Docker之在一个镜像中开启多服务,容器的安全机制,做压测,cgroup的权限限制
[root@foundation44 ~]# cd /tmp/docker/
[root@foundation44 docker]# systemctl start dokcer
[root@foundation44 docker]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@foundation44 docker]# docker run -d --name vm1 nginx #打入后台运行,不能查看内容,nginx后面默认跟的是cmd命令,此时无法进入vm1内部
68469b00bffe1e5dd6ba4ddaf8c9eb7a2c1be4e8d4949c0526debc1ffbc14429
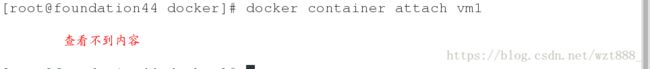
[root@foundation44 docker]# docker container attach vm1 #查看容器内部,查看不到,而且一旦执行此命令,vm1就会自动退出
[root@foundation44 docker]# docker start vm1
vm1
[root@foundation44 docker]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
68469b00bffe nginx "nginx -g 'daemon ..." 7 minutes ago Up 7 seconds 80/tcp vm1
[root@foundation44 docker]# docker container exec -it vm1 bash #这个命令可以进入容器,并且可以查看内容
root@68469b00bffe:/# ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
root@68469b00bffe:/# exit
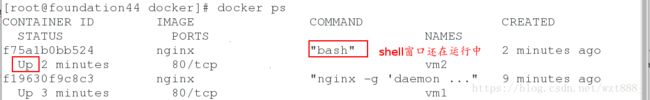
[root@foundation44 docker]# docker run -it --name vm2 nginx bash #run=create+start,交互式运行,bash可以覆盖cmd,打开交互shell,进入到容器内部查看信息
root@db59ec377fa8:/# #不能关闭容器退出, ctrl + p q ,这个是没有关闭容器的退出,ctrl + d ,关闭容器并且退出
[root@foundation44 docker]#
[root@foundation44 docker]# docker container attach vm2 #查看容器内容
root@db59ec377fa8:/# ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
root@db59ec377fa8:/# exit
1.开启多个服务在一个镜像中(以httpd+ssh为例)
镜像分层是为了共享
Dockerfile 负责安装; supervisor负责开启多个服务
因为cmd命令只能有一条所以想要同时开启多个服务定制到镜像中就需要调用一个管理进程来管理这些并行
进程的运行启动。
supervisor管理进程,是通过fork/exec的方式将这些被管理的进程当作supervisor的子进程来启动,
所以我们只需要将要管理进程的可执行文件的路径添加到supervisor的配置文件中就好了。此时被管理进
程被视为supervisor的子进程,若该子进程异常中断,则父进程可以准确的获取子进程异常中断的信息,
通过在配置文件中设置autostart=ture,可以实现对异常中断的子进程的自动重启。
[root@foundation44 tmp]# cd docker/
[root@foundation44 docker]# ls
Dockerfile dvd.repo ssh web
[root@foundation44 docker]# vim dvd.repo #编辑yum源
1 [dvd]
2 name=dvd
3 baseurl=http://172.25.44.250/rhel7.3
4 gpgcheck=0
5
6 [docker]
7 name=docker
8 baseurl=http://172.25.254.250/pub/docker
9 gpgcheck=0
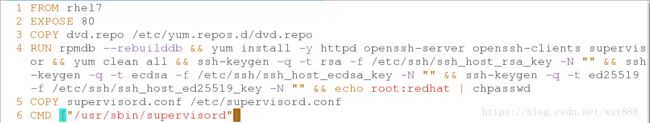
[root@foundation44 docker]# vim Dockerfile #编辑安装脚本
1 FROM rhel7
2 EXPOSE 80
3 COPY dvd.repo /etc/yum.repos.d/dvd.repo
4 RUN rpmdb --rebuilddb && yum install -y httpd openssh-server openssh-clients supervis or && yum clean all && ssh-keygen -q -t rsa -f /etc/ssh/ssh_host_rsa_key -N "" && ssh -keygen -q -t ecdsa -f /etc/ssh/ssh_host_ecdsa_key -N "" && ssh-keygen -q -t ed25519 -f /etc/ssh/ssh_host_ed25519_key -N "" && echo root:redhat | chpasswd
5 COPY supervisord.conf /etc/supervisord.conf
6 CMD ["/usr/sbin/supervisord"]
[root@foundation44 docker]# docker cp dvd.repo vm1:/etc/yum.repos.d/ #把yum源复制到默认目录下
#重新打开一个shell,测试yum源
[root@foundation44 ~]# docker run -it --name vm1 rhel7 bash
bash-4.2# ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
