- springboot 外卖-Day3-1
CHARLIIE
springbootjava后端
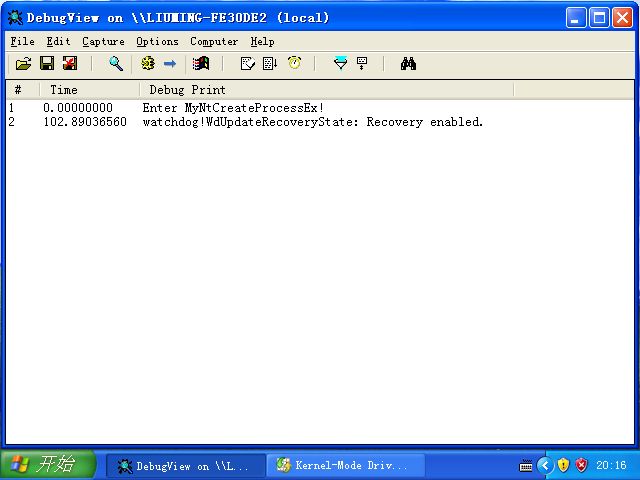
进度好难推救命自定义注解注解@Target和@Retention的作用_target注解retention注解-CSDN博客其实都是规定动作AOP三点:切面、切入点、通知SpringBoot中使用Aspect实现切面,超详细_aspect切面-CSDN博客自定义注解中定义了value这个方法参数要有@AutoFill(value=OperationType.INSERT)@RequestBody要
- 推动视觉AI边界,智象未来HiDream荣登全球技术先锋榜单
雷焰财经
人工智能AIGC计算机视觉
近日,世界经济论坛“全球技术先锋”荣誉榜单正式揭晓,智象未来HiDream凭借尖端技术成就入选。智象未来HiDream成立于2023年3月,是一家专注于多模态AIGC技术应用的公司,由加拿大工程院外籍院士IEEE/IAPR/CAAIFellow梅涛博士创立。回顾过往,众多知名企业,如Airbnb、Google、Twitter和Spotify等,都曾获得世界经济论坛的“全球技术先锋”称号。然而,今年
- MySQL(105) 如何进行数据库分片?
辞暮尔尔-烟火年年
MySQL数据库mysql
数据库分片(Sharding)是一种将数据库表的数据分布到多个物理数据库实例上的技术,以提高数据库的性能和可扩展性。下面将详细介绍如何在Java中实现数据库分片,包括分片策略、分片管理和数据访问。1.环境准备假设我们使用SpringBoot和MySQL,并且需要分片的表是users表。2.分片策略常见的分片策略有哈希分片(HashSharding)、范围分片(RangeSharding)和列表分片
- 一只亚洲水牛跳水视频提示词-一语乾坤韵芳华-仙界AI——仙盟创梦IDE
未来之窗软件服务
人工智能人工智能东方仙盟仙盟创梦IDEAI视频
提示词奥运会期间,一只亚洲水牛,从10米高的跳水板,跳向游泳池,慢走几步起跳,跳跃过程中进行后空翻转,进入游泳池溅起水花,电视镜头英文DuringtheOlympicGames,anAsianwaterbuffalojumpedintotheswimmingpoolfroma10-meter-highdivingboard.Itwalkedslowlyforafewstepsbeforetakin
- 虚幻引擎编程反射系统实现
污领巾
虚幻php游戏引擎
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档文章目录前言1、反射的核心实现流程1.1宏定义标记1.2UnrealHeaderTool(UHT)处理1.3生成的代码结构1.4运行时反射数据注册2、反射系统的关键数据结构2.1UClass2.2UProperty及其派生类2.3UFunction3、反射的实际应用场景3.1蓝图与C++交互3.2序列化与反序列化3.3网络同步(Rep
- 通过虚幻控件Slate了解虚幻GC(Garbage Collection, GC)的垃圾回收系统
污领巾
虚幻jvmjava
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档文章目录前言一、GC的核心机制1.1根集(RootSet)1.2标记阶段(Marking)1.3清扫阶段(Sweeping)二、控件生命周期管理2.1控件创建2.2添加到视口(成为根集)2.3移除视口(断开根集)2.4显式销毁三、代码示例与流程分析3.1控件创建与添加3.2控件移除与GC回收3.3防止误回收:使用UPROPERTY四、
- 技术实录-从 MySQL 启动失败到大小写兼容恢复:一次完整故障排查复盘20250614
Narutolxy
智浪初航技术干货分享mysqladbandroid
