- SpringMVC参数统一处理
一劍侵心
java杂记Spring
项目中遇到有些用户不小心输入空格,导致校验时,出现校验失败的现场,为此,写一个拦截器统一处理下入参。/***去掉前后空格和特殊字符**@authoryupeng*/@Slf4j@ControllerAdvicepublicclassOAuth2RequestBodyAdviceimplementsRequestBodyAdvice{@Overridepublicbooleansupports(Me
- CRM 微服务
山猪打不过家猪
C#微服务架构云原生
文章目录项目地址一、项目地址教程作者:教程地址:代码仓库地址:所用到的框架和插件:dbtairflow一、用户与认证服务主要功能:用户注册、登录、注销。认证(OAuth、JWT等)。权限和角色管理(RBAC/ABAC)。单点登录(SSO)。技术亮点:集成第三方身份认证(如Google、AzureAD)。使用APIGateway统一进行身份认证。客户管理服务主要功能:存储和管理客户信息(姓名、联系方
- Maui学习笔记-身份认证和授权案例
Mr.L70517
Maui学习笔记学习笔记iosc#http
在深入研究身份验证和授权时,可能会遇到很多术语。我们来简单介绍一下。Authentication,简单来讲时认证、验证身份检查用户名和密码,更高级方法设计到指纹、扫描、人脸识别或2FA认证。Authorization,授权,一旦通过身份认证,系统就可以决定当前用户是否有访问某些信息或执行一些操作的授权。OpenAuthorization(OAuth),开放授权,它允许第三方用户访问你的程序,而无需
- 使用python调用JIRA6 进行OAuth1认证获取AccessToken
yaoshengting
python#jirapython
Jira配置应用程序链接1)创建应用程序链接登录JIRA管理后台。转到Administration>Applications>ApplicationLinks。在输入框中输入外部应用程序的URL(例如GitLab或自定义应用),然后点击Createnewlink。2)配置ConsumerKey和PublicKey在创建应用链接的过程中:ConsumerKey:自定义一个唯一的字符串标识应用程序(例
- 为了避免工作疏忽,钉钉推送通知到个人(实例)
小小蚂蚁
钉钉java前端
publicstaticvoidmain(Stringargs[]){//获取tokenJSONObjectjson=newJSONObject();json.put("appKey","应用程序的唯一标识符");json.put("appSecret","应用程序(App)的密钥");StringURL="https://api.dingtalk.com/v1.0/oauth2/accessTo
- 【原生JS】如何优雅地读、改location.search(queryString或GET参数)
warmbook
前端javascript开发语言ecmascript
应用场景location.search完全由JS脚本管理,并且需要不刷新页面地修改其内容。例如在Oauth2授权中,如果是前端取参提交给后端API向平台方请求accessToken,需要及时删除GET参数中的code,以防用户刷新浏览器导致用失效的code处理登录。实现思路将queryString转为对象并用ES6的Proxy代理,在set、delete钩子中调用history.replaceSt
- 【Python】Python-JOSE:Python 中的 JSON Web Token 处理库
@Unity打怪升级
Pythonpythonjson人工智能前端开发语言开源机器学习
Python-JOSE是一个用于处理JSONWebToken(JWT)和JOSE(JSONObjectSigningandEncryption)标准的Python库。它支持对JWT进行签名、加密、解密和验证等操作,是处理基于OAuth2.0和OpenIDConnect协议的身份验证和授权任务的理想选择。Python-JOSE实现了JOSE规范中定义的JWS(JSONWebSignature)、JW
- 客户订单管理的微服务例子
自由鬼
Java程序微服务架构云原生
下述代码实现了一个客户基本信息管理的微服务,包含以下功能:1、用户认证:使用SpringSecurity和OAuth2进行认证。配置了角色和权限控制。2、角色授权:通过@PreAuthorize注解实现角色授权,只有管理员可以执行某些操作。3、调用其他微服务:使用FeignClient调用用户管理微服务,从中获取用户数据。此示例具备扩展性,可以轻松增加其他功能,例如更多的RESTAPI或与其他微服
