01Editor最新破解
文章目录
- 01Editor最新版注册算法逆向
-
- 1.定位注册算法代码
- 2.整体注册算法
- 3.Check1算法分析
- 4.Check2算法分析
- 5.获得正确的任意用户名对应的序列号
01Editor最新版注册算法逆向
1.定位注册算法代码
【版本】 13.0.1 64 b i t \textcolor{green}{【版本】13.0.1\ 64bit} 【版本】13.0.1 64bit
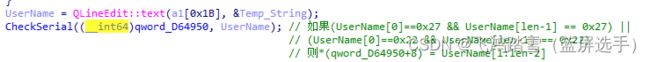
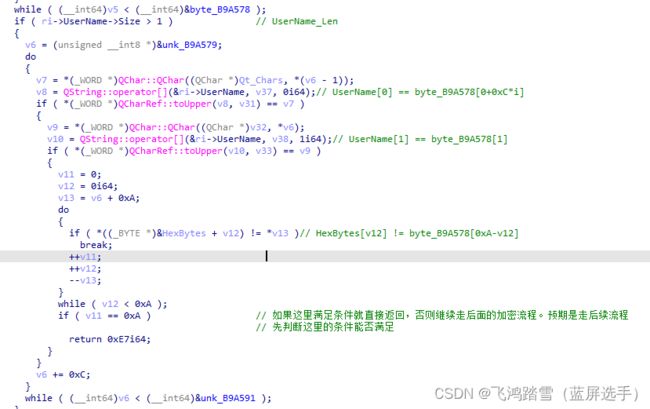
注册的提示信息还有界面的提示信息很丰富,这为我们定位关键代码提供了充分的线索。将01Editor拖入IDA分析,直接字符串搜索“Thank you for purchasing 010 Editor!”就来到了关键位置( R V A = 0 x 210520 \textcolor{orange}{RVA = 0x210520} RVA=0x210520)。
2.整体注册算法
- 判断序列号是否包含空格,有空格就是非法的序列号
- 判断序列号格式是否符合XXXX-XXXX-XXXX-XXXX
- 对序列号进行简单的字符替换
-
进入序列号和用户名加密运算验证(*重点部分,后面再说。这里用 C h e c k 1 \textcolor{cornflowerblue}{Check1} Check1代替),会返回一个结果,这里用rs1代替。
-
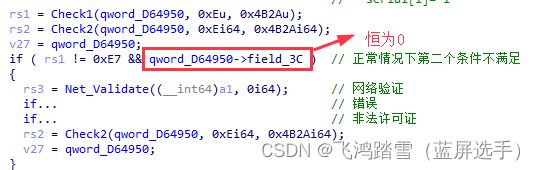
进入第二处验证,用 C h e c k 2 \textcolor{cornflowerblue}{Check2} Check2代替,返回结果用rs2代替。
-
网络验证。发现最新版没有走网络验证。。。。因为有处条件永不满足
- 用rs1和rs2作为注册的最终结果进行反馈,可以确定 r s 2 = = 0 x D B \textcolor{orange}{rs2 == 0xDB} rs2==0xDB就是我们期望的结果
3.Check1算法分析
-
先判断用户名和序列号的长度均不为0才能往下验证,否则直接返回0x93。
-
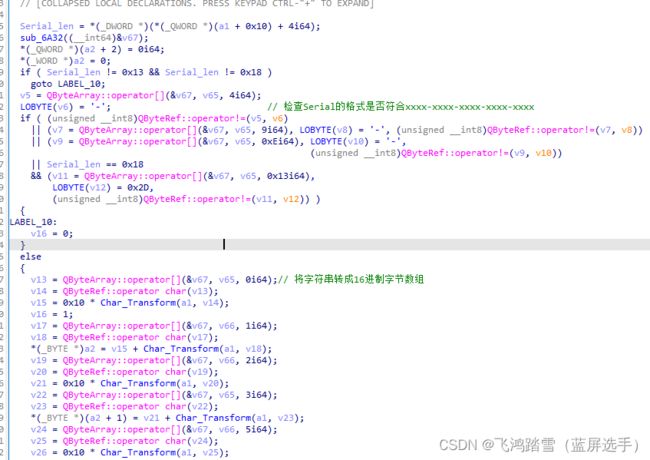
再次检查序列号格式,并按照自定义方法将序列号转成16进制的字节数组
-
序列号的长度分为两种0x13和0x18。
-
转换结果用hb代称,hb中的每一个元素都是 serial 中除 ‘-’ 元素外的两两元素组合而成。 C h a r _ T r a n s F o r m \textcolor{cornflowerblue}{Char\_TransForm} Char_TransForm实现:
-
__int64 __fastcall Jmp_CharTransForm(__int64 a1, char a2) { if ( (unsigned __int8)(a2 - 0x30) <= 9u ) return (unsigned int)(a2 - 0x30); if ( ((a2 - 'O') & 0xDF) == 0 ) // 只有a2 == 'O' 才满足,但是前面预处理的时候将'O'换成了0, // 因此这里永不满足。 return 0i64; if ( a2 == 'l' ) return 1i64; if ( (unsigned __int8)(a2 - 'a') <= 0x19u ) return a2 - (unsigned int)'W'; if ( (unsigned __int8)(a2 - 'A') <= 0x19u ) return a2 - (unsigned int)'7'; else return 0i64; }注意:这个函数是多对一的,所以这个函数的反函数就成了一对多。例如原函数输入一个‘ l ’或者‘ 1 ’,输出都是 1 ,反函数输入一个 1 ,输出可以任选‘ l ’和‘ 1 ’其一。 \textcolor{BrickRed}{注意:这个函数是多对一的,所以这个函数的反函数就成了一对多。例如原函数输入一个‘l’或者‘1’,输出都是1,反函数输入一个1,输出可以任选‘l’和‘1’其一。} 注意:这个函数是多对一的,所以这个函数的反函数就成了一对多。例如原函数输入一个‘l’或者‘1’,输出都是1,反函数输入一个1,输出可以任选‘l’和‘1’其一。
要对其进行求逆 R e C h a r T o B y t e \textcolor{cornflowerblue}{ReCharToByte} ReCharToByte,可以写成如下形式:
char ReCharToByte(unsigned char chr) { if (chr > 1 && chr <= 9) return chr + 0x30; if (chr == 0) { // 原输入有3种情况,这里随机选一种 switch (rand() % 3) { case 0:return chr + 0x30; case 1:return 'O'; case 2:return 'o'; } } if (chr == 1) { switch (rand() % 2) { case 0:return chr + 0x30; case 1:return 'l'; } } // 其余情况就是原本的输入是字母a-z/A-Z if (chr + '7' <= 'Z') return chr + '7'; return chr + 'W'; }
- 如果 U s e r N a m e [ 0 ] = = ‘ C ’ \textcolor{orange}{UserName[0] == ‘C’} UserName[0]==‘C’ ,且 U s e r N a m e [ 1 ] = = ‘ O ’ \textcolor{orange}{UserName[1] == ‘O’} UserName[1]==‘O’,则serial不能全等于某一个字符数组(byte_B9A578)前0xA个元素的倒序;如果 U s e r N a m e [ 0 ] = = ‘ J ’ \textcolor{orange}{UserName[0] == ‘J’} UserName[0]==‘J’ ,且 U s e r N a m e [ 1 ] = = ‘ U ’ \textcolor{orange}{UserName[1] == ‘U’} UserName[1]==‘U’,则serial不能全等于 b y t e B 9 A 578 + 0 x C \textcolor{orange}{byte_B9A578+0xC} byteB9A578+0xC前0xA个元素的倒序。
实际这个位置的校验没多大用处。 \textcolor{green}{实际这个位置的校验没多大用处。} 实际这个位置的校验没多大用处。
-
根据 h b [ 3 ] \textcolor{orange}{hb[3]} hb[3]的取值,分三种处理情况:
switch ( BYTE3(HexBytes) ) // HexBytes[3] { case 0x9C: v19 = (unsigned __int8)(BYTE5(HexBytes) ^ BYTE2(HexBytes))// HexBytes[5] ^ HexBytes[2] + ((unsigned __int8)(HIBYTE(HexBytes) ^ BYTE1(HexBytes)) << 8);// (HexBytes[1] ^ HexBytes[7]) << 8 ri->X1 = (unsigned __int8)Xor_1((unsigned __int8)(BYTE6(HexBytes) ^ (unsigned __int8)HexBytes));// ((a1 ^ 0x18) + 0x3D) ^ 0xA7 v20 = (unsigned __int16)Calc_1(v19); ri->X2 = (unsigned __int16)v20; X1 = ri->X1; if ( X1 && (unsigned int)(v20 - 1) <= 0x3E7 ) { v22 = 0; if ( X1 < 2 ) v22 = ri->X1; End: QString::toUtf8(&ri->UserName, v36); // UserName LOBYTE(v4) = v18 != (char)0xFC; v24 = QByteArray::data((QByteArray *)v36); v25 = Calc_2((__int64)v24, v4, v22, (unsigned int)ri->X2); if ( BYTE4(HexBytes) == (_BYTE)v25 && (_BYTE)v14 == BYTE1(v25) && BYTE6(HexBytes) == BYTE2(v25) && HIBYTE(HexBytes) == HIBYTE(v25) ) { if ( v18 == (char)0x9C ) { if ( v34 > ri->X1 ) { v26 = 0x4E; LABEL_41: QByteArray::~QByteArray((QByteArray *)v36); return v26; } LABEL_33: v26 = 0x2D; goto LABEL_41; } if ( v18 == (char)0xFC ) { v27 = Calc_3((unsigned __int8)HexBytes + (BYTE1(HexBytes) << 8) + (BYTE2(HexBytes) << 0x10), v25); if ( v27 ) { ri->X0 = v27; v26 = 0x93; goto LABEL_41; } } else if ( v29 ) { if ( v35 > v29 ) { v26 = 