bash-4.2# cd /etc/yum.repos.d/
bash-4.2# ls
dvd.repo rhel7.repo
bash-4.2# yum repolist
Skipping unreadable repository '///etc/yum.repos.d/rhel7.repo'
docker | 2.9 kB 00:00
dvd | 4.1 kB 00:00
(1/3): docker/primary_db | 9.1 kB 00:00
(2/3): dvd/primary_db | 3.9 MB 00:00
(3/3): dvd/group_gz | 136 kB 00:00
repo id repo name status
docker docker 11
dvd dvd 4751
repolist: 4762
# 回到刚才的shell继续进行操作
[root@foundation44 docker]# vim supervisord.conf
1 [supervisord] #开启多个服务
2 nodaemon=true
3
4 [program:sshd] #运行sshd
5 command=/usr/sbin/sshd -D
6
7 [program:httpd] #运行httpd
8 command=/usr/sbin/httpd
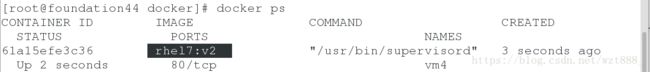
[root@foundation44 docker]# docker build -t rhel7:v2 /tmp/docker #执行脚本,构建镜像v2
Successfully built 3fe178f06b6e
[root@foundation44 docker]# docker run -d --name vm4 -v /tmp/docker/web:/var/www/html rhel7:v2 #挂载
3354cf9ae475d36ac68e298f4b9f2d2c69ed3335535fae70ef2acf271b283a5e
[root@foundation44 docker]# docker ps #查看挂载情况
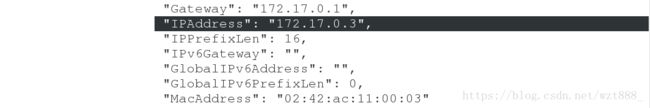
[root@foundation44 docker]# docker inspect vm4
"Gateway": "172.17.0.1",
"IPAddress": "172.17.0.3",
"IPPrefixLen": 16,
"IPv6Gateway": "",
"GlobalIPv6Address": "",
"GlobalIPv6PrefixLen": 0,
"MacAddress": "02:42:ac:11:00:03"
[root@foundation44 docker]# curl 172.17.0.3 # httpd部署成功
www.westos.org
www.westos.org
www.westos.org
www.westos.org
www.westos.org
www.westos.org
[root@foundation44 docker]# ssh -l root 172.17.0.3 #如果出现这种情况,按照提示操作即可
[root@foundation44 docker]# ssh -l root 172.17.0.3 # ssh部署成功
[email protected]'s password:
-bash-4.2# ls
anaconda-ks.cfg
-bash-4.2# yum install net-tools -y
-bash-4.2# netstat -antlp
![]()
RUN #运行容器
2.传参
区分CMD , ENTRYOINT ,RUN
容器启动时:
1.CMD,可以被覆盖,只能用一次
2.ENTRYOINT ,不可以被覆盖,CMD可以作为ENTRYOINT的内部参数进行传参
3.run 装包,运行;镜像之后跟命令会覆盖cmd
# 1.CMD
[root@foundation44 docker]# mkdir test
[root@foundation44 docker]# cd test/
[root@foundation44 test]# ls
[root@foundation44 test]# vim Dockerfile
1 FROM rhel7
2 CMD echo "hello world!!"
[root@foundation44 test]# docker build -t rhel7:v4 /tmp/docker/test
Sending build context to Docker daemon 2.048 kB
Step 1/2 : FROM rhel7
---> 0a3eb3fde7fd
Step 2/2 : CMD echo "hello world!!"
---> Running in a703e0ab164b
---> 374c56e16685
Removing intermediate container a703e0ab164b
Successfully built 374c56e16685
[root@foundation44 test]# docker run --rm rhel7:v4
hello world!!
[root@foundation44 test]# docker run --rm rhel7:v4 echo westos #被覆盖
westos
# 2.ENTRYOINT
[root@foundation44 test]# docker rmi rhel7:v4
Untagged: rhel7:v4
Deleted: sha256:374c56e1668565a40d17eed549e7317fdda5ddfb8e6f92d7278117083bfc8466
[root@foundation44 test]# vim Dockerfile
1 FROM rhel7
2 ENTRYPOINT echo "hello world!!"
[root@foundation44 test]# docker build -t rhel7:v4 .