- 用java 实现 同意授权给公众号访问其信息。这通常通过将用户重定向到一个由微信提供的授权页面完成。
用心去追梦
java微信开发语言
在Java中实现微信公众号的OAuth2.0网页授权流程,主要涉及构建一个HTTP请求来重定向用户到微信提供的授权页面。以下是一个简单的示例,演示如何创建这个重定向链接并将其发送给客户端浏览器。步骤1:构建授权URL首先,你需要根据微信官方文档构造授权URL。这个URL将包含你的应用ID(appid)、回调地址(redirect_uri)、响应类型(response_type=code)、授权作用
- 用java 实现 生成二维码 同意授权给公众号访问其信息。这通常通过将用户重定向到一个由微信提供的授权页面完成。
用心去追梦
java微信python
要使用Java实现生成二维码以同意授权给微信公众号访问用户信息,你可以结合OAuth2.0网页授权流程与微信提供的二维码生成接口。具体来说,你需要创建一个带有授权链接的二维码,当用户扫描并同意授权后,可以重定向到指定页面。步骤1:构建授权URL首先,根据之前的指导构建授权URL。这个URL将用于生成二维码,使得用户在扫描二维码时被重定向到微信的授权页面。步骤2:使用微信API生成二维码微信提供了两
- midjourney初学者必看(迅速入门)
会飞the羊
midjourney
Midjourney初步学习:基本操作流程:-新建一个服务器-在输入框里添加MJROBOT:https://discord.com/oauth2/authorize?client_id=936929561302675456&permissions=2147601472&scope=applications.commands%20bot-输入/→选择imagine开始写prompt-prompt使用
- 使用 Next 14 + NextAuth 4 + Strapi v4进行 Google 和凭据提供商身份验证的完整指南(02)
javascript前端
CSS技巧与案例详解vue2与vue3技巧合集VueUse源码解读NextAuthv4介绍NextAuth是一个开源的身份验证解决方案,适用于全栈(Next)应用程序。它支持不同的登录方式,如OAuth提供商(如Google、GitHub等)、凭据(经典的邮箱+密码)以及邮箱登录(通过用户点击的"魔法链接")。它还提供不同的数据库适配器,可以直接将登录信息存入特定的数据库(如MongoDB)或与O
- php 实现JWT
每天瞎忙的农民工
phpphp
在PHP中,JSONWebToken(JWT)是一种开放标准(RFC7519)用于在各方之间作为JSON对象安全地传输信息。JWT通常用于身份验证系统,如OAuth2或基于令牌的身份验证。以下是一个基本的PHP实现JWT生成和验证的代码示例。JWT的组成部分JWT包含三个部分:Header(头部):说明算法和令牌类型。Payload(有效载荷):包含声明(如用户数据、过期时间等)。Signatur
- springcloud — 微服务鉴权管理Spring Security原理解析(二)
RachelHwang
springcloudspringjavaspringsecurityoauth2springcloud
引言:回顾之前介绍的OAuth2简单分析与介绍,微服务鉴权管理之OAuth2原理解析(一),前面的部分,我们关注了SpringSecurity是如何完成认证工作的,但是另外一部分核心的内容:过滤器,一直没有提到,我们已经知道SpringSecurity使用了springSecurityFilterChain作为了安全过滤的入口,这一节主要分析一下这个过滤器链都包含了哪些关键的过滤器,并且各自的使命
- 三十五、Gin注册功能实战
Boo_T
gogingolang开发语言后端
目录一、创建请求组二、service下创建register.go文件三、实现密码加密功能四、在register方法中使用encryptPassword函数一、创建请求组const(rootPath="/api/"noAuthPath="/out/api/")//创建请求组noAuth:=r.Group(noAuthPath)//注册功能路由绑定noAuth.POST("cms/register",
- Spring Boot整合Spring Security+JWT+OAuth 2.0 实现认证鉴权登录(框架介绍)
