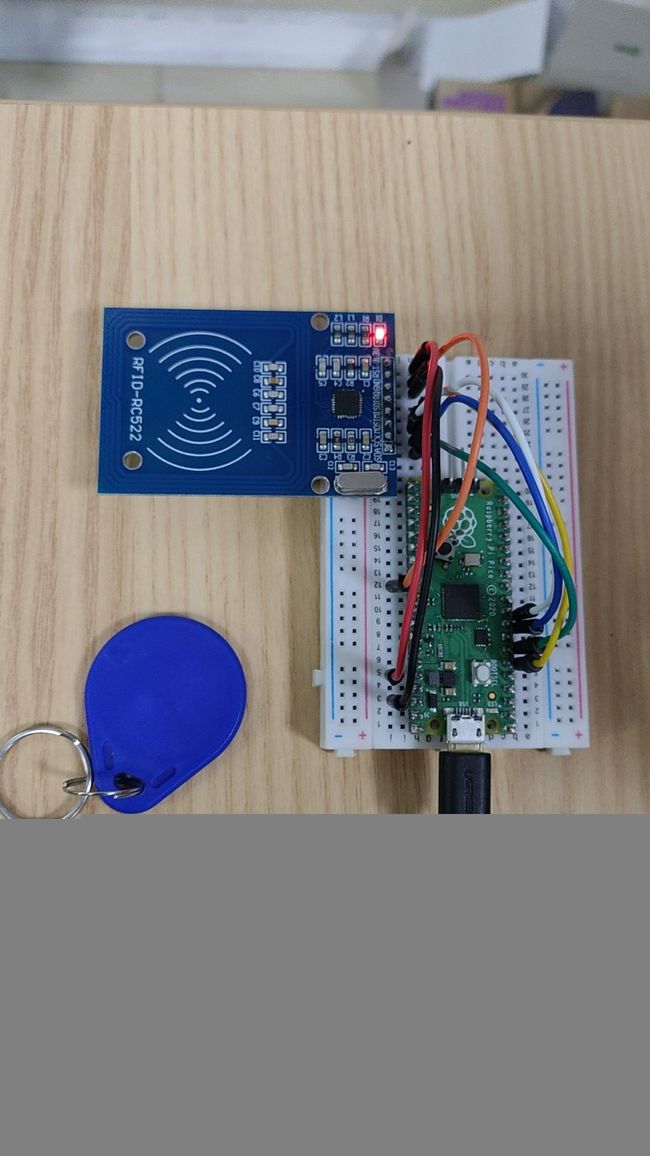
树莓派PICO+RC522读写M1卡
树莓派PICO+RC522读写M1卡
- M1卡简介
-
- M1卡的基本信息:
- M1卡的存储结构 :
- 树莓派PICO+RC522读写示例
-
- micropython RC522库
- 读扇区代码示例
- 写扇区代码示例
M1卡简介
M1芯片:全称为NXP Mifare1系列是由菲利浦子公司恩智浦生产。如常用的S50及S70。
M1卡的基本信息:
- 容量为8K位EEPROM
- 分为16个扇区,每个扇区为4块,每块16个字节,以块为存取单位
- 每个扇区有独立的一组密码及访问控制 l 每张卡有唯一序列号,为32位
- 具有防冲突机制,支持多卡操作
- 无电源,自带天线,内含加密控制逻辑和通讯逻辑电路
- 数据保存期为10年,可改写10万次,读无限次
- 工作温度:-20℃~50℃(湿度为90%) l 工作频率:13.56MHZ
- 通信速率:106 KBPS
- 读写距离:10 cm以内(与读写器有关)
M1卡的存储结构 :
- M1卡分为16个扇区,每个扇区由4块(块0、块1、块2、块3)组成,将16个扇区的64个块按绝对地址编号为0~63,存贮结构如下图所示:
| 扇区 | 块 | 数据类型 | 地址编号 | |
|---|---|---|---|---|
| 块0 | 用户数据 | 数据块 | 0 | |
| 扇区0 | 块1 | 用户数据 | 数据块 | 1 |
| 块2 | 用户数据 | 数据块 | 2 | |
| 块3 | 密码A 存取控制 密码B | 控制块 | 3 | |
| 块0 | 用户数据 | 数据块 | 4 | |
| 扇区1 | 块1 | 用户数据 | 数据块 | 5 |
| 块2 | 用户数据 | 数据块 | 6 | |
| 块3 | 密码A 存取控制 密码B | 控制块 | 7 | |
| 扇区n | … | … | … | |
| 块0 | 用户数据 | 数据块 | 60 | |
| 扇区15 | 块1 | 用户数据 | 数据块 | 61 |
| 块2 | 用户数据 | 数据块 | 62 | |
| 块3 | 密码A 存取控制 密码B | 控制块 | 63 |
- 第0扇区的块0(即绝对地址0块)出厂固化用于存放厂商代码,不可改写。
- 每个扇区的块0、块1、块2为数据块,可用于存贮数据。数据块可用作数据保存(读、写操作)。亦可用作数据值,可进行(初始化值、加值、减值、读值等操作)。
- 每个扇区的块3为控制块,包括了密码A、存取控制、密码B。具体结构如
下:
| 密码A(6字节) | 存取控制(4字节) | 密码B(6字节) |
|---|---|---|
| A0 A1 A2 A3 A4 A5 | FF 07 80 69 | B0 B1 B2 B3 B4 B5 |
存取控制共4个字节,如:(FF 07 80 69),其中字节9为备用字节,存储结构如下:
| bit | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
|---|---|---|---|---|---|---|---|---|
| 字节6 | C23_b | C22_b | C21_b | C20_b | C13_b | C12_b | C11_b | C10_b |
| 字节7 | C13 | C12 | C11 | C10 | C33_b | C32_b | C31_b | C30_b |
| 字节8 | C33 | C32 | C31 | C30 | C23 | C22 | C21 | C20 |
| 字节9 |
(注:_b表示取反)
树莓派PICO+RC522读写示例
micropython RC522库
mfrc522.py
from machine import Pin, SPI
from os import uname
class MFRC522:
DEBUG = False
OK = 0
NOTAGERR = 1
ERR = 2
REQIDL = 0x26
REQALL = 0x52
AUTHENT1A = 0x60
AUTHENT1B = 0x61
PICC_ANTICOLL1 = 0x93
PICC_ANTICOLL2 = 0x95
PICC_ANTICOLL3 = 0x97
def __init__(self, sck, mosi, miso, rst, cs,baudrate=1000000,spi_id=0):
self.sck = Pin(sck, Pin.OUT)
self.mosi = Pin(mosi, Pin.OUT)
self.miso = Pin(miso)
self.rst = Pin(rst, Pin.OUT)
self.cs = Pin(cs, Pin.OUT)
self.rst.value(0)
self.cs.value(1)
board = uname()[0]
if board == 'WiPy' or board == 'LoPy' or board == 'FiPy':
self.spi = SPI(0)
self.spi.init(SPI.MASTER, baudrate=1000000, pins=(self.sck, self.mosi, self.miso))
elif (board == 'esp8266') or (board == 'esp32'):
self.spi = SPI(baudrate=100000, polarity=0, phase=0, sck=self.sck, mosi=self.mosi, miso=self.miso)