Sending build context to Docker daemon 2.048 kB
Step 1/2 : FROM rhel7
---> 0a3eb3fde7fd
Step 2/2 : ENTRYPOINT echo "hello world!!"
---> Running in 1ead5bf5c1ee
---> e6f40aeb66c1
Removing intermediate container 1ead5bf5c1ee
Successfully built e6f40aeb66c1
[root@foundation44 test]# docker run --rm rhel7:v4
hello world!!
[root@foundation44 test]# docker run --rm rhel7:v4 echo westos #不会被覆盖
hello world!!
传参
两种传参方式
1.CMD(可以被覆盖)
2.shell的形式
# 1.CMD
[root@foundation44 test]# docker rmi rhel7:v4
Untagged: rhel7:v4
Deleted: sha256:e6f40aeb66c190f98fb5cd96b6c4a689271ea10af462984b2000bcf2f71b0
[root@foundation44 test]# vim Dockerfile
1 FROM rhel7
2 ENTRYPOINT ["/bin/echo", "hello"]
3 CMD ["world!"]
[root@foundation44 test]# docker build -t rhel7:v4 .
Sending build context to Docker daemon 2.048 kB
Step 1/3 : FROM rhel7
---> 0a3eb3fde7fd
Step 2/3 : ENTRYPOINT /bin/echo hello
---> Running in 0ccc2501a708
---> 32b041b67ea0
Removing intermediate container 0ccc2501a708
Step 3/3 : CMD world!
---> Running in 77d4400df12c
---> c5ff0c186624
Removing intermediate container 77d4400df12c
Successfully built c5ff0c186624
[root@foundation44 test]# docker run --rm rhel7:v4 #world!是调用CMD的传参
hello world!
[root@foundation44 test]# docker run --rm rhel7:v4 westos # world! 被westos覆盖
hello westos
# 2.shell的形式
[root@foundation44 test]# docker rmi rhel7:v4
Untagged: rhel7:v4
Deleted: sha256:c5ff0c18662440a61361579244e1033a4ddb4493c4f13ca52bb00f25d04b49ec
Deleted: sha256:32b041b67ea021f6b7e48069faf1ff44957796732c6a48715fd224b3e8ba4377
[root@foundation44 test]# vim Dockerfile
1 FROM rhel7
2 ENV name westos
3 ENTRYPOINT echo "hello $name"
3. 容器的安全机制
Privileged #true赋予所有权限
设置特权级运行的容器:--privileged=true
有的时候我们需要容器具备更多的权限,比如操作内核模块,控制 swap 交换分区,挂载
USB 磁盘,修改 MAC 地址等。
[root@foundation44 test]# docker run -it --name vm2 ubuntu
root@4d76704c488f:/# ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
root@4d76704c488f:/# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
12: eth0@if13: mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.3/16 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::42:acff:fe11:3/64 scope link
valid_lft forever preferred_lft forever
root@4d76704c488f:/# ip link set down eth0
RTNETLINK answers: Operation not permitted
root@db3b92742767:/# ip link set down eth0
RTNETLINK answers: Operation not permitted
[root@foundation44 test]# docker run -it --name vm3 --privileged=true ubuntu #赋予所有的权限,是以超户身份运行的
root@f77d8142bc8b:/# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
14: eth0@if15: mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.3/16 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::42:acff:fe11:3/64 scope link
valid_lft forever preferred_lft forever
root@f77d8142bc8b:/# ip link set down eth0
root@f77d8142bc8b:/# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
14: eth0@if15: mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.3/16 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::42:acff:fe11:3/64 scope link