星空下夜猫子
springspringboot数据库
简介SpringSecurity框架描述SpringSecurity是一个基于Spring框架的安全性框架,可以为Web应用程序提供身份验证(Authentication)、授权(Authorization)、攻击防御等安全功能。SpringSecurity框架提供了一整套的身份验证、授权、ACL(访问控制列表)等模块和类库,还提供了一系列的安全过滤器、安全标签等,可以方便地实现常见的安全性控制。
- Elasticsearch 安装
哒哒-blog
Elasticsearchelasticsearchjenkins大数据
下载安装elasticsearch下载链接运行:bin\elasticsearch.bat设置密码:.\bin\elasticsearch-setup-passwordsinteractive这边设置密码遇到一个坑PSG:\elasticsearch-8.8.1>.\bin\elasticsearch-setup-passwordsinteractiveFailedtoauthenticateus
- Spring Cloud云架构 - SSO单点登录之OAuth2.0 根据token获取用户信息(4)
初夏_91fb
上一篇我根据框架中OAuth2.0的使用总结,画了SSO单点登录之OAuth2.0登出流程,今天我们看一下根据用户token获取yoghurt信息的流程:image/***根据token获取用户信息*@paramaccessToken*@return*@throwsException*/@RequestMapping(value="/user/token/{accesstoken}",method
- 【网络安全】漏洞挖掘之会话管理缺陷
秋说
网络安全web安全漏洞挖掘会话管理
未经许可,不得转载。文章目录正文正文目标:example.com该站点允许存在主要邮箱和次要邮箱。在尝试使用次要邮箱和密码登录时,由于账户最初是通过主邮箱创建的,无法登录。于是,我通过次要邮箱使用GoogleOAuth进行登录。令人意外的是,我成功通过GoogleOAuth登录了该账户。接着,我在两个浏览器上登录了同一个账户:Chrome浏览器使用主邮箱(
[email protected])和
- 这可能是全网最详细的 Spring Cloud OAuth2 单点登录使用教程了,妈妈再也不用担心我被面试官吊打了!
2401_84558091
程序员java面试学习
最后对于很多Java工程师而言,想要提升技能,往往是自己摸索成长,不成体系的学习效果低效漫长且无助。整理的这些资料希望对Java开发的朋友们有所参考以及少走弯路,本文的重点是你有没有收获与成长,其余的都不重要,希望读者们能谨记这一点。再分享一波我的Java面试真题+视频学习详解+技能进阶书籍本文已被CODING开源项目:【一线大厂Java面试题解析+核心总结学习笔记+最新讲解视频+实战项目源码】收
- 【DevOps工具篇】使用Ansible部署Keycloak oauth2proxy 和 单点登录(SSO)设置
小涵
DevOps企业级项目实战devopsansible运维ldapkeycloakproxyoauth
【DevOps工具篇】使用Ansible部署Keycloakoauth2proxy和单点登录(SSO)设置目录【DevOps工具篇】使用Ansible部署Keycloakoauth2proxy和单点登录(SSO)设置Ansible基础知识部署Keycloak创建OIDC-客户端创建oauth2proxy部署顶级AnsiblePlaybookHost.iniplaybook.yaml推荐超级课程:D
- <二> speed_bounds_decider(3)
不知道是谁2
自动驾驶apollo规划控制
st_boundary_mapper.cc/*******************************************************************************Copyright2017TheApolloAuthors.AllRightsReserved.**LicensedundertheApacheLicense,Version2.0(the"Lice
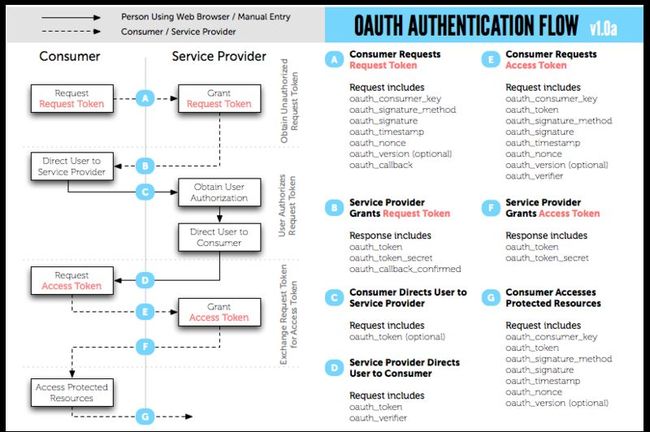
- Oauth2简介
Lill_bin
杂谈githubgit网络服务器大数据java
