- 自学网络安全(黑客技术)2025年 —100天学习计划
白帽黑客cst
学习网络安全web安全linux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- 自学网络安全(黑客技术)2025年 —100天学习计划
白帽黑客cst
学习web安全安全网络linux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- 自学网络安全(黑客技术)2025年 —100天学习计划
白帽黑客cst
学习web安全安全网络linux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- 网络安全(黑客技术) 最新—90天学习计划
白帽黑客cst
网络安全web安全网络安全学习数据结构mysql
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- 自学网络安全(黑客技术)2024年 —100天学习计划
白帽黑客cst
学习web安全安全网络linux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- mPaas-RPC拦截器各种场景下的使用指南
阿里开发者
移动开发运维JavaScriptJava
简介:mPaas-RPC拦截器各种场景下的使用指南1.背景金融级移动开发平台mPaaS[1](MobilePaaS)为App开发、测试、运营及运维提供云到端的一站式解决方案,能有效降低技术门槛、减少研发成本、提升开发效率,协助企业快速搭建稳定高质量的移动应用。其中移动网关服务(MobileGatewayService,简称MGS)作为mPaas最重要的组件之一,连接了移动客户端与服务端,简化了移动
- 分享---rpc运维事故处理
XiaoDuofCSDN
rpc运维网络协议
事故案例03-QserverRPC调用大量失败一、事故背景Queryserver是内部的核心服务,负责处理数据查询请求并支持分布式缓存功能。为优化缓存一致性,新增了分布式锁逻辑:在查询请求命中缓存时需先获取分布式锁(基于Tair实现),若未获取成功则等待1秒后重试。此功能上线后,在特定异常场景下(如SQL执行失败)触发了线程池资源耗尽,最终导致RPC请求被拒绝,引发服务故障。二、事故影响(一)业务
- DeepSeek本地部署必要性分析及云端替代方案推荐
Asher_Yao
人工智能
一、本地部署适用场景分析硬件要求完整版模型需≥32GB显存(推荐NVIDIAA100/A800)基础版也需RTX3090级别显卡(约150W功耗)适用人群建议✔️企业用户:需私有化部署处理敏感数据✔️研究人员:需定制模型微调✔️开发者:需API深度集成维护成本单节点年运维成本≈¥18,000(含电费/散热)二、已验证的云端替代方案(2025.2实测)方案1:硅基流动SaaS平台技术特性:支持API
- Python自动化运维实战,怎么构建分布式质量监控平台
好知识传播者
Python实例开发实战运维python自动化分布式质量监控平台linux
注意:本文的下载教程,与以下文章的思路有相同点,也有不同点,最终目标只是让读者从多维度去熟练掌握本知识点。下载教程:Python自动化运维项目开发实战_构建分布式质量监控平台_编程案例解析实例课程教程.pdf一、引言随着企业业务的不断扩展和复杂化,系统运维面临着越来越多的挑战。传统的运维方式已经无法满足现代企业的需求,因此,自动化运维成为了企业提升运维效率、保障系统稳定性的重要手段。在自动化运维中
- 分布式服务监控
点滴~
分布式
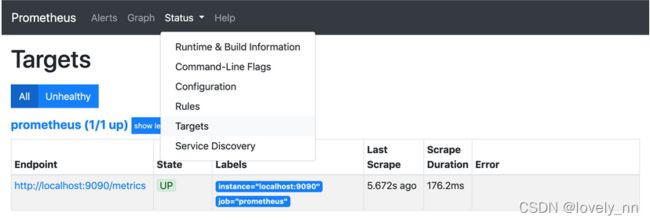
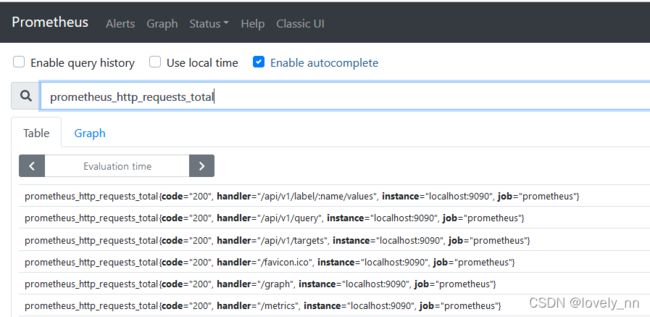
目录分布式服务监控CAT(CentralApplicationTracking)监控对象和指标分布式服务监控分布式服务监控在保障分布式系统稳定运行中至关重要,通过各类监控组件对关键指标进行监测,能及时发现并解决问题。下面将从监控组件、其优缺点、监控指标及其作用展开介绍。监控组件Prometheus:一个开源的系统监控和报警工具包。它采用拉取式采集数据,支持多种数据采集方式,如直接采集应用程序暴露的