valid_lft forever preferred_lft forever
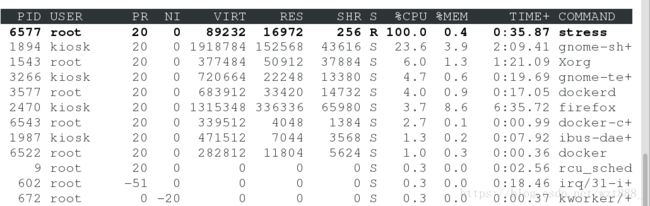
4.做压测,设置允许容器占用的内存大小和swap分区大小
stress #做压测
momory #控制内存
--vm 1 #开启多少个线程去吃内存,1 表示一个
交换分区的大小一般是物理分区的2倍
(1)内存占用的测试:
[root@foundation44 test]# docker rm -f `docker ps -aq`
f77d8142bc8b
4d76704c488f
c0ee54b33346
[root@foundation44 test]# docker ps -f status=exited #查看没有运行但是存在的容器
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3354cf9ae475 rhel7:v2 "/usr/bin/supervisord" 2 hours ago Exited (255) 11 minutes ago 80/tcp vm4
6cda812453fd rhel7 "bash" 3 hours ago Exited (255) 11 minutes ago vm1
db59ec377fa8 nginx "bash" 3 hours ago Exited (130) 3 hours ago vm2
[root@foundation44 ~]# cd /var/www/html/images/
[root@foundation44 images]# ls
game2048.tar nginx.tar rhel7.tar stress.tar
[root@foundation44 images]# docker load -i stress.tar
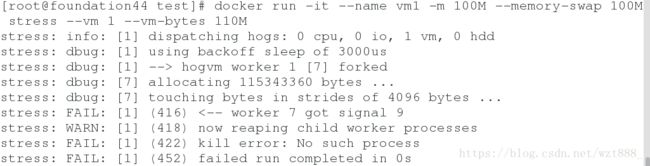
[root@foundation44 test]# docker run -it --name vm1 -m 100M --memory-swap 100M stress --vm 1 --vm-bytes 110M # 设置提供和给vm1的内存大小为100M,内存加交换分区的大小为100M,则能处理的最大压测也是100M,超出100M就会失败
[root@foundation44 test]# docker run --rm -it --name vm1 -m 100M --memory-swap 100M stress --vm 1 --vm-bytes 80M #未超出100M就会成功
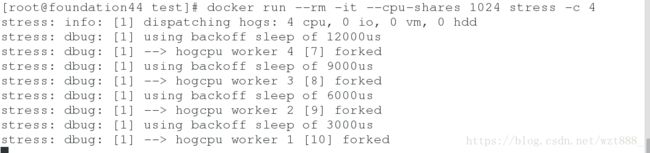
(2)cpu的测试,1024比512的优先级高:
[root@foundation44 test]# free -m
total used free shared buff/cache available
Mem: 3834 985 865 259 1984 2261
Swap: 3839 0 3839
[root@foundation44 test]# lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
CPU(s): 4 #查看到cpu是4个
### 测试时候需要打开三个shell,两个运行,一个监控,都不能退出去
[root@foundation44 test]# docker run --rm -it --cpu-shares 512 stress -c 4 #必须占满才能看出效果
[root@foundation44 test]# docker run --rm -it --cpu-shares 1024 stress -c 4
1024是512的2倍
3.区分pause 与 stop
[root@foundation44 test]# docker run -it --name vm1 ubuntu
root@c267d104277e:/# [root@foundation44 test]# # ctrl + p q
[root@foundation44 test]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c267d104277e ubuntu "/bin/bash" 25 seconds ago Up 24 seconds vm1
- pause
[root@foundation44 test]# docker container pause vm1
vm1
[root@foundation44 test]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c267d104277e ubuntu "/bin/bash" About a minute ago Up About a minute (Paused) vm1
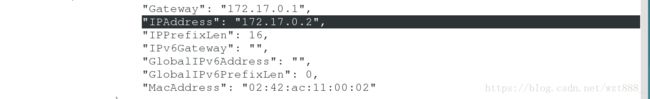
[root@foundation44 test]# docker inspect vm1 # ip还在
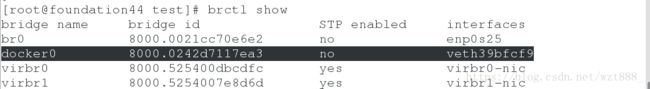
[root@foundation44 test]# brctl show #桥接也在
[root@foundation44 test]# docker container unpause vm1 #开启vm1
vm1
[root@foundation44 test]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c267d104277e ubuntu "/bin/bash" 5 minutes ago Up 5 minutes vm1
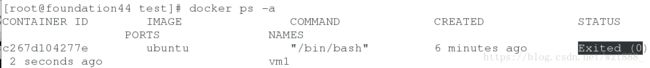
[root@foundation44 test]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c267d104277e ubuntu "/bin/bash" 5 minutes ago Up 5 minutes vm1
- stop
[root@foundation44 test]# docker stop vm1
vm1
[root@foundation44 test]# docker ps -a # 状态已变
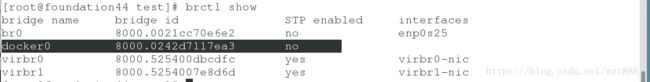