OAuth2.0是一个行业标准的协议,用于授权。它允许应用程序代表用户访问服务器上的数据,而无需暴露用户的用户名和密码。OAuth2.0专注于简化客户端开发人员的操作,同时为Web应用、桌面应用、手机和客厅设备提供专门的认证流程。OAuth2.0的核心概念:资源所有者(ResourceOwner):指的是数据的拥有者,即用户。在OAuth2.0中,资源所有者授权第三方应用访问其数据。资源服务器(R
- Spring-Security(二)OAuth2认证详解(持续更新)
lbmydream
springcloud架构spring探析springjava后端
SpringSecurity&Oauth2系列:SpringSecurity(一)源码分析及认证流程SpringSecurity(二)OAuth2认证详解及自定义异常处理文章目录1、OAuth2.0简介1.1OAuth2.0相关名词解释1.2四种授权模式1.3、OAuth2框架1.4OAuth2.0客户端提供功能2、OAuth2.0认证服务2.1SpringSecurityOAuth2提供的程序实
- 支付宝生活号获取用户授权
Strawberry96
支付宝生活号前端
为了下次不用再去看一遍官方文档,简单的做一下笔记。想了解更多的细节,请移步支付宝官方文档1、用户授权,拼接的url,如下:获取用户信息的授权scope=auth_user:https://openauth.alipay.com/oauth2/publicAppAuthorize.htm?app_id=APPID&scope=auth_user&redirect_uri=ENCODED_URL?st
- 【JS 逆向百例】当乐网登录接口参数逆向
K哥爬虫
声明本文章中所有内容仅供学习交流,严禁用于商业用途和非法用途,否则由此产生的一切后果均与作者无关,若有侵权,请联系我立即删除!逆向目标目标:当乐网登录主页:https://oauth.d.cn/auth/goLogin.html接口:https://oauth.d.cn/auth/login逆向参数:QueryStringParameters:pwd:26fac08e6b524bef29c0947
- Dzzoffice 入口文件所对应的程序文件
小胡2024
DzzOffice小胡社区前端javascript开源软件开发语言php
介绍入口文件是一个PHP文件,用于启动系统流程控制。入口文件所对应的程序文件包括多个类文件和配置文件。入口文件对应目录admin.php对应/admin目录;index.php对应/dzz目录;user.php对应/user目录;misc.php对应/misc目录;oauth.php对应/dzz目录;avatar.php对应/data/avatar目录;程序文件目录下通常含有以下目录和文件clas
- 微信投票系统源码开源版 投票活动制作平台源码
源码师傅
源码分享php源码软件
分享一个微信投票系统源码,系统基于微信公众平台,含完整搭建教程和程序包,可以任意制作各种投票活动。主要功能一览:01.界面配色后台自定义,轻松搭建不同风格,我们后台还内置3套模板,一键随意切换02.100%防暴力高并发刷票03.支持微信开放平台,订阅号如服务号操作,用户体验极佳04.支持所有类型公众号活动(非服务号需要借用认证服务号oauth权限即可,未认证号不能借用支付礼物)05.首页列表全aj
- 教程:在Spring Boot应用中集成OAuth 2.0认证
微赚淘客系统开发者@聚娃科技
springboot后端java
教程:在SpringBoot应用中集成OAuth2.0认证大家好,我是免费搭建查券返利机器人省钱赚佣金就用微赚淘客系统3.0的小编,也是冬天不穿秋裤,天冷也要风度的程序猿!OAuth2.0是一种广泛使用的授权框架,用于安全地授权第三方应用程序访问HTTP服务,而无需将用户的用户名和密码暴露给第三方。在现代的分布式系统中,使用OAuth2.0认证可以有效地保护API端点和用户数据。本文将介绍如何在S
- Spring OAuth2.0 OIDC详解
Mr. bigworth
OAuth2.0springspringboot
OIDC简介作用身份验证:OIDC在OAuth2授权的基础上增加了身份验证功能,通过IDToken验证用户身份的真实性。用户信息获取:通过IDToken和用户信息端点,客户端可以获取用户的详细信息。安全性增强:通过引入nonce参数和IDToken,OIDC增强了请求的安全性,防止重放攻击等安全问题。总的来说,OIDC提供了比OAuth2更加完整和安全的身份验证和授权机制,确保在授权第三方应用访问
- ios内付费
374016526