技术实录|从MySQL启动失败到大小写兼容恢复:一次完整故障排查复盘作者:Narutolxy|日期:2025-06-14|标签:MySQL、权限修复、大小写敏感、数据迁移引言:一次意外引发的MySQL修复实践在一次对客户MySQL数据库进行表迁移和大小写兼容性调整的过程中,我遇到了一个典型但复杂的问题——MySQL配置了lower_case_table_names=1后无法启动,root用户密码遗
- DAY 42 Grad-CAM与Hook函数
@浙大疏锦行https://blog.csdn.net/weixin_45655710知识点回顾回调函数lambda函数hook函数的模块钩子和张量钩子Grad-CAM的示例作业:理解下今天的代码即可importtorchimporttorch.nnasnnimporttorch.nn.functionalasFimporttorchvisionimporttorchvision.transfor
- vscode插件和源码通过命令进行通信
zhouhangzooo
【VisualStudioCode】vscode通信vscode命令
本文讲述一下vscode插件和源码通过命令进行通信原文链接:https://zhouhangzooo.github.io/2019/04/10/vscode插件与源码通信/在之前"vscode插件与webview相互通信"文章中,讲述webview和插件进行通信,里面有个注册命令,之前文章没有详细代码,其实代码vscoode官网都有,##接下来要说命令,那么先贴一下注册命令的代码123456789
- 免费实时AI图片编辑工具-多模态大模型:GPT-4o、grok、豆包、BAGEL、MagicQuill、OmniGen2
loong_XL
AIGCaigc
纯自然语言对话实现图像编辑;参考https://zhuanlan.zhihu.com/p/1890036563586577897GPT-4ohttps://chatgpt.com/geminihttps://gemini.google.com/grokhttps://grok.com/?referrer=website
- react gsap动画库使用详解之scroll滑动动画
伍哥的传说
前端源码分享react.js前端前端框架vue.jsvue动画javascript
简介gsap高性能的JavaScript动画库,在现代网页设计和开发中运用。安装npminstallgsapReact框架中使用可以考滤使用react-gsap-enhancer库,或者@gasp/react。类组件使用react-gsap-enhancer高阶组件,函数组件使用@gasp/react自定义Hook。npminstallreact-gsap-enhancer#oryarnaddre
- Spring Boot获取节假日API
涛哥是个大帅比
Spring节假日休息日节假日apispringboot工作日
项目场景:需要知道某一天是不是节假日,或者是休息日。问题描述我们知道每年的假节日要等国家规定好,我们才能知道,所以自己是算不出的。马上想到的两个解决方法:1.通过调用互联网的节假日API(优点:方便,缺点:主动权在别人手里,万一别人的服务器出了问题,自己的服务也会受影响)2.每年自己手动配置一次(优点:安全不会出问题,缺点:麻烦)感觉都不是很完美,最后把这两种结合一下,生成的解决方案:每年年底定时
- SpringCloud-config配置中心
Enter_灵猴
每日一记
config服务端启动类要加@EnableConfigServerbootstrap.propertiesspring.application.name=config-serverserver.port=f服务端启动端口号spring.cloud.config.server.git.uri=https://github.com/登陆账号/仓库名spring.cloud.config.server.
