Linux tun虚拟网卡通信初识
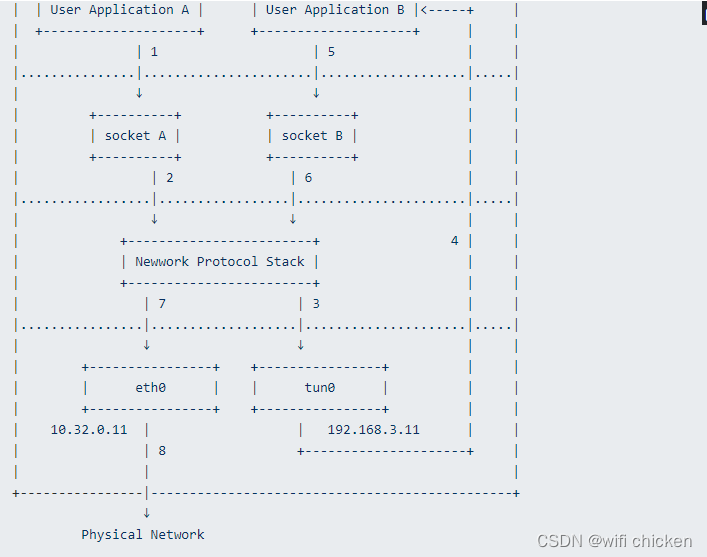
什么是linux tun设备
Linux TUN 设备是一种虚拟网络设备,用于在用户空间和内核空间之间建立数据通道,使用户空间程序可以通过这个设备与内核网络栈进行交互。TUN 设备是一种通用的网络隧道设备,常用于实现虚拟专用网络(VPN)和其他网络隧道技术。
TUN 设备的工作原理
- 将网络数据包从用户空间发送到内核空间,或者从内核空间发送到用户空间。可以收发第三层数据报文包,如IP封包,这使得用户空间的应用程序可以读取和处理传入的数据包,然后将数据包发送回TUN 设备,再由内核负责将数据包发送到目标地址。
- 在使用 TUN 设备时,用户空间程序通常会打开 TUN 设备文件,并像读写普通文件一样对其进行读写操作。这样,用户空间程序就可以将网络数据包发送到 TUN 设备或者从 TUN 设备读取接收到的数据包。TUN 设备通常具有一个虚拟的 IP 地址,作为与内核网络栈进行交互的入口和出口
基本处理框架
- 创建 TUN 设备: 在 Linux 系统中,可以使用 ip 命令或者其他网络管理工具来创建 TUN 设备。
- 用户空间应用程序与 TUN 设备交互: 用户空间的应用程序通常会打开 TUN 设备文件,这类似于打开普通文件。例如,应用程序可以打开 /dev/net/tun 设备文件。
- 数据包传输: 当用户空间的应用程序向 TUN 设备文件写入数据包时,数据包将被发送到内核空间的 TUN 设备驱动程序。这个过程是由内核的 TUN/TAP 驱动来完成的。
- 内核处理: 内核中的 TUN/TAP 驱动程序接收从用户空间传入的数据包。对于 TUN 设备,它会将数据包解析为 IP 数据包,并将其发送到内核网络栈进行进一步处理。
- 数据包处理: 在内核网络栈中,数据包将按照路由表和网络配置进行处理。如果数据包的目标地址与本地网络或者路由表匹配,那么数据包将被内核转发到目标地址。
- 接收数据包: 当内核收到其他网络设备传入的数据包(如网络接口收到的数据包),如果目标地址是 TUN 设备的 IP 地址,那么数据包将被传递给 TUN 设备驱动程序。
- 用户空间读取: 数据包通过 TUN 设备驱动程序传递到用户空间的应用程序打开的 TUN 设备文件。应用程序可以读取这些数据包并进行处理。
linux tun设备可以用作什么技术
- VPN(Virtual Private Network): TUN 设备可用于构建 VPN。通过将数据包从用户空间发送到内核空间,再通过TUN 设备进行加密、隧道封装和传输,可以实现安全的远程访问和数据传输。
- 隧道技术: TUN 设备也可用于其他隧道技术,如隧道模式下的 IPv6-over-IPv4 和 IPv4-over-IPv6 隧道。它允许不同网络之间通过隧道进行通信。
- 加密通信: TUN 设备可以用于实现端到端的加密通信,保护数据的安全性和隐私。
- 虚拟专用网络: 使用 TUN 设备,可以创建虚拟专用网络(VPN)或虚拟局域网(VLAN),将不同的网络或子网连接在一起。
- 网络隔离: TUN 设备可以用于实现网络隔离,将不同的应用程序或服务隔离在不同的虚拟网络中,增强网络的安全性。
- 协议代理: TUN 设备还可以用作协议代理,允许用户空间应用程序处理特定的网络协议,例如将 UDP 或 TCP 流量进行自定义处理。
- 网络测试和仿真: 利用 TUN 设备,可以在用户空间中模拟网络环境,用于测试和仿真网络应用程序的性能和稳定性。
本文今天要完成什么?