ios内付费
近年来写了很多IOS的程序,内付费也用到不少,使用IOS的内付费实现起来比较麻烦,这里我写了一个简单的内付费包,希望对大家有帮助。
具体使用如下:
这里的sender其实就是调用者,这里主要是为了回调使用。
[KuroStoreApi kuroStoreProductId:@"产品ID" storeSender:self storeFinishCallBa
- 20 款优秀的 Linux 终端仿真器
brotherlamp
linuxlinux视频linux资料linux自学linux教程
终端仿真器是一款用其它显示架构重现可视终端的计算机程序。换句话说就是终端仿真器能使哑终端看似像一台连接上了服务器的客户机。终端仿真器允许最终用户用文本用户界面和命令行来访问控制台和应用程序。(LCTT 译注:终端仿真器原意指对大型机-哑终端方式的模拟,不过在当今的 Linux 环境中,常指通过远程或本地方式连接的伪终端,俗称“终端”。)
你能从开源世界中找到大量的终端仿真器,它们
- Solr Deep Paging(solr 深分页)
eksliang
solr深分页solr分页性能问题
转载请出自出处:http://eksliang.iteye.com/blog/2148370
作者:eksliang(ickes) blg:http://eksliang.iteye.com/ 概述
长期以来,我们一直有一个深分页问题。如果直接跳到很靠后的页数,查询速度会比较慢。这是因为Solr的需要为查询从开始遍历所有数据。直到Solr的4.7这个问题一直没有一个很好的解决方案。直到solr
- 数据库面试题
18289753290
面试题 数据库
1.union ,union all
网络搜索出的最佳答案:
union和union all的区别是,union会自动压缩多个结果集合中的重复结果,而union all则将所有的结果全部显示出来,不管是不是重复。
Union:对两个结果集进行并集操作,不包括重复行,同时进行默认规则的排序;
Union All:对两个结果集进行并集操作,包括重复行,不进行排序;
2.索引有哪些分类?作用是
- Android TV屏幕适配
酷的飞上天空
android
先说下现在市面上TV分辨率的大概情况
两种分辨率为主
1.720标清,分辨率为1280x720.
屏幕尺寸以32寸为主,部分电视为42寸
2.1080p全高清,分辨率为1920x1080
屏幕尺寸以42寸为主,此分辨率电视屏幕从32寸到50寸都有
适配遇到问题,已1080p尺寸为例:
分辨率固定不变,屏幕尺寸变化较大。
如:效果图尺寸为1920x1080,如果使用d
- Timer定时器与ActionListener联合应用
永夜-极光
java
功能:在控制台每秒输出一次
代码:
package Main;
import javax.swing.Timer;
import java.awt.event.*;
public class T {
private static int count = 0;
public static void main(String[] args){
- Ubuntu14.04系统Tab键不能自动补全问题解决
随便小屋
Ubuntu 14.04
Unbuntu 14.4安装之后就在终端中使用Tab键不能自动补全,解决办法如下:
1、利用vi编辑器打开/etc/bash.bashrc文件(需要root权限)
sudo vi /etc/bash.bashrc
接下来会提示输入密码
2、找到文件中的下列代码
#enable bash completion in interactive shells
#if
- 学会人际关系三招 轻松走职场
aijuans
职场
要想成功,仅有专业能力是不够的,处理好与老板、同事及下属的人际关系也是门大学问。如何才能在职场如鱼得水、游刃有余呢?在此,教您简单实用的三个窍门。
第一,多汇报
最近,管理学又提出了一个新名词“追随力”。它告诉我们,做下属最关键的就是要多请示汇报,让上司随时了解你的工作进度,有了新想法也要及时建议。不知不觉,你就有了“追随力”,上司会越来越了解和信任你。
第二,勤沟通
团队的力
- 《O2O:移动互联网时代的商业革命》读书笔记
aoyouzi
读书笔记
移动互联网的未来:碎片化内容+碎片化渠道=各式精准、互动的新型社会化营销。
O2O:Online to OffLine 线上线下活动
O2O就是在移动互联网时代,生活消费领域通过线上和线下互动的一种新型商业模式。
手机二维码本质:O2O商务行为从线下现实世界到线上虚拟世界的入口。
