Ubuntu 22.04安装配置snort
文章目录
-
- 安装
-
- 环境配置
- 安装snort
- 配置
- 使用
-
- 规则编写
- 简单ping测试
- 监听数据包获取raw数据
- 检测大小超过800的ICMP包(ping)
- TCP数据包检测
- TCP异常检测
- 参考
入侵检测系统(IntrusionDetectionSystem,IDS)是一种主动保护自己免受攻击的一种网络安全技术。作为防火墙的合理补充,入侵检测技术能够帮助系统监测攻击行为,扩展了系统管理员的安全管理能力(包括安全审计、监视、攻击识别和响应),提高了信息安全基础结构的完整性。它从计算机网络系统中的若干关键点收集信息,并分析这些信息。入侵检测被认为是防火墙之后的第二道安全闸门,能够在不影响网络性能的情况下能对网络进行监测,防止或减轻上述的网络威胁。
入侵检测系统有很多种,从部署的位置可以分为以下几种:
- 基于网络的系统。它放置于网络之上,靠近被检测的系统,它们监测网络流量并判断是否正常。
- 基于主机的系统。其经常运行在被监测的系统之上,用以监测系统上正在运行的进程是否合法。
最近出现的一种系统,位于操作系统的内核之中,并监测系统的最底层行为。
从检测的技术手段上可以分为以下两种:
- 误用检测:是将收集到的数据与预先确定的特征知识库里的各种攻击模式进行比较,如果发现有攻击特征,则判断有攻击。特征知识库是将己知的攻击方法和技术的特征提取出来建立的一个知识库。
- 异常检测:是对收集到的数据进行统计分析。它首先假定所有的攻击行为与正常行为不同,这样发现与正常行为有不同时,则判断存在攻击。它需要建立正常行为的标准,如登录时错误次数为多少时视为正常。
相比而言,误用检测的原理简单,很容易配置,特征知识库也容易扩充。但它存在一个致命的弱点――只能检测到已知的攻击方法和技术。异常检测可以检测出已知的和未知的攻击方法和技术,但是其问题在于正常行为标准只能采用人工智能、机器学习算法等来生成,并且需要大量的数据和时间,同时,由于现在人工智能和机器学习算法仍处于研究阶段。所以现在的入侵检测系统大多采用误用检测的分析方法。
安装
环境配置
安装依赖
apt install build-essential libpcap-dev libpcre3-dev libnet1-dev zlib1g-dev luajit hwloc libdnet-dev libdumbnet-dev bison flex liblzma-dev openssl libssl-dev pkg-config libhwloc-dev cmake cpputest libsqlite3-dev uuid-dev libcmocka-dev libnetfilter-queue-dev libmnl-dev autotools-dev libluajit-5.1-dev libunwind-dev -y
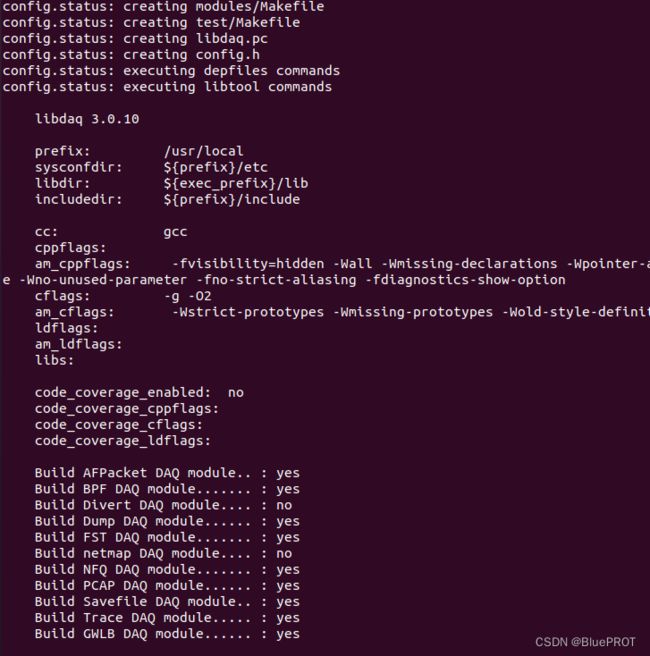
安装DAQ,这个是什么数据采集库,不知道干啥用的,要从github下载https://github.com/snort3/libdaq,我这用3.0.10版本
tar -zxvf libdaq-3.0.10.tar.gz
安装libdaq
./bootstrap
./configure
make
make install
安装snort
这是snort官网
从github获取snort
wget https://github.com/snort3/snort3/archive/3.0.2-5.tar.gz
我是用的这个版本https://github.com/snort3/snort3/releases/tag/3.1.51.0
解压
tar -zxvf snort3-3.1.51.0.tar.gz
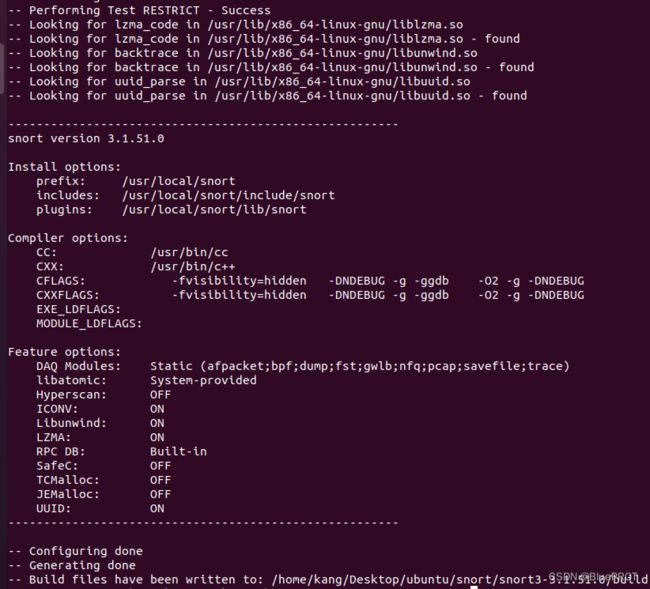
配置、编译和安装