- 国内三大云数据库测试对比
m0_63984008
数据库腾讯云阿里云
导读腾讯云数据库提供了可视化的运维操作页面和自动备份的能力,降低了数据库运维的门槛。同时云数据库还支持高可用架构,对数据的安全性和服务的可靠性更有保障。另外有的云数据库厂商还提供了诸如数据库审计、慢查询分析、数据回档等能力,大大减轻了数据库运维和DBA的工作量。我司CTO和技术总监都是腾讯系的,所以我们一开始就选用腾讯云的服务。他们家的云数据库提供了可视化的运维操作页面和自动备份的能力,降低了数据
- 如何建设IT运维管理体系
运维管理
在当今数字化和信息化不断发展的背景下,企业的IT基础设施扮演着越来越重要的角色。为了确保这些基础设施稳定、安全和高效地运行,建设完善的IT运维管理体系是企业必不可少的一部分。IT运维管理体系不仅有助于提升企业系统的可用性和性能,还能减少系统故障,提高响应速度,确保业务持续性。通过系统化的管理和高效的运维流程,企业能够确保其信息技术基础设施始终保持在最佳状态,满足日益增长的业务需求。本文将详细探讨如
- [k8s源码]9.workqueue
weixin_45396500
k8s源码java开发语言
client-go是一个库,提供了与KubernetesAPI服务器交互的基础设施。它提供了诸如Informer、Lister、ClientSet等工具,用于监听、缓存和操作Kubernetes资源。而自定义控制器则利用这些工具来实现特定的业务逻辑和自动化任务。业务逻辑实现:client-go不包含特定的业务逻辑。自定义控制器允许实现特定于您的应用程序或需求的逻辑。扩展Kubernetes:通过自
- 作为一名测试工程师如何学习Kubernetes(k8s)技能
网络安全小宇哥
学习kubernetes容器计算机网络web安全安全dubbo
前言Kubernetes(K8s)作为云原生时代的关键技术之一,对于运维工程师、开发工程师以及测试工程师来说,都是一门需要掌握的重要技术。作为一名软件测试工程师,学习Kubernetes是一个有助于提升自动化测试、容器化测试以及云原生应用测试能力的重要过程。以下是一个系统性的学习路径和建议:一、了解基础概念1)容器技术:学习Docker等容器技术的基础知识,了解容器的基本概念、镜像、容器运行与管理
- 深入理解 Kubernetes 命名空间:高效管理与隔离资源的关键
简单简单小白
kubernetes贪心算法java
深入理解Kubernetes命名空间:高效管理与隔离资源的关键目录深入理解Kubernetes命名空间:高效管理与隔离资源的关键什么是命名空间?命名空间的作用1.资源隔离2.多租户支持3.资源管理和策略控制4.简化管理创建和使用命名空间命名空间与集群中的其他资源结语在Kubernetes(k8s)中,命名空间(Namespace)是资源隔离和组织管理的核心概念之一。本文将详细探讨命名空间的作用,以
- 202年充电计划——自学手册 网络安全(黑客技术)
网安康sir
web安全安全网络pythonlinux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- 202年充电计划——自学手册 网络安全(黑客技术)
网安康sir
web安全安全网络pythonlinux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- 202年充电计划——自学手册 网络安全(黑客技术)
网安康sir
web安全安全网络pythonlinux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包前言什么是网络安全网络安全可以基于攻击和防御视角来分类,我们经常听到的“红队”、“渗透测试”等就是研究攻击技术,而“蓝队”、“安全运营”、“安全运维”则研究防御技术。如何成为一名黑客很多朋友在学习安全方面都会半路转行,因为不知如何去学,在这里,我将这个整份答案分为黑客(网络安全)入门必备、黑客(网络安全)职业指南、黑客(网络安全)学习
- BY组态-低代码web可视化组件
万维——组态
低代码前端物联网运维数学建模编辑器