线上虚拟世界创造的本意是打破信息鸿沟,让不同地域、不同需求的人
- js实现图片随鼠标滚动的效果
百合不是茶
JavaScript滚动属性的获取图片滚动属性获取页面加载
1,获取样式属性值
top 与顶部的距离
left 与左边的距离
right 与右边的距离
bottom 与下边的距离
zIndex 层叠层次
例子:获取左边的宽度,当css写在body标签中时
<div id="adver" style="position:absolute;top:50px;left:1000p
- ajax同步异步参数async
bijian1013
jqueryAjaxasync
开发项目开发过程中,需要将ajax的返回值赋到全局变量中,然后在该页面其他地方引用,因为ajax异步的原因一直无法成功,需将async:false,使其变成同步的。
格式:
$.ajax({ type: 'POST', ur
- Webx3框架(1)
Bill_chen
eclipsespringmaven框架ibatis
Webx是淘宝开发的一套Web开发框架,Webx3是其第三个升级版本;采用Eclipse的开发环境,现在支持java开发;
采用turbine原型的MVC框架,扩展了Spring容器,利用Maven进行项目的构建管理,灵活的ibatis持久层支持,总的来说,还是一套很不错的Web框架。
Webx3遵循turbine风格,velocity的模板被分为layout/screen/control三部
- 【MongoDB学习笔记五】MongoDB概述
bit1129
mongodb
MongoDB是面向文档的NoSQL数据库,尽量业界还对MongoDB存在一些质疑的声音,比如性能尤其是查询性能、数据一致性的支持没有想象的那么好,但是MongoDB用户群确实已经够多。MongoDB的亮点不在于它的性能,而是它处理非结构化数据的能力以及内置对分布式的支持(复制、分片达到的高可用、高可伸缩),同时它提供的近似于SQL的查询能力,也是在做NoSQL技术选型时,考虑的一个重要因素。Mo
- spring/hibernate/struts2常见异常总结
白糖_
Hibernate
Spring
①ClassNotFoundException: org.aspectj.weaver.reflect.ReflectionWorld$ReflectionWorldException
缺少aspectjweaver.jar,该jar包常用于spring aop中
②java.lang.ClassNotFoundException: org.sprin
- jquery easyui表单重置(reset)扩展思路
bozch
formjquery easyuireset
在jquery easyui表单中 尚未提供表单重置的功能,这就需要自己对其进行扩展。
扩展的时候要考虑的控件有:
combo,combobox,combogrid,combotree,datebox,datetimebox
需要对其添加reset方法,reset方法就是把初始化的值赋值给当前的组件,这就需要在组件的初始化时将值保存下来。
在所有的reset方法添加完毕之后,就需要对fo
- 编程之美-烙饼排序
bylijinnan
编程之美
package beautyOfCoding;
import java.util.Arrays;
/*
*《编程之美》的思路是:搜索+剪枝。有点像是写下棋程序:当前情况下,把所有可能的下一步都做一遍;在这每一遍操作里面,计算出如果按这一步走的话,能不能赢(得出最优结果)。
*《编程之美》上代码有很多错误,且每个变量的含义令人费解。因此我按我的理解写了以下代码:
*/
- Struts1.X 源码分析之ActionForm赋值原理
chenbowen00
struts
struts1在处理请求参数之前,首先会根据配置文件action节点的name属性创建对应的ActionForm。如果配置了name属性,却找不到对应的ActionForm类也不会报错,只是不会处理本次请求的请求参数。
如果找到了对应的ActionForm类,则先判断是否已经存在ActionForm的实例,如果不存在则创建实例,并将其存放在对应的作用域中。作用域由配置文件action节点的s
- [空天防御与经济]在获得充足的外部资源之前,太空投资需有限度
comsci
资源
这里有一个常识性的问题:
地球的资源,人类的资金是有限的,而太空是无限的.....
就算全人类联合起来,要在太空中修建大型空间站,也不一定能够成功,因为资源和资金,技术有客观的限制....
