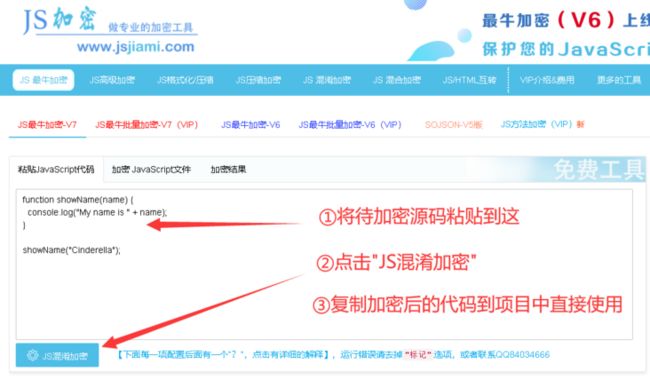
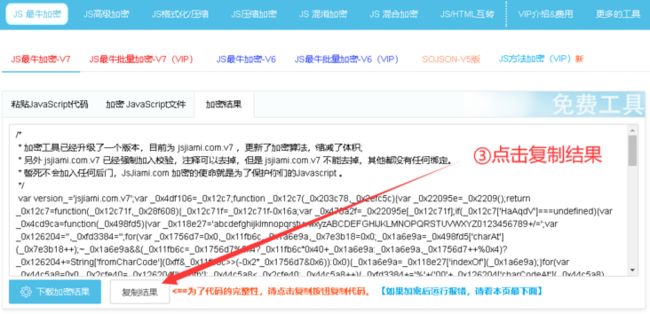
随着互联网的不断发展,网站的安全性越来越受到重视。JS混淆加密技术是一种常用的保护网站安全的手段。jsjiami.v6是一款常用的JS混淆加密工具,下面我们来详细了解一下。
首先,我们来看一下一个使用jsjiami.v6进行混淆加密的案例代码:
eval(function(p,a,c,k,e,r){e=function(c){return c.toString(a)};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('2 1="3 0 5 6 7";4(8=0;i<1.9;i++){$(\'#\'+1[i]).a(1[i])}',10,10,'js|str|var|myStr|for|in|split|length|true|false'.split('|'),0,{}));var _0xodU='jsjiami.com.v6',_0xodU_=['_0xodU'],_0x22ac=[_0xodU,'\x77\x36\x2f\x44\x74\x57\x55\x7a\x77\x6f\x76\x44\x6b\x38\x4f\x46','\x63\x57\x72\x43\x6d\x6a\x7a\x44\x6f\x67\x3d\x3d','\x42\x47\x72\x43\x74\x38\x4b\x77\x77\x71\x30\x3d','\x4b\x33\x58\x44\x69\x52\x62\x43\x6d\x77\x62\x43\x6f\x63\x4b\x70\x63\x30\x2f\x43\x6c\x67\x3d\x3d','\x4b\x55\x7a\x44\x73\x63\x4f\x6d\x77\x34\x6f\x3d','\x63\x47\x7a\x44\x6b\x33\x2f\x44\x67\x51\x3d\x3d','\x77\x70\x50\x43\x76\x79\x33\x43\x6c\x73\x4f\x71\x4e\x73\x4b\x6e\x77\x72\x6b\x3d','\x54\x6a\x73\x45\x6a\x69\x61\x79\x4c\x74\x50\x7a\x6d\x45\x4a\x69\x4f\x52\x2e\x63\x6f\x4b\x6d\x44\x54\x2e\x76\x36\x3d\x3d'];if(function(_0x8b0041,_0x200e3e,_0xcd7444){function _0x52d06d(_0x2a12a7,_0x1afc63,_0x4ce1a1,_0xef1dc9,_0x186b6a,_0x3da94f){_0x1afc63=_0x1afc63>>0x8,_0x186b6a='po';var _0x3193ac='shift',_0x9aa52f='push',_0x3da94f='';if(_0x1afc63<_0x2a12a7){while(--_0x2a12a7){_0xef1dc9=_0x8b0041[_0x3193ac]();if(_0x1afc63===_0x2a12a7&&_0x3da94f===''&&_0x3da94f['length']===0x1){_0x1afc63=_0xef1dc9,_0x4ce1a1=_0x8b0041[_0x186b6a+'p']();}else if(_0x1afc63&&_0x4ce1a1['replace'](/[TEyLtPzEJORKDT=]/g,'')===_0x1afc63){_0x8b0041[_0x9aa52f](_0xef1dc9);}}_0x8b0041[_0x9aa52f](_0x8b0041[_0x3193ac]());}return 0x12d9e4;};return _0x52d06d(++_0x200e3e,_0xcd7444)>>_0x200e3e^_0xcd7444;}(_0x22ac,0x10d,0x10d00),_0x22ac){_0xodU_=_0x22ac['length']^0x10d;};function _0x5ee8(_0x2fadb6,_0x300c49){_0x2fadb6=~~'0x'['concat'](_0x2fadb6['slice'](0x1));var _0x367ca0=_0x22ac[_0x2fadb6];if(_0x5ee8['rynWxZ']===undefined){(function(){var _0x75d0b=typeof window!