OverTheWireBandit教程(11-20)
Bandit Level 11 → Level 12
Level Goal
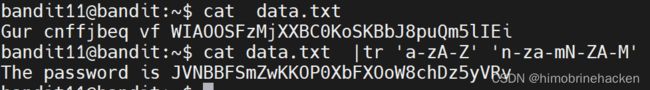
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
Commands you may need to solve this level
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Helpful Reading Material
- Rot13 on Wikipedia
经典的ROT13加密。
JVNBBFSmZwKKOP0XbFXOoW8chDz5yVRv
Bandit Level 12 → Level 13
Level Goal
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
Commands you may need to solve this level
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd, mkdir, cp, mv, file
Helpful Reading Material
- Hex dump on Wikipedia
16进制文件。
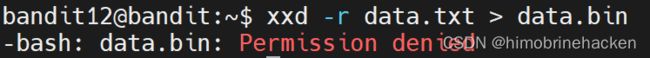
坏事权限不够,算了直接下载来弄。(操作大差不差,要注意有没有目标文件,没有目标文件可不不写目标文件)
mkdir /tmp/himobrine
cp data.txt /tmp/himobrine
cd /tmp/himobrine
xxd -r data.txt >data.bin
file data.bin
mv data.bin data.gz
gzip -d data.gz
file data
mv data data.bz2
bunzip2 -d data.bz2
file data
mv data data.gz
gzip -d data.gz
file data
mv data data.tar
tar xvf data.tar
file data5.bin
mv data5.bin data5.tar
tar xvf data5.tar
file data6
file data6.bin.out
mv data6.bin.out data.tar
tar xvf data.tar
file data8.bin
mv data8.bin data8.gz
gzip -d data8.gz
cat data8wbWdlBxEir4CaE8LaPhauuOo6pwR
Bandit Level 13 → Level 14
Level Goal
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
Commands you may need to solve this level
ssh, telnet, nc, openssl, s_client, nmap
Helpful Reading Material
- SSH/OpenSSH/Keys
mrDw
这一关解密工具开始更换,需要明白黑客常用的工具了,以及连接方式,凭证,密钥啥的。
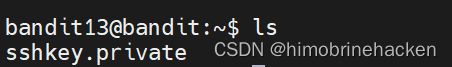
我们可以看到
.private就是ssh的密钥文件,直接使用就可以
ssh -p 2220 bandit.labs.overthewire.org -i ./sshkey.private -l bandit14
找密码,在/etc/bandit_pass有
fGrHPx402xGC7U7rXKDaxiWFTOiF0ENq
Bandit Level 14 → Level 15
Level Goal
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
Commands you may need to solve this level
ssh, telnet, nc, openssl, s_client, nmap
Helpful Reading Material
- How the Internet works in 5 minutes (YouTube) (Not completely accurate, but good enough for beginners)
- IP Addresses
- IP Address on Wikipedia
- Localhost on Wikipedia
- Ports
- Port (computer networking) on Wikipedia
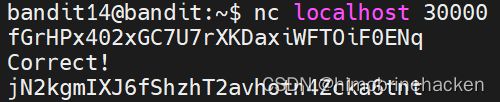
要将14的密码发送到端口30000,建议使用netcat
nc localhost 30000jN2kgmIXJ6fShzhT2avhotn4Zcka6tnt
Bandit Level 15 → Level 16
Level Goal
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
Helpful note: Getting “HEARTBEATING” and “Read R BLOCK”? Use -ign_eof and read the “CONNECTED COMMANDS” section in the manpage. Next to ‘R’ and ‘Q’, the ‘B’ command also works in this version of that command…
