使用 Openssl 备忘录
Openssl 创建 certificates
创建 self-signed 证书
“certificate authority” 要创建一个自己的证书来签名别的 server 证书
- 创建
CA的private key和self-signed certificate。
openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem
req:request请求创建-x509: 用来告知 openssl 输出一个x509 格式的 public key certificate,而不是创建一个 CSR。-newkey: 用来告知 openssl 使用 rsa 4096 bit key 来创建 private key。-days: 用来告知 openssl certificate 的有效期。pem: 常用格式后缀。
命令执行过程中会要求设置密码,用于保护 ca-key.pem private key。同时会需要输入一些身份信息,其中比较重要的是 Common Name(Domain name)用于后续的访问。如下
openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem
Generating a 4096 bit RSA private key
..........................................................++
..............................................................................................................................++
writing new private key to 'ca-key.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) []:CN
State or Province Name (full name) []:BJ
Locality Name (eg, city) []:CY
Organization Name (eg, company) []:GOV
Organizational Unit Name (eg, section) []:SEC
Common Name (eg, fully qualified host name) []:*.test.com
Email Address []:
cat 一下 ca-key.pem,可以看到 ENCRYPTED PRIVATE KEY。
cat ca-key.pem
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIJnzBJBgkqhkiG9w0BBQ0wPDAbBgkqhkiG9w0BBQwwDgQIvFS8k4gUo4ECAggA
MB0GCWCGSAFlAwQBKgQQBpr4eUDvLnLDM/vByHSJxgSCCVAMn4NTiA5PKYpvbGfI
...
z2bl5JB7l32UU1nlgql3b5m+6w==
-----END ENCRYPTED PRIVATE KEY-----
cat 一下 ca-cert.pem,可以看到 crt 并没有 ENCRYPTED,只是 base64 了一下。因为 ca-cert.pem 只包含 public key,身份信息,和 signature。这些都是一些公开的信息。
cat ca-cert.pem
-----BEGIN CERTIFICATE-----
MIIFLDCCAxQCCQCO9xL3XIFtpTANBgkqhkiG9w0BAQsFADBYMQswCQYDVQQGEwJD
TjELMAkGA1UECAwCQkoxCzAJBgNVBAcMAkNZMQwwCgYDVQQKDANHT1YxDDAKBgNV
...
zF5g86JXkox1GzAYaU3VCzGaH+hbKZFZFiz7T2f/VWA=
-----END CERTIFICATE-----
ca-cert.pem 信息可以使用 openssl x509 命令查看。
openssl x509 -in ca-cert.pem -noout -text
-noout:告知 openssl 不用输出base64后的值。-text:告知 openssl 输出 readabletext格式。
openssl x509 -in ca-cert.pem -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 10301723526251507109 (0x8ef712f75c816da5)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=BJ, L=CY, O=GOV, OU=SEC, CN=*.test.com
Validity
Not Before: Mar 12 06:59:43 2023 GMT
Not After : Mar 11 06:59:43 2024 GMT
Subject: C=CN, ST=BJ, L=CY, O=GOV, OU=SEC, CN=*.test.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:bb:3c:ab:8f:2c:2f:61:04:f2:a1:48:02:0c:48:
85:9d:35:2e:7f:58:a3:db:0f:af:11:ac:3d:44:34:
0d:12:3e:c7:25:9b:8c:93:06:5b:c8:a1:ee:12:4d:
e2:c5:0b:07:2f:46:b8:e8:3d:a5:97:da:27:88:1f:
01:b1:59:79:91:56:e6:c6:a0:1e:95:12:1c:0c:a3:
54:dd:ce:45:d1:2b:61:98:ef:c1:41:c2:f9:c9:4c:
b6:5b:54:43:00:9c:87:8a:73:c4:8e:ca:28:8c:f1:
29:2a:a4:8b:6e:c4:86:fb:56:fe:17:a4:e0:9b:b1:
a5:f0:8f:8f:a8:5a:bb:8f:81:da:e4:39:e9:44:0c:
dd:f4:d2:29:13:3d:73:ce:4a:82:90:70:c5:c5:9a:
20:cf:d5:48:a3:13:2a:bb:09:8a:d8:ae:76:3c:af:
1d:e8:80:e2:a6:48:f2:55:8c:27:4c:19:08:d1:a0:
da:d1:70:c4:d9:90:b5:df:8f:4c:e1:26:3e:2d:48:
4f:a1:28:42:0e:4e:02:34:f3:cb:9f:6b:23:e6:33:
fd:64:6c:4d:77:45:09:97:42:5c:cb:71:de:94:49:
41:27:28:30:dd:c9:7f:35:08:a5:6f:2b:ea:35:f2:
77:3a:a7:a3:71:75:9b:60:d4:59:31:3f:08:44:af:
aa:00:4b:c9:d7:21:02:77:e9:9f:f8:47:f5:84:cd:
ff:9c:aa:bd:66:d3:53:fa:7e:60:07:c3:a7:f5:f9:
b3:dd:25:3c:4f:7f:95:62:72:f4:9b:0f:e4:f2:09:
74:96:a7:96:33:4a:fd:51:3b:f3:51:f2:41:97:51:
51:c6:fe:95:25:97:fc:15:22:51:79:78:b7:a3:f3:
e6:2d:69:49:1b:18:02:99:20:8e:fd:c8:86:ac:d8:
ab:fa:cf:1e:43:1c:be:c2:1f:a2:61:0d:3c:11:6f:
06:b6:36:c1:20:83:ef:4d:e8:e5:8c:cd:f9:fd:cf:
b2:1a:9d:09:99:94:2d:d6:0c:bf:88:6a:03:f8:6d:
20:94:48:f5:6e:74:cf:ba:7b:d4:f7:a1:29:7e:95:
60:1f:ed:2b:e4:54:2c:d3:dd:67:a4:b9:af:30:55:
b1:74:c7:f8:05:7b:d2:f4:8f:ac:4c:cc:27:de:1d:
4a:89:09:80:f1:3d:3d:ba:92:c0:71:50:3f:7a:08:
d8:10:49:4d:69:b2:74:1e:b6:34:06:c3:19:6f:ba:
24:75:97:bc:40:f4:6a:13:50:c8:fe:e9:c8:b8:10:
94:af:f5:57:8d:3c:38:2e:2a:4d:b4:03:58:ed:8c:
1d:86:ce:61:15:69:14:1f:bc:d0:b6:86:34:86:4b:
1d:69:91
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
2f:7d:64:1d:6f:45:58:7a:d9:13:ec:d5:22:31:95:87:58:d4:
2e:ae:e9:0e:7f:d1:c9:ce:57:e2:b8:38:e0:c5:c7:f9:03:23:
ca:4c:2d:6b:80:40:51:71:5d:87:2e:29:c2:cd:a9:72:08:10:
1e:86:10:bf:4d:b7:9a:69:61:78:90:97:7a:8c:c1:8b:48:fc:
b0:d7:e5:96:c6:6a:3f:b7:3d:41:91:20:0e:2b:d2:16:60:a8:
56:03:c5:10:f8:ed:14:b9:1e:8f:6b:b2:2f:e9:2d:fe:ea:25:
15:85:6c:65:51:96:f8:c3:99:66:72:c5:d9:93:bf:b4:c4:4d:
32:21:dd:84:68:c7:d7:69:ca:6b:26:cd:83:39:11:6e:56:ae:
90:2e:f8:0e:3b:43:e1:89:9a:c7:7d:be:30:8b:13:5c:1b:5c:
f2:b7:35:dc:e9:2c:76:fd:fa:c3:b2:ef:ba:57:2a:e1:60:a0:
e4:62:7d:ee:ff:f7:23:4d:14:43:6e:c2:53:a2:09:ef:b3:36:
13:31:80:42:12:17:b9:47:ef:88:e3:91:bc:af:0c:93:02:fd:
0b:58:8d:f2:1d:b1:14:b6:8c:eb:71:22:06:c0:ec:3b:a4:d9:
86:65:42:ca:30:b3:b2:24:fb:1d:20:55:e8:74:d8:3f:77:7e:
11:46:aa:7e:90:17:52:69:03:fc:21:2f:6e:c4:4a:5f:25:85:
9c:be:8b:25:f5:24:7a:83:e7:98:ee:7f:27:97:47:6e:57:68:
84:9f:bb:07:d1:7c:2c:f6:dd:c1:6e:a4:a8:63:99:5d:96:33:
f0:a2:91:d4:71:51:81:5d:c8:61:9f:fe:bf:1d:91:ab:fa:dd:
67:91:15:eb:26:f1:22:58:22:ad:16:01:78:f2:14:57:fa:ec:
ad:98:cc:be:e5:a7:24:04:2b:84:2a:22:cc:d1:e8:b6:0f:e4:
19:8a:a4:66:15:a2:f9:c5:94:a7:4e:00:51:02:0e:2e:24:e3:
52:e2:ce:79:34:62:1e:c2:3e:01:d5:1e:85:5b:33:07:61:83:
00:a8:00:48:43:82:0e:7d:33:cf:79:52:36:c9:2e:87:fc:b1:
ed:5a:34:0d:d3:41:2a:4b:e4:4b:a6:4c:fa:e4:1d:09:41:1a:
98:92:ec:d1:40:3c:fa:55:0e:e3:9a:b4:b9:7b:f9:f0:02:0c:
09:c3:d8:9d:04:50:f6:e4:5c:1d:d8:1c:43:ce:88:bf:b1:38:
35:05:99:00:e1:42:dc:d7:cf:1b:e8:db:cc:5e:60:f3:a2:57:
92:8c:75:1b:30:18:69:4d:d5:0b:31:9a:1f:e8:5b:29:91:59:
16:2c:fb:4f:67:ff:55:60
这个证书的 Issuer 和 Subject 一样,原因是这是我们自己 self signed CA 证书。同时可以看到 Subject Public Key 和 Signature。
如何避免交互模式
避免交互身份信息
openssl 如何避免使用interactive mode。可以使用 -subj 选项配置身份信息,但是还是需要输入 private key 的密码。
openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem -subj "/C=CN/ST=BJ/L=CY/O=GOV/OU=SEC/CN=*.test.com"
openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem -subj "/C=CN/ST=BJ/L=CY/O=GOV/OU=SEC/CN=*.test.com"
Generating a 4096 bit RSA private key
..............++
.......................................................................++
writing new private key to 'ca-key.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
避免 encrypted private key(测试使用)
-nodes 选项可以让 openssl 命令避免加密 private key。
openssl req -x509 -newkey rsa:4096 -days 365 -nodes -keyout ca-key.pem -out ca-cert.pem -subj "/C=CN/ST=BJ/L=CY/O=GOV/OU=SEC/CN=*.test.com"
Generating a 4096 bit RSA private key
....................++
......++
writing new private key to 'ca-key.pem'
-----
cat 一下 ca-key.pem,看看 private key 文件内容变化。
cat ca-key.pem
-----BEGIN PRIVATE KEY-----
MIIJQwIBADANBgkqhkiG9w0BAQEFAASCCS0wggkpAgEAAoICAQC+z0yX8yIOlNB1
BxxG1nbarVqUuh+V4wyGBNT+Klo/Dov0iaUg6giTYVtSsYrQ+0IN8YhiezIc6e9N
...
lA8Y3j5m24j01sWZm9K8xI/plLI/dFo=
-----END PRIVATE KEY-----
可以看到这里已经不是 encrypted private,只是-----BEGIN PRIVATE KEY-----。
创建 web server 的 private key 和 certificate signing request(CSR)。
创建CA 根证书命令如下
openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem -subj "/C=CN/ST=BJ/L=CY/O=GOV/OU=SEC/CN=*.test.com"
对比创建 web server 的 private key 和 CSR 命令几乎和创建 CA 根证书类似,只是去掉了-x509 ,-days 365,修改了身份信息和输出文件,如下
openssl req -newkey rsa:4096 -keyout server-key.pem -out server-req.pem -subj "/C=CN/ST=SH/L=YY/O=OV/OU=SEC/CN=*.shtest.com"
cat 一下 server-key.pem 可以看到 private key 还是 ENCRYPTED。
cat server-key.pem
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIJnzBJBgkqhkiG9w0BBQ0wPDAbBgkqhkiG9w0BBQwwDgQIdM4hPMIR/pgCAggA
MB0GCWCGSAFlAwQBKgQQ92ZEhY0dtQ12BtIZT8aA+ASCCVC+3tpLpF1uPztSpCkt
...