[root@foundation44 test]# brctl show #桥接也不见了
bridge name bridge id STP enabled interfaces
br0 8000.0021cc70e6e2 no enp0s25
docker0 8000.0242d7117ea3 no
virbr0 8000.525400dbcdfc yes virbr0-nic
virbr1 8000.5254007e8d6d yes virbr1-nic
[root@foundation44 test]# docker inspect vm1 # ip也查看不到
5.利用cgroup对docker做权限限制(用虚拟机进行测试)
Linux Cgroup(Control Groups)是Linux内核提供的用于限制、记录、隔离进程组可以使用的资源(cpu、memory、IO等)的一种机制。
cgroup # 控制组
容器分很多种
runc # jdk底层容器
docker engine #引擎
free -m #企业7中查看内存大小的命令
# 安装cgroup管理工具
[root@server1 ~]# yum search cgroup

[root@server1 ~]# yum install libcgroup.x86_64 -y
[root@server1 ~]# cd /cgroup/ #生成了这个目录代表安装成功
[root@server1 cgroup]# ls
[root@server1 cgroup]# /etc/init.d/cgconfig start
(1)对mem内存的限制
[root@server1 shm]# bc # bc命令是一种支持任意精度的交互执行的计算器语言。
bc 1.06.95
Copyright 1991-1994, 1997, 1998, 2000, 2004, 2006 Free Software Foundation, Inc.
This is free software with ABSOLUTELY NO WARRANTY.
For details type `warranty'.
200*1024*1024
209715200
[root@server1 cgroup]# cd memory/
[root@server1 memory]# vim /etc/cgconfig.conf
28 group x1 {
29 memory {
30 memory.limit_in_bytes = 209715200; # 限制使用的最大内存数
31 }
[root@server1 ~]# /etc/init.d/cgconfig restart #重启服务必须在路径之外,因为是挂载的方式
[root@server1 ~]# cd /cgroup/memory/x1/
[root@server1 x1]# cat memory.limit_in_bytes
209715200
[root@server1 x1]# cd /dev/shm/
[root@server1 shm]# ls
[root@server1 shm]# free -m
[root@server1 shm]# dd if=/dev/zero of=file2 bs=1M count=100
[root@server1 shm]# free -m
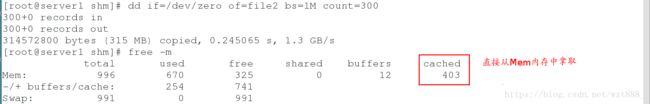
[root@server1 shm]# dd if=/dev/zero of=file2 bs=1M count=300
[root@server1 shm]# free -m
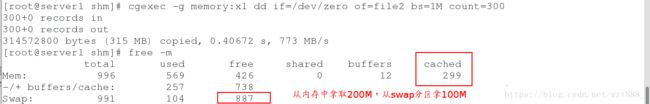
[root@server1 shm]# cgexec -g memory:x1 dd if=/dev/zero of=file2 bs=1M count=300 #cgexec是直接在某些子系统中的指定控制组运行的程序, memory:x1 是被指定的程序
[root@server1 shm]# free -m
(2)对资源的限制
[root@server1 memory]# cd
[root@server1 ~]# vim /etc/cgconfig.conf
28 group x1 {
29 memory {
30 memory.limit_in_bytes = 209715200; # 限制使用的最大内存数
31 memory.memsw.limit_in_bytes = 209715200; # 限制内存和交换分区的大小之和
32 }
33 }
[root@server1 ~]# /etc/init.d/cgconfig restart
[root@server1 ~]# cd /dev/shm/
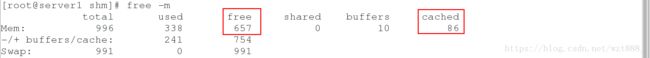
[root@server1 shm]# free -m
total used free shared buffers cached
Mem: 996 484 511 0 30 197
-/+ buffers/cache: 256 740
Swap: 991 0 991
[root@server1 shm]# cgexec -g memory:x1 dd if=/dev/zero of=file2 bs=1M count=190 #没有超过200M,可以进行截取
[root@server1 shm]# rm -fr file2
[root@server1 shm]# cgexec -g memory:x1 dd if=/dev/zero of=file2 bs=1M count=300 #超过200M,所以被拒绝,进程直接被杀死
Killed
[root@server1 ~]# ls
memapp2 memapp1
[root@server1 ~]# chmod +x memapp*
[root@server1 ~]# ./memapp1 #执行脚本时,发现有依赖性
-bash: ./memapp1: /lib/ld-linux.so.2: bad ELF interpreter: No such file or directory
[root@server1 ~]# yum install -y /lib/ld-linux.so.2
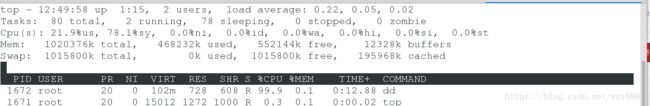
[root@server1 ~]# ./memapp1 #因为是超级用户,所以不会受到限制,不管多大都可以截取成功
Process ID is: 8774
Grabbing 4096 pages of memory #一个内存页为 4k
Success!