- gem5-gpu教程 DSENT (Design Space Exploration of Networks Tool) 配合gem5
事橙1999
gem5-gpu硬件架构
概述DSENT是一种建模工具,旨在快速探索电子和新兴的片上光电网络(NoC)的设计空间。它为各种网络组件提供分析和参数化模型,并可在一系列技术假设下移植。给定架构级参数,DSENT从电气和光学构建块分层构建指定的模型,并输出详细的功率和面积估计。版本当前:0.91(2012年6月26日)最新版本或其他信息可在以下网址找到https://sites.google.com/site/mitdsent系
- 通过 es6的标签模板字符串,调用函数
改了一个昵称
es6javascript
es6的标签模板字符串/***讲一下es6的标签模板字符串*/functionfoo(...args){console.log(args);//打印的是:['why',18,1.88]}`调用foo函数,方式一`//foo('why',18,1.88)`调用foo函数,方式二`letname='coder'letage=19//也可以这样调用foo函数foo`mynameis${name},age
- python 获取节假日
AI算法网奇
python宝典
www.easybots.cn是不准的,不能用,比如20190913,不能判断节假日#-*-coding:utf-8-*-importjsonimporturllib.requestimporttimeimportdatetimedefa1(date_str):server_url="http://api.goseek.cn/Tools/holiday?date="#server_url="htt
- Error in created hook: “TypeError: Cannot read properties of undefined (reading ‘style‘)“
本郡主是喵
#JS相关vue.jsjavascript前端
问题解决这个错误通常在Vue组件的created钩子函数中发生,它表示在该钩子函数中尝试读取一个未定义的对象的style属性。造成这个错误的原因可能是:你在`created`钩子函数中引用了一个未定义的数据属性或计算属性。在`created`钩子函数中尝试访问组件的DOM元素,但DOM元素尚未完全加载或渲染。为了解决这个问题,你可以按照以下步骤进行排查:检查在created钩子函数中访问的数据属性
- 【节假日】通过开放Api获取节假日数据并保存到json文件
Leslie_Lei
#随笔jsonjava节日
目录依赖节假日数据返回结果类工具类依赖com.fasterxml.jackson.corejackson-databindcom.google.code.gsongson2.8.6cn.hutoolhutool-all5.8.18org.projectlomboklombok节假日数据返回结果类HolidayResponseimportcom.fasterxml.jackson.annotatio
- 一个非常好用的快速生成数据库表映射工具-Screw
qq_21526409
数据库java
将数据库的表结构生成文档需要引入的依赖org.springframework.bootspring-boot-starter-jdbcorg.springframework.bootspring-boot-starter-testtestcn.smallbun.screwscrew-core1.0.5com.zaxxerHikariCP5.1.0测试代码importcn.smallbun.scre
- Veo 3 视频生成大模型完整操作教程(2025)
迎风斯黄
音视频人工智能
随着AI多模态能力的飞跃,GoogleDeepMind发布的Veo3成为了生成视频领域的一颗重磅炸弹。它不仅能够根据文本生成高质量的视频画面,还能同步生成对白、背景音和环境音,是目前最接近真正“AI导演”的大模型。本文将带你详细了解Veo3的功能、使用方式、提示词撰写技巧,以及完整的创作流程,适合希望用AI快速生成短视频、概念片段、广告、剧情短片等内容的创作者与开发者。一、Veo3是什么?Veo3
- Netty堆内存字节缓冲区深度解析
lifallen
Nettyjava后端nio开发语言算法
UnpooledHeapByteBufUnpooledHeapByteBuf是Netty中基于堆内存(JVM堆)的非池化字节缓冲区实现。它直接使用Java的byte[]数组作为底层存储,适用于常规的JVM堆内存分配场景。核心特点如下:非池化设计:每次分配都会创建新的字节数组,不涉及对象复用。堆内存存储:数据存储在JVM堆上,受GC管理。引用计数:继承AbstractReferenceCounted
- SpringBoot-SpringBoot整合Swagger使用教程(详细图文介绍,一篇就够了)
只吹45°风
