NAT-HCIA阶段综合实验
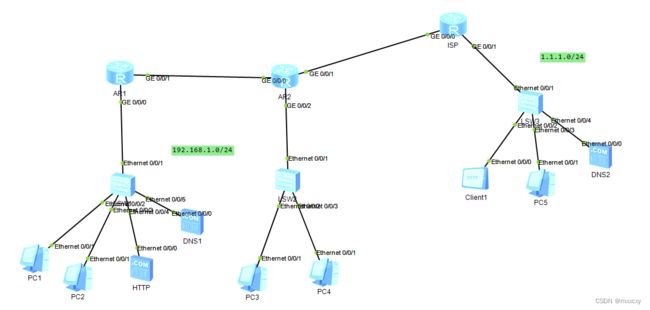
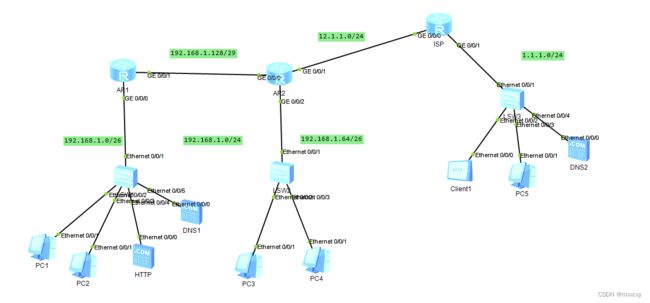
拓扑结构:
要求
1、ISP路由器只能配置IP地址,之后不得进行其他配置
2、内部整个网络基于192.168.1.0/24进行地址规划
3、R1、R2之间启动OSPF协议,单区域
4、PC1~PC4自动获取IP地址
5、PC1不能telnetR1,PC1外的其他内网PC可以telnet
6、PC1~PC4可以访问PC5,R2的公网接口只拥有一个公有IP12.1.1.1
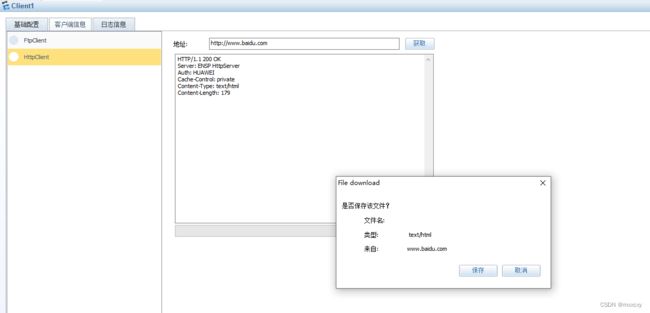
7、外部的client可以通过域名访问http server
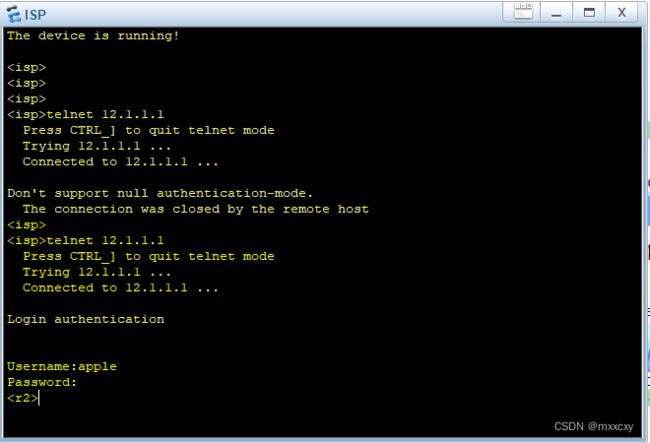
8、ISP路由telnet 12.1.1.1,最终成功登录到R1上
使用的设备:3台![]() 路由器、3台
路由器、3台![]() 交换机、5台
交换机、5台 电脑、3台
电脑、3台 服务器和一台
服务器和一台 终端
终端
解决网络拓扑:
1、确定广播域的个数
2、分配网段
3、配置IP地址 (优先配置路由器)
确定广播域的个数
根据拓扑结构图以及要求可知,本拓扑结构一共拥有5个网段,包括3个内网网段和两个给定网段
分配网段
其中3个内网网段基于192.168.1.0/24进行划分
划分为4个网段,需要借2位子网掩码:
两个内网网段:
192.168.1.0 /26
192.168.1.64 /26
一个接口网段:
192.168.1.128 /26
给一整个26位子网掩码的网段用于两个接口,过于浪费,所以给与4个地址的网段即可
192.168.1.128/29
一个备用网段:
192.168.1.192 /26
配置路由器IP地址
AR1:
system
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname r1
[r1]dhcp enable
Info: The operation may take a few seconds. Please wait for a moment.done.
