网络安全 Day28-运维安全项目-加密隧道
运维安全项目-加密隧道
- 1. 加密隧道服务概述
- 2. openVPN应用场景
- 3. 虚拟机环境准备
-
- 3.0 准备知识
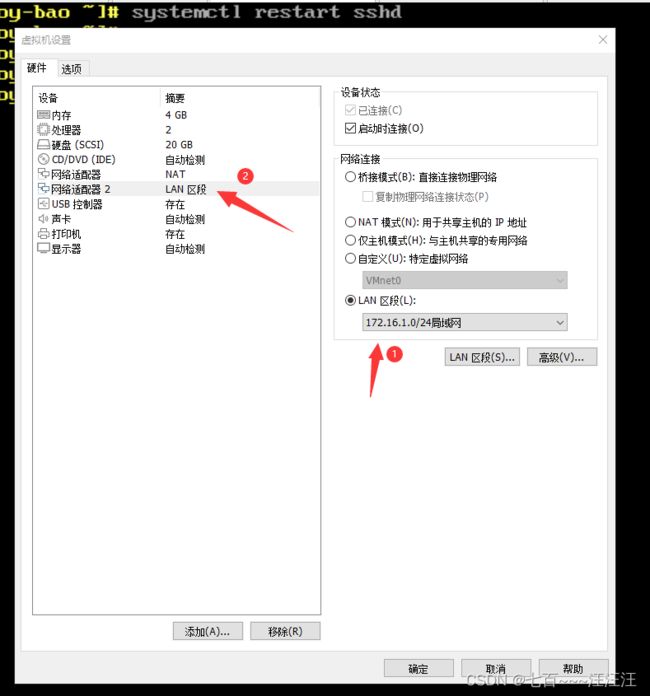
- 3.1 添加网卡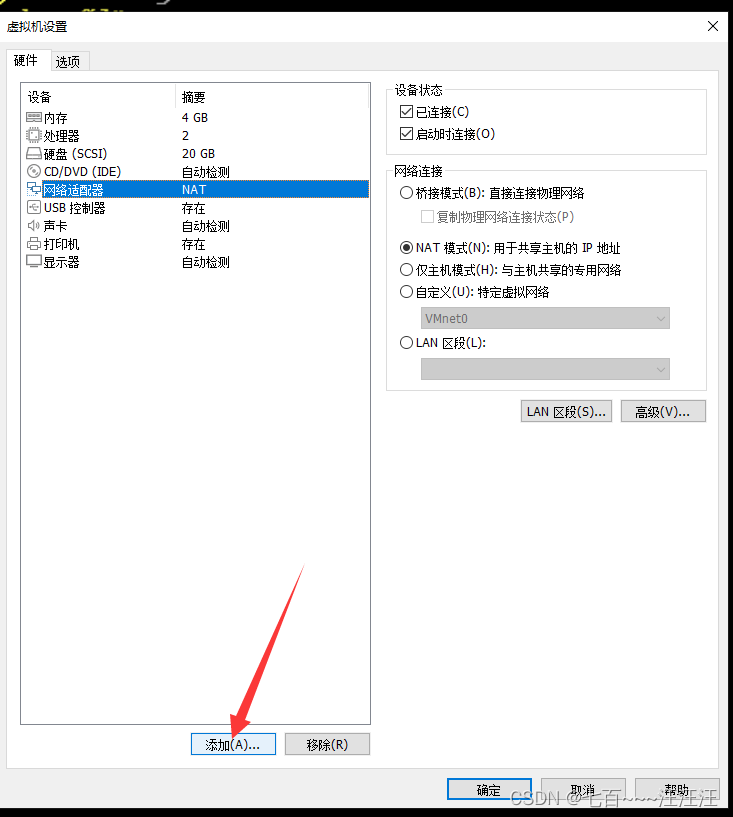
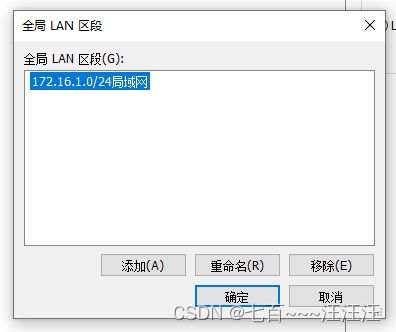
- 3.2 配置内网(LAN区段)
- 3.3 虚拟机选择LAN区段
- 3.4 书写eth1网卡配置文件
- 4. OpenVPN服务端配置
-
- 4.1 环境准备简介
- 4.2 证书准备流程
-
- 4.2.1 安装证书创建工具
- 4.2.2 创建ca证书
-
- 4.2.2.1 充当权威机构 修改vars文件
- 4.2.2.2 充当权威机构 创建ca证书
- 4.2.3 创建server端证书和私钥文件
- 4.2.4 创建dh-pem 算法文件和目录汇总
- 4.2.5 创建client证书
- 4.2.6 汇总
- 4.2.7 小结
- 4.3 服务端配置文件
-
- 4.3.1 书写open服务端配置文件
- 4.3.2 准备服务端需要的文件
- 4.3.3 修改systemctl配置文件
- 4.3.4 启动
- 4.3.5 检查进程与端口
- 5. 排障流程
- 6. 客户端配置文件
-
- 6.1 安装客户端
- 6.2 书写配置文件
- 6.3 准备配置文件需要的文件
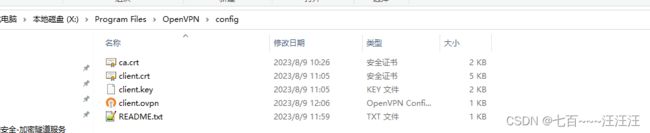
- 6.4 复制对应的文件到config目录下
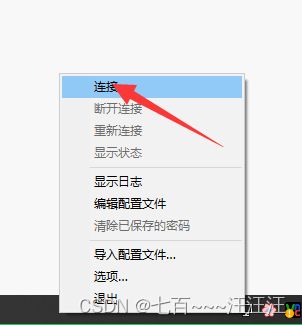
- 6.5 启动客户端
1. 加密隧道服务概述
- 两点如何传输数据最安全
- 方案1: 专线(成本高)
- 方案2: 硬件设备3层路由器 , 硬件设备 virtual private network 虚拟专有网络 深信服VPN
- 方案3: 开源软件
- pptp (不推荐) 使用最简单,不是很稳定,依赖于网络设备的支持.
- OpenVPN 实现用户/运维/开发,访问网站内网.
2. openVPN应用场景
- 运营:通过OpenVPN实现网站安全登录:(后台管理地址,设置为只能能通过访问.)
- 开发:通过OpenVPN让开发与测试人员连接网站,进行开发测试(在家的时候)
- 运维:通过OpenVPN让各种用户(运维)连接网站内网服务器,或者是连接JMS

3. 虚拟机环境准备
3.0 准备知识
- LAN区段
- 没有外网IP,可以理解为一个LAN区段,作为一个虚拟的交换机连接内内网的设备让其进行通信
- 在堡垒机中作为内网IP与此同时此虚拟机也有外网IP
- 在配置好VPN之后,VPN客户端就会访问内网了
3.1 添加网卡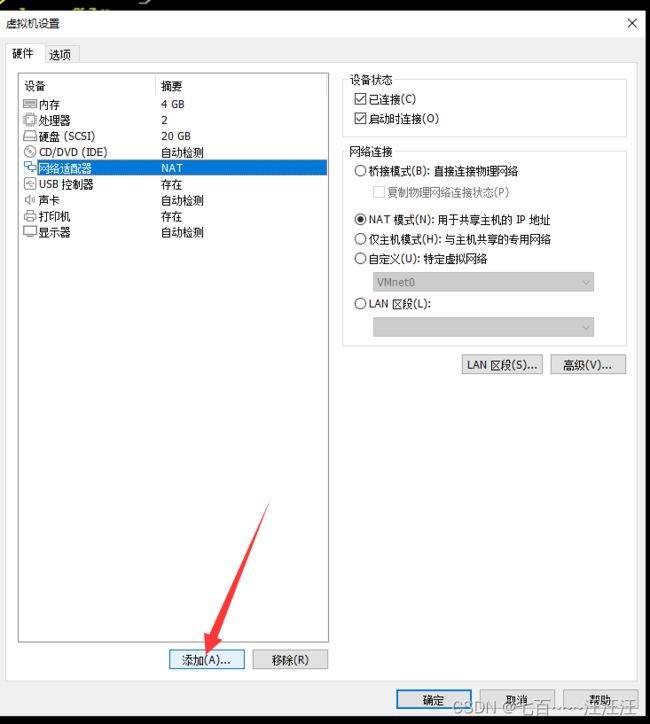
3.2 配置内网(LAN区段)
3.3 虚拟机选择LAN区段
3.4 书写eth1网卡配置文件
- 编辑与创建新的网卡配置文件
vim /etc/sysconfig/network-scripts/ifcfg-eth1 TYPE=Ethernet BOOTPROTO=none IPADDR=172.16.1.61 PREFIX=24 NAME=eth1 DEVICE=eth1 ONBOOT=yes - 然后重启network:
systemctl restart network - 检查ip:
ip a(如果和配置文件中的IP一致就对了)
4. OpenVPN服务端配置
4.1 环境准备简介
- m01 10.0.0.61
| 环境准备 | 说明 |
|---|---|
| oldboy-bao | open server服务端 |
| windows 笔记本 | open 客户端 |
4.2 证书准备流程
1️⃣创建CA证书 ca.crt 公章
2️⃣server密钥 server.crt server.key服务端使用的毕业证书
3️⃣client密钥
4️⃣OpenVPN服务端配置文件
4.2.1 安装证书创建工具
- 检查是否可以访问网络:
ping baidu.com 结果中只要有time表示可以链接 - open 服务端安装:
yum install -y open easy-rsa - 检查是否完成安装:
