在已有的k8s中部署rancher
在k8s中rancher, 接上文安装ingress之后, 需要先安装ingress-nginx, 链接
安装需要Helm, 请自行安装Helm.
k8s的master节点是: 10.6.14.23
第一步: 安装证书
vim cert.sh
#!/bin/bash -e
help ()
{
echo ' ================================================================ '
echo ' --ssl-domain: 生成ssl证书需要的主域名,如不指定则默认为localhost,如果是ip访问服务,则可忽略;'
echo ' --ssl-trusted-ip: 一般ssl证书只信任域名的访问请求,有时候需要使用ip去访问server,那么需要给ssl证书添加扩展IP,多个IP用逗号隔开;'
echo ' --ssl-trusted-domain: 如果想多个域名访问,则添加扩展域名(SSL_TRUSTED_DOMAIN),多个扩展域名用逗号隔开;'
echo ' --ssl-size: ssl加密位数,默认2048;'
echo ' --ssl-date: ssl有效期,默认10年;'
echo ' --ca-date: ca有效期,默认10年;'
echo ' --ssl-cn: 国家代码(2个字母的代号),默认CN;'
echo ' 使用示例:'
echo ' ./create_self-signed-cert.sh --ssl-domain=www.test.com --ssl-trusted-domain=www.test2.com \ '
echo ' --ssl-trusted-ip=1.1.1.1,2.2.2.2,3.3.3.3 --ssl-size=2048 --ssl-date=3650'
echo ' ================================================================'
}
case "$1" in
-h|--help) help; exit;;
esac
if [[ $1 == '' ]];then
help;
exit;
fi
CMDOPTS="$*"
for OPTS in $CMDOPTS;
do
key=$(echo ${OPTS} | awk -F"=" '{print $1}' )
value=$(echo ${OPTS} | awk -F"=" '{print $2}' )
case "$key" in
--ssl-domain) SSL_DOMAIN=$value ;;
--ssl-trusted-ip) SSL_TRUSTED_IP=$value ;;
--ssl-trusted-domain) SSL_TRUSTED_DOMAIN=$value ;;
--ssl-size) SSL_SIZE=$value ;;
--ssl-date) SSL_DATE=$value ;;
--ca-date) CA_DATE=$value ;;
--ssl-cn) CN=$value ;;
esac
done
#CA相关配置
CA_DATE=${CA_DATE:-3650}
CA_KEY=${CA_KEY:-cakey.pem}
CA_CERT=${CA_CERT:-cacerts.pem}
CA_DOMAIN=localhost
#ssl相关配置
SSL_CONFIG=${SSL_CONFIG:-$PWD/openssl.cnf}
SSL_DOMAIN=${SSL_DOMAIN:-localhost}
SSL_DATE=${SSL_DATE:-3650}
SSL_SIZE=${SSL_SIZE:-2048}
##国家代码(2个字母的代号),默认CN;
CN=${CN:-CN}
SSL_KEY=$SSL_DOMAIN.key
SSL_CSR=$SSL_DOMAIN.csr
SSL_CERT=$SSL_DOMAIN.crt
echo -e "\033[32m ---------------------------- \033[0m"
echo -e "\033[32m | 生成 SSL Cert | \033[0m"
echo -e "\033[32m ---------------------------- \033[0m"
if [[ -e ./${CA_KEY} ]]; then
echo -e "\033[32m ====> 1. 发现已存在CA私钥,备份"${CA_KEY}"为"${CA_KEY}"-bak,然后重新创建 \033[0m"
mv ${CA_KEY} "${CA_KEY}"-bak
openssl genrsa -out ${CA_KEY} ${SSL_SIZE}
else
echo -e "\033[32m ====> 1. 生成新的CA私钥 ${CA_KEY} \033[0m"
openssl genrsa -out ${CA_KEY} ${SSL_SIZE}
fi
if [[ -e ./${CA_CERT} ]]; then
echo -e "\033[32m ====> 2. 发现已存在CA证书,先备份"${CA_CERT}"为"${CA_CERT}"-bak,然后重新创建 \033[0m"
mv ${CA_CERT} "${CA_CERT}"-bak
openssl req -x509 -sha256 -new -nodes -key ${CA_KEY} -days ${CA_DATE} -out ${CA_CERT} -subj "/C=${CN}/CN=${CA_DOMAIN}"
else
echo -e "\033[32m ====> 2. 生成新的CA证书 ${CA_CERT} \033[0m"
openssl req -x509 -sha256 -new -nodes -key ${CA_KEY} -days ${CA_DATE} -out ${CA_CERT} -subj "/C=${CN}/CN=${CA_DOMAIN}"
fi