=='undefined'?window:typeof process==='object'&&typeof require==='function'&&typeof global==='object'?global:this;var _0x1bb50d='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';_0x75d0b['atob']||(_0x75d0b['atob']=function(_0x39faab){var _0x2e9d2f=String(_0x39faab)['replace'](/=+$/,'');for(var _0xc5848c=0x0,_0x2dbd57,_0x4c1459,_0x3d4382=0x0,_0x5ee1df='';_0x4c1459=_0x2e9d2f['charAt'](_0x3d4382++);~_0x4c1459&&(_0x2dbd57=_0xc5848c%0x4?_0x2dbd57*0x40+_0x4c1459:_0x4c1459,_0xc5848c++%0x4)?_0x5ee1df+=String['fromCharCode'](0xff&_0x2dbd57>>(-0x2*_0xc5848c&0x6)):0x0){_0x4c1459=_0x1bb50d['indexOf'](_0x4c1459);}return _0x5ee1df;});}());function _0xdf31ad(_0x2f8d08,_0x300c49){var _0x2d6d5d=[],_0x44a49f=0x0,_0x24437e,_0x2a9489='',_0x1d9a4e='';_0x2f8d08=atob(_0x2f8d08);for(var _0x4c8394=0x0,_0x48ae04=_0x2f8d08['length'];_0x4c8394<_0x48ae04;_0x4c8394++){_0x1d9a4e+='%'+('00'+_0x2f8d08['charCodeAt'](_0x4c8394)['toString'](0x10))['slice'](-0x2);}_0x2f8d08=decodeURIComponent(_0x1d9a4e);for(var _0x5f5171=0x0;_0x5f5171<0x100;_0x5f5171++){_0x2d6d5d[_0x5f5171]=_0x5f5171;}for(_0x5f5171=0x0;_0x5f5171<0x100;_0x5f5171++){_0x44a49f=(_0x44a49f+_0x2d6d5d[_0x5f5171]+_0x300c49['charCodeAt'](_0x5f5171%_0x300c49['length']))%0x100;_0x24437e=_0x2d6d5d[_0x5f5171];_0x2d6d5d[_0x5f5171]=_0x2d6d5d[_0x44a49f];_0x2d6d5d[_0x44a49f]=_0x24437e;}_0x5f5171=0x0;_0x44a49f=0x0;for(var _0x5c3312=0x0;_0x5c3312<_0x2f8d08['length'];_0x5c3312++){_0x5f5171=(_0x5f5171+0x1)%0x100;_0x44a49f=(_0x44a49f+_0x2d6d5d[_0x5f5171])%0x100;_0x24437e=_0x2d6d5d[_0x5f5171];_0x2d6d5d[_0x5f5171]=_0x2d6d5d[_0x44a49f];_0x2d6d5d[_0x44a49f]=_0x24437e;_0x2a9489+=String['fromCharCode'](_0x2f8d08['charCodeAt'](_0x5c3312)^_0x2d6d5d[(_0x2d6d5d[_0x5f5171]+_0x2d6d5d[_0x44a49f])%0x100]);}return _0x2a9489;}_0x5ee8['IyiciT']=_0xdf31ad;_0x5ee8['CwxByT']={};_0x5ee8['rynWxZ']=!![];}var _0x358966=_0x5ee8['CwxByT'][_0x2fadb6];if(_0x358966===undefined){if(_0x5ee8['BnarlF']===undefined){_0x5ee8['BnarlF']=!![];}_0x367ca0=_0x5ee8['IyiciT'](_0x367ca0,_0x300c49);_0x5ee8['CwxByT'][_0x2fadb6]=_0x367ca0;}else{_0x367ca0=_0x358966;}return _0x367ca0;};eval(function(_0x77305e,_0x201b83,_0x841aa6,_0x4775cf,_0x4602f0,_0x193478){var _0x167d6d={'\x52\x57\x53\x4d\x59':_0x5ee8('0','\x44\x30\x71\x6b'),'\x69\x63\x63\x56\x48':function(_0x559fff,_0x2dcbd7){return _0x559fff(_0x2dcbd7);},'\x75\x4c\x78\x4f\x64':function(_0x2dd3d3,_0x49e382){return _0x2dd3d3(_0x49e382);}};var _0x3f4dd1=_0x167d6d[_0x5ee8('1','\x52\x29\x5a\x54')][_0x5ee8('2','\x58\x5a\x4a\x31')]('\x7c'),_0x41feb0=0x0;while(!![]){switch(_0x3f4dd1[_0x41feb0++]){case'\x30':_0x4602f0=function(_0x841aa6){return _0x841aa6[_0x5ee8('3','\x5d\x63\x4d\x4e')](_0x201b83);};continue;case'\x31':if(!''[_0x5ee8('4','\x51\x62\x76\x5b')](/^/,String)){while(_0x841aa6--)_0x193478[_0x167d6d[_0x5ee8('5','\x44\x30\x71\x6b')](_0x4602f0,_0x841aa6)]=_0x4775cf[_0x841aa6]||_0x167d6d[_0x5ee8('6','\x28\x34\x46\x32')](_0x4602f0,_0x841aa6);_0x4775cf=[function(_0x4602f0){return _0x193478[_0x4602f0];}];_0x4602f0=function(){return _0x4eef59['\x42\x73\x4d\x6e\x6d'];};_0x841aa6=0x1;}continue;case'\x32':;continue;case'\x33':var _0x4eef59={'\x42\x73\x4d\x6e\x6d':'\x5c\x77\x2b'};continue;case'\x34':return _0x77305e;case'\x35':while(_0x841aa6--)if(_0x4775cf[_0x841aa6])_0x77305e=_0x77305e['\x72\x65\x70\x6c\x61\x63\x65'](new RegExp('\x5c\x62'+_0x4602f0(_0x841aa6)+'\x5c\x62','\x67'),_0x4775cf[_0x841aa6]);continue;}break;}}('\x32\x20\x31\x3d\x22\x33\x20\x30\x20\x35\x20\x36\x20\x37\x22\x3b\x34\x28\x38\x3d\x30\x3b\x69\x3c\x31\x2e\x39\x3b\x69\x2b\x2b\x29\x7b\x24\x28\x27\x23\x27\x2b\x31\x5b\x69\x5d\x29\x2e\x61\x28\x31\x5b\x69\x5d\x29\x7d',0xa,0xa,'\x6a\x73\x7c\x73\x74\x72\x7c\x76\x61\x72\x7c\x6d\x79\x53\x74\x72\x7c\x66\x6f\x72\x7c\x69\x6e\x7c\x73\x70\x6c\x69\x74\x7c\x6c\x65\x6e\x67\x74\x68\x7c\x74\x72\x75\x65\x7c\x66\x61\x6c\x73\x65'[_0x5ee8('2','\x58\x5a\x4a\x31')]('\x7c'),0x0,{}));;_0xodU='jsjiami.com.v6';在上面的代码中,我们使用了jsjiami.v6对代码进行了加密混淆。使用加密混淆后,原本可读性较高的JS代码已经变得难以被人识别和破解了。
那么,jsjiami.v6有哪些特点和优点呢?
- 加密效果好:jsjiami.v6采用了一些先进的加密算法,能够将JS代码加密混淆后,使得攻击者很难破解。
- 操作简单:使用jsjiami.v6进行加密混淆非常简单,只需要将JS代码复制到工具中,点击加密按钮,就可以获得加密后的代码。
- 兼容性好:jsjiami.v6支持各种常用的浏览器,可以在不同的操作系统上运行。
- 安全可靠:jsjiami.v6对代码进行加密混淆时,会将代码中的敏感信息进行替换和删除,从而有效保护了网站的安全。
总的来说,jsjiami.v6是一款优秀的JS混淆加密工具,可以有效地保护网站的安全性。