等保测评linux主机整改
安全加固部份:
一。密码90天更换,最小长度8
建议:
对login.defs文件修只影响后续建立的用户,如果要改变以前建立的用户的有效期等可以使用chage命令.
1)/etc/login.defs,参考以下设置:
PASS_MAX_DAYS 90;
PASS_MIN_DAYS 1;
PASS_WARN_AGE 28;密码失效28天通知用户
PASS_MIN_LEN 8;
修改命令
sed -i.bak -r ‘/^PASS_MAX_DAYS/s/99999/90/’ /etc/login.defs
sed -ir ‘/^PASS_MIN_DAYS/s/0/1/’ /etc/login.defs
sed -ir ‘/^PASS_WARN_AGE/s/7/28/’ /etc/login.defs
sed -ir ‘/^PASS_MIN_LEN/s/5/8/’ /etc/login.defs
二。)在/etc/pam.d/system-auth文件中配置密码复杂度:
sed -i.bak '/password required pam_deny.so/i\password requisite pam_cracklib.so minlen=8 ucredit=-2 lcredit=-1 dcredit=-4 ocredit=-1' /etc/pam.d/system-auth
在pam_pwquality.so 后面配置参数
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type=
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type= minlen=8 ucredit=-1 lcredit=-1 ocredit=-1 dcredit=-1
=1111==
retry=5 difok=3 minlen=10 ucredit=-1 lcredit=-3 dcredit=-3 dictpath=/usr/share/cracklib/pw_dict
参数含义:
尝试次数:5 ;最少不同字符:3 ;最小密码长度:10 ;最少大写字母:1;最少小写字母:3 ;最少数字:3 ;字典位置:/usr/share/cracklib/pw_dict
=1111==
操作系统所有账户登陆密码和密码策略配置必须同时具备,才为符合。
配置失败登陆锁定:
1种方式.(/etc/pam.d/sshd前面添加一行 测试能锁定用户)
auth required pam_tally2.so onerr=fail deny=3 unlock_time=300 even_deny_root root_unlock_time=300)
sed -i.bak ‘2i\auth required pam_tally2.so onerr=fail deny=3 unlock_time=300 even_deny_root root_unlock_time=300’ /etc/pam.d/sshd
2.种方式(测试有问题)
sed -i.bak ‘/auth required pam_deny.so/i\auth required pam_tally2.so even_deny_root deny=8 unlock_time=180’ /etc/pam.d/system-auth
sed -i.bak ‘/auth required pam_deny.so/i\auth required pam_tally2.so even_deny_root deny=8 unlock_time=180’ /etc/pam.d/system-auth
建议在:/etc/pam.d/system-auth文件中配置:
(在centos7不存在这个库:pam_tally.so)
auth required /lib/security/pam_tally.so onerr=fail no_magic_root
account required /lib/security/pam_tally.so deny=5 no_magic_root reset(建议普通用户设置为5次,root用户设置为30次),或在sshd中设置。
查找用户失败次数
pam_tally2 -u root
解锁用户
pam_tally2 -r -u root
================================
centos8登陆失败处理:
修改以下文件
/etc/pam.d/password-auth
/etc/pam.d/system-auth
添加内容:
auth required pam_faillock.so preauth silent audit deny=5 unlock_time=300
auth [default=die] pam_faillock.so authfail audit deny=5 unlock_time=300
account required pam_faillock.so

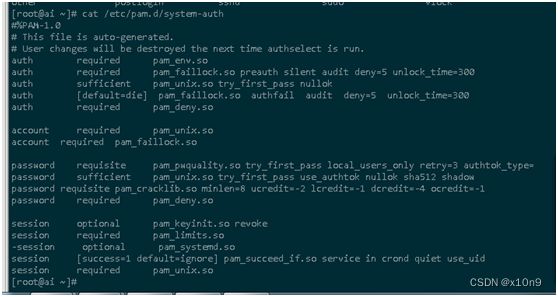
查找用户失败次数
faillock -u root
解锁用户
faillock --user root --reset
三。
建议对服务器操作系统审计记录进行备份,且日志保存时间应为6个月。改/etc/logrotate.conf 配置为rotate 26;或改weekly为monthly,rotate为6,并进行有效备份,备份至日志服务器中。
sed -i.bak ‘s/weekly/monthly/’ /etc/logrotate.conf
sed -i.bak ‘s/rotate 4/rotate 6/’ /etc/logrotate.conf
四。ssh建议操作系统限制终端可接入方式或限制可登录的网络地址范围。
配置用例:
在/etc/ssh/sshd_config内添加
AllowUsers [email protected].*
AllowUsers [email protected].*
#AllowUsers [email protected].*