0x4E; goto LABEL_41; } goto LABEL_33; } } v26 = 0xE7; goto LABEL_41; } break; case 0xFC: v22 = 0xFF; ri->X1 = 0xFF; ri->X2 = 1; ri->field_40 = 1; goto End; case 0xAC: ri->X1 = 2; v23 = Calc_1((unsigned __int16)((unsigned __int8)(v14 ^ v15) + ((unsigned __int8)(HIBYTE(HexBytes) ^ v16) << 8))); ri->X2 = v23; if ( (unsigned int)v23 - 1 <= 0x3E7 ) { v29 = Calc_3( (BYTE6(HexBytes) ^ v17) + ((v14 ^ HexBytes_Off_9) << 0x10) + ((HexBytes_Off_8 ^ (unsigned int)BYTE4(HexBytes)) << 8), 0x5B8C27i64); ri->field_44 = v29; v22 = v29; goto End; } break; } return 0xE7i64; } return 0x93i64; }由于编译器优化,这部分代码可读性比较差,手动分析整理之后得到伪代码:
/* Check1后部分的逻辑 */ if(len(UserName)==0 || len(Serial) == 0) return 0x93; v29 = 0; // case 0x9C: v19 = (hb[5] ^ hb[2]) + ((hb[1] ^ hb[7])<<8); v21 = Xor_1(hb[6] ^ hb[0]); // v21 v20 = Calc_1(v19); // if(v21 && (v20-1) <= 999) { v22 = 0; if(v21 < 2) v22 = v21; v25 = Calc_2(UserName, True, v22, v20); // v25 是4字节长度 if(hb[4] == v25[0] && hb[5] == v25[1] && hb[6] == v25[2] && hb[7] == v25[3]) { if(0xE > v21) return 0x4E; return 0x2D; } } return 0xE7; //case 0xFC: v25 = Calc_2(UserName, False, 0xFF, 1); // v25 是4字节长度 if(hb[4] == v25[0] && hb[5] == v25[1] && hb[6] == v25[2] && hb[7] == v25[3]) { v27 = Calc_3(hb[0] + (hb[1] << 8) + (hb[2] << 0x10), v25); if(v27) { *(_DWORD *)(a1 + 0x28) = v27; return 0x93; } } return 0xE7; //case 0xAC: v23 = Calc_1((hb[5] ^ hb[2]) + ((hb[7] ^ hb[1]) << 8)); if ( (unsigned int)v23 - 1 <= 0x3E7 ) { v29 = Calc_3( (hb[6] ^ hb[0]) + ((hb[5] ^ v41) << 0x10) + ((v40 ^ hb[4]) << 8), 0x5B8C27); v25 = Calc_2(UserName, False, v29, v23); // v25 是4字节长度 if(hb[4] == v25[0] && hb[5] == v25[1] && hb[6] == v25[2] && hb[7] == v25[3]) { if(v29) { if(0x4B2>v29) return 0x4E; } } } return 0xE7;其中有几个函数需要关注:
-
X o r _ 1 \textcolor{cornflowerblue}{Xor\_1} Xor_1
-
char __fastcall sub_36D330(char a1) { return ((a1 ^ 0x18) + 0x3D) ^ 0xA7; } -
这个函数可逆,单射。逆函数 R e X o r _ 1 \textcolor{cornflowerblue}{ReXor\_1} ReXor_1
-
return ((a1 ^ 0xA7) - 0x3D) ^ 0x18;
-
-
-
C a l c _ 1 \textcolor{cornflowerblue}{Calc\_1} Calc_1
-