正常应该是./configure && make && make install,不知道是不是我的版本比较高,只有./configure_cmake.sh,那就执行这个吧
./configure_cmake
cd build
make
./src/snort: error while loading shared libraries: libdaq.so.3: cannot open shared object file: No such file or directory
执行strace ./src/snort追踪一下,发现他寻找的目录和我们上面安装的目录不一致,导致找不到
openat(AT_FDCWD, "/usr/lib/x86_64/libdaq.so.3", O_RDONLY|O_CLOEXEC) = -1 ENOENT (No such file or directory)
stat("/usr/lib/x86_64", 0x7ffc11dfb6c0) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/usr/lib/libdaq.so.3", O_RDONLY|O_CLOEXEC) = -1 ENOENT (No such file or directory)
stat("/usr/lib", {st_mode=S_IFDIR|0755, st_size=4096, ...}) = 0
writev(2, [{iov_base="./src/snort", iov_len=11}, {iov_base=": ", iov_len=2}, {iov_base="error while loading shared libra"..., iov_len=36}, {iov_base=": ", iov_len=2}, {iov_base="libdaq.so.3", iov_len=11}, {iov_base=": ", iov_len=2}, {iov_base="cannot open shared object file", iov_len=30}, {iov_base=": ", iov_len=2}, {iov_base="No such file or directory", iov_len=25}, {iov_base="\n", iov_len=1}], 10./src/snort: error while loading shared libraries: libdaq.so.3: cannot open shared object file: No such file or directory
创建一个链接
ln -s /usr/local/lib/libdaq.so.3.0.0 /usr/lib/x86_64-linux-gnu/libdaq.so.3
然后执行./src/snort -v就可以看到了
我的小猪怎么裂开了,不对,我这好像不是个猪,难道版本太新了猪被更新了?

配置
这里需要对规则集进行配置一下
规则集分为三种:
- 社区规则集:免费用
- 主责规则:注册以后用
- 商业规则:收费
snort配置文件的路径在/usr/local/snort/etc/snort/snort_defaults.lua
在里面可以看到RULE_PATH是RULE_PATH = ‘…/rules’
我改成了RULE_PATH = ‘/usr/local/snort/rules’
创建文件夹顺便授权777
mkdir /usr/local/snort/rules
进去下载
wget https://www.snort.org/downloads/community/snort3-community-rules.tar.gz
tar -zxvf snort3-community-rules.tar.gz
修改配置文件,前者是需要防护的网络,后者是外部网络
HOME_NET = '192.168.1.30/32'
EXTERNAL_NET = '!$HOME_NET'
...
