7 Yara Modules
Sounds pretty cool!
Task8 Other tools and Yara
Releases · Neo23x0/Loki (github.com)
Cool tools. I’m ready to use one of them.
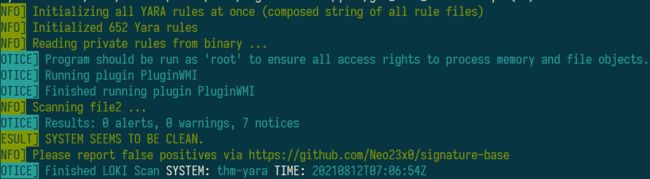
Task9 Using LOKI and its Yara rule set
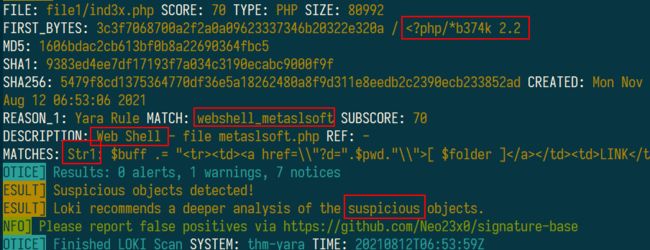
1.Scan file 1. Does Loki detect this file as suspicious/malicious or benign?
使用loki扫描文件夹,python loki.py -p file1/2
Suspicious
2.What Yara rule did it match on?
Webshell_metaslsoft
3.What does Loki classify this file as?
Web Shell
4.Based on the output, what string within the Yara rule did it match on?
Str1
5.What is the name and version of this hack tool?
b374k 2.2
6.Inspect the actual Yara file that flagged file 1. Within this rule, how many strings are there to flag this file?
1
7.Scan file 2. Does Loki detect this file as suspicious/malicious or benign?
benign
8.Inspect file 2. What is the name and version of this web shell?
b374k 3.2.3
Task10 Creating Yara rules with yarGen
Releases · Neo23x0/yarGen (github.com)
strings 1ndex.php | wc -l
1.From within the root of the suspicious files directory, what command would you run to test Yara and your Yara rule against file 2?
yara file2.yar file2/1ndex.php
2.Did Yara rule flag file 2? (Yay/Nay)
Yay
3.Copy the Yara rule you created into the Loki signatures directory
4.Test the Yara rule with Loki, does it flag file 2? (Yay/Nay)
Yay
5.What is the name of the variable for the string that it matched on?
Zepto
6.Inspect the Yara rule, how many strings were generated?
python loki.py /file2
20
7.One of the conditions to match on the Yara rule specifies file size. The file has to be less than what amount?
700kb
Task11 Valhalla
1.Enter the SHA256 hash of file 1 into Valhalla. Is this file attributed to an APT group? (Yay/Nay)
Yay
2.Do the same for file 2. What is the name of the first Yara rule to detect file 2?
webshell_b374k_rule1
3.Examine the information for file 2 from Virus Total (VT). The Yara Signature Match is from what scanner?
THOR APT Scanner
4.Enter the SHA256 hash of file 2 into Virus Total. Did every AV detect this as malicious? (Yay/Nay)
nay
5.Besides .PHP, what other extension is recorded for this file?
exe
6.Back to Valhalla, inspect the Info for this rule. Under Statistics what was the highest rule match per month in the last 2 years? (YYYY/M)
7.What JavaScript library is used by file 2?
zepto
8.Is this Yara rule in the default Yara file Loki uses to detect these type of hack tools? (Yay/Nay)
Nay
Task12 Conclusion
No answer needed
参考链接Yara on Tryhackme - The Dutch Hacker
OpenVAS
Task1 Introduction
Read the introduction
Task2 GVM Framework Architecture
Read about GVM architecture and move on to setting up OpenVAS
Task3 Installing OpenVAS
Read the above and prepare your environment
Task4 Initial Configuration
gvm-start/stop – 启动/关闭OpenVAS
gvm-check-setup --检测初始化是否完成
gvm-feed-update – 升级特征库
runuser -u _gvm – gvmd --user=admin --new-password=password – 修改密码
runuser -u _gvm – gvmd --create-user=admin --new-password=password – 添加新用户
默认账密admin/admin
Read the above and complete your first scan!
Task5 Scanning Infrastructure
Read the above and complete your scan on DVWA to test scanning remote infrastructure.
Task6 Reporting and Continuous Monitoring
Read the above and practice reporting and monitoring
Task7 Practical Vulnerability Management
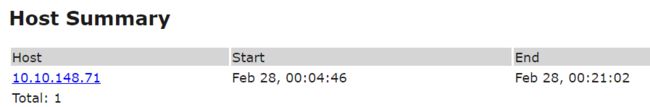
1.When did the scan start in Case 001?
Feb 28, 00:04:46
2.When did the scan end in Case 001?
Feb 28, 00:21:02
3.How many ports are open in Case 001?
3
4.How many total vulnerabilities were found in Case 001?
5
5.What is the highest severity vulnerability found? (MSxx-xxx)
MS17-010
6.What is the first affected OS to this vulnerability?
Microsoft Windows 10 x32/x64 Edition
7.What is the recommended vulnerability detection method?
Send the crafted SMB transaction request with fid = 0 and check the response to confirm the vulnerability
Task8 Conclusion
Check out the provided links and keep learning