Springspringbootswagger整合
前言日常开发中,接口都是和开发文档相结合的。不论是和前端对接还是三方对接亦或者是接口留档,当我们开发完接口后,都需要去创建对应的接口文档。而修改接口后也要修改相对应的接口文档,但是这个真的很容易疏漏。而且相对于繁重的开发任务而言,维护文档又是一个同样让人心累的事情。那么有没有能针对我们的接口自动生成接口说明的工具呢,这样我们就不需要特意去生成和实时的去维护api文档?答案当然是-有,这就是今天要介
- 基于MySQL的分布式锁实现(Spring Boot + MyBatis)
weixin_43833540
mysql分布式springboot
基于MySQL的分布式锁实现(SpringBoot+MyBatis)实现原理基于数据库的唯一索引特性实现分布式锁,通过插入唯一索引记录表示获取锁,删除记录表示释放锁。1.创建锁表首先需要在MySQL中创建一个锁表,用于存储锁信息:CREATETABLE`distributed_lock`(`id`bigint(20)NOTNULLAUTO_INCREMENT,`lock_key`varchar(6
- xdata的使用
一切顺势而行
bigdata
{"job":{"setting":{"speed":{"channel":3},"errorLimit":{"record":0,"percentage":0.02}},"content":[{"reader":{"name":"mysqlreader","parameter":{"username":"root","password":"123456","column":["id","name
- Host '*' is not allowed to connect to this MariaDB server
weixin_34358365
数据库python
2019独角兽企业重金招聘Python工程师标准>>>MYSQL权限问题原因:安装MySQL时没有勾选“Enablerootaccessfromremotemachines”如何开启MySQL的远程帐号-1)首先以root帐户登陆MySQL在Windows主机中点击开始菜单,运行,输入“cmd”,进入控制台,然后cd进入MySQL的bin目录下,然后输入下面的命令。>MySQL-uroot-p12
- 解决报错:错误1130- Host xxx is not allowed to connect to this MariaDb server
phymat.nico
系统内核
这个问题是因为在数据库服务器中的mysql数据库中的user的表中没有权限(也可以说没有用户),下面将记录我遇到问题的过程及解决的方法。在搭建完LNMP环境后用Navicate连接出错遇到这个问题首先到mysql所在的服务器上用连接进行处理1、连接服务器:mysql-uroot-p2、看当前所有数据库:showdatabases;3、进入mysql数据库:usemysql;4、查看mysql数据库
- PAT A1052Linked List Sorting(测试点3:输出首节点地址时也要保证格式)
明亮的托比
PATPAT真题静态链表
#include#include#includeusingnamespacestd;#defineMAX100010structnode{intadd;intkey;intnext;intflag;};boolcmp(nodea,nodeb){returna.key>n>>first;inti,x;node*s=newnode[MAX];
- could not import google.golang.org/protobuf/proto
ezreal_pan
Go后端golang前端开发语言
背景import("encoding/json""testing""google.golang.org/protobuf/proto")在测试中需要使用proto,但是,import这个包之后,一直报couldnotimportgoogle.golang.org/protobuf/proto这个错误,尝试了各种方法,依然没有解决这个问题。临时方案执行gomodvendor这个命令。项目的目录下多了
- JAVA springboot Access-Control-Allow-Origin
墨着染霜华
javaspringbootspring
response.setHeader("Access-Control-Allow-Origin","https:/your-domain.com");意思是:只有来自https:/your-domain.com的前端页面(即请求的来源Origin是这个域名),才能通过浏览器发起跨域请求访问这个接口区分大小写&完全匹配这个设置是完全匹配的,也就是说:https://epos.whbswdt.com
- Java web%10
好学且牛逼的马
java前端AI编程