#AllowUsers [email protected],192.168.16.167
#AllowUsers [email protected]/24
systemctl restart sshd
以上配置修改集合
#!/bin/bash
echo “=密码90天更换,最小长度8”
sed -i.bak -r ‘/^PASS_MAX_DAYS/s/99999/90/’ /etc/login.defs
sed -ir ‘/^PASS_MIN_DAYS/s/0/1/’ /etc/login.defs
sed -ir ‘/^PASS_WARN_AGE/s/7/28/’ /etc/login.defs
sed -ir ‘/^PASS_MIN_LEN/s/5/8/’ /etc/login.defs
echo “=/etc/pam.d/system-auth文件中配置密码复杂度=====”
sed -i.bak -r ‘/^password requisite/s/$/ minlen=8 ucredit=-1 lcredit=-1 ocredit=-1 dcredit=-1/’ /etc/pam.d/system-auth
echo “=配置用户锁定:==”
sed -i.bak ‘2i\auth required pam_tally2.so onerr=fail deny=3 unlock_time=300 even_deny_root root_unlock_time=300’ /etc/pam.d/sshd
echo “=配置日志保存时间应为6个月”
sed -i.bak ‘s/weekly/monthly/’ /etc/logrotate.conf
sed -i ‘s/rotate 4/rotate 6/’ /etc/logrotate.conf
echo “配置限制登陆地址范围”
echo “AllowUsers [email protected].*” >> /etc/ssh/sshd_config
systemctl restart sshd
五:配置denyhosts防爆破
systemctl status denyhosts
[root@SSHGRATEWAY data]# cat /usr/share/denyhosts/denyhosts.cfg|grep -v ^#|grep -v ^$
############ THESE SETTINGS ARE REQUIRED ############
SECURE_LOG = /var/log/secure
HOSTS_DENY = /etc/hosts.deny
PURGE_DENY = 5m
BLOCK_SERVICE = sshd
DENY_THRESHOLD_INVALID = 5
DENY_THRESHOLD_VALID = 5
DENY_THRESHOLD_ROOT = 5
DENY_THRESHOLD_RESTRICTED = 20
WORK_DIR = /usr/share/denyhosts/data
SUSPICIOUS_LOGIN_REPORT_ALLOWED_HOSTS=YES
HOSTNAME_LOOKUP=NO
LOCK_FILE = /var/lock/subsys/denyhosts
############ THESE SETTINGS ARE OPTIONAL ############
ADMIN_EMAIL =
SMTP_HOST = localhost
SMTP_PORT = 25
SMTP_FROM = DenyHosts nobody@localhost
SMTP_SUBJECT = DenyHosts Report
AGE_RESET_VALID=1w
AGE_RESET_ROOT=1w
AGE_RESET_RESTRICTED=1w
AGE_RESET_INVALID=1w
RESET_ON_SUCCESS = yes
######### THESE SETTINGS ARE SPECIFIC TO DAEMON MODE ##########
DAEMON_LOG = /var/log/denyhosts
DAEMON_SLEEP = 30s
DAEMON_PURGE = 5m
######### THESE SETTINGS ARE SPECIFIC TO ##########
######### DAEMON SYNCHRONIZATION ##########
修改完配置文件后
systemctl restart denyhosts
六
ip超过允许阀值后被锁除方式
停用 DenyHosts : systemctl stop denyhosts.service
删除黑名单中当前的ip地址: vim /etc/hosts.deny
进入 /var/lib/denyhosts 或者这个目录cd /usr/share/denyhosts/data
-rw-r–r-- 1 root root 39 2月 16 2015 allowed-hosts
-rw-r–r-- 1 root root 71451 7月 19 10:58 hosts
-rw-r–r-- 1 root root 71270 7月 19 10:58 hosts-restricted
-rw-r–r-- 1 root root 71433 7月 19 10:58 hosts-root
-rw-r–r-- 1 root root 71280 7月 19 10:58 hosts-valid
-rw-r–r-- 1 root root 105 7月 19 10:58 offset
-rw-r–r-- 1 root root 0 7月 19 10:58 suspicious-logins
-rw-r–r-- 1 root root 44731 7月 19 10:58 users-hosts
-rw-r–r-- 1 root root 50925 7月 19 10:58 users-invalid
-rw-r–r-- 1 root root 643 7月 19 10:58 users-valid
依次在上面各个文件中移除自己当前的IP地址