rpm -qa open
4.2.2 创建ca证书
4.2.2.1 充当权威机构 修改vars文件
- 创建指令(学安全现阶段没必要弄懂)
#准备目录 mkdir -p /opt/easy-rsa #已有的内容复制过去 cp -a /usr/share/easy-rsa/3.0.8/* /opt/easy-rsa/ #准备配置文件 cp /usr/share/doc/easy-rsa-3.0.8/vars.example /opt/easy-rsa/vars #书写配置内容 cat >/opt/easy-rsa/vars<<'EOF' if [ -z "$EASYRSA_CALLER" ]; then echo "You appear to be sourcing an Easy-RSA 'vars' file." >&2 echo "This is no longer necessary and is disallowed. See the section called" >&2 echo "'How to use this file' near the top comments for more details." >&2 return 1 fi set_var EASYRSA_DN "cn_only" set_var EASYRSA_REQ_COUNTRY "CN" set_var EASYRSA_REQ_PROVINCE "Beijing" set_var EASYRSA_REQ_CITY "Beijing" set_var EASYRSA_REQ_ORG "oldboylinux" set_var EASYRSA_REQ_EMAIL "[email protected]" set_var EASYRSA_NS_SUPPORT "yes" EOF - 检查指令
##创建var后 检查 权威机构信息 cd /opt/easy-rsa tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── vars #var ca权威机构信息 └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 1 directory, 11 files
4.2.2.2 充当权威机构 创建ca证书
- 初始化,在当前目录创建PKI目录,用于存储证书
- 命令和结果
cd /opt/easy-rsa ./easyrsa init-pki #初始化,第1次的时候运行,后面不需要重复运行。结果 Note: using Easy-RSA configuration from: /opt/easy-rsa/vars #正在使用来自于vars init-pki complete; you may now create a CA or requests. #初始化完成 显示你可以尝试创建 CA证书 Your newly created PKI dir is: /opt/easy-rsa/pki #初始化后的目录在 pki下面 - 检查是否成功:
tree结果中多了个pki目录即可。
- 命令和结果
- 创建根证书,会提示设置密码,用于ca对之后生成的server和client证书签名时使用,其他可默认
- 命令和结果
./easyrsa build-ca结果 Note: using Easy-RSA configuration from: /opt/easy-rsa/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Enter New CA Key Passphrase: #输入密码 并保存好 4-1023位 Re-Enter New CA Key Passphrase: #输入密码 并保存好 Generating RSA private key, 2048 bit long modulus .....................................+++ ................................+++ e is 65537 (0x10001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]:oldboylinux.cn #域名即可 CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /opt/easy-rsa/pki/ca.crt - 检查是否成功:检查是否有这个文件即可