jMKNNOB34KxuOtJirCCHMJ31ww==
-----END ENCRYPTED PRIVATE KEY-----
cat 一下 server-req.pem 可以看到 server-req.pem 是 CERTIFICATE REQUEST。
cat server-req.pem
-----BEGIN CERTIFICATE REQUEST-----
MIIEnjCCAoYCAQAwWTELMAkGA1UEBhMCQ04xCzAJBgNVBAgMAlNIMQswCQYDVQQH
DAJZWTELMAkGA1UECgwCT1YxDDAKBgNVBAsMA1NFQzEVMBMGA1UEAwwMKi5zaHRl
...
zTYvI36Tn9F6HiRoxa4X7qanazYDKWDIvmKn9PskWY0GAg==
-----END CERTIFICATE REQUEST-----
用 self-signed CA 证书的 private key 签名 web server 的 certificate signing request(CSR),最后得到 signed web server certificate。
openssl x509 -req -in server-req.pem -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem
-req: 告知 openssl 命令传入一个 certificate signing request。-in: 传入certificate signing request。-CA: 指定 CA 根证书。-CAkey: 指定 CA 根证书的private key。-CAcreateserial: 给每个 certificate 一个独有的序列号。-out: 输出 web server 的 certificate。
openssl x509 -req -in server-req.pem -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem
Signature ok
subject=/C=CN/ST=SH/L=YY/O=OV/OU=SEC/CN=*.shtest.com
Getting CA Private Key
Enter pass phrase for ca-key.pem:
运行后,因为 CA 根证书的 private key 创建时候有设置密码,所以使用的时候需要同样输入 private key 的密码。
创建完 web server 的 certificate 后可以使用之前 openssl x509 命令查看
openssl x509 -in server-cert.pem -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 11480488640831871058 (0x9f52e397b4b0d852)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=CN, ST=BJ, L=CY, O=GOV, OU=SEC, CN=*.test.com
Validity
Not Before: Mar 12 07:58:37 2023 GMT
Not After : Apr 11 07:58:37 2023 GMT
Subject: C=CN, ST=SH, L=YY, O=OV, OU=SEC, CN=*.shtest.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:b7:8f:5b:b8:a0:8e:53:ab:4e:8b:23:ee:49:7a:
e8:07:ec:d2:0d:11:83:65:93:dc:1b:ed:ac:81:3f:
5b:70:d5:6e:2d:14:f1:b1:62:92:3e:70:9e:6e:78:
06:43:b5:3b:c2:ed:e6:7e:f4:2f:59:c1:b9:aa:cc:
0b:09:a2:a0:15:90:e9:8d:da:1d:b4:73:ea:83:6a:
13:48:57:dc:1c:f3:45:86:e7:d8:48:98:df:ae:4d:
e5:7f:dc:23:54:64:58:34:28:88:39:b0:89:bc:af:
75:1d:6a:a3:c6:87:56:3a:4f:c9:a6:6f:d7:74:ba:
79:5d:9b:79:ab:dc:c7:06:c5:d9:05:9e:fa:52:d8:
d2:4d:95:e9:61:ec:ca:5a:1b:0e:0a:c9:09:c1:10:
1e:61:3f:84:99:f9:ab:c8:f1:16:65:53:ad:f2:b0:
4d:33:35:e9:06:30:bf:08:6e:ec:df:ac:cd:19:cc:
8e:62:73:8f:63:65:a3:32:35:a0:83:b8:a8:a3:f2:
8a:80:0f:62:82:49:7f:5c:c0:b4:c4:ec:e3:3c:4b:
ef:ca:fd:99:8e:67:e0:99:a5:32:2a:33:49:73:81:
05:e2:99:04:20:ad:a5:10:3f:f4:f4:35:d4:8e:f4:
6c:f5:e2:32:99:56:0c:34:c7:80:d3:4f:a2:af:fa:
b0:ef:1b:70:44:7a:7a:29:f6:d8:d8:05:3a:3f:b1:
4b:91:07:7e:36:6f:5f:83:f7:5e:6f:c4:b9:bc:c4:
0d:cb:57:58:99:a3:91:7e:fb:a0:93:91:4f:84:be:
b4:00:81:e8:94:d9:f5:c7:a4:57:b1:f3:a0:e4:71:
08:ad:90:0f:ea:ae:63:64:92:88:7e:44:e1:3a:f5:
87:9f:eb:bb:a5:b0:49:f3:99:68:38:17:ca:32:60:
ea:ec:ef:9d:80:05:a3:6d:bb:e5:ed:a2:c2:ae:38:
96:d1:e0:fa:b8:a8:ed:be:54:13:97:5d:ce:35:f1:
06:cb:1c:35:2d:5c:ea:2b:91:4c:99:cd:9b:da:21:
ec:2b:a3:ff:1d:3c:0e:9e:dc:25:c0:06:37:81:e5:
14:80:c5:6f:22:58:bf:25:04:00:0f:a4:6d:0c:d9:
e6:68:bc:f7:61:5d:04:e9:d9:c7:e7:8c:15:82:f1:
df:26:cc:46:1e:fb:ef:d8:96:36:c7:3e:6c:06:cb:
56:72:9a:d1:78:79:65:cc:b8:40:13:31:a0:6e:29:
e2:80:93:7d:a4:ac:73:fc:24:70:de:8c:74:9c:36:
91:7d:f1:5b:6c:69:37:63:3c:10:04:49:8c:17:84:
75:d9:0b:86:3f:1c:00:43:5b:b2:76:85:e8:bd:ed:
95:8d:db
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
13:c4:26:76:2e:d9:22:13:9a:41:d0:6d:45:a2:f0:06:b2:83:
85:7b:fc:e6:34:9e:e4:14:64:23:59:08:bf:0d:b1:55:e8:56:
ce:91:05:0f:5b:80:28:89:8a:4a:bd:1f:39:61:1f:b9:f7:45:
55:38:8b:8f:c2:ad:a9:cc:58:6a:d5:f7:a7:0f:f4:6f:af:b3:
6a:0d:d7:35:10:8e:65:ba:17:5a:da:9e:cf:b5:e3:9f:db:43:
76:81:89:ee:77:23:5c:4b:d6:bc:df:81:44:ce:7a:7f:b3:bb:
97:9d:cf:61:c5:b2:07:d9:12:5e:26:8b:e2:f8:7a:02:18:b7:
42:db:2f:74:7e:bf:71:65:4d:c9:d2:21:92:75:56:7b:e5:32:
86:50:22:72:65:e1:1c:c4:0a:a4:ac:d9:47:98:6e:1a:c6:08:
d9:11:2b:1d:f8:14:f3:d4:0f:99:79:35:a5:c5:95:20:09:f0:
1c:1b:34:ff:f5:09:1a:74:14:dc:4e:a3:c1:0c:a2:33:0a:59:
51:95:2f:ef:30:7f:9f:7c:54:35:88:5e:a0:f1:31:99:19:d0:
e7:c2:fb:a8:50:9e:9f:48:95:2b:af:a1:1c:9e:13:9f:e7:eb:
92:19:55:9c:db:1c:fe:bd:80:a9:bb:62:68:1c:10:c4:5c:7f:
6f:93:7e:40:54:77:26:78:d8:a6:f7:f6:f0:a3:a2:92:08:5f:
67:0b:d3:19:34:85:59:61:2d:87:f7:ea:d4:f4:59:ae:0f:2b:
e3:10:b5:96:1b:e9:fb:d0:8f:83:6a:28:6f:42:40:1a:83:43:
5b:49:ea:c5:4e:80:af:51:b8:cc:82:e8:8c:d7:0f:59:29:59:
53:c7:0a:2e:c8:8e:99:17:a7:a0:f9:d6:33:5e:63:12:bd:26:
13:2b:d0:a3:5e:a4:a0:24:2c:3b:d9:6b:43:44:84:82:bd:53:
2e:ed:c4:b9:8d:29:e5:a0:7a:f3:fa:97:6c:df:9b:95:94:1d:
40:29:cf:67:ac:27:ec:04:44:9d:08:56:1d:95:00:7f:ed:e2:
63:44:b5:03:f9:09:9f:df:db:ed:38:da:e4:ce:e3:df:78:ac:
0b:bf:69:8f:ab:e1:f5:21:47:96:f4:ac:73:79:d8:cd:a1:71:
89:b4:4d:0d:96:82:64:7b:b1:66:c3:d0:28:ad:a2:10:80:27:
80:8e:df:f3:ae:b9:27:e2:04:68:68:53:60:c4:d3:2e:9e:e0:
38:88:38:b1:da:92:b6:23:ee:42:1f:b2:89:57:c9:7f:40:56:
11:b7:98:01:a2:28:65:b0:e3:c2:a1:fc:4d:08:03:ba:9f:87:
84:4d:e6:88:f2:e3:e1:bd
修改 web server certificate validate days
可以看到 web server certificate validate 30 days
Validity
Not Before: Mar 12 07:58:37 2023 GMT
Not After : Apr 11 07:58:37 2023 GMT
可以通过 -days 选项指定 certificate 的 validate days。
openssl x509 -req -in server-req.pem -days 60 -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem
Signature ok
subject=/C=CN/ST=SH/L=YY/O=OV/OU=SEC/CN=*.shtest.com
Getting CA Private Key
Enter pass phrase for ca-key.pem:
这里可以看到 Validity 为 60 天。
openssl x509 -in server-cert.pem -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 11480488640831871059 (0x9f52e397b4b0d853)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=CN, ST=BJ, L=CY, O=GOV, OU=SEC, CN=*.test.com
Validity
Not Before: Mar 12 08:12:00 2023 GMT
Not After : May 11 08:12:00 2023 GMT
Subject: C=CN, ST=SH, L=YY, O=OV, OU=SEC, CN=*.shtest.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:b7:8f:5b:b8:a0:8e:53:ab:4
给 web server certificate 指定多个 domain name 和 IP address
可以通过给 certificate 的 Extension Subject Alternative Name 来制定 certificate 的不同 domain name,甚至到是 IP 地址。
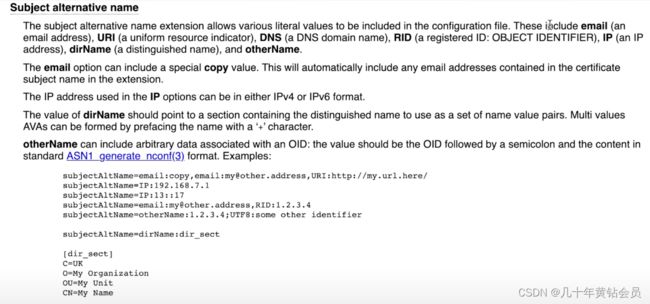
指定 Extension Subject Alternative Name 需要再创建一个文件 server-ext.cnf,内容如下
# cat server-ext.cnf
subjectAltName=DNS:*.hello.com,DNS:*.world.org,IP:0.0.0.0
DNS:指定其他的domain nameIP: 指定 IP 地址
重新生成带 web server certificate。 通过 -extfile 选项指定 Extension Subject Alternative Name 文件 server-ext.cnf 。
openssl x509 -req -in server-req.pem -days 60 -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem -extfile server-ext.cnf
Signature ok
subject=/C=CN/ST=SH/L=YY/O=OV/OU=SEC/CN=*.shtest.com