%10新路线Javawebai笔记阶段时长内容Web前端基础2天HTML、CSS、JS、Vue3、AjaxWeb后端基础4天Maven、HTTP协议、SpringIOC、DI、MySQL、JDBC、MybatisWeb后端实战6天Tlias案例(基于案例讲解web开发的核心知识)Web后端进阶2天SpringAOP、SpringBoot原理、自定义Starter、Maven高级前端web实战4天V
- sql统计相同项个数并按名次显示
朱辉辉33
javaoracle
现在有如下这样一个表:
A表
ID Name time
------------------------------
0001 aaa 2006-11-18
0002 ccc 2006-11-18
0003 eee 2006-11-18
0004 aaa 2006-11-18
0005 eee 2006-11-18
0004 aaa 2006-11-18
0002 ccc 20
- Android+Jquery Mobile学习系列-目录
白糖_
JQuery Mobile
最近在研究学习基于Android的移动应用开发,准备给家里人做一个应用程序用用。向公司手机移动团队咨询了下,觉得使用Android的WebView上手最快,因为WebView等于是一个内置浏览器,可以基于html页面开发,不用去学习Android自带的七七八八的控件。然后加上Jquery mobile的样式渲染和事件等,就能非常方便的做动态应用了。
从现在起,往后一段时间,我打算
- 如何给线程池命名
daysinsun
线程池
在系统运行后,在线程快照里总是看到线程池的名字为pool-xx,这样导致很不好定位,怎么给线程池一个有意义的名字呢。参照ThreadPoolExecutor类的ThreadFactory,自己实现ThreadFactory接口,重写newThread方法即可。参考代码如下:
public class Named
- IE 中"HTML Parsing Error:Unable to modify the parent container element before the
周凡杨
html解析errorreadyState
错误: IE 中"HTML Parsing Error:Unable to modify the parent container element before the child element is closed"
现象: 同事之间几个IE 测试情况下,有的报这个错,有的不报。经查询资料后,可归纳以下原因。
- java上传
g21121
java
我们在做web项目中通常会遇到上传文件的情况,用struts等框架的会直接用的自带的标签和组件,今天说的是利用servlet来完成上传。
我们这里利用到commons-fileupload组件,相关jar包可以取apache官网下载:http://commons.apache.org/
下面是servlet的代码:
//定义一个磁盘文件工厂
DiskFileItemFactory fact
- SpringMVC配置学习
510888780
springmvc
spring MVC配置详解
现在主流的Web MVC框架除了Struts这个主力 外,其次就是Spring MVC了,因此这也是作为一名程序员需要掌握的主流框架,框架选择多了,应对多变的需求和业务时,可实行的方案自然就多了。不过要想灵活运用Spring MVC来应对大多数的Web开发,就必须要掌握它的配置及原理。
一、Spring MVC环境搭建:(Spring 2.5.6 + Hi
- spring mvc-jfreeChart 柱图(1)
布衣凌宇
jfreechart
第一步:下载jfreeChart包,注意是jfreeChart文件lib目录下的,jcommon-1.0.23.jar和jfreechart-1.0.19.jar两个包即可;
第二步:配置web.xml;
web.xml代码如下
<servlet>
<servlet-name>jfreechart</servlet-nam
- 我的spring学习笔记13-容器扩展点之PropertyPlaceholderConfigurer
aijuans
Spring3
PropertyPlaceholderConfigurer是个bean工厂后置处理器的实现,也就是BeanFactoryPostProcessor接口的一个实现。关于BeanFactoryPostProcessor和BeanPostProcessor类似。我会在其他地方介绍。PropertyPlaceholderConfigurer可以将上下文(配置文件)中的属性值放在另一个单独的标准java P
- java 线程池使用 Runnable&Callable&Future
antlove
javathreadRunnablecallablefuture
1. 创建线程池
ExecutorService executorService = Executors.newCachedThreadPool();