[r1]ip pool a
Info: It's successful to create an IP address pool.
[r1-ip-pool-a]network 192.168.1.0 mask 26
[r1-ip-pool-a]gateway-list 192.168.1.1
[r1-ip-pool-a]dns-list 114.114.114.114 8.8.8.8
[r1-ip-pool-a]q
[r1]interface GigabitEthernet 0/0/1
[r1-GigabitEthernet0/0/1]ip address 192.168.1.129 255.255.255.248
Info: A similar IP subnet already exists. Please verify the current IP subnet design.
[r1-GigabitEthernet0/0/1]
Apr 18 2023 22:16:57-08:00 r1 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP on the interface GigabitEthernet0/0/1 has entered the UP state.
[r1-GigabitEthernet0/0/1]q
[r1]interface GigabitEthernet 0/0/0
[r1-GigabitEthernet0/0/0]ip address 192.168.1.1 255.255.255.248
[r1-GigabitEthernet0/0/0]
Apr 18 2023 22:17:44-08:00 r1 %%01IFNET/4/LINK_STATE(l)[3]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[r1-GigabitEthernet0/0/0]dhcp select global
[r1-GigabitEthernet0/0/0]q
[r1] AR2:
system
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname r2
[r2]dhcp enable
Info: The operation may take a few seconds. Please wait for a moment.done.
[r2]ip pool b
Info: It's successful to create an IP address pool.
[r2-ip-pool-b]network 192.168.1.64 mask 26
[r2-ip-pool-b]gateway-list 192.168.1.65
[r2-ip-pool-b]dns-list 114.114.114.114 8.8.8.8
[r2-ip-pool-b]q
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]ip address 192.168.1.130 29
[r2-GigabitEthernet0/0/0]
Apr 18 2023 22:20:18-08:00 r2 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[r2-GigabitEthernet0/0/0]q
[r2]interface GigabitEthernet 0/0/1
[r2-GigabitEthernet0/0/1]ip address 12.1.1.1 24
[r2-GigabitEthernet0/0/1]
Apr 18 2023 22:20:45-08:00 r2 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP on the interface GigabitEthernet0/0/1 has entered the UP state.
[r2-GigabitEthernet0/0/1]q
[r2]interface GigabitEthernet 0/0/2
[r2-GigabitEthernet0/0/2]ip address 192.168.1.65 29
Apr 18 2023 22:21:06-08:00 r2 %%01IFNET/4/LINK_STATE(l)[2]:The line protocol IP on the interface GigabitEthernet0/0/2 has entered the UP state.
[r2-GigabitEthernet0/0/2]dhcp select global
[r2-GigabitEthernet0/0/2]q
[r2] AR3:
system
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname isp
[isp]interface GigabitEthernet 0/0/0
[isp-GigabitEthernet0/0/0]ip address 12.1.1.2 24
[isp-GigabitEthernet0/0/0]
Apr 18 2023 22:24:50-08:00 isp %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[isp-GigabitEthernet0/0/0]q
[isp]interface GigabitEthernet 0/0/1
[isp-GigabitEthernet0/0/1]ip address 1.1.1.1 24
[isp-GigabitEthernet0/0/1]
Apr 18 2023 22:25:13-08:00 isp %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP on the interface GigabitEthernet0/0/1 has entered the UP state.
[isp-GigabitEthernet0/0/1]q
[isp]dhcp enable
Info: The operation may take a few seconds. Please wait for a moment.done.
[isp]ip pool c
Info: It's successful to create an IP address pool.