-- 添含上面添加的规则集的地址到include里
ips =
{
-- use this to enable decoder and inspector alerts
--enable_builtin_rules = true,
-- use include for rules files; be sure to set your path
-- note that rules files can include other rules files
-- (see also related path vars at the top of snort_defaults.lua)
include = 'usr/local/snort/rules/snort3-community-rules/snort3-community.rules',
variables = default_variables
}
配置日志文件夹
mkdir /var/log/snort
chmod 777 /var/log/snort
检查一下./src/snort -c /usr/local/snort/etc/snort/snort.lua,0warnings和successfully应该就好了
root@controller:/home/kang/Desktop/ubuntu/snort/snort3-3.1.51.0/build# ./src/snort -c /usr/local/snort/etc/snort/snort.lua
--------------------------------------------------
o")~ Snort++ 3.1.51.0
--------------------------------------------------
Loading /usr/local/snort/etc/snort/snort.lua:
Loading snort_defaults.lua:
Finished snort_defaults.lua:
ssh
...
stream_file
Finished /usr/local/snort/etc/snort/snort.lua:
Loading file_id.rules_file:
Loading file_magic.rules:
Finished file_magic.rules:
Finished file_id.rules_file:
Loading /usr/local/snort/rules/snort3-community-rules/snort3-community.rules:
Finished /usr/local/snort/rules/snort3-community-rules/snort3-community.rules:
--------------------------------------------------
ips policies rule stats
id loaded shared enabled file
0 4239 0 4239 /usr/local/snort/etc/snort/snort.lua
--------------------------------------------------
rule counts
total rules loaded: 4239
text rules: 4239
option chains: 4239
chain headers: 326
flowbits: 48
flowbits not checked: 23
--------------------------------------------------
port rule counts
tcp udp icmp ip
any 473 58 147 22
src 177 17 0 0
dst 787 154 0 0
both 6 11 0 0
total 1443 240 147 22
--------------------------------------------------
service rule counts to-srv to-cli
dcerpc: 7 4
dhcp: 2 2
dns: 28 7
file_id: 208 208
ftp: 90 4
...
wins: 1 0
total: 6998 1416
--------------------------------------------------
fast pattern groups
src: 118
dst: 316
any: 8
to_server: 71
to_client: 48
--------------------------------------------------
search engine
instances: 340
patterns: 10724
pattern chars: 174587
num states: 122936
num match states: 10484
memory scale: MB
total memory: 3.67728
pattern memory: 0.575263
match list memory: 1.3313
transition memory: 1.72921
fast pattern only: 7107
--------------------------------------------------
pcap DAQ configured to passive.
Snort successfully validated the configuration (with 0 warnings).
o")~ Snort exiting
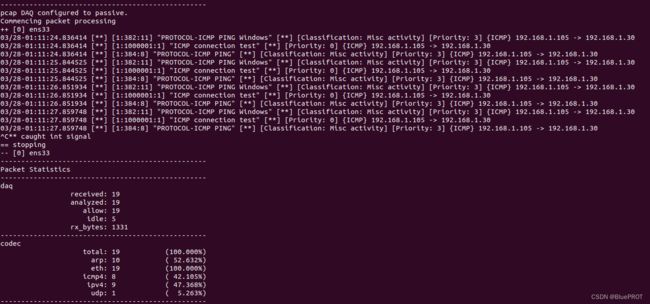
这里创建一个本地测试集试试,vim /usr/local/snort/rules/snort3-community-rules/local.rules,添加了一条检测ping的规则
alert icmp any any -> $HOME_NET any (msg:"ICMP connection test"; sid:1000001; rev:1;)
验证一下,0wagings应该就没问题
./src/snort -c /usr/local/snort/etc/snort/snort.lua -R /usr/local/snort/rules/snort3-community-rules/local.rules
使用