Getting CA Private Key
Enter pass phrase for ca-key.pem:
查看 web server certificate。
openssl x509 -in server-cert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 11480488640831871060 (0x9f52e397b4b0d854)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=CN, ST=BJ, L=CY, O=GOV, OU=SEC, CN=*.test.com
Validity
Not Before: Mar 12 08:23:43 2023 GMT
Not After : May 11 08:23:43 2023 GMT
Subject: C=CN, ST=SH, L=YY, O=OV, OU=SEC, CN=*.shtest.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:b7:8f:5b:b8:a0:8e:53:ab:4e:8b:23:ee:49:7a:
e8:07:ec:d2:0d:11:83:65:93:dc:1b:ed:ac:81:3f:
5b:70:d5:6e:2d:14:f1:b1:62:92:3e:70:9e:6e:78:
06:43:b5:3b:c2:ed:e6:7e:f4:2f:59:c1:b9:aa:cc:
0b:09:a2:a0:15:90:e9:8d:da:1d:b4:73:ea:83:6a:
13:48:57:dc:1c:f3:45:86:e7:d8:48:98:df:ae:4d:
e5:7f:dc:23:54:64:58:34:28:88:39:b0:89:bc:af:
75:1d:6a:a3:c6:87:56:3a:4f:c9:a6:6f:d7:74:ba:
79:5d:9b:79:ab:dc:c7:06:c5:d9:05:9e:fa:52:d8:
d2:4d:95:e9:61:ec:ca:5a:1b:0e:0a:c9:09:c1:10:
1e:61:3f:84:99:f9:ab:c8:f1:16:65:53:ad:f2:b0:
4d:33:35:e9:06:30:bf:08:6e:ec:df:ac:cd:19:cc:
8e:62:73:8f:63:65:a3:32:35:a0:83:b8:a8:a3:f2:
8a:80:0f:62:82:49:7f:5c:c0:b4:c4:ec:e3:3c:4b:
ef:ca:fd:99:8e:67:e0:99:a5:32:2a:33:49:73:81:
05:e2:99:04:20:ad:a5:10:3f:f4:f4:35:d4:8e:f4:
6c:f5:e2:32:99:56:0c:34:c7:80:d3:4f:a2:af:fa:
b0:ef:1b:70:44:7a:7a:29:f6:d8:d8:05:3a:3f:b1:
4b:91:07:7e:36:6f:5f:83:f7:5e:6f:c4:b9:bc:c4:
0d:cb:57:58:99:a3:91:7e:fb:a0:93:91:4f:84:be:
b4:00:81:e8:94:d9:f5:c7:a4:57:b1:f3:a0:e4:71:
08:ad:90:0f:ea:ae:63:64:92:88:7e:44:e1:3a:f5:
87:9f:eb:bb:a5:b0:49:f3:99:68:38:17:ca:32:60:
ea:ec:ef:9d:80:05:a3:6d:bb:e5:ed:a2:c2:ae:38:
96:d1:e0:fa:b8:a8:ed:be:54:13:97:5d:ce:35:f1:
06:cb:1c:35:2d:5c:ea:2b:91:4c:99:cd:9b:da:21:
ec:2b:a3:ff:1d:3c:0e:9e:dc:25:c0:06:37:81:e5:
14:80:c5:6f:22:58:bf:25:04:00:0f:a4:6d:0c:d9:
e6:68:bc:f7:61:5d:04:e9:d9:c7:e7:8c:15:82:f1:
df:26:cc:46:1e:fb:ef:d8:96:36:c7:3e:6c:06:cb:
56:72:9a:d1:78:79:65:cc:b8:40:13:31:a0:6e:29:
e2:80:93:7d:a4:ac:73:fc:24:70:de:8c:74:9c:36:
91:7d:f1:5b:6c:69:37:63:3c:10:04:49:8c:17:84:
75:d9:0b:86:3f:1c:00:43:5b:b2:76:85:e8:bd:ed:
95:8d:db