简介BY组态是集实时数据展示、动态交互等一体的全功能可视化平台。帮助物联网、工业互联网、电力能源、水利工程、智慧农业、智慧医疗、智慧城市等场景快速实现数字孪生、大屏可视化、Web组态、SCADA等解决方案。具有实时监控、多样、变化、动态交互、高效、可扩展、支持自动算法、跨平台等特点,最大程度减少研发和运维的成本,并致力于普通业务人员0代码开发实现数字孪生、大屏可视化、Web组态、SCADA等解决方
- 为什么企业必须拥有SAP内部顾问?10大核心价值深度解析
EasyStudios
SAP实施知识SAP内部顾问企业数字化转型ERP系统运维IT与业务融合
引言:一个价值百万的抉择"当企业投入百万级资金建设SAP系统后,持续运维成本中最大的隐性开支是什么?——是外部顾问高昂的服务费,还是内部沟通的损耗成本?"本文将通过10个真实场景,揭示SAP内部顾问如何成为企业数字化进程中的战略性资产。一、破解沟通困局:从网状结构到单点枢纽1.多对多沟通VS单点对接外部顾问模式:复制业务部门A↔顾问团队X业务部门B↔顾问团队Y业务部门C↔顾问团队Z内部顾问模式:复
- Kubernetes 从入门到精通:解锁容器编排的终极指南 [特殊字符]
a小胡哦
kubernetes容器云原生
为什么需要Kubernetes?Kubernetes(简称K8s)是容器编排领域的王者,它能帮你:自动扩缩容:流量激增时自动扩展应用实例(HorizontalPodAutoscaler)自愈能力:崩溃的容器秒级重启,节点故障自动迁移(Self-Healing设计)服务发现:动态管理微服务通信(Service机制)存储编排:一键挂载云存储/本地磁盘(PersistentVolumes)跨环境部署:一
- 数据中心场地设施管理规范—构建安全高效的数字基础设施
数据中心运维高级工程师
安全大数据运维云计算人工智能
引言:数据中心场地设施管理作为数据中心运营的重要组成部分,涵盖了从基础设施建设到日常运维的全方位工作。其管理质量直接关系到数据中心的可用性、可靠性和经济性。本文将全面探讨数据中心场地设施管理的重要性、目标、适用范围、遵循标准、组织架构及职责、场地设施分类与功能,以及管理要求,旨在为数据中心管理者提供一份实用的管理指南。一、目的数据中心场地设施管理的核心目的是确保数据中心的高效、稳定运行,同时优化资
- 资源池化构想
qq_1572902205
个人笔记
实验室模块化使得实验室同类资源聚集,便于维护管理。但实验室仪器更换因仪器聚集而变得困难,这给后期运维带来极大不便,同时闲置资源无法得到及时释放和利用。基于地址池和黑盒构想,若对内将实验室仪器资源池化,对外封装只留接口。则可以最大化的利用有效资源,减少人工维护。
- 基于Prometheus和Grafana的现代服务器监控体系构建
丁爸
运维服务器
1.简介1.1.概述基于Prometheus和Grafana的现代服务器监控体系是一种高效、灵活的监控解决方案,广泛应用于云计算和微服务架构的环境中。以下是这一监控体系的概述:Prometheus:Prometheus是一个开源的系统监控和警报工具包,由SoundCloud开发并维护。它具有强大的数据收集能力、灵活的查询语言以及与微服务架构的无缝集成。Prometheus的核心概念包括时间序列数据
- Spring Boot 启动时间优化全攻略
一休哥助手
springboot后端java
引言随着SpringBoot的广泛应用,开发者享受到了快速开发和自动化配置的便利。然而,随着项目复杂度的增加,SpringBoot项目启动时间也变得越来越长,这在开发、调试和部署阶段可能会成为效率瓶颈。如何优化SpringBoot的启动时间,已经成为开发者和运维人员关注的重要问题。本文将详细分析影响SpringBoot启动时间的主要因素,并提供一套从配置优化到代码调整的全方位优化方案,帮助开发者显
- 深入探讨K8s资源管理和性能优化
磐基Stack专业服务团队
Kuberneteskubernetes性能优化容器
#作者:曹付江文章目录前言:1.监控Kubernetes集群的资源利用率1.1Prometheus1.2Kubernetes度量服务器1.3Grafana1.4自定义指标2.识别资源瓶颈2.1.监控工具2.2.性能剖析2.3Kubernetes事件和日志2.4.群集自动扩展2.5.负载测试3.扩展应用程序以提高性能3.1.水平Pod自动缩放器(HPA)3.2.垂直PodAutoscaler(VPA