/opt/easy-rsa/pki/ca.crt
- 命令和结果
4.2.3 创建server端证书和私钥文件
- 请求盖章命令和结果
./easyrsa gen-req server nopassNote: using Easy-RSA configuration from: /opt/easy-rsa/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key ....................................+++ .................+++ writing new private key to '/opt/easy-rsa/pki/easy-rsa-2426.tjsuP4/tmp.wLJyRY' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [server]: Keypair and certificate request completed. Your files are: req: /opt/easy-rsa/pki/reqs/server.req #server.req 用于 创建证书(证书资料) key: /opt/easy-rsa/pki/private/server.key #server私钥文件 - 给server端证书签名,首先是对一些信息的确认,可以输入yes,然后创建ca根证书时设置的密码:
./easyrsa sign server server - 检查是否操作成功(有结果就成功了)
ll /opt/easy-rsa/pki/issued/server.crt ll /opt/easy-rsa/pki/private/server.key
4.2.4 创建dh-pem 算法文件和目录汇总
- 创建Diffie-Hellman文件,秘钥交换时的Diffie-Hellman算法:
/easyrsa gen-dh(用于存放在服务端,生成一次即可) - 检查结果:
/opt/easy-rsa/pki/dh.pem
4.2.5 创建client证书
- 创建client端证书和私钥文件
- 创建client端证书和私钥文件,nopass表示不加密私钥文件,其他可默认:
./easyrsa gen-req client nopass - 给client端证书签名,首先是对一些信息的确认,可以输入yes,然后创建ca根证书时设置的密码:
./easyrsa sign client client
- 创建client端证书和私钥文件,nopass表示不加密私钥文件,其他可默认:
- 检查是否成功:
ll /opt/easy-rsa/pki/private/client.key /opt/easy-rsa/pki/issued/client.crt
4.2.6 汇总
| 服务端使用的文件 | 客户端使用的文件 |
|---|---|
| /opt/easy-rsa/pki/ca.crt | /opt/easy-rsa/pki/ca.crt |
| /opt/easy-rsa/pki/dh.pem | |
| /opt/easy-rsa/pki/issued/server.crt | /opt/easy-rsa/pki/issued/client.crt |
| /opt/easy-rsa/pki/private/server.key | /opt/easy-rsa/pki/private/client.key |
| 服务端配置文件 | 客户端配置文件 |
- 目录汇总
[root@m01 /opt/easy-rsa]# tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── pki │ ├── ca.crt #ca证书 │ ├── dh.pem #df算法文件 │ ├── certs_by_serial │ │ ├── 9F69296953C7B7F6DC39C539706A4CA5.pem │ │ └── C98F71084F5C70CCBFEEA9FCB5E94912.pem │ ├── index.txt │ ├── index.txt.attr │ ├── index.txt.attr.old │ ├── index.txt.old │ ├── issued │ │ ├── client.crt #client证书 │ │ └── server.crt #server证书 │ ├── openssl-easyrsa.cnf │ ├── private │ │ ├── ca.key │ │ ├── client.key #客户端私钥 │ │ └── server.key #服务端私钥 │ ├── renewed │ │ ├── certs_by_serial │ │ ├── private_by_serial │ │ └── reqs_by_serial │ ├── reqs │ │ ├── client.req │ │ └── server.req │ ├── revoked │ │ ├── certs_by_serial │ │ ├── private_by_serial │ │ └── reqs_by_serial │ ├── safessl-easyrsa.cnf │ ├── serial │ └── serial.old ├── vars └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 14 directories, 29 file
4.2.7 小结
- 创建vars文件创建ca证书 build-ca
- 创建server证书和私钥
- gen-req server nopass
- sign server server
- dh.pem 文件
- 创建client证书和私钥
- gen-req client nopass
- sign client client
4.3 服务端配置文件
#服务端配置文件
#配置文件中 各种路径默认相对于 /etc/open
4.3.1 书写open服务端配置文件
-
查看配置文件
[root@m01 ~] tree -F /etc/open/ /etc/open/ ├── client/ └── server/ 2 directories, 0 files -
配置文件
vim /etc/open/server/server.conf port 1194 proto udp dev tun ca ca.crt cert server/server.crt key server/server.key dh server/dh.pem server 10.8.0.0 255.255.255.0 push "route 172.16.1.0 255.255.255.0" #ifconfig-pool-persist ipp.txt keepalive 10 120 max-clients 100 status /var/log/open-status.log log /var/log/open.log verb 3 client-to-client persist-key persist-tun duplicate-cn -
配置文件详解
[root@web01 open]# vim /etc/opn/server/server.conf port 1194 #端口 proto udp #协议 dev tun #采用路由隧道模式tun ca ca.crt #ca证书文件位置 /etc/open/ca.crt cert server/server.crt #服务端公钥名称 /etc/open key server/server.key #服务端私钥名称 /etc/open dh server/dh.pem #加密算法文件, 交换证书 校验算法 #/etc/open/server/dh.pem server 10.8.0.0 255.255.255.0 #给客户端分配地址池(ip地址范围),注意:不能和VPN服务器内网网段有相同 push "route 172.16.1.0 255.255.255.0" #客户端连接后,推送给客户端的路由规则 #客户端想访问 172.16.1.0/24 网段联系open服务端 #ifconfig-pool-persist ipp.txt #地址池记录文件位置 未来让open 客户端固定ip地址使用的. keepalive 10 120 #存活时间,10秒ping一次,120 如未收到响应则视为断线 max-clients 100 #最多允许100个客户端连接 status /var/log/open-status.log #日志记录位置 open状态 log /var/log/open.log #open日志记录位置 verb 3 #verbose 日志输出级别 数字越大越详细 最多11(debug) client-to-client #客户端与客户端之间支持通信 persist-key #通过keepalive检测超时后,重新启动VPN,不重新读取keys,保留第一次使用的keys 对私钥进行缓存. persist-tun #检测超时后,重新启动VPN,一直保持tun是linkup的。否则网络会先linkdown然后再linkup duplicate-cn #客户端密钥(证书和私钥)是否可以重复