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Alternative Name:
DNS:*.hello.com, DNS:*.world.org, IP Address:0.0.0.0
Signature Algorithm: sha1WithRSAEncryption
90:3d:97:f8:03:bb:8c:f4:35:2d:3a:7a:46:6e:92:0b:93:bb:
dd:a5:b0:2a:cb:0f:0f:aa:76:50:f0:71:a8:0c:8e:08:36:36:
b8:44:cc:e1:d8:06:7e:ab:5f:29:e7:f4:2d:e2:20:2a:b4:8a:
eb:61:9f:b5:fa:3a:8d:3c:fc:df:b3:2a:c2:be:de:e1:e5:31:
6f:82:cc:54:83:8a:4c:c2:cc:fe:e8:04:64:8d:8e:bb:f5:54:
f8:e5:c1:1e:3f:30:26:87:45:e6:72:5a:ae:1d:ef:a1:8e:7a:
59:54:05:0e:b4:e9:bb:ff:4b:c3:16:b8:f7:77:50:d0:7f:ce:
4b:81:0b:ba:8d:07:93:c2:6f:dc:31:8d:6d:4d:76:fc:84:47:
7b:8e:bc:12:dd:2c:df:3c:32:18:e7:6b:77:1e:6c:6d:99:72:
ca:1e:fe:7c:cf:85:40:90:7b:64:c2:22:e5:eb:f1:78:ab:4f:
d5:9d:77:28:84:e4:1a:14:01:54:32:6b:4d:40:ba:8c:ea:c3:
c8:5e:9b:cd:a9:7e:e6:89:21:75:1c:3c:75:4f:29:04:ff:77:
46:34:b6:14:32:3c:98:8f:11:5e:5f:7f:54:b7:30:42:63:b6:
cf:a5:52:85:42:29:23:a2:15:55:13:3d:20:91:b0:d3:4a:f9:
40:21:a2:86:7d:1d:b0:46:03:e7:3f:89:e4:0f:fc:ce:bb:a6:
dd:f6:63:80:74:f0:bb:22:77:ba:f3:c0:24:e4:ce:74:37:32:
c5:a7:52:db:e9:19:51:91:da:7b:a8:51:df:b7:1f:42:ad:25:
a5:ec:2d:01:b5:f5:45:11:34:2c:b9:57:99:c9:f7:25:f7:04:
81:74:f5:e3:c3:62:b3:e5:b7:89:57:c4:4a:20:23:9e:50:24:
b2:cd:8d:33:d6:80:8c:28:13:89:92:1b:c3:66:11:9f:6d:96:
c8:14:41:18:90:bc:09:9b:69:64:7c:57:5e:85:47:14:e9:39:
48:5f:57:69:bb:40:11:5e:de:99:26:66:f0:98:32:ce:f6:5f:
be:a7:a3:d7:9c:a5:45:cb:71:cb:45:df:f7:11:9c:95:3e:f9:
10:80:77:57:c1:ce:40:fa:46:53:da:3d:ef:67:f6:79:d3:2c:
5a:dc:de:6d:ad:ff:04:c1:86:94:b0:ab:32:e0:83:db:09:cd:
79:4b:c0:3e:29:b8:60:e1:25:fe:45:26:3b:3c:31:79:1d:8c:
bc:af:56:9b:65:97:ce:5d:ae:9e:30:28:12:7c:fb:8e:e1:f6:
a8:65:4f:fb:ef:28:d5:20:70:3a:bf:a6:e9:b0:5b:0a:a1:d3:
33:b0:55:52:43:ca:0f:dc
可以看到 Subject Alternative Name 改变。
X509v3 extensions:
X509v3 Subject Alternative Name:
DNS:*.hello.com, DNS:*.world.org, IP Address:0.0.0.0
用 self-sgined CA 验证 web server certificate
可以使用命令 openssl verify -CAfile ca-cert.pem server-cert.pem
-CAfile: 指定 self-signed CA 证书
openssl verify -CAfile ca-cert.pem server-cert.pem
server-cert.pem: OK
reference
https://www.youtube.com/watch?v=7YgaZIFn7mY