Commands you may need to solve this level
ssh, telnet, nc, openssl, s_client, nmap
Helpful Reading Material
- Secure Socket Layer/Transport Layer Security on Wikipedia
- OpenSSL Cookbook - Testing with OpenSSL
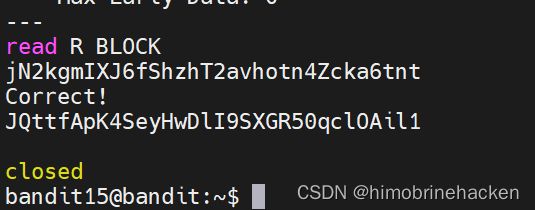
openssl基础知识,连接30001
openssl s_client -connect localhost:30001 -ign_eofJQttfApK4SeyHwDlI9SXGR50qlOAil1
Bandit Level 16 → Level 17
Level Goal
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
Commands you may need to solve this level
ssh, telnet, nc, openssl, s_client, nmap
Helpful Reading Material
- Port scanner on Wikipedia
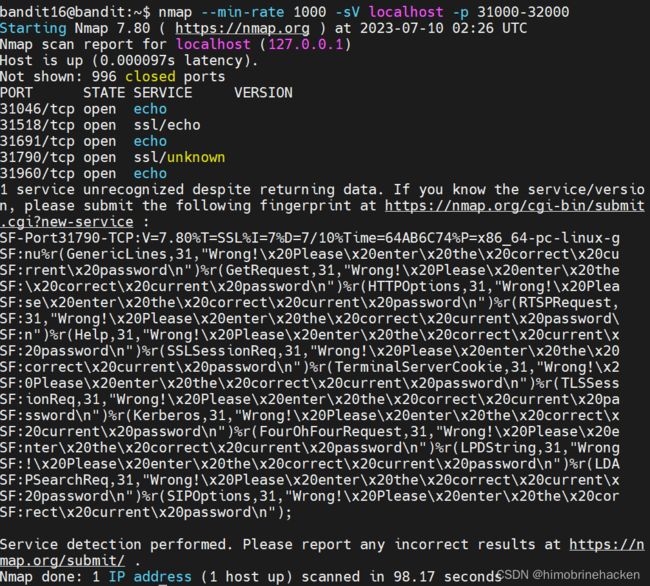
要求31000扫描秒到32000直接nmap
nmap --min-rate 1000 -sV localhost -p 31000-32000顶上端口31790,并且查看端口
JQttfApK4SeyHwDlI9SXGR50qclOAil1
把这个数据写进去,再连接(记得改权限600)
VwOSWtCA7lRKkTfbr2IDh6awj9RNZM5e
Bandit Level 17 → Level 18
Level Goal
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
NOTE: if you have solved this level and see ‘Byebye!’ when trying to log into bandit18, this is related to the next level, bandit19
Commands you may need to solve this level
cat, grep, ls, diff
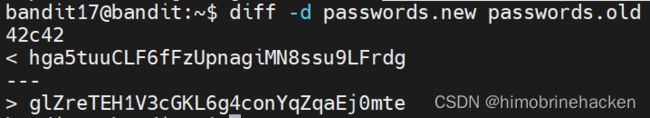
diff -d passwords.new passwords.oldhga5tuuCLF6fFzUpnagiMN8ssu9LFrdg
glZreTEH1V3cGKL6g4conYqZqaEj0mte
Bandit Level 18 → Level 19
Level Goal
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
Commands you may need to solve this level
ssh, ls, cat
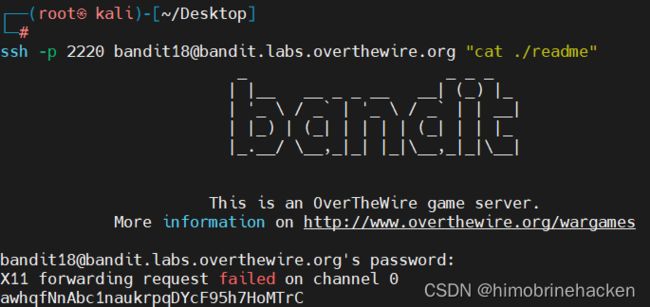
这一关直接登录的话,会显示一个“Byebye”,然后会话被关闭,原因是.bashrc被改动了,我们可以用带命令的ssh来查看文件。
ssh -p 2220 [email protected] "cat ./readme" awhqfNnAbc1naukrpqDYcF95h7HoMTrC
Bandit Level 19 → Level 20
Level Goal
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
Helpful Reading Material
- setuid on Wikipedia
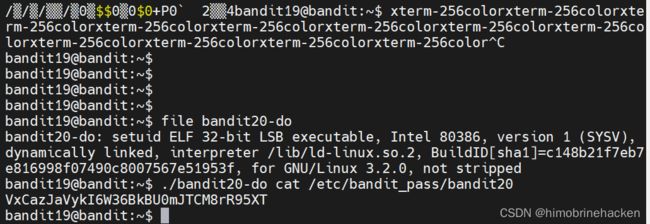
setuid可以查看到用户权限,ls -al列出所有文件及权限,注意到bandit20-do是-rws-r-x---,这个文件有sudo权限,用它来读取Level 20的文件,获得密码
./bandit20-do cat /etc/bandit_pass/bandit20VxCazJaVykI6W36BkBU0mJTCM8rR95XT
Bandit Level 20 → Level 21
Level Goal
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
NOTE: Try connecting to your own network daemon to see if it works as you think
Commands you may need to solve this level
ssh, nc, cat, bash, screen, tmux, Unix ‘job control’ (bg, fg, jobs, &, CTRL-Z, …)
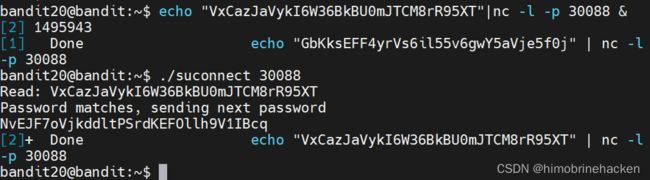
登录到Bandit20,查看文件,找到一个suconnect,注意看题目的描述,告诉了我们怎么弄
echo "VxCazJaVykI6W36BkBU0mJTCM8rR95XT"|nc -l -p 30088 &
./suconnect 30088
NvEJF7oVjkddltPSrdKEFOllh9V1IBcq