规则编写
控制控制报警频率
这个好像在版本里取消了
threshold: type <threshold|limit|both>, track <by_src|by_dst>, count , seconds
可以更好地进行过滤
- threshold:最小阈值。至少匹配多少次时才告警
- limit:限制告警次数。比如至少五分钟告警一次
- both:二合一
比如,对于下面这三个
threshold: type threshold, track by_src, count 10, seconds 60
在60秒内对同一个源ip匹配到10次才产生告警
threshold: type limit, track by_src, seconds 180, count 1
如果匹配成功,则在3分钟内每个源ip最多生成1个警报
threshold: type both, track by_src, count 5, seconds 360;
如果在6分钟内有5个或更多匹配,将生成警报,并且在6分钟内仅警报一次
推荐用detection_filter或者event_filter
detection_filter:track by_dst,count 30,seconds 30;
简单ping测试
执行如下命令,进行监听。可以把这个规则文件添加到配置文件里面,用include
./src/snort -c /usr/local/snort/etc/snort/snort.lua -R /usr/local/snort/rules/snort3-community-rules/local.rules -i ens33 -A alert_fast -s 65535 -k none
然后我从宿主机ping过去,看到终端有输出,ctrl-c停止

在使用之前要设置网卡为混杂模式,要记得设置网卡的混杂模式
ip link set dev ens33 promisc on
还要检查是否禁用了这个功能,禁用的话就会把大数据包截获了,如果GRE是开的,执行第二条命令关闭
ethtool -k ens33 | grep receive-off
ethtool -K ens33 gro off lro off
监听数据包获取raw数据
随便对ens33网卡监听一个数据包,抓到这个了
抓包
root@controller:/home/kang/Desktop/ubuntu/snort/snort3-3.1.51.0/build# ./src/snort -d -e -v -X -L dump -Q -n 1 -i ens33
--------------------------------------------------
o")~ Snort++ 3.1.51.0
--------------------------------------------------
--------------------------------------------------
Network Policy : policy id 0 :
--------------------------------------------------
Inspection Policy : policy id 0 :
--------------------------------------------------
pcap DAQ configured to inline.
--------------------------------------------------
host_cache
memcap: 8388608 bytes
Commencing packet processing
++ [0] ens33
Instance 0 daq pool size: 256
Instance 0 daq batch size: 64
pkt:1
eth(DLT): B0:95:8E:33:26:A8 -> 00:0C:29:EA:74:56 type:0x0800
ipv4(0x0800): 60.29.252.197 -> 192.168.1.30
Next:0x06 TTL:54 TOS:0x0 ID:45807 IpLen:20 DgmLen:1480 DF
tcp(0x06): ***A**** SrcPort:80 DstPort:35278
Seq: 0x9AE588C6 Ack: 0xDE56B703 Win: 0xB3 TcpLen: 20
snort.raw[1440]:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
0000 01 50 1C 0D 9E 18 CC E7 2E 91 36 81 78 33 65 7B .P...... ..6.x3e{
0010 60 CE AE D4 C2 DB 7F A4 2A 46 3D AB F3 63 B5 68 `....... *F=..c.h
0020 46 5E 0D B8 1D 0A 08 79 02 72 50 E0 38 A3 3A 4D F^.....y .rP.8.:M
0030 3A 29 C6 DF EB 34 DE 5C A6 24 8E 0B 13 BD B1 F1 :)...4.\ .$......
0040 DD 43 B7 D6 FB D7 37 E3 0D 6B 26 04 CA 19 5C F1 .C....7. .k&...\.
0050 D9 2C C9 17 0D AE E0 18 88 FC B4 74 D9 0F 67 B6 .,...... ...t..g.
0060 C8 E0 B5 94 CE 38 91 20 C2 BF 04 04 BA A5 82 83 .....8. ........
0070 9B 52 A5 F0 B4 4B 58 60 AB 81 46 86 9B 1E 90 1E .R...KX` ..F.....
0080 3F 34 01 1B AE DB FB 67 84 4A D7 6B C5 90 97 74 ?4.....g .J.k...t
0090 36 BB FB A9 98 F9 CB 46 48 63 21 9A DC C1 A7 13 6......F Hc!.....
00A0 41 52 E7 9C E1 42 D9 92 37 78 FA 54 2E 46 19 36 AR...B.. 7x.T.F.6
00B0 91 7D 49 F2 7E E4 1C 46 B2 13 5A 54 CD C6 AA A1 .}I.~..F ..ZT....