Press any key to exit
[root@server1 ~]# ./memapp2
Process ID is: 8775
Grabbing 8192 pages of memory
Success!
Press any key to exit
[root@server1 ~]# bc
bc 1.06.95
Copyright 1991-1994, 1997, 1998, 2000, 2004, 2006 Free Software Foundation, Inc.
This is free software with ABSOLUTELY NO WARRANTY.
For details type `warranty'.
5000*4*1024
20480000
[root@server1 ~]# vim /etc/cgconfig.conf
28 group x1 {
29 memory {
30 memory.limit_in_bytes = 20480000;
31 memory.memsw.limit_in_bytes = 20480000;
32 }
我们用普通用户来进行测试
[root@server1 ~]# useradd wzt
[root@server1 ~]# su - wzt
[wzt@server1 ~]$ cd /dev/shm/
[wzt@server1 shm]$ ls
file2
[wzt@server1 shm]$ rm -fr file2
[wzt@server1 shm]$ logout
[root@server1 ~]# cd /dev/shm/
[root@server1 shm]# ls
file2
[root@server1 shm]# rm -fr file2
[root@server1 shm]# ls
[root@server1 shm]# su - wzt
[wzt@server1 ~]$ cd /dev/shm/
[wzt@server1 shm]$ ls
[wzt@server1 shm]$ dd if=/dev/zero of=file2 bs=1M count=300
[wzt@server1 shm]$ ls
file2
[wzt@server1 shm]$ rm -fr file2
[wzt@server1 shm]$ logout
[root@server1 shm]# vim /etc/cgrules.conf #编辑文件,使普通用户调用 x1规则,
12 wzt:memapp1 memory x1/
13 wzt:memapp2 memory x1/
[root@server1 shm]# /etc/init.d/cgred start
[root@server1 shm]# cd
[root@server1 ~]# mv memapp* /home/wzt
[root@server1 ~]# su - wzt
[wzt@server1 ~]$ ls
memapp1 memapp2
[wzt@server1 ~]$ ./memapp1 #可以执行成功
Process ID is: 8907
Grabbing 4096 pages of memory
# 4096*4*1024=16777216 < 20480000
Success!
Press any key to exit
[wzt@server1 ~]$ ./memapp2 #不能执行成功
Process ID is: 8908
Grabbing 8192 pages of memory
# 8192*4*1024= 33554432 > 20480000
Killed
[wzt@server1 ~]$ logout
(3)cpu
[root@server1 ~]# cd /cgroup/
[root@server1 cgroup]# ls
blkio cpu cpuacct cpuset devices freezer memory net_cls
[root@server1 cgroup]# cd cpu
[root@server1 cpu]# ls
cgroup.event_control cpu.cfs_quota_us cpu.shares release_agent
cgroup.procs cpu.rt_period_us cpu.stat tasks
cpu.cfs_period_us cpu.rt_runtime_us notify_on_release
[root@server1 cpu]# pwd
/cgroup/cpu
[root@server1 cpu]# cat cpu.shares
1024
[root@server1 cpu]# cd
[root@server1 ~]# vim /etc/cgconfig.conf
34 group x2 {
35 cpu {
36 cpu.shares =100;
# 在cpu.shares文件中,可以对进程调度程序所处理的进程组设置CPU时间
分配的比重。通过修改这个值,就可以在分组间调整CPU时间的比例。默认
值为1024
37 }
[root@server1 ~]# /etc/init.d/cgconfig restart
[root@server1 ~]# cgexec -g cpu:x2 dd if=/dev/zero of=/dev/null &
[1] 8931
[root@server1 ~]# lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
CPU(s): 1 #只有一个cpu
[root@server1 ~]# cd /sys/
[root@server1 sys]# ls
block bus class dev devices firmware fs hypervisor kernel module power
[root@server1 sys]# cd devices/
[root@server1 devices]# ls
LNXSYSTM:00 platform software tracepoint virtual
pci0000:00 pnp0 system uncore_cbox
