HCIP-Datacom:一篇掌握IPSec VPN的原理与配置!!!
一、背景
随着Internet的发展,越来越多的企业直接通过Internet进行互联,但由于IP协议未考虑安全性,而且Internet上有大量的不可靠用户和网络设备,所以用户业务数据要穿越这些未知网络,根本无法保证数据的安全性,数据易被伪造、篡改或窃取。因此,迫切需要一种兼容IP协议的通用的网络安全方案。为了解决上述问题,IPSec(Internet Protocol Security)应运而生。IPSec是对IP的安全性补充,其工作在IP层,为IP网络通信提供透明的安全服务。
1、IPSCE VPN解决的问题
- 数据来源验证:接收方验证发送方身份是否合法。
- 数据加密:发送方对数据进行加密,以密文的形式在Internet上传送,接收方对接收的加密数据进行解密后处理或直接转发。
- 数据完整性:接收方对接收的数据进行验证,以判定报文是否被篡改。
- 抗重放:接收方拒绝旧的或重复的数据包,防止恶意用户通过重复发送捕获到的数据包所进行的攻击。
2、IPSEC 协议框架
1)安全联盟SA(Security Association)
- 安全参数索引SPI(Security Parameter Index)
- 目的IP地址
- 使用的安全协议号(AH或ESP)
2)安全协议
- 认证头AH(Authentication Header):只支持认证,不支持加密
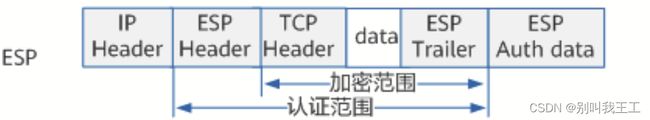
- 装安全载荷ESP(Encapsulating Security Payload)
3)封装模式
- 传输模式,传输模式如图12-1所示:
图12-1:传输模式
- 隧道模式,隧道模式如图12-2所示:
图12-2:隧道模式
4)加密和验证
加密算法:DES、3DES、AES
验证算法:MD5、SHA1、SHA2
5)密钥交换
因特网密钥交换IKE(Internet Key Exchange)协议
想要华为数通配套实验拓扑和配置笔记的朋友们点赞+关注,评论区留下邮箱发给你
二、原理
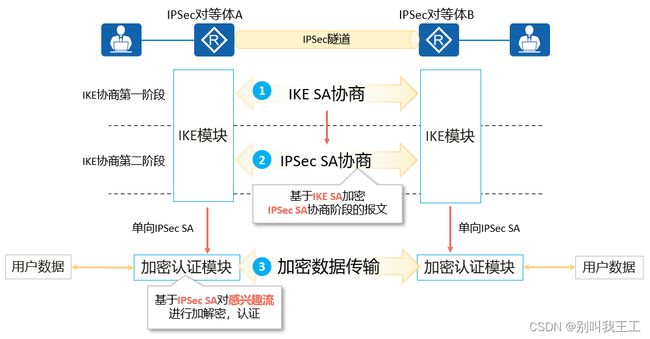
IPSec隧道建立过程中需要协商IPSec SA(Security Association,安全联盟),IPSec SA一般通过IKE协商生成。其流程图如图12-3所示:
图12-3:IPSec基本原理流程图
- SA由一个三元组来唯一标识,这个三元组包括安全参数索引SPI(Security Parameter Index)、目的IP地址和使用的安全协议号(AH或ESP)。其中,SPI是为唯一标识SA而生成的一个32位比特的数值,它在AH和ESP头中传输。在手工配置SA时,需要手工指定SPI的取值。使用IKE协商产生SA时,SPI将随机生成。
- SA是单向的逻辑连接,因此两个IPSec对等体之间的双向通信,最少需要建立两个SA来分别对两个方向的数据流进行安全保护。
IKE作为秘钥协商协议,存在两个版本:IKEv1和IKEv2,我们采用IKEv1为例进行介绍,IKEv2内容可参考产品文档对应内容。
- IKEv1协商阶段1的目的是建立IKE SA。IKE SA建立后对等体间的所有ISAKMP消息都将通过加密和验证,这条安全通道可以保证IKEv1第二阶段的协商能够安全进行。IKE SA是一个双向的逻辑连接,两个IPSec对等体间只建立一个IKE SA。
- IKEv1协商阶段2的目的就是建立用来安全传输数据的IPSec SA,并为数据传输衍生出密钥。该阶段使用IKEv1协商阶段1中生成的密钥对ISAKMP消息的完整性和身份进行验证,并对ISAKMP消息进行加密,故保证了交换的安全性。
- IKE协商成功意味着双向的IPSec隧道已经建立,可以通过ACL方式或者安全框架方式定义IPSec“感兴趣流”,符合感兴趣流流量特征的数据都将被送入IPSec隧道进行处理。
- 感兴趣流:需要被IPSec保护的数据流。
想要华为数通配套实验拓扑和配置笔记的朋友们点赞+关注,评论区留下邮箱发给你
三、实验配置
- 实验目的
1)熟悉ipsec 的应用场景
2)掌握ipsec 的配置方法
2.实验拓扑
- 实验步骤
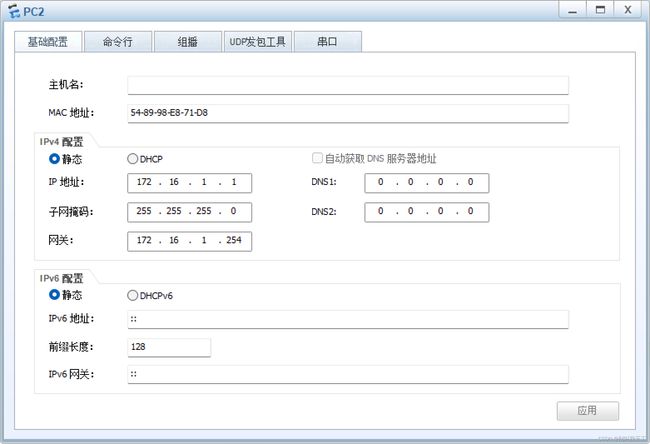