- 国产化数据库选型比较
小四的快乐生活
数据库
近年来国产化数据库越来越多,目前可选性的数据库也琳琅满目,各厂家也都有自己独特的产品,在去IOE的进程中,都有自己独特的迁移工具和产品能力去支撑,汇总了一下目前市面上数据库使用较多和较运用广泛的数据库,详细内容如下:数据库名称优点缺点支撑的数据量架构设计运维能力SQL标准openGauss开源社区驱动,架构灵活,对国产软硬件适配性好特定行业成功案例积累不足PB级多模存储架构,支持行、列存储,有智能
- Ansible角色之Jenkins自动化安装指南
姜俭
本文还有配套的精品资源,点击获取简介:Ansible是一个用于IT运维的自动化工具,通过编写YAML剧本实现服务器管理与部署。本文介绍了一个专用于安装Jenkins的Ansible角色——ansible-role-jenkins,它自动化了Jenkins的安装、配置和维护过程,支持依赖管理、安全设置、构建管道、插件安装和版本控制等功能。使用此角色可以提高DevOps流程中Jenkins部署的效率和
- 运维案例之记一次Kubernetes集群证书过期或延期操作处理实践指南
全栈工程师修炼指南
云原生落地实用指南kubernetes运维docker容器云原生
欢迎关注「WeiyiGeek」公众号点击下方卡片即可关注我哟!设为「星标⭐」每天带你基础入门到进阶实践再到放弃学习!涉及网络安全运维、应用开发、物联网IOT、学习路径、个人感悟等知识“花开堪折直须折,莫待无花空折枝。”作者主页:[https://www.weiyigeek.top]作者博客:[https://blog.weiyigeek.top]作者答疑学习交流群:
- 运维工程师的日常巡检内容
AustinCien
linux
服务器健康状态:检查服务器的硬件、操作系统和服务的运行状态,确保服务器正常工作并且没有异常。网络设备状态:检查网络交换机、路由器、防火墙等网络设备的连通性和运行状态,确保网络设备正常工作。存储设备空间:检查存储设备(如磁盘阵列、NAS等)的可用空间和使用率,及时处理存储空间不足的情况。数据库状态:检查数据库服务器的运行状态、连接数和查询性能,并进行必要的优化和维护。应用程序状态:检查应用程序服务器
- Spring4.1新特性——综述
jinnianshilongnian
spring 4.1
目录
Spring4.1新特性——综述
Spring4.1新特性——Spring核心部分及其他
Spring4.1新特性——Spring缓存框架增强
Spring4.1新特性——异步调用和事件机制的异常处理
Spring4.1新特性——数据库集成测试脚本初始化
Spring4.1新特性——Spring MVC增强
Spring4.1新特性——页面自动化测试框架Spring MVC T
- Schema与数据类型优化
annan211
数据结构mysql
目前商城的数据库设计真是一塌糊涂,表堆叠让人不忍直视,无脑的架构师,说了也不听。
在数据库设计之初,就应该仔细揣摩可能会有哪些查询,有没有更复杂的查询,而不是仅仅突出
很表面的业务需求,这样做会让你的数据库性能成倍提高,当然,丑陋的架构师是不会这样去考虑问题的。
选择优化的数据类型
1 更小的通常更好
更小的数据类型通常更快,因为他们占用更少的磁盘、内存和cpu缓存,
- 第一节 HTML概要学习
chenke
htmlWebcss
第一节 HTML概要学习
1. 什么是HTML
HTML是英文Hyper Text Mark-up Language(超文本标记语言)的缩写,它规定了自己的语法规则,用来表示比“文本”更丰富的意义,比如图片,表格,链接等。浏览器(IE,FireFox等)软件知道HTML语言的语法,可以用来查看HTML文档。目前互联网上的绝大部分网页都是使用HTML编写的。
打开记事本 输入一下内
- MyEclipse里部分习惯的更改
Array_06
eclipse
继续补充中----------------------
1.更改自己合适快捷键windows-->prefences-->java-->editor-->Content Assist-->