2. 执行一次线程,调用Runnable接口实现
Future<?> future = executorService.submit(new DefaultRunnable());
System.out.prin
- XML语法元素结构的总结
百合不是茶
xml树结构
1.XML介绍1969年 gml (主要目的是要在不同的机器进行通信的数据规范)1985年 sgml standard generralized markup language1993年 html(www网)1998年 xml extensible markup language
- 改变eclipse编码格式
bijian1013
eclipse编码格式
1.改变整个工作空间的编码格式
改变整个工作空间的编码格式,这样以后新建的文件也是新设置的编码格式。
Eclipse->window->preferences->General->workspace-
- javascript中return的设计缺陷
bijian1013
JavaScriptAngularJS
代码1:
<script>
var gisService = (function(window)
{
return
{
name:function ()
{
alert(1);
}
};
})(this);
gisService.name();
&l
- 【持久化框架MyBatis3八】Spring集成MyBatis3
bit1129
Mybatis3
pom.xml配置
Maven的pom中主要包括:
MyBatis
MyBatis-Spring
Spring
MySQL-Connector-Java
Druid
applicationContext.xml配置
<?xml version="1.0" encoding="UTF-8"?>
&
- java web项目启动时自动加载自定义properties文件
bitray
javaWeb监听器相对路径
创建一个类
public class ContextInitListener implements ServletContextListener
使得该类成为一个监听器。用于监听整个容器生命周期的,主要是初始化和销毁的。
类创建后要在web.xml配置文件中增加一个简单的监听器配置,即刚才我们定义的类。
<listener>
<des
- 用nginx区分文件大小做出不同响应
ronin47
昨晚和前21v的同事聊天,说到我离职后一些技术上的更新。其中有个给某大客户(游戏下载类)的特殊需求设计,因为文件大小差距很大——估计是大版本和补丁的区别——又走的是同一个域名,而squid在响应比较大的文件时,尤其是初次下载的时候,性能比较差,所以拆成两组服务器,squid服务于较小的文件,通过pull方式从peer层获取,nginx服务于较大的文件,通过push方式由peer层分发同步。外部发布
- java-67-扑克牌的顺子.从扑克牌中随机抽5张牌,判断是不是一个顺子,即这5张牌是不是连续的.2-10为数字本身,A为1,J为11,Q为12,K为13,而大
bylijinnan
java
package com.ljn.base;
import java.util.Arrays;
import java.util.Random;
public class ContinuousPoker {
/**
* Q67 扑克牌的顺子 从扑克牌中随机抽5张牌,判断是不是一个顺子,即这5张牌是不是连续的。
* 2-10为数字本身,A为1,J为1
- 翟鸿燊老师语录
ccii
翟鸿燊
一、国学应用智慧TAT之亮剑精神A
1. 角色就是人格
就像你一回家的时候,你一进屋里面,你已经是儿子,是姑娘啦,给老爸老妈倒怀水吧,你还觉得你是老总呢?还拿派呢?就像今天一样,你们往这儿一坐,你们之间是什么,同学,是朋友。
还有下属最忌讳的就是领导向他询问情况的时候,什么我不知道,我不清楚,该你知道的你凭什么不知道
- [光速与宇宙]进行光速飞行的一些问题
comsci
问题
在人类整体进入宇宙时代,即将开展深空宇宙探索之前,我有几个猜想想告诉大家
仅仅是猜想。。。未经官方证实
1:要在宇宙中进行光速飞行,必须首先获得宇宙中的航行通行证,而这个航行通行证并不是我们平常认为的那种带钢印的证书,是什么呢? 下面我来告诉
- oracle undo解析
cwqcwqmax9
oracle
oracle undo解析2012-09-24 09:02:01 我来说两句 作者:虫师收藏 我要投稿
Undo是干嘛用的? &nb
- java中各种集合的详细介绍
dashuaifu
java集合
一,java中各种集合的关系图 Collection 接口的接口 对象的集合 ├ List 子接口 &n
- 卸载windows服务的方法
dcj3sjt126com
windowsservice
卸载Windows服务的方法