&
- ORACLE临时表—ON COMMIT PRESERVE ROWS
daizj
oracle临时表
ORACLE临时表 转
临时表:像普通表一样,有结构,但是对数据的管理上不一样,临时表存储事务或会话的中间结果集,临时表中保存的数据只对当前
会话可见,所有会话都看不到其他会话的数据,即使其他会话提交了,也看不到。临时表不存在并发行为,因为他们对于当前会话都是独立的。
创建临时表时,ORACLE只创建了表的结构(在数据字典中定义),并没有初始化内存空间,当某一会话使用临时表时,ORALCE会
- 基于Nginx XSendfile+SpringMVC进行文件下载
denger
应用服务器Webnginx网络应用lighttpd
在平常我们实现文件下载通常是通过普通 read-write方式,如下代码所示。
@RequestMapping("/courseware/{id}")
public void download(@PathVariable("id") String courseID, HttpServletResp
- scanf接受char类型的字符
dcj3sjt126com
c
/*
2013年3月11日22:35:54
目的:学习char只接受一个字符
*/
# include <stdio.h>
int main(void)
{
int i;
char ch;
scanf("%d", &i);
printf("i = %d\n", i);
scanf("%
- 学编程的价值
dcj3sjt126com
编程
发一个人会编程, 想想以后可以教儿女, 是多么美好的事啊, 不管儿女将来从事什么样的职业, 教一教, 对他思维的开拓大有帮助
像这位朋友学习:
http://blog.sina.com.cn/s/articlelist_2584320772_0_1.html
VirtualGS教程 (By @林泰前): 几十年的老程序员,资深的
- 二维数组(矩阵)对角线输出
飞天奔月
二维数组
今天在BBS里面看到这样的面试题目,
1,二维数组(N*N),沿对角线方向,从右上角打印到左下角如N=4: 4*4二维数组
{ 1 2 3 4 }
{ 5 6 7 8 }
{ 9 10 11 12 }
{13 14 15 16 }
打印顺序
4
3 8
2 7 12
1 6 11 16
5 10 15
9 14
13
要
- Ehcache(08)——可阻塞的Cache——BlockingCache
234390216
并发ehcacheBlockingCache阻塞
可阻塞的Cache—BlockingCache
在上一节我们提到了显示使用Ehcache锁的问题,其实我们还可以隐式的来使用Ehcache的锁,那就是通过BlockingCache。BlockingCache是Ehcache的一个封装类,可以让我们对Ehcache进行并发操作。其内部的锁机制是使用的net.
- mysqldiff对数据库间进行差异比较
jackyrong
mysqld
mysqldiff该工具是官方mysql-utilities工具集的一个脚本,可以用来对比不同数据库之间的表结构,或者同个数据库间的表结构
如果在windows下,直接下载mysql-utilities安装就可以了,然后运行后,会跑到命令行下:
1) 基本用法
mysqldiff --server1=admin:12345
- spring data jpa 方法中可用的关键字
lawrence.li
javaspring
spring data jpa 支持以方法名进行查询/删除/统计。
查询的关键字为find
删除的关键字为delete/remove (>=1.7.x)
统计的关键字为count (>=1.7.x)
修改需要使用@Modifying注解
@Modifying
@Query("update User u set u.firstna
- Spring的ModelAndView类
nicegege
spring
项目中controller的方法跳转的到ModelAndView类,一直很好奇spring怎么实现的?
/*
* Copyright 2002-2010 the original author or authors.
*
* Licensed under the Apache License, Version 2.0 (the "License");
* yo
- 搭建 CentOS 6 服务器(13) - rsync、Amanda
rensanning
centos
(一)rsync
Server端
# yum install rsync
# vi /etc/xinetd.d/rsync
service rsync
{
disable = no
flags = IPv6
socket_type = stream
wait
- Learn Nodejs 02
toknowme
nodejs
(1)npm是什么
npm is the package manager for node
官方网站:https://www.npmjs.com/
npm上有很多优秀的nodejs包,来解决常见的一些问题,比如用node-mysql,就可以方便通过nodejs链接到mysql,进行数据库的操作
在开发过程往往会需要用到其他的包,使用npm就可以下载这些包来供程序调用
&nb
- Spring MVC 拦截器
xp9802
spring mvc
Controller层的拦截器继承于HandlerInterceptorAdapter
HandlerInterceptorAdapter.java 1 public abstract class HandlerInterceptorAdapter implements HandlerIntercep