Activation triggers for java的右侧“.”就可以改变常用的快捷键
选中 Text
- 近一个月的面试总结
cugfy
面试
本文是在学习中的总结,欢迎转载但请注明出处:http://blog.csdn.net/pistolove/article/details/46753275
前言
打算换个工作,近一个月面试了不少的公司,下面将一些面试经验和思考分享给大家。另外校招也快要开始了,为在校的学生提供一些经验供参考,希望都能找到满意的工作。
- HTML5一个小迷宫游戏
357029540
html5
通过《HTML5游戏开发》摘抄了一个小迷宫游戏,感觉还不错,可以画画,写字,把摘抄的代码放上来分享下,喜欢的同学可以拿来玩玩!
<html>
<head>
<title>创建运行迷宫</title>
<script type="text/javascript"
- 10步教你上传githib数据
张亚雄
git
官方的教学还有其他博客里教的都是给懂的人说得,对已我们这样对我大菜鸟只能这么来锻炼,下面先不玩什么深奥的,先暂时用着10步干净利索。等玩顺溜了再用其他的方法。
操作过程(查看本目录下有哪些文件NO.1)ls
(跳转到子目录NO.2)cd+空格+目录
(继续NO.3)ls
(匹配到子目录NO.4)cd+ 目录首写字母+tab键+(首写字母“直到你所用文件根就不再按TAB键了”)
(查看文件
- MongoDB常用操作命令大全
adminjun
mongodb操作命令
成功启动MongoDB后,再打开一个命令行窗口输入mongo,就可以进行数据库的一些操作。输入help可以看到基本操作命令,只是MongoDB没有创建数据库的命令,但有类似的命令 如:如果你想创建一个“myTest”的数据库,先运行use myTest命令,之后就做一些操作(如:db.createCollection('user')),这样就可以创建一个名叫“myTest”的数据库。
一
- bat调用jar包并传入多个参数
aijuans
下面的主程序是通过eclipse写的:
1.在Main函数接收bat文件传递的参数(String[] args)
如: String ip =args[0]; String user=args[1]; &nbs
- Java中对类的主动引用和被动引用
ayaoxinchao
java主动引用对类的引用被动引用类初始化
在Java代码中,有些类看上去初始化了,但其实没有。例如定义一定长度某一类型的数组,看上去数组中所有的元素已经被初始化,实际上一个都没有。对于类的初始化,虚拟机规范严格规定了只有对该类进行主动引用时,才会触发。而除此之外的所有引用方式称之为对类的被动引用,不会触发类的初始化。虚拟机规范严格地规定了有且仅有四种情况是对类的主动引用,即必须立即对类进行初始化。四种情况如下:1.遇到ne
- 导出数据库 提示 outfile disabled
BigBird2012
mysql
在windows控制台下,登陆mysql,备份数据库:
mysql>mysqldump -u root -p test test > D:\test.sql
使用命令 mysqldump 格式如下: mysqldump -u root -p *** DBNAME > E:\\test.sql。
注意:执行该命令的时候不要进入mysql的控制台再使用,这样会报
- Javascript 中的 && 和 ||
bijian1013
JavaScript&&||
准备两个对象用于下面的讨论
var alice = {
name: "alice",
toString: function () {
return this.name;
}
}
var smith = {
name: "smith",
- [Zookeeper学习笔记之四]Zookeeper Client Library会话重建
bit1129
zookeeper
为了说明问题,先来看个简单的示例代码:
package com.tom.zookeeper.book;
import com.tom.Host;
import org.apache.zookeeper.WatchedEvent;
import org.apache.zookeeper.ZooKeeper;