self.spi.init()
elif board == 'rp2':
self.spi = SPI(spi_id,baudrate=baudrate,sck=self.sck, mosi= self.mosi, miso= self.miso)
else:
raise RuntimeError("Unsupported platform")
self.rst.value(1)
self.init()
def _wreg(self, reg, val):
self.cs.value(0)
self.spi.write(b'%c' % int(0xff & ((reg << 1) & 0x7e)))
self.spi.write(b'%c' % int(0xff & val))
self.cs.value(1)
def _rreg(self, reg):
self.cs.value(0)
self.spi.write(b'%c' % int(0xff & (((reg << 1) & 0x7e) | 0x80)))
val = self.spi.read(1)
self.cs.value(1)
return val[0]
def _sflags(self, reg, mask):
self._wreg(reg, self._rreg(reg) | mask)
def _cflags(self, reg, mask):
self._wreg(reg, self._rreg(reg) & (~mask))
def _tocard(self, cmd, send):
recv = []
bits = irq_en = wait_irq = n = 0
stat = self.ERR
if cmd == 0x0E:
irq_en = 0x12
wait_irq = 0x10
elif cmd == 0x0C:
irq_en = 0x77
wait_irq = 0x30
self._wreg(0x02, irq_en | 0x80)
self._cflags(0x04, 0x80)
self._sflags(0x0A, 0x80)
self._wreg(0x01, 0x00)
for c in send:
self._wreg(0x09, c)
self._wreg(0x01, cmd)
if cmd == 0x0C:
self._sflags(0x0D, 0x80)
i = 2000
while True:
n = self._rreg(0x04)
i -= 1
if ~((i != 0) and ~(n & 0x01) and ~(n & wait_irq)):
break
self._cflags(0x0D, 0x80)
if i:
if (self._rreg(0x06) & 0x1B) == 0x00:
stat = self.OK
if n & irq_en & 0x01:
stat = self.NOTAGERR
elif cmd == 0x0C:
n = self._rreg(0x0A)
lbits = self._rreg(0x0C) & 0x07
if lbits != 0:
bits = (n - 1) * 8 + lbits
else:
bits = n * 8
if n == 0:
n = 1
elif n > 16:
n = 16
for _ in range(n):
recv.append(self._rreg(0x09))
else:
stat = self.ERR
return stat, recv, bits
def _crc(self, data):
self._cflags(0x05, 0x04)
self._sflags(0x0A, 0x80)
for c in data:
self._wreg(0x09, c)
self._wreg(0x01, 0x03)
i = 0xFF
while True:
n = self._rreg(0x05)
i -= 1
if not ((i != 0) and not (n & 0x04)):
break
return [self._rreg(0x22), self._rreg(0x21)]
def init(self):
self.reset()
self._wreg(0x2A, 0x8D)
self._wreg(0x2B, 0x3E)
self._wreg(0x2D, 30)
self._wreg(0x2C, 0)
self._wreg(0x15, 0x40)
self._wreg(0x11, 0x3D)
self.antenna_on()
def reset(self):
self._wreg(0x01, 0x0F)
def antenna_on(self, on=True):
if on and ~(self._rreg(0x14) & 0x03):
self._sflags(0x14, 0x03)
else:
self._cflags(0x14, 0x03)
def request(self, mode):
self._wreg(0x0D, 0x07)
(stat, recv, bits) = self._tocard(0x0C, [mode])
if (stat != self.OK) | (bits != 0x10):
stat = self.ERR
return stat, bits
def anticoll(self,anticolN):
ser_chk = 0