[root@server1 devices]# cd system/
[root@server1 system]# ls
clocksource i8237 ioapic lapic memory timekeeping
cpu i8259 irqrouter machinecheck node
[root@server1 system]# cd cpu/
[root@server1 cpu]# ls #由于虚拟机只有一个CPU,所以不可以查看CPU0,cpu0也不可改动
cpu0 cpufreq cpuidle kernel_max offline online possible present
(4)磁盘(io)空间读写的速度限制
[root@server1 ~]# cd /cgroup/blkio/
[root@server1 blkio]# vim /etc/cgconfig.conf
40 group x3 {
41 blkio{
42 blkio.throttle.read_bps_device = "252:0 1000000"; # 252:0是/dev/vda这个块设备的信息
43 }
[root@server1 blkio]# cd
[root@server1 ~]# /etc/init.d/cgconfig restart
[root@server1 ~]# cd /cgroup/blkio/
[root@server1 blkio]# ls
blkio.io_merged blkio.throttle.io_service_bytes blkio.weight_device
blkio.io_queued blkio.throttle.io_serviced cgroup.event_control
blkio.io_service_bytes blkio.throttle.read_bps_device cgroup.procs
blkio.io_serviced blkio.throttle.read_iops_device notify_on_release
blkio.io_service_time blkio.throttle.write_bps_device release_agent
blkio.io_wait_time blkio.throttle.write_iops_device tasks
blkio.reset_stats blkio.time x3
blkio.sectors blkio.weight
[root@server1 blkio]# cd x3/
[root@server1 x3]# ls
blkio.io_merged blkio.sectors blkio.time
blkio.io_queued blkio.throttle.io_service_bytes blkio.weight
blkio.io_service_bytes blkio.throttle.io_serviced blkio.weight_device
blkio.io_serviced blkio.throttle.read_bps_device cgroup.event_control
blkio.io_service_time blkio.throttle.read_iops_device cgroup.procs
blkio.io_wait_time blkio.throttle.write_bps_device notify_on_release
blkio.reset_stats blkio.throttle.write_iops_device tasks
[root@server1 x3]# cat blkio.throttle.read_bps_device
252:0 1000000
[root@server1 x3]# yum install iotop -y
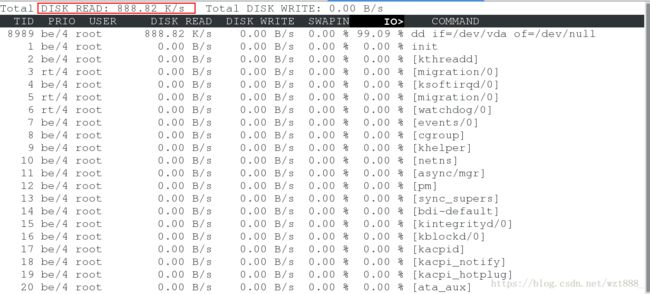
[root@server1 ~]# cgexec -g blkio:x3 dd if=/dev/vda of=/dev/null &
[1] 8989
[root@server1 ~]# iotop
(5)使用–privileged=true参数给容器内设置权限:
[root@server1 ~]# vim /etc/cgconfig.conf
45 group x4 {
46 freezer {}
47
48 }
[root@server1 ~]# /etc/init.d/cgconfig restart
Stopping cgconfig service: [ OK ]
Starting cgconfig service: [ OK ]
[root@foundation44 Desktop]# docker run --rm -it --device-read-bps /dev/sda:1M --privileged ubuntu
root@f554af227afc:/# fdiskl
bash: fdiskl: command not found
root@f554af227afc:/# fdisk -l
Disk /dev/sda: 320.1 GB, 320072933376 bytes
255 heads, 63 sectors/track, 38913 cylinders, total 625142448 sectors
Units = sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk identifier: 0x00009e67
Device Boot Start End Blocks Id System
/dev/sda1 * 2048 2099199 1048576 83 Linux
/dev/sda2 2099200 625141759 311521280 8e Linux LVM
root@f554af227afc:/# dd if=/dev/sda of=/dev/null bs=1M count=2
2+0 records in
2+0 records out