import org.apache.zookeeper.Wat
- 【Scala十一】Scala核心五:case模式匹配
bit1129
scala
package spark.examples.scala.grammars.caseclasses
object CaseClass_Test00 {
def simpleMatch(arg: Any) = arg match {
case v: Int => "This is an Int"
case v: (Int, String)
- 运维的一些面试题
yuxianhua
linux
1、Linux挂载Winodws共享文件夹
mount -t cifs //1.1.1.254/ok /var/tmp/share/ -o username=administrator,password=yourpass
或
mount -t cifs -o username=xxx,password=xxxx //1.1.1.1/a /win
- Java lang包-Boolean
BrokenDreams
boolean
Boolean类是Java中基本类型boolean的包装类。这个类比较简单,直接看源代码吧。
public final class Boolean implements java.io.Serializable,
- 读《研磨设计模式》-代码笔记-命令模式-Command
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
import java.util.ArrayList;
import java.util.Collection;
import java.util.List;
/**
* GOF 在《设计模式》一书中阐述命令模式的意图:“将一个请求封装
- matlab下GPU编程笔记
cherishLC
matlab
不多说,直接上代码
gpuDevice % 查看系统中的gpu,,其中的DeviceSupported会给出matlab支持的GPU个数。
g=gpuDevice(1); %会清空 GPU 1中的所有数据,,将GPU1 设为当前GPU
reset(g) %也可以清空GPU中数据。
a=1;
a=gpuArray(a); %将a从CPU移到GPU中
onGP
- SVN安装过程
crabdave
SVN
SVN安装过程
subversion-1.6.12
./configure --prefix=/usr/local/subversion --with-apxs=/usr/local/apache2/bin/apxs --with-apr=/usr/local/apr --with-apr-util=/usr/local/apr --with-openssl=/
- sql 行列转换
daizj
sql行列转换行转列列转行
行转列的思想是通过case when 来实现
列转行的思想是通过union all 来实现
下面具体例子:
假设有张学生成绩表(tb)如下:
Name Subject Result
张三 语文 74
张三 数学 83
张三 物理 93
李四 语文 74
李四 数学 84
李四 物理 94
*/
/*
想变成
姓名 &
- MySQL--主从配置
dcj3sjt126com
mysql
linux下的mysql主从配置: 说明:由于MySQL不同版本之间的(二进制日志)binlog格式可能会不一样,因此最好的搭配组合是Master的MySQL版本和Slave的版本相同或者更低, Master的版本肯定不能高于Slave版本。(版本向下兼容)
mysql1 : 192.168.100.1 //master mysq
- 关于yii 数据库添加新字段之后model类的修改
dcj3sjt126com
Model
rules:
array('新字段','safe','on'=>'search')
1、array('新字段', 'safe')//这个如果是要用户输入的话,要加一下,
2、array('新字段', 'numerical'),//如果是数字的话
3、array('新字段', 'length', 'max'=>100),//如果是文本