ser = [anticolN, 0x20]
self._wreg(0x0D, 0x00)
(stat, recv, bits) = self._tocard(0x0C, ser)
if stat == self.OK:
if len(recv) == 5:
for i in range(4):
ser_chk = ser_chk ^ recv[i]
if ser_chk != recv[4]:
stat = self.ERR
else:
stat = self.ERR
return stat, recv
def PcdSelect(self, serNum,anticolN):
backData = []
buf = []
buf.append(anticolN)
buf.append(0x70)
#i = 0
###xorsum=0;
for i in serNum:
buf.append(i)
#while i<5:
# buf.append(serNum[i])
# i = i + 1
pOut = self._crc(buf)
buf.append(pOut[0])
buf.append(pOut[1])
(status, backData, backLen) = self._tocard( 0x0C, buf)
if (status == self.OK) and (backLen == 0x18):
return 1
else:
return 0
def SelectTag(self, uid):
byte5 = 0
#(status,puid)= self.anticoll(self.PICC_ANTICOLL1)
#print("uid",uid,"puid",puid)
for i in uid:
byte5 = byte5 ^ i
puid = uid + [byte5]
if self.PcdSelect(puid,self.PICC_ANTICOLL1) == 0:
return (self.ERR,[])
return (self.OK , uid)
def tohexstring(self,v):
s="["
for i in v:
if i != v[0]:
s = s+ ", "
s=s+ "0x{:02X}".format(i)
s= s+ "]"
return s
def SelectTagSN(self):
valid_uid=[]
(status,uid)= self.anticoll(self.PICC_ANTICOLL1)
#print("Select Tag 1:",self.tohexstring(uid))
if status != self.OK:
return (self.ERR,[])
if self.DEBUG: print("anticol(1) {}".format(uid))
if self.PcdSelect(uid,self.PICC_ANTICOLL1) == 0:
return (self.ERR,[])
if self.DEBUG: print("pcdSelect(1) {}".format(uid))
#check if first byte is 0x88
if uid[0] == 0x88 :
#ok we have another type of card
valid_uid.extend(uid[1:4])
(status,uid)=self.anticoll(self.PICC_ANTICOLL2)
#print("Select Tag 2:",self.tohexstring(uid))
if status != self.OK:
return (self.ERR,[])
if self.DEBUG: print("Anticol(2) {}".format(uid))
rtn = self.PcdSelect(uid,self.PICC_ANTICOLL2)
if self.DEBUG: print("pcdSelect(2) return={} uid={}".format(rtn,uid))
if rtn == 0:
return (self.ERR,[])
if self.DEBUG: print("PcdSelect2() {}".format(uid))
#now check again if uid[0] is 0x88
if uid[0] == 0x88 :
valid_uid.extend(uid[1:4])
(status , uid) = self.anticoll(self.PICC_ANTICOLL3)
#print("Select Tag 3:",self.tohexstring(uid))
if status != self.OK:
return (self.ERR,[])
if self.DEBUG: print("Anticol(3) {}".format(uid))
if self.PcdSelect(uid,self.PICC_ANTICOLL3) == 0:
return (self.ERR,[])
if self.DEBUG: print("PcdSelect(3) {}".format(uid))
valid_uid.extend(uid[0:5])
# if we are here than the uid is ok
# let's remove the last BYTE whic is the XOR sum
return (self.OK , valid_uid[:len(valid_uid)-1])