使用虚拟机ubuntu 自带tun驱动完成:
- 虚拟驱动的启动
- 应用层发包给虚拟网卡驱动tun并写入设备节点文件,应用层完成读取,加密,写入设备节点并发送给协议栈
- 使用tcpdump工具抓取包验证是否正确发送与接收
完成框架
- 利用已有的tun设备驱动,打开并配置ip,添加静态路由表
- 写两个应用层进程,分别完成数据发送到tun和数据接收处理加密并发回tun驱动
linux已经自带驱动:
ubuntu:/dev/net$ ls
tun
应用层代码1:
基本逻辑:
- 打开虚拟设备网卡
- 添加静态路由
- 阻塞等待数据的到来
- read后,再进行wirite操作
#include 应用层2代码
基本逻辑:
负责给虚拟网卡驱动发送应用层数据包
#include 应用层如何编译
如果您经常阅读我的文章,就不应该问出这样的问题,以前的文章都有提及!
验证
root权限执行应用层代码1与结果(有删减):
sudo ./net_device_user1
RTNETLINK answers: File exists
Open tun/tap device: tun0 for reading...
Read 50 bytes from tun/tap device
45 00 00 32 03 FFFFFF9E 40 00 40 11 23 1B 0A 00 00 01
0A 00 00 02 FFFFFF86 0D 30 39 00 1E 05 27 48 65 6C 6C
6F 2C 20 54 55 4E 20 64 65 76 69 63 65 21 21 21
21 21
Sent 28 bytes to TUN device.
Read 47 bytes from tun/tap device
45 00 00 2F 03 FFFFFF9F 40 00 40 11 23 1D 0A 00 00 01
0A 00 00 02 FFFFFFC0 3E 04 FFFFFFD2 00 1B FFFFFFF3 FFFFFFDE 74 75 6E 20
74 75 6E 74 20 74 75 6E 74 21 21 21 21 21 21
Sent 28 bytes to TUN device.
root权限执行应用层代码2与结果:
sudo ./net_device.o
------------start-------------------
抓取tupdump包
sudo tcpdump -i tun0 -w tcpdump_30.pcap
tcpdump: listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
tcpdump: pcap_loop: The interface went down
16 packets captured
16 packets received by filter
0 packets dropped by kernel
![]()
分别抓到了应用层发来的数据包(两个包),读取完后完成数据包的发送
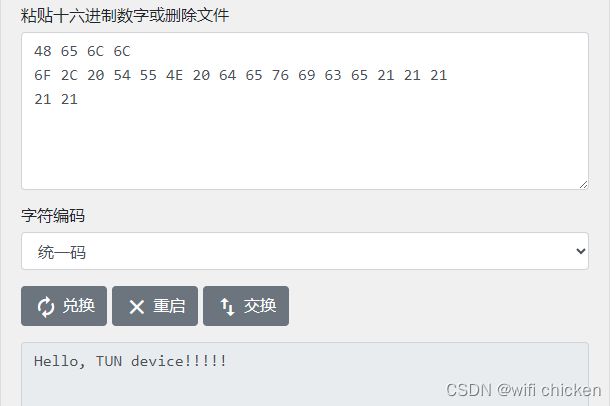
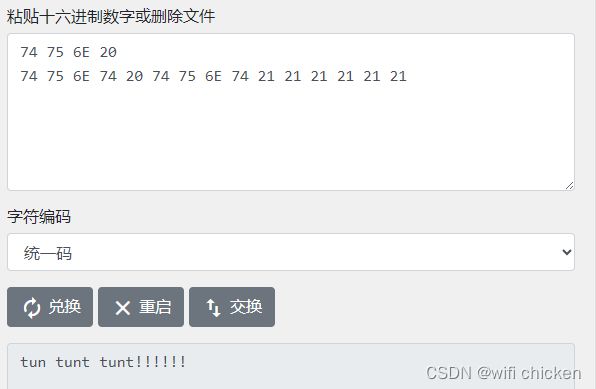
利用十六进制转字符串验证应用代码2发送给应用代码1的数据是否发送成功:
第一个包
Read 50 bytes from tun/tap device
45 00 00 32 03 FFFFFF9E 40 00 40 11 23 1B 0A 00 00 01
0A 00 00 02 FFFFFF86 0D 30 39 00 1E 05 27 48 65 6C 6C
6F 2C 20 54 55 4E 20 64 65 76 69 63 65 21 21 21
21 21
Read 47 bytes from tun/tap device
45 00 00 2F 03 FFFFFF9F 40 00 40 11 23 1D 0A 00 00 01
0A 00 00 02 FFFFFFC0 3E 04 FFFFFFD2 00 1B FFFFFFF3 FFFFFFDE 74 75 6E 20
74 75 6E 74 20 74 75 6E 74 21 21 21 21 21 21
结果
验证成功
ps
完成的功能很少,希望这能抛砖引玉
代码解释不是特别详细,代码行中有很多注释,希望能帮助到你