在Windows中,有一类程序称为服务,在操作系统内核加载完成后就开始加载。这里程序往往运行在操作系统的底层,因此资源占用比较大、执行效率比较高,比较有代表性的就是杀毒软件。但是一旦因为特殊原因不能正确卸载这些程序了,其加载在Windows内的服务就不容易删除了。即便是删除注册表中的相 应项目,虽然不启动了,但是系统中仍然存在此项服务,只是没有加载而已。如果安装其他
- Warning: The Copy Bundle Resources build phase contains this target's Info.plist
dcj3sjt126com
iosxcode
http://developer.apple.com/iphone/library/qa/qa2009/qa1649.html
Excerpt:
You are getting this warning because you probably added your Info.plist file to your Copy Bundle
- 2014之C++学习笔记(一)
Etwo
C++EtwoEtwoiterator迭代器
已经有很长一段时间没有写博客了,可能大家已经淡忘了Etwo这个人的存在,这一年多以来,本人从事了AS的相关开发工作,但最近一段时间,AS在天朝的没落,相信有很多码农也都清楚,现在的页游基本上达到饱和,手机上的游戏基本被unity3D与cocos占据,AS基本没有容身之处。so。。。最近我并不打算直接转型
- js跨越获取数据问题记录
haifengwuch
jsonpjsonAjax
js的跨越问题,普通的ajax无法获取服务器返回的值。
第一种解决方案,通过getson,后台配合方式,实现。
Java后台代码:
protected void doPost(HttpServletRequest req, HttpServletResponse resp)
throws ServletException, IOException {
String ca
- 蓝色jQuery导航条
ini
JavaScripthtmljqueryWebhtml5
效果体验:http://keleyi.com/keleyi/phtml/jqtexiao/39.htmHTML文件代码:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>jQuery鼠标悬停上下滑动导航条 - 柯乐义<
- linux部署jdk,tomcat,mysql
kerryg
jdktomcatlinuxmysql
1、安装java环境jdk:
一般系统都会默认自带的JDK,但是不太好用,都会卸载了,然后重新安装。
1.1)、卸载:
(rpm -qa :查询已经安装哪些软件包;
rmp -q 软件包:查询指定包是否已
- DOMContentLoaded VS onload VS onreadystatechange
mutongwu
jqueryjs
1. DOMContentLoaded 在页面html、script、style加载完毕即可触发,无需等待所有资源(image/iframe)加载完毕。(IE9+)
2. onload是最早支持的事件,要求所有资源加载完毕触发。
3. onreadystatechange 开始在IE引入,后来其它浏览器也有一定的实现。涉及以下 document , applet, embed, fra
- sql批量插入数据
qifeifei
批量插入
hi,
自己在做工程的时候,遇到批量插入数据的数据修复场景。我的思路是在插入前准备一个临时表,临时表的整理就看当时的选择条件了,临时表就是要插入的数据集,最后再批量插入到数据库中。
WITH tempT AS (
SELECT
item_id AS combo_id,
item_id,
now() AS create_date
FROM
a
- log4j打印日志文件 如何实现相对路径到 项目工程下
thinkfreer
Weblog4j应用服务器日志
最近为了实现统计一个网站的访问量,记录用户的登录信息,以方便站长实时了解自己网站的访问情况,选择了Apache 的log4j,但是在选择相对路径那块 卡主了,X度了好多方法(其实大多都是一样的内用,还一个字都不差的),都没有能解决问题,无奈搞了2天终于解决了,与大家分享一下
需求:
用户登录该网站时,把用户的登录名,ip,时间。统计到一个txt文档里,以方便其他系统调用此txt。项目名
- linux下mysql-5.6.23.tar.gz安装与配置
笑我痴狂
mysqllinuxunix
1.卸载系统默认的mysql
[root@localhost ~]# rpm -qa | grep mysql
mysql-libs-5.1.66-2.el6_3.x86_64
mysql-devel-5.1.66-2.el6_3.x86_64
mysql-5.1.66-2.el6_3.x86_64
[root@localhost ~]# rpm -e mysql-libs-5.1