__int64 __fastcall sub_36D2A0(__int16 a1) { unsigned int v1; // r8d v1 = (unsigned __int16)((a1 ^ 0x7892) + 0x4D30) ^ 0x3421; if ( v1 % 0xB ) return 0i64; else return (unsigned __int16)(v1 / 0xB); } -
此函数条件为真的分支存在多对1情况,导致逆函数不能保证得到正确的原函数输入,而原函数的输入在后面验证的时候还需要用到。因此,这个函数的逆函数没有意义。
-
-
C a l c _ 2 \textcolor{cornflowerblue}{Calc\_2} Calc_2
-
__int64 __fastcall sub_36D380(BYTE *UserName, int a2, char a3, __int64 a4) { ... v5 = 0; if ( len_username > 0 ) { i = 0i64; v9 = 0; v10 = 0xF * a4; v11 = 0; v12 = 0x11 * a3; do { v13 = toupper(UserName[i]); v14 = &g_Box[v12]; v15 = v5 + g_Box[v13]; v16 = &g_Box[v10]; if ( a2 ) { v17 = g_Box[(unsigned __int8)(v13 + 0xD)]; v18 = (unsigned __int8)(v13 + 0x2F); v19 = v9; } else { v17 = g_Box[(unsigned __int8)(v13 + 0x3F)]; v18 = (unsigned __int8)(v13 + 0x17); v19 = v11; } v12 += 9; v10 += 13; v9 += 19; v11 += 7; ++i; v5 = *v16 + *v14 + g_Box[v19] + g_Box[v18] * (v15 ^ v17); } while ( i < len_username ); } return v5; }此函数是将UserName编码,记为ans,用来和序列号某个部分进行对比的,所以该函数也不用求逆。
-
-
4.Check2算法分析
这部分校验只要返回0xDB,就表示注册成功了,这就要求Check1返回0x2D,所以重点还是在Check1。
以上就是所有注册算法流程,接下来考虑如何获得正确的任意用户名的序列号。
5.获得正确的任意用户名对应的序列号
我们期望Check1返回0x2D。通过分析,得知只有一条路径可以返回,即 h b [ 3 ] = = 0 x 9 C \textcolor{orange}{hb[3]\ ==\ 0x9C} hb[3] == 0x9C时,满足:
v19 = (hb[5] ^ hb[2]) + ((hb[1] ^ hb[7])<<8);
v20 = Calc_1(v19);
v20 - 1 < 999;
v25 = Calc_2(user, true, 0, v20);
char* a1 = reinterpret_cast(&v25);
hb[4] == a1[0] && hb[5] == a1[1] && hb[6] == a1[2] && hb[7] == a1[3]
Xor_1(hb[6] ^ hb[0]) > 0xE
从条件约束中发现,其实serial长度应该是20。我们可以先枚举hb下标为1,2,5,7对应的元素,这样枚举空间就在 25 6 4 = 4294967296 \textcolor{orange}{256^4\ =\ 4294967296} 2564 = 4294967296内,还能接受。在满足条件3、6和7,就能确定hb中的所有元素,然后反求得serial。
综合以上条件得到注册机的代码:
unsigned char g_Data[24] = { 0x43,0x4f,0x57,0xd6,0x30,0xe3,0xca,0xb9,0xac,0xab,0xa1,0xc4,0x4a,0x55,0x59,0x2a,0x35,0xe2,0xc4,0x65,0xac,0xd3,0xa4,0xcb };
unsigned int g_Box[308] = { 0x39cb44b8,0x23754f67,0x5f017211,0x3ebb24da,0x351707c6,0x63f9774b,0x17827288,0xfe74821,0x5b5f670f,0x48315ae8,0x785b7769,0x2b7a1547,0x38d11292,0x42a11b32,0x35332244,0x77437b60,0x1eab3b10,0x53810000,0x1d0212ae,0x6f0377a8,0x43c03092,0x2d3c0a8e,0x62950cbf,0x30f06ffa,0x34f710e0,0x28f417fb,0x350d2f95,0x5a361d5a,0x15cc060b,0xafd13cc,0x28603bcf,0x3371066b,0x30cd14e4,0x175d3a67