#return (self.OK , valid_uid)
def auth(self, mode, addr, sect, ser):
return self._tocard(0x0E, [mode, addr] + sect + ser[:4])[0]
def authKeys(self,uid,addr,keyA=None, keyB=None):
status = self.ERR
if keyA is not None:
status = self.auth(self.AUTHENT1A, addr, keyA, uid)
elif keyB is not None:
status = self.auth(self.AUTHENT1B, addr, keyB, uid)
return status
def stop_crypto1(self):
self._cflags(0x08, 0x08)
def read(self, addr):
data = [0x30, addr]
data += self._crc(data)
(stat, recv, _) = self._tocard(0x0C, data)
return stat, recv
def write(self, addr, data):
buf = [0xA0, addr]
buf += self._crc(buf)
(stat, recv, bits) = self._tocard(0x0C, buf)
if not (stat == self.OK) or not (bits == 4) or not ((recv[0] & 0x0F) == 0x0A):
stat = self.ERR
else:
buf = []
for i in range(16):
buf.append(data[i])
buf += self._crc(buf)
(stat, recv, bits) = self._tocard(0x0C, buf)
if not (stat == self.OK) or not (bits == 4) or not ((recv[0] & 0x0F) == 0x0A):
stat = self.ERR
return stat
def writeSectorBlock(self,uid, sector, block, data, keyA=None, keyB = None):
absoluteBlock = sector * 4 + (block % 4)
if absoluteBlock > 63 :
return self.ERR
if len(data) != 16:
return self.ERR
if self.authKeys(uid,absoluteBlock,keyA,keyB) != self.ERR :
return self.write(absoluteBlock, data)
return self.ERR
def readSectorBlock(self,uid ,sector, block, keyA=None, keyB = None):
absoluteBlock = sector * 4 + (block % 4)
if absoluteBlock > 63 :
return self.ERR, None
if self.authKeys(uid,absoluteBlock,keyA,keyB) != self.ERR :
return self.read(absoluteBlock)
return self.ERR, None
def MFRC522_DumpClassic1K(self,uid, Start=0, End=64, keyA=None, keyB=None):
for absoluteBlock in range(Start,End):
status = self.authKeys(uid,absoluteBlock,keyA,keyB)
# Check if authenticated
print("{:02d} S{:02d} B{:1d}: ".format(absoluteBlock, absoluteBlock//4 , absoluteBlock % 4),end="")
if status == self.OK:
status, block = self.read(absoluteBlock)
if status == self.ERR:
break
else:
for value in block:
print("{:02X} ".format(value),end="")
print(" ",end="")
for value in block:
if (value > 0x20) and (value < 0x7f):
print(chr(value),end="")
else:
print('.',end="")
print("")
else:
break
if status == self.ERR:
print("Authentication error")
return self.ERR
return self.OK
读扇区代码示例
mfrc522_read_sectory.py
from mfrc522 import MFRC522
import utime
reader = MFRC522(spi_id=0,sck=6,miso=4,mosi=7,cs=5,rst=22)
print("Bring TAG closer...")