1、2、3适当的最少要加一条,新字段才会被
- sublime text3 中文乱码解决
dyy_gusi
Sublime Text
sublime text3中文乱码解决
原因:缺少转换为UTF-8的插件
目的:安装ConvertToUTF8插件包
第一步:安装能自动安装插件的插件,百度“Codecs33”,然后按照步骤可以得到以下一段代码:
import urllib.request,os,hashlib; h = 'eb2297e1a458f27d836c04bb0cbaf282' + 'd0e7a30980927
- 概念了解:CGI,FastCGI,PHP-CGI与PHP-FPM
geeksun
PHP
CGI
CGI全称是“公共网关接口”(Common Gateway Interface),HTTP服务器与你的或其它机器上的程序进行“交谈”的一种工具,其程序须运行在网络服务器上。
CGI可以用任何一种语言编写,只要这种语言具有标准输入、输出和环境变量。如php,perl,tcl等。 FastCGI
FastCGI像是一个常驻(long-live)型的CGI,它可以一直执行着,只要激活后,不
- Git push 报错 "error: failed to push some refs to " 解决
hongtoushizi
git
Git push 报错 "error: failed to push some refs to " .
此问题出现的原因是:由于远程仓库中代码版本与本地不一致冲突导致的。
由于我在第一次git pull --rebase 代码后,准备push的时候,有别人往线上又提交了代码。所以出现此问题。
解决方案:
1: git pull
2:
- 第四章 Lua模块开发
jinnianshilongnian
nginxlua
在实际开发中,不可能把所有代码写到一个大而全的lua文件中,需要进行分模块开发;而且模块化是高性能Lua应用的关键。使用require第一次导入模块后,所有Nginx 进程全局共享模块的数据和代码,每个Worker进程需要时会得到此模块的一个副本(Copy-On-Write),即模块可以认为是每Worker进程共享而不是每Nginx Server共享;另外注意之前我们使用init_by_lua中初
- java.lang.reflect.Proxy
liyonghui160com
1.简介
Proxy 提供用于创建动态代理类和实例的静态方法
(1)动态代理类的属性
代理类是公共的、最终的,而不是抽象的
未指定代理类的非限定名称。但是,以字符串 "$Proxy" 开头的类名空间应该为代理类保留
代理类扩展 java.lang.reflect.Proxy
代理类会按同一顺序准确地实现其创建时指定的接口
- Java中getResourceAsStream的用法
pda158
java
1.Java中的getResourceAsStream有以下几种: 1. Class.getResourceAsStream(String path) : path 不以’/'开头时默认是从此类所在的包下取资源,以’/'开头则是从ClassPath根下获取。其只是通过path构造一个绝对路径,最终还是由ClassLoader获取资源。 2. Class.getClassLoader.get
- spring 包官方下载地址(非maven)
sinnk
spring
SPRING官方网站改版后,建议都是通过 Maven和Gradle下载,对不使用Maven和Gradle开发项目的,下载就非常麻烦,下给出Spring Framework jar官方直接下载路径:
http://repo.springsource.org/libs-release-local/org/springframework/spring/
s
- Oracle学习笔记(7) 开发PLSQL子程序和包
vipbooks
oraclesql编程
哈哈,清明节放假回去了一下,真是太好了,回家的感觉真好啊!现在又开始出差之旅了,又好久没有来了,今天继续Oracle的学习!
这是第七章的学习笔记,学习完第六章的动态SQL之后,开始要学习子程序和包的使用了……,希望大家能多给俺一些支持啊!
编程时使用的工具是PLSQL