2097152 bytes (2.1 MB) copied, 2.0455 s, 1.0 MB/s
root@f554af227afc:/# dd if=/dev/sda of=/dev/null bs=1M count=1
1+0 records in
1+0 records out
1048576 bytes (1.0 MB) copied, 0.000582921 s, 1.8 GB/s
root@f554af227afc:/# cd /dev/
root@f554af227afc:/dev# ls -l /dev/null
crw-rw-rw- 1 root root 1, 3 Aug 21 10:42 /dev/null
root@f554af227afc:/dev# dd if=/dev/sda of=file bs=1M count=10 oflag=direct
dd: failed to open 'file': Invalid argument
root@f554af227afc:/dev# dd if=/dev/sda of=file3 bs=1M count=10 oflag=direct
dd: failed to open 'file3': Invalid argument
root@f554af227afc:/dev# cd
root@f554af227afc:~# dd if=/dev/sda of=file3 bs=1M count=10 oflag=direct10+0 records in
10+0 records out
10485760 bytes (10 MB) copied, 4.01672 s, 2.6 MB/s
# 4.freezer子系统
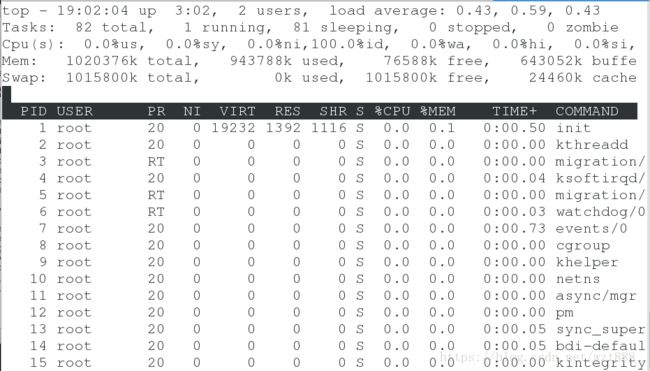
[root@server1 x4]# dd if=/dev/zero of=/dev/null &
[1] 9008
[root@server1 ~]# top #使用截取命令后,系统的CPU立即被消耗至大致百分之百

在这种情况发生的时候,我们不能立即kill掉该进程,因为它可能和别的 进程共同占用某种资源,如果现在是它在使用资源,一旦kill,它会将资源释放,影响别的进程,最好的解决办法是:我们将该进程“冰冻”,观察其是否对别的进程有影响,再加以决定
[root@server1 x4]# ps ax
[root@server1 x4]# ls
cgroup.event_control freezer.state tasks
cgroup.procs notify_on_release
[root@server1 x4]# echo 9008 > tasks
[root@server1 x4]# cat freezer.state
THAWED
[root@server1 x4]# echo FROZEN > freezer.state
[root@server1 x4]# cat freezer.state
FROZEN
[root@server1 ~]# top
[root@server1 x4]# killall dd # 将后台运行的dd服务关闭
[root@server1 x4]# cd
[root@server1 ~]# poweroff
6.认识文件的命名方式
[root@foundation44 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@foundation44 ~]# docker run -it --name vm1 ubuntu
root@560710a8abe5:/# [root@foundation44 ~]#
[root@foundation44 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
560710a8abe5 ubuntu "/bin/bash" 10 seconds ago Up 9 seconds vm1
[root@foundation44 ~]# docker inspect vm1 | grep Pid
"Pid": 16004,
"PidMode": "",
"PidsLimit": 0,
[root@foundation44 ~]# cd /proc/16004
[root@foundation44 16004]# ls
attr cpuset limits net projid_map stat
autogroup cwd loginuid ns root statm
auxv environ map_files numa_maps sched status
cgroup exe maps oom_adj schedstat syscall
clear_refs fd mem oom_score sessionid task
cmdline fdinfo mountinfo oom_score_adj setgroups timers
comm gid_map mounts pagemap smaps uid_map
coredump_filter io mountstats personality stack wchan
[root@foundation44 16004]# cd ns
[root@foundation44 ns]# ll
total 0
lrwxrwxrwx 1 root root 0 Aug 23 15:42 ipc -> ipc:[4026532503]
lrwxrwxrwx 1 root root 0 Aug 23 15:42 mnt -> mnt:[4026532501]
lrwxrwxrwx 1 root root 0 Aug 23 15:42 net -> net:[4026532507]
lrwxrwxrwx 1 root root 0 Aug 23 15:42 pid -> pid:[4026532505]
lrwxrwxrwx 1 root root 0 Aug 23 15:42 user -> user:[4026531837]
lrwxrwxrwx 1 root root 0 Aug 23 15:42 uts -> uts:[4026532502]