print("")
while True:
# 初始化读卡器
reader.init()
# 寻卡
(stat, tag_type) = reader.request(reader.REQIDL)
# 寻到卡
if stat == reader.OK:
(stat, uid) = reader.SelectTagSN()
if stat == reader.OK:
card = int.from_bytes(bytes(uid),"little",False)
print("CARD ID: "+str(card))
keyA = [0xFF,0xFF,0xFF,0xFF,0xFF,0xFF]
keyB = [0xFF,0xFF,0xFF,0xFF,0xFF,0xFF]
sector = 2 # M1卡分为16个扇区,每个扇区4块(0~3)共64块,按块号编址为0~63
block = 0 # 0~3 每个块0,1,2为数据块存放用户数据,块3为控制字 6字节密码A+4字节控制字+6字节密码B AAAAAAAAAAAACCCCCCCCBBBBBBBBBBBB
(stat, recv) = reader.readSectorBlock(uid ,sector, block, keyA, None) # 验证密码A
#(stat, recv) = reader.readSectorBlock(uid ,sector, block, None, keyB) # 验证密码B
print(stat, recv)
utime.sleep_ms(500)
写扇区代码示例
mfrc522_write_sectory.py
from mfrc522 import MFRC522
import utime
reader = MFRC522(spi_id=0,sck=6,miso=4,mosi=7,cs=5,rst=22)
print("Bring TAG closer...")
print("")
while True:
# 初始化读卡器
reader.init()
# 寻卡
(stat, tag_type) = reader.request(reader.REQIDL)
# 找到卡
if stat == reader.OK:
(stat, uid) = reader.SelectTagSN()
if stat == reader.OK:
card = int.from_bytes(bytes(uid),"little",False)
print("CARD ID: "+str(card))
# 密码A,密码B 定义
keyA = [0xFF,0xFF,0xFF,0xFF,0xFF,0xFF]
keyB = [0xFF,0xFF,0xFF,0xFF,0xFF,0xFF]
# 要操作的扇区
sector = 2 # M1卡分为16个扇区,每个扇区4块(0~3)共64块,按块号编址为0~63
# 要操作的块
block = 0 # 0~3 每个块0,1,2为数据块存放用户数据,块3为控制字 6字节密码A+4字节控制字+6字节密码B
# 读扇区数据
(stat, recv) = reader.readSectorBlock(uid ,sector, block, keyA, None) # 验证密码A
#(stat, recv) = reader.readSectorBlock(uid ,sector, block, None, keyB) # 验证密码B
print(stat, recv)
# 改扇区数据
data = [] # 数据长度必须为16个字节
for x in range(0, 16):
data.append(0x03)
# 写扇区数据
stat = reader.writeSectorBlock(uid, sector, block, data, keyA)
if stat == reader.OK:
print("write ok.")
else:
print("write error.")
utime.sleep_ms(1000)