,0x6dd66a13,0x2d3409f9,0x581e7b82,0x76526b99,0x5c8d5188,0x2c857971,0x15f51fc0,0x68cc0d11,0x49f55e5c,0x275e4364,0x2d1e0dbc,0x4cee7ce3,0x32555840,0x112e2e08,0x6978065a,0x72921406,0x314578e7,0x175621b7,0x40771dbf,0x3fc238d6,0x4a31128a,0x2dad036e,0x41a069d6,0x25400192,0xdd4667,0x6afc1f4f,0x571040ce,0x62fe66df,0x41db4b3e,0x3582231f,0x55f6079a,0x1ca70644,0x1b1643d2,0x3f7228c9,0x5f141070,0x3e1474ab,0x444b256e,0x537050d9,0xf42094b,0x2fd820e6,0x778b2e5e,0x71176d02,0x7fea7a69,0x5bb54628,0x19ba6c71,0x39763a99,0x178d54cd,0x1246e88,0x3313537e,0x2b8e2d17,0x2a3d10be,0x59d10582,0x37a163db,0x30d6489a,0x6a215c46,0xe1c7a76,0x1fc760e7,0x79b80c65,0x27f459b4,0x799a7326,0x50ba1782,0x2a116d5c,0x63866e1b,0x3f920e3c,0x55023490,0x55b56089,0x2c391fd1,0x2f8035c2,0x64fd2b7a,0x4ce8759a,0x518504f0,0x799501a8,0x3f5b2cad,0x38e60160,0x637641d8,0x33352a42,0x51a22c19,0x85c5851,0x32917ab,0x2b770ac7,0x30ac77b3,0x2bec1907,0x35202d0,0xfa933d3,0x61255df3,0x22ad06bf,0x58b86971,0x5fca0de5,0x700d6456,0x56a973db,0x5ab759fd,0x330e0be2,0x5b3c0ddd,0x495d3c60,0x53bd59a6,0x4c5e6d91,0x49d9318d,0x103d5079,0x61ce42e3,0x7ed5121d,0x14e160ed,0x212d4ef2,0x270133f0,0x62435a96,0x1fa75e8b,0x6f092fbe,0x4a000d49,0x57ae1c70,0x4e2477,0x561e7e72,0x468c0033,0x5dcc2402,0x78507ac6,0x58af24c7,0xdf62d34,0x358a4708,0x3cfb1e11,0x2b71451c,0x77a75295,0x56890721,0xfef75f3,0x120f24f1,0x1990ae7,0x339c4452,0x27a15b8e,0xba7276d,0x60dc1b7b,0x4f4b7f82,0x67db7007,0x4f4a57d9,0x621252e8,0x20532cfc,0x6a390306,0x18800423,0x19f3778a,0x462316f0,0x56ae0937,0x43c2675c,0x65ca45fd,0xd604ff2,0xbfd22cb,0x3afe643b,0x3bf67fa6,0x44623579,0x184031f8,0x32174f97,0x4c6a092a,0x5fb50261,0x1650174,0x33634af1,0x712d18f4,0x6e997169,0x5dab7afe,0x7c2b2ee8,0x6edb75b4,0x5f836fb6,0x3c2a6dd6,0x292d05c2,0x52244db,0x149a5f4f,0x5d486540,0x331d15ea,0x4f456920,0x483a699f,0x3b450f05,0x3b207c6c,0x749d70fe,0x417461f6,0x62b031f1,0x2750577b,0x29131533,0x588c3808,0x1aef3456,0xf3c00ec,0x7da74742,0x4b797a6c,0x5ebb3287,0x786558b8,0xed4ff2,0x6269691e,0x24a2255f,0x62c11f7e,0x2f8a7dcd,0x643b17fe,0x778318b8,0x253b60fe,0x34bb63a3,0x5b03214f,0x5f1571f4,0x1a316e9f,0x7acf2704,0x28896838,0x18614677,0x1bf569eb,0xba85ec9,0x6aca6b46,0x1e43422a,