4.3.2 准备服务端需要的文件
- 复制证书及密钥
cd /opt/easy-rsa/pki/ \cp ca.crt /etc/open/ \cp dh.pem /etc/open/server/ \cp issued/server.crt private/server.key /etc/open/server/ - 检查是否操作成功
[root@oldboy-bao pki]# tree -F /etc/open/ /etc/open/ ├── ca.crt ├── client/ └── server/ ├── dh.pem ├── server.conf ├── server.crt └── server.key 2 directories, 5 files
4.3.3 修改systemctl配置文件
- 修改open的systemctl配置文件
vim /usr/lib/systemd/system/[email protected] 修改ExecStart这行 在%i前面加上 %i/即可。 修改后的样子 ExecStart=/usr/sbin/open --cd /etc/open/ --config %i/%i.conf %i表示 server或 client - 让linux系统重新加载systemctl配置文件:
systemctl daemon-reload
4.3.4 启动
systemctl enable open@server
systemctl start open@server
4.3.5 检查进程与端口
检查端口
ss -lntup |grep 1194
检查进程
ps -ef |grep open
检查ip
ip a s tun0
5. 排障流程
- 检查配置文件书写与相关的文件是否存在。
- 查看日志/var/log/open.log.
- 如果不存在查看/var/log/messages
6. 客户端配置文件
6.1 安装客户端
- 默认安装到C:\Program Files\OpenVPN\
6.2 书写配置文件
存到临时目录
client.o
client
dev tun
proto udp
remote 10.0.0.61 1194
resolv-retry infinite
nobind
ca ca.crt
cert client.crt
key client.key
verb 3
persist-key
########配置说明###################################
client #指定当前VPN是客户端
dev tun #使用tun隧道传输协议
proto udp #使用udp协议传输数据
remote 10.0.0.61 1194 #open服务器IP地址端口号
resolv-retry infinite #断线自动重新连接,在网络不稳定的情况下非常有用
nobind #不绑定本地特定的端口号
ca ca.crt #指定CA证书的文件路径
cert client.crt #指定当前客户端的证书文件路径
key client.key #指定当前客户端的私钥文件路径
verb 3 #指定日志文件的记录详细级别,可选0-9,等级越高日志内容越详细
persist-key #通过keepalive检测超时后,重新启动VPN,不重新读取keys,保留第一次使用的keys
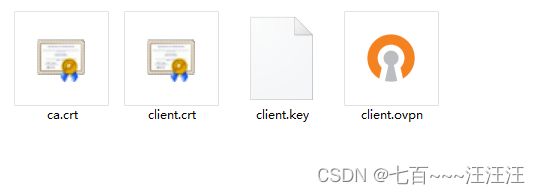
6.3 准备配置文件需要的文件
sz /opt/easy-rsa/pki/ca.crt
sz /opt/easy-rsa/pki/issued/client.crt
sz /opt/easy-rsa/pki/private/client.key
上传到windows桌面,避免直接上传到c盘open目录。