echo -e "\033[32m ====> 3. 生成Openssl配置文件 ${SSL_CONFIG} \033[0m"
cat > ${SSL_CONFIG} <<EOM
[req]
req_extensions = v3_req
distinguished_name = req_distinguished_name
[req_distinguished_name]
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = clientAuth, serverAuth
EOM
if [[ -n ${SSL_TRUSTED_IP} || -n ${SSL_TRUSTED_DOMAIN} ]]; then
cat >> ${SSL_CONFIG} <<EOM
subjectAltName = @alt_names
[alt_names]
EOM
IFS=","
dns=(${SSL_TRUSTED_DOMAIN})
dns+=(${SSL_DOMAIN})
for i in "${!dns[@]}"; do
echo DNS.$((i+1)) = ${dns[$i]} >> ${SSL_CONFIG}
done
if [[ -n ${SSL_TRUSTED_IP} ]]; then
ip=(${SSL_TRUSTED_IP})
for i in "${!ip[@]}"; do
echo IP.$((i+1)) = ${ip[$i]} >> ${SSL_CONFIG}
done
fi
fi
echo -e "\033[32m ====> 4. 生成服务SSL KEY ${SSL_KEY} \033[0m"
openssl genrsa -out ${SSL_KEY} ${SSL_SIZE}
echo -e "\033[32m ====> 5. 生成服务SSL CSR ${SSL_CSR} \033[0m"
openssl req -sha256 -new -key ${SSL_KEY} -out ${SSL_CSR} -subj "/C=${CN}/CN=${SSL_DOMAIN}" -config ${SSL_CONFIG}
echo -e "\033[32m ====> 6. 生成服务SSL CERT ${SSL_CERT} \033[0m"
openssl x509 -sha256 -req -in ${SSL_CSR} -CA ${CA_CERT} \
-CAkey ${CA_KEY} -CAcreateserial -out ${SSL_CERT} \
-days ${SSL_DATE} -extensions v3_req \
-extfile ${SSL_CONFIG}
echo -e "\033[32m ====> 7. 证书制作完成 \033[0m"
echo
echo -e "\033[32m ====> 8. 以YAML格式输出结果 \033[0m"
echo "----------------------------------------------------------"
echo "ca_key: |"
cat $CA_KEY | sed 's/^/ /'
echo
echo "ca_cert: |"
cat $CA_CERT | sed 's/^/ /'
echo
echo "ssl_key: |"
cat $SSL_KEY | sed 's/^/ /'
echo
echo "ssl_csr: |"
cat $SSL_CSR | sed 's/^/ /'
echo
echo "ssl_cert: |"
cat $SSL_CERT | sed 's/^/ /'
echo
echo -e "\033[32m ====> 9. 附加CA证书到Cert文件 \033[0m"
cat ${CA_CERT} >> ${SSL_CERT}
echo "ssl_cert: |"
cat $SSL_CERT | sed 's/^/ /'
echo
echo -e "\033[32m ====> 10. 重命名服务证书 \033[0m"
echo "cp ${SSL_DOMAIN}.key tls.key"
cp ${SSL_DOMAIN}.key tls.key
echo "cp ${SSL_DOMAIN}.crt tls.crt"
cp ${SSL_DOMAIN}.crt tls.crt
#生成证书
sudo chmod +x cert.sh
./cert.sh --ssl-domain=rancher.sigs.applysquare.net --ssl-size=2048 --ssl-date=3650
#创建namespace
kubectl create namespace cattle-system
#服务证书和私钥密文
kubectl -n cattle-system create \
secret tls tls-rancher-ingress \
--cert=./tls.crt \
--key=./tls.key
#ca证书密文
kubectl -n cattle-system create secret \
generic tls-ca \
--from-file=./cacerts.pem
第二步: Helm安装Rancher
#添加仓库
helm repo add rancher-stable https://releases.rancher.com/server-charts/stable
#安装rancher
helm install rancher rancher-stable/rancher \
--namespace cattle-system \
--set hostname=rancher.test.com \
--set ingress.tls.source=secret \
--set privateCA=false #为false不启用验证
第三步, 配置hosts
#节点的/etc/hosts 以及 本地访问的windows的hosts
10.6.14.23 rancher.test.com
这里需要使用到ingress-nginx配置的端口来访问.
