Harbor—镜像仓库
1、Harbor介绍
Docker容器应用的开发和运行离不开可靠的镜像管理,虽然Docker官方也提供了公共的镜像仓库,但是从安全和效率等方面考虑,部署我们私有环境内的Registry也是非常必要的。Harbor是由VMware公司开源的企业级的Docker Registry管理项目,它包括权限管理(RBAC)、LDAP、日志审核、管理界面、自我注册、镜像复制和中文支持等功能。
官网地址:https://github.com/goharbor/harbor
2、Harbor镜像仓库部署
2.1、环境准备
harbor:192.168.4.5 2CPU、内存4G
关闭防火墙、selinux
2.2、自签发证书
1)创建存放证书目录
[root@harbor ~]# openssl version # 检查是否安装了openssl
[root@harbor ~]# mkdir /opt/harbor-ca-key
[root@harbor ~]# cd /opt/harbor-ca-key/2)创建ca证书
[root@harbor harbor-ca-key]# openssl genrsa -out ca.key 3072 # 生成3072位的ca.key的私钥
[root@harbor harbor-ca-key]# openssl req -new -x509 -days 3650 -key ca.key -out ca.pem # 生成一个数字证书 ca.pem,3650 表示证书的有效时间是 10 年,按箭头提示填写即可,没有箭头 标注的为空:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:guangzhou
Organization Name (eg, company) [Default Company Ltd]:harbor
Organizational Unit Name (eg, section) []:CA
Common Name (eg, your name or your server's hostname) []:harbor64.cn
Email Address []:[email protected]3)生成域名的证书
[root@harbor harbor-ca-key]# openssl genrsa -out harbor.key 3072 # 生成一个 3072 位的 key,也就是私钥
[root@harbor harbor-ca-key]# openssl req -new -key harbor.key -out harbor.csr #生成一个证书请求,一会签发证书时需要的,标箭头的按提示填写,没有箭头标注的为空:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:guangzhou
Organization Name (eg, company) [Default Company Ltd]:harbor
Organizational Unit Name (eg, section) []:CA
Common Name (eg, your name or your server's hostname) []:harbor64.cn
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:1234
An optional company name []:harbor4)签发证书
[root@harbor harbor-ca-key]# openssl x509 -req -in harbor.csr -CA ca.pem -CAkey ca.key -CAcreateserial -out harbor.pem -days 3650
Signature ok
subject=/C=CN/ST=guangdong/L=guangzhou/O=harbor/OU=CA/CN=harbor64.cn/[email protected]
Getting CA Private Key
[root@harbor harbor-ca-key]# openssl x509 -noout -text -in harbor.pem # 查看证书是否有效
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
ed:66:8a:c0:ca:d3:2b:9e
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=guangdong, L=guangzhou, O=harbor, OU=CA, CN=harbor64.cn/[email protected]
Validity
Not Before: Jun 5 10:33:54 2022 GMT
Not After : Jun 2 10:33:54 2032 GMT
Subject: C=CN, ST=guangdong, L=guangzhou, O=harbor, OU=CA, CN=harbor64.cn/[email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (3072 bit)
Modulus:
…………………………………………………… # 显示以上内容证明有效
[root@harbor harbor-ca-key]# ls
ca.key ca.pem ca.srl harbor.csr harbor.key harbor.pem2.3、安装 Harbor
1)安装docker、docker-compose
[root@harbor ~]# yum -y install wget
# 安装epel源,并将repo 配置中的地址替换为阿里云镜像站地址
[root@harbor ~]# wget -O /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-7.repo
[root@harbor ~]# sed -i 's|^#baseurl=https://download.fedoraproject.org/pub|baseurl=https://mirrors.aliyun.com|' /etc/yum.repos.d/epel*
[root@harbor ~]# sed -i 's|^metalink|#metalink|' /etc/yum.repos.d/epel*
# 下载阿里云的yum源文件
[root@harbor ~]# wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.cloud.tencent.com/repo/centos7_base.repo
# 配置docker源
[root@harbor ~]# wget https://download.docker.com/linux/centos/docker-ce.repo -P /etc/yum.repos.d/
[root@harbor ~]# yum clean all && yum makecache
[root@harbor ~]# yum install -y docker-ce docker-compose
[root@harbor ~]# systemctl enable docker
[root@harbor ~]# systemctl restart docker
2)安装harbor
[root@harbor ~]# wget --no-check-certificate http://github.com/goharbor/harbor/releases/download/v2.3.0/harbor-offline-installer-v2.3.0.tgz
[root@harbor ~]# cd harbor/
[root@harbor harbor]# cp harbor.yml.tmpl harbor.yml
[root@harbor harbor]# vim harbor.yml
5 hostname: harbor64 # 修改 hostname,跟上面签发的证书域名保持一致
17 certificate: /opt/harbor-ca-key/harbor.pem
18 private_key: /opt/harbor-ca-key/harbor.key
3) 在 hosts 文件添加如下一行,然后保存即可
192.168.4.5 harbor64
4)安装Harbor
[root@harbor harbor]# ./install.sh
[root@harbor harbor]# docker-compose stop # 停止harbor
[root@harbor harbor]# docker-compose start # 启动harbor5)Harbor图形化界面
浏览器输入网址:https://harbor64
![]()
2.4、Harbor镜像仓库使用
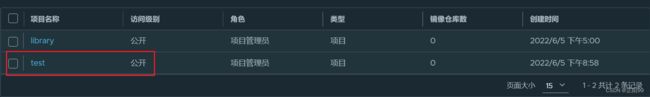
所有基础镜像都会放在 library 里面,这是一个公开的镜像仓库。
1)新建项目—>起个项目名字 test(把访问级别公开那个选中,让项目才可以被公开使用)
2.5、在node1上测试使用 harbor64 的 harbor 镜像仓库
1)修改 docker 配置
[root@node01 ~]# vim /etc/docker/daemon.json
{
"exec-opts": ["native.cgroupdriver=systemd"],
"registry-mirrors": ["http://f1361db2.m.daocloud.io"],
"insecure-registries": ["192.168.4.5"]
}
2)重启docker,查看docker是否启动成功
[root@node01 ~]# systemctl daemon-reload && systemctl restart docker
[root@node01 ~]# systemctl status docker3)登录harbor,验证
[root@node01 ~]# docker login 192.168.4.5
Username: admin
Password: 密码
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded4)导入 nginx 镜像
[root@node01 ~]# ls
anaconda-ks.cfg k8s-install nginx.tar.gz
[root@node01 ~]# docker load -i nginx.tar.gz
[root@node01 ~]# docker tag nginx:latest 192.168.4.5/test/nginx:v1
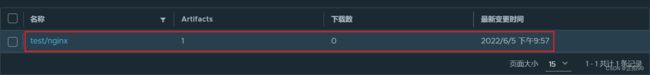
[root@node01 ~]# docker push 192.168.4.5/test/nginx:v1 #执行命令把nginx:v1上传到 harbor 里的 test 项目下
5)Harbor仓库,可以查看到nginx镜像
6)从 Harbor 仓库下载镜像
[root@node01 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
192.168.4.5/test/nginx v1 0e901e68141f 8 days ago 142MB
nginx latest 0e901e68141f 8 days ago 142MB
[root@node01 ~]# docker rmi -f 192.168.4.5/test/nginx:v1 # 删除镜像
[root@node01 ~]# docker pull 192.168.4.5/test/nginx:v1 # 拉取镜像