2020 hxpctf kernel-rop
学kernel的第四天,还是挺不好学的···
通过这道题我们来学习一下通过覆盖modprobe_path的内核漏洞利用姿势
拿到题目后先解包,分析下启动脚本
#!/bin/sh
qemu-system-x86_64 \
-m 128M \
-cpu kvm64,+smep,+smap \
-kernel vmlinuz \
-initrd initramfs.cpio.gz \
-hdb flag.txt \
-snapshot \
-nographic \
-monitor /dev/null \
-no-reboot \
-append "console=ttyS0 kaslr kpti=1 quiet panic=1"
开启了smep和smap,无法直接访问用户数据或者执行用户代码,开了kaslr
然后来分析下ko
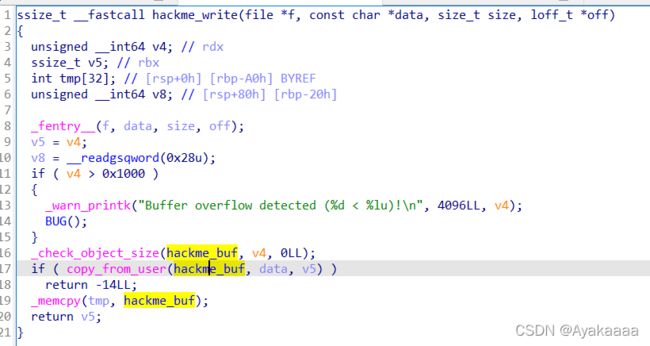
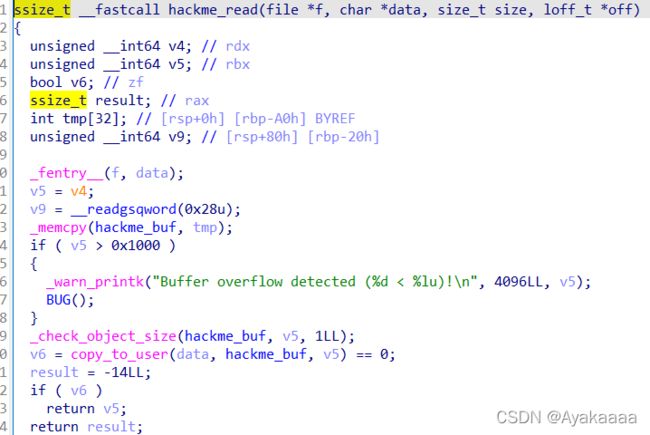
平平无奇的读写,但是都存在大范围的溢出。
这道题主要就是考察当有了内核任意地址读写之后,如何进行提权操作
首先,什么是modprobe呢?根据维基百科的说法:“modprobe是一个Linux程序,最初由Rusty Russell编写,用于在Linux内核中添加一个可加载的内核模块,或者从内核中移除一个可加载的内核模块”。也就是说,它是我们在Linux内核中安装或卸载新模块时都要执行的一个程序。该程序的路径是一个内核全局变量,默认为/sbin/modprobe,我们可以通过运行以下命令来查看该路径:
cat /proc/sys/kernel/modprobe
而这个程序的路径存放在modprobe_path,它位于一个可写的内存页中,我们可以通过读取/proc/kallsyms得到它的地址
如:
cat /proc/kallsyms | grep modprobe_path
当我们执行的文件类型是系统未知的类型时,将执行modprobe程序,准确的来说,应该是对文件签名(又称魔术头)为系统未知的文件调用execve()函数时,它将调用下列函数,并最终调用modprobe:
do_execve()
do_execveat_common()
bprm_execve()
exec_binprm()
search_binary_handler()
request_module()
call_modprobe()
最后会执行下列代码:
static int call_modprobe(char *module_name, int wait)
{
...
argv[0] = modprobe_path;
argv[1] = "-q";
argv[2] = "--";
argv[3] = module_name;
argv[4] = NULL;
info = call_usermodehelper_setup(modprobe_path, argv, envp, GFP_KERNEL,
NULL, free_modprobe_argv, NULL);
...
}
也就是说如果我们用任意写将modprobe_path覆盖成一个我们自己编写的shell脚本的路径,然后我们执行一个未知文件签名的文件。其结果是,当系统仍处于内核模式时,shell脚本将被执行,从而导致具有root权限的任意代码执行
后面具体如何通过modprobe_path覆盖读flag可以参考这篇文章:https://blog.csdn.net/weixin_46483787/article/details/124240829?spm=1001.2014.3001.5501
这里直接给出具体exp:
#include