https://rancher.test.com:32443 #其中32443端口来自上一篇文章安装ingress-nginx中
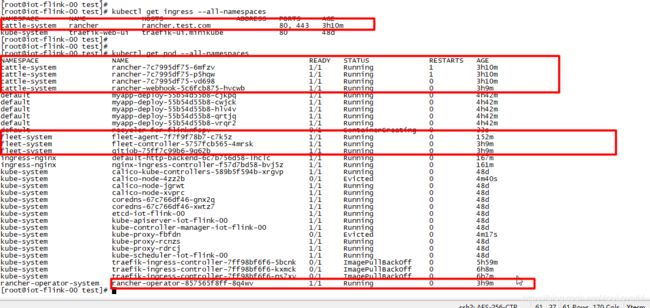
运行成功后pod和ingress如下:
第四步, 如果rancher安装失败,想要重新安装, 那么需要将rancher卸载干净, 那么需要执行脚本
vi delete-rancher.sh
sh delete-rancher.sh
#!/bin/bash
# k8s=1.18 rchaner=2.5.5
api_server="https://10.6.14.23:6443"
token=`cat .kube/admin-token`
echo "处理删除中断"
curl -k $api_server/api/v1/namespaces/local/finalize \
-H "Authorization: Bearer $token" \
-H "Content-Type: application/json" \
-XPUT \
-d '{"apiVersion":"v1","kind":"Namespace","metadata":{"name":"local"},"spec":{"finalizers":[]}}'
kubectl patch --type='json' -p='[{"op": "remove", "path": "/metadata/finalizers"}]' ns $(kubectl get ns |egrep 'cattle|fleet|rancher|local|^p-|^user-' |awk '{print $1}')
project_ns=`kubectl get ns |egrep '^p-|local' |awk '{print $1}'`
project_crd=(clusterroletemplatebindings.management.cattle.io clusteralertgroups.management.cattle.io projects.management.cattle.io projectalertgroups.management.cattle.io projectalertrules.management.cattle.io projectroletemplatebindings.management.cattle.io nodes.management.cattle.io)
for ns in ${project_ns[@]}
do
for crd in ${project_crd[@]}
do
kubectl patch --type='json' -p='[{"op": "remove", "path": "/metadata/finalizers"}]' $crd -n $ns $(kubectl get $crd -n $ns|grep -v NAME|awk '{print $1}')
done
done
crd_list=`kubectl get crd |grep cattle.io |awk '{print $1}'`
for crd in $crd_list
do
kubectl patch --type='json' -p='[{"op": "remove", "path": "/metadata/finalizers"}]' $crd $(kubectl get $crd |grep -v NAME|awk '{print $1}')
done
echo "使用rancher清理工具 https://docs.rancher.cn/docs/rancher2/system-tools/_index/"
./system-tools remove -c .kube/config
kubectl get crd
echo "理论上所有rancher的crd都会被删除,如果还有说明有异常,继续会强制删除"
echo "按任意键继续"
read anykey
echo "helm卸载"
helm uninstall rancher -n cattle-system
helm uninstall rancher-operator -n rancher-operator-system
helm uninstall rancher-operator-crd -n rancher-operator-system
helm uninstall fleet -n fleet-system
helm uninstall fleet-crd -n fleet-system
echo "清理剩余资源"
sleep 5
for ns in $(kubectl get ns |grep -v NAME|awk '{print $1}')
do
kubectl delete rolebinding $(kubectl get rolebinding -n $ns --selector='cattle.io/creator=norman' |grep -v NAME|awk '{print $1}') -n $ns
done
ns_list=`kubectl get ns |egrep 'cattle|fleet|rancher|local' |awk '{print $1}'`
kubectl delete ns $ns_list
kubectl patch --type='json' -p='[{"op": "remove", "path": "/metadata/finalizers"}]' crd $(kubectl get crd |grep 'cattle.io' |awk '{print $1}')
kubectl get crd |grep 'cattle.io' |awk '{print $1}' |xargs kubectl delete crd
kubectl get clusterrolebinding |egrep 'default-admin|fleet|pod-impersonation-helm-op|rancher' |awk '{print $1}' |xargs kubectl delete clusterrolebinding
kubectl get clusterrole |egrep 'fleet|pod-impersonation-helm-op' |awk '{print $1}' |xargs kubectl delete clusterrole
kubectl label ns $(kubectl get ns |egrep -v 'NAME' |awk '{print $1}') field.cattle.io/projectId-
参考文档:
https://blog.51cto.com/13760351/2494356?source=dra
https://www.cnblogs.com/37yan/p/14275214.html