00C0 85 DB 84 DB 98 27 98 DA FD D0 EC B2 1C 1F 2C AD .....'.. ......,.
00D0 FF 7B F3 00 6F F9 27 EB 5D 7C D9 C7 C2 F1 A5 2A .{..o.'. ]|.....*
00E0 E5 C4 9D 29 49 2D 4F E1 8B 57 8E CA 59 4C B1 EE ...)I-O. .W..YL..
00F0 B6 B1 78 38 0C F4 DC 0A 13 CA 56 1F F6 A5 B6 BB ..x8.... ..V.....
0100 42 F5 22 A4 7C 70 85 3B 2F 9D 3F D3 C9 ED 5E 31 B.".|p.; /.?...^1
0110 DC 64 B1 2D A2 2D 6F 20 65 FC 21 B0 72 80 88 C0 .d.-.-o e.!.r...
0120 6A 07 37 2D D2 10 3F 26 B5 2B E3 6E C4 15 18 BA j.7-..?& .+.n....
0130 1A ED 14 2C 03 9C C7 FE 42 1F 43 BA 36 8E 2F E4 ...,.... B.C.6./.
0140 2E E4 00 E4 40 48 CA 3B 21 69 4B 32 81 F3 7A 88 ....@H.; !iK2..z.
0150 E8 CF 14 22 F7 C7 85 CC 23 7B 37 00 E4 D3 3B 37 ...".... #{7...;7
0160 09 1F 30 E3 47 D2 BD 72 4F F5 87 BF AE 7E 8C E9 ..0.G..r O....~..
0170 DC E1 16 07 E3 EC 7C 6C 85 29 B4 C8 5A D9 11 BD ......|l .)..Z...
0180 08 EC 7F D1 6E 3C E0 75 C9 1D 47 38 4A 8E 09 1E ....n<.u ..G8J...
0190 F2 A7 9D 5D 1D 20 C9 D9 93 42 3B E4 66 E2 9B 48 ...]. .. .B;.f..H
01A0 7A E8 98 E2 97 4D 7A EF 34 C2 50 B9 8C 0A 54 93 z....Mz. 4.P...T.
01B0 C4 9D 8A 4F 74 62 94 69 D1 BE AD 99 B1 04 56 03 ...Otb.i ......V.
01C0 59 5C BA 53 0A 8F 7E D0 5C AB EE E0 11 AE 03 B0 Y\.S..~. \.......
01D0 40 AE 6D 37 D8 38 F6 44 D7 79 5A B8 47 01 3B AB @.m7.8.D .yZ.G.;.
01E0 C1 3A E5 4A 58 34 2A 94 29 03 77 B3 70 3F 85 73 .:.JX4*. ).w.p?.s
01F0 53 0D E3 43 48 2E 5E 9D F6 3C BB 6D 1A 6C 11 70 S..CH.^. .<.m.l.p
0200 56 1A 4D 63 D2 ED DC 65 E5 5A BE 12 DB F9 D2 76 V.Mc...e .Z.....v
0210 C1 46 F7 96 CB 60 37 B5 C6 C1 D6 AC C2 72 A4 A0 .F...`7. .....r..
0220 9C 93 87 F5 8B 8B FB 36 DA C8 C5 03 8C A5 CC 29 .......6 .......)
0230 F6 A2 41 95 B7 D7 1C FC A4 CC 30 B2 D9 65 C1 2A ..A..... ..0..e.*
0240 F9 E0 38 2A 6E 7F EA 74 19 E4 01 95 BD 7E A0 8A ..8*n..t .....~..
0250 09 57 EC 36 DC D9 98 C1 92 47 5A 64 CC BA 25 23 .W.6.... .GZd..%#
0260 30 BC 0B 9E 84 0D DA E2 2F 3C 54 82 BD 8D DA 19 0....... /<T.....
0270 41 8D 4A 82 FF 6E 12 45 DF AD 50 84 80 D6 9C 52 A.J..n.E ..P....R
0280 9B 42 3B 4F BC 34 D7 6D FC 65 AE A2 94 75 BB C7 .B;O.4.m .e...u..