[isp-ip-pool-c]network 1.1.1.0 mask 24
[isp-ip-pool-c]gateway-list 1.1.1.1
[isp-ip-pool-c]dns-list 114.114.114.114 8.8.8.8
[isp-ip-pool-c]q
[isp]interface GigabitEthernet 0/0/1
[isp-GigabitEthernet0/0/1]dhcp select global
[isp-GigabitEthernet0/0/1]q
[isp] 配置OSPF动态路由协议
AR1:
[r1]ospf 1 router-id 1.1.1.1
[r1-ospf-1]area 0
[r1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.63
[r1-ospf-1-area-0.0.0.0]network 192.168.1.128 0.0.0.7
[r1-ospf-1-area-0.0.0.0]q
[r1-ospf-1]q
[r1]
[r1]interface GigabitEthernet 0/0/1
[r1-GigabitEthernet0/0/1]ospf authentication-mode md5 1 cipher 123456AR2:
[r2]ospf 1 router-id 2.2.2.2
[r2-ospf-1]area 0
[r2-ospf-1-area-0.0.0.0]network 192.168.1.64 0.0.0.63
[r2-ospf-1-area-0.0.0.0]network 192.168.1.128 0.0.0.7
[r2-ospf-1-area-0.0.0.0]q
[r2-ospf-1]q
[r2]
[r2]interface GigabitEthernet 0/0/0
[r2-GigabitEthernet0/0/0]ospf authentication-mode md5 1 cipher 123456PC1~PC4通过DHCP服务获取IP地址,此时内网已经全网可达,并且可以通过域名访问http服务器。最后对运行OSPF协议之间的路由器做认证,保证更新安全。
ACL访问控制列表
AR1:
[r1]acl 3000
[r1-acl-adv-3000]rule deny tcp source 192.168.1.2 0 destination 192.168.1.1 0 destination-port eq 23
[r1-acl-adv-3000]q
[r1]interface GigabitEthernet 0/0/0
[r1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
[r1-GigabitEthernet0/0/0]q
[r1]aaa
[r1-aaa]local-user panda privilege level 15 password cipher 123456
Info: Add a new user.
[r1-aaa]local-user panda service-type telnet
[r1-aaa]q
[r1]user-interface vty 0
[r1-ui-vty0]authentication-mode aaa
[r1-ui-vty0]q
[r1]在PC1上无法测试,将PC1替换为一个路由器可以实现ACL的功能,但是在R2的路由器上可以远程登录到R1
配置缺省路由
通过R2向内部网络发布一条通往外网的缺省静态路由,并配置telnet
AR2:
[r2]ip route-static 0.0.0.0 0 12.1.1.2
[r2]ospf 1
[r2-ospf-1]default-route-advertise always
[r2-ospf-1]q
[r2]
[r2]aaa
[r2-aaa]local-user apple privilege level 15 password cipher 123456
Info: Add a new user.
[r2-aaa]local-user apple service-type telnet
[r2-aaa]q
[r2]user-interface vty 0
[r2-ui-vty0]authentication-mode aaa
[r2-ui-vty0]q
[r2]
此时内网可以正常访问PC5
配置NAT协议
[r2]acl 2000
[r2-acl-basic-2000]rule permit source 192.168.1.0 0.0.0.255
[r2-acl-basic-2000]q
[r2]interface GigabitEthernet 0/0/1
[r2-GigabitEthernet0/0/1]nat outbound 2000
[r2-GigabitEthernet0/0/1]nat server protocol tcp global current-interface 80 ins
ide 192.168.1.4 80
Warning:The port 80 is well-known port. If you continue it may cause function fa
ilure.
Are you sure to continue?[Y/N]:y并做好80端口映射,配置完后,外网的client可以访问内网的网址
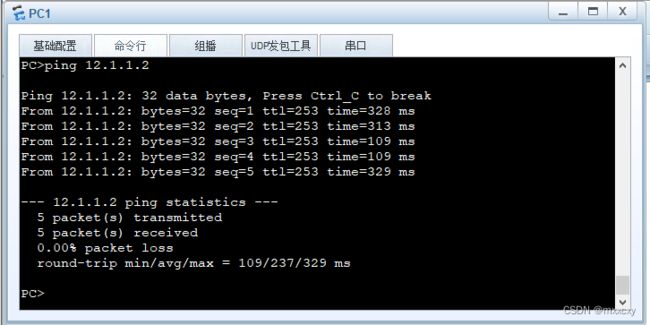
ISP也可以正常远程登录到12.1.1.1上
实验到此为止,就完成了 ,要求也是全部完成。