0x514d5f0e,0x413e018c,0x307626e9,0x1ed1dfa,0x49f46f5a,0x461b642b,0x7d7007f2,0x13652657,0x6b160bc5,0x65e04849,0x1f526e1c,0x5a0251b6,0x2bd73f69,0x2dbf7acd,0x51e63e80,0x5cf2670f,0x21cd0a03,0x5cff0261,0x33ae061e,0x3bb6345f,0x5d814a75,0x257b5df4,0xa5c2c5b,0x16a45527,0x16f23945,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0 };
void ReStrsToHexBytes(unsigned char* hb, char* serial);
void BruteForce(char* user);
int main()
{
char user[] = "";
BruteForce(user);
return 0;
}
void BruteForce(char* user)
{
char serial[0x19] = { 0 };
unsigned char hb[8] = { 0 };
bool bGo = true;
hb[3] = 0x9C;
// 根据hb爆破serial,先找出符合条件的1,2,5,7下标对应的元素
for(unsigned char i1 = 0;i1<0xFF && bGo;i1++)
for (unsigned char i2 = 0; i2 < 0xFF && bGo; i2++)
for (unsigned char i5 = 0; i5 < 0xFF && bGo; i5++)
for (unsigned char i7 = 0; i7 < 0xFF && bGo; i7++)
{
unsigned short v19 = (i5 ^ i2) + ((i1 ^ i7) << 8);
unsigned int v20 = Calc_1(v19);
if((v20-1)>=999)
continue;
unsigned int v25 = Calc_2(user, true, 0, v20);
char* a1 = reinterpret_cast(&v25);
if (i5 == a1[1] && i7 == a1[3])
{
hb[1] = i1;
hb[2] = i2;
hb[4] = a1[0];
hb[5] = i5;
hb[6] = a1[2];
hb[7] = i7;
hb[0] = ReXor_1(0xF)^hb[6];
bGo = false;
break;
}
}
ReStrsToHexBytes(hb, serial);
printf("UserName: %s\nSerial: %s\n",user,serial);
}
void ReStrsToHexBytes(unsigned char* hb, char* serial)
{
serial[0] = ReCharToByte(hb[0] >> 4);
serial[1] = ReCharToByte(hb[0] & 0xF);
serial[2] = ReCharToByte(hb[1] >> 4);
serial[3] = ReCharToByte(hb[1] & 0xF);
serial[4] = '-';
serial[5] = ReCharToByte(hb[2] >> 4);
serial[6] = ReCharToByte(hb[2] & 0xF);
serial[7] = ReCharToByte(hb[3] >> 4);
serial[8] = ReCharToByte(hb[3] & 0xF);
serial[9] = '-';
serial[0xA] = ReCharToByte(hb[4] >> 4);
serial[0xB] = ReCharToByte(hb[4] & 0xF);
serial[0xC] = ReCharToByte(hb[5] >> 4);
serial[0xD] = ReCharToByte(hb[5] & 0xF);
serial[0xE] = '-';
serial[0xF] = ReCharToByte(hb[6] >> 4);
serial[0x10] = ReCharToByte(hb[6] & 0xF);
serial[0x11] = ReCharToByte(hb[7] >> 4);
serial[0x12] = ReCharToByte(hb[7] & 0xF);
}
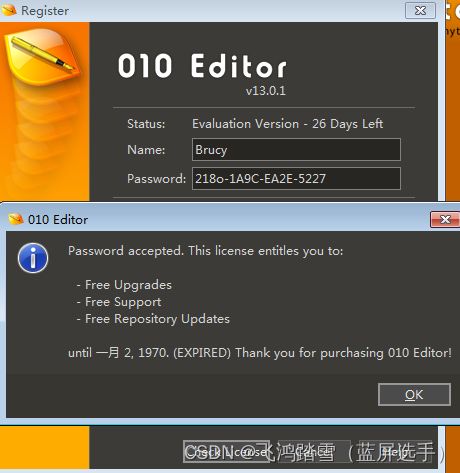
由于没有网络验证,所以同一个用户名和序列号可无限使用。这里给出一组可用的用户名和序列号:
Username:Brucy
Serial:218o-1A9C-EA2E-5227