0290 8B 95 37 B8 FB 3F AF DF 8F 81 9E B0 FB C4 35 69 ..7..?.. ......5i
02A0 74 73 6A 7C 62 3D 03 96 AA 93 AC CF ED 13 B8 7D tsj|b=.. .......}
02B0 B8 BC B9 18 06 A7 B6 C6 01 F1 AD A0 AD B3 CA 6A ........ .......j
02C0 C3 3A 3A 78 CD EC AB 78 36 59 05 E2 25 D4 9D 24 .::x...x 6Y..%..$
02D0 65 45 77 CF 00 34 F6 A8 E4 00 98 D6 22 9E 8C 22 eEw..4.. ....".."
02E0 1E CD 55 41 FF C0 4A 7A 35 A9 4E 89 BA FB 83 4B ..UA..Jz 5.N....K
02F0 6E 4D D7 C6 AF FD ED 6A BB 48 D3 9D C5 1E 16 46 nM.....j .H.....F
0300 F6 15 0D DD 3E 0B E4 D5 65 97 A0 9F D3 10 51 78 ....>... e.....Qx
0310 4F DD 4E 04 BA B9 BB B8 09 A3 D4 3E 9A 20 42 A8 O.N..... ...>. B.
0320 65 3F 04 F6 57 BC 2C 66 CF FA 59 6D 43 F1 DF E1 e?..W.,f ..YmC...
0330 04 D5 A1 D1 C5 29 27 99 F7 F4 85 EA 07 59 A3 BB .....)'. .....Y..
0340 82 AC 69 E3 A7 FB 4D 23 24 5C 51 68 BF 6B 5A 6F ..i...M# $\Qh.kZo
0350 4C CD E2 28 47 5A 32 7D 5D F5 B0 AB 1B 2B 48 3C L..(GZ2} ]....+H<
0360 BB D7 3B 6F E8 EF AA 2B 5B 35 0A 4F 6E C1 82 B7 ..;o...+ [5.On...
0370 E8 FB FC 3A D3 79 A5 E2 C4 DF AA 02 88 40 35 E4 ...:.y.. .....@5.
0380 E1 9B 17 E5 55 8B B0 66 4B BD 76 8E CC 8C A4 1A ....U..f K.v.....
0390 C0 82 6D D2 1F 48 FC CC 6E 40 C3 8F 42 48 02 8C ..m..H.. [email protected]..
03A0 5C 86 92 34 D6 DE 10 20 80 AD 9D 00 63 FA A8 B3 \..4... ....c...
03B0 A2 35 3E 0E 84 07 E2 10 71 72 02 5C 73 1E 94 AD .5>..... qr.\s...
03C0 9A DD C0 6F 52 71 75 D0 D1 4E 92 7D FF 6E 1C 71 ...oRqu. .N.}.n.q
03D0 37 55 EF 80 33 8C 8A E3 E3 79 81 7B 21 95 FD BC 7U..3... .y.{!...
03E0 BB E4 09 E3 50 1B A5 06 10 4D B1 82 43 B7 CD 78 ....P... .M..C..x
03F0 EB EA CD 3B 27 81 B3 F4 C4 7F AD D1 95 14 ED 3C ...;'... .......<
0400 0E 63 E9 D0 69 51 16 0E 3C 06 34 1B 04 16 D1 25 .c..iQ.. <.4....%
0410 4B 88 8F 16 AF 95 77 99 56 53 D4 33 7D D3 0C C1 K.....w. VS.3}...
0420 7D 4C 2B 41 6A CA 5E 14 DE 90 14 B1 05 59 AE D5 }L+Aj.^. .....Y..
0430 96 2B F0 8B 86 27 4B 1B 89 7F 3B 32 CB 53 94 DD .+...'K. ..;2.S..
0440 C5 FF 02 C7 4F ED 60 4E C4 38 BB EB D2 6B CD FA ....O.`N .8...k..
0450 FC 47 EC B2 FF 5E D5 66 62 C4 81 8D 01 93 32 05 .G...^.f b.....2.
0460 B2 A6 0F 36 11 F2 52 9C CA 56 25 EF EE 25 0C 0C ...6..R. .V%..%..
0470 43 28 D4 6A A9 3D 19 1E 39 1F 3B D7 7F 77 26 72 C(.j.=.. 9.;..w&r
0480 B8 00 2E 6B F4 E7 4A 3A 91 4E 9A 6B F3 F0 4B 7C ...k..J: .N.k..K|
0490 59 D7 78 F9 17 43 11 F6 47 BE 8E F6 AD DE CF D7 Y.x..C.. G.......
04A0 CD A2 C9 4E 43 80 33 EF 45 2B 67 A5 47 3D 1F 4F ...NC.3. E+g.G=.O
04B0 B7 FA 55 FB CE 47 FD 90 5E 5E 88 E6 57 42 1D E0 ..U..G.. ^^..WB..
04C0 9D 07 F8 9D CD 21 94 D6 36 12 27 A7 06 DF 98 AD .....!.. 6.'.....
04D0 51 09 53 F5 5F DA 0E F9 5E AB 3B 71 5F FE EF 88 Q.S._... ^.;q_...
04E0 00 5A A1 70 3A 96 2C DF 6E 81 4B D6 10 F9 A4 2B .Z.p:.,. n.K....+
04F0 45 FE E1 E3 5D 97 3C 58 AF 1A F9 DF CE E3 73 23 E...].. |....1..
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
-- [0] ens33
--------------------------------------------------
Packet Statistics
--------------------------------------------------
daq
received: 22
analyzed: 1
outstanding: 21
allow: 1
rx_bytes: 1494
--------------------------------------------------
codec
total: 1 (100.000%)
eth: 1 (100.000%)
ipv4: 1 (100.000%)
tcp: 1 (100.000%)
--------------------------------------------------
Module Statistics
--------------------------------------------------
detection
analyzed: 1
logged: 1
--------------------------------------------------
Summary Statistics
--------------------------------------------------
timing
runtime: 00:00:00
seconds: 0.115728
pkts/sec: 9
o" )~ Snort exiting
检测大小超过800的ICMP包(ping)
修改规则/usr/local/snort/rules/snort3-community-rules/local.rules,注释掉原来的,添加这个
#alert icmp any any -> $HOME_NET any (msg:"ICMP connection test"; sid:1000001; rev:1;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP Large ICMP Packet"; dsize:>800; reference:arachnids,246; classtype:bad-unknown; sid:499; rev:4;)
这里 我ping了两次,一次正常ping,第二次每个包大小1000字节,检测到了第二次

TCP数据包检测
编写规则,第一个any表示源端口为任意,第二个any表示目的端口为任意端口
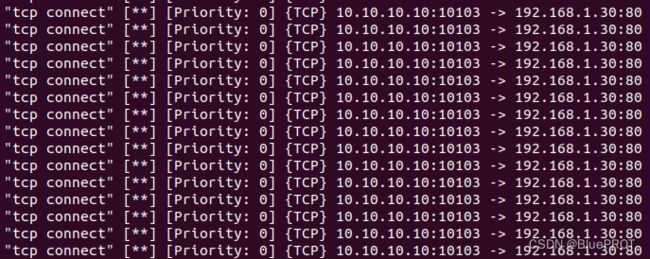
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"tcp connect"; sid:500;)
然后用python发包
from scapy.all import *
for i in range(100):
send(IP(dst="192.168.1.30",src="10.10.10.10")/TCP(sport=10103,dport=80,flags="S"))
TCP异常检测
现在添加一下参数,检测一下异常TCP
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"tcp src is to quick"; sid:500;detection_filter:track by_src,count 10,seconds 30;)
这里阈值是10,所以发11个包试试
看到输出,这里只有一条输出,因为我们规定的是30s以内如果相同源IP超过10个就告警,这里刚好满足一次
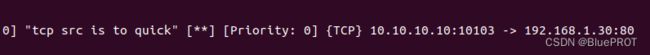 然后我发了21次试试,告警了11次,应该是这个阈值10相当于是个窗口,每来一个窗口都会满,所以就再告警一次。
然后我发了21次试试,告警了11次,应该是这个阈值10相当于是个窗口,每来一个窗口都会满,所以就再告警一次。
参考
snort3安装测试
有安装和报错还有简单的测试
在Ubuntu 上安装和配置Snort 3 NIDS
有很多环境配置用到的安装包,直接复制过来基本就是所有环境依赖了。
有很完善的测试入门,可以监听到ping的东西
3.6 Snort 规则阈值
一点手册,从这里面才知道threadhold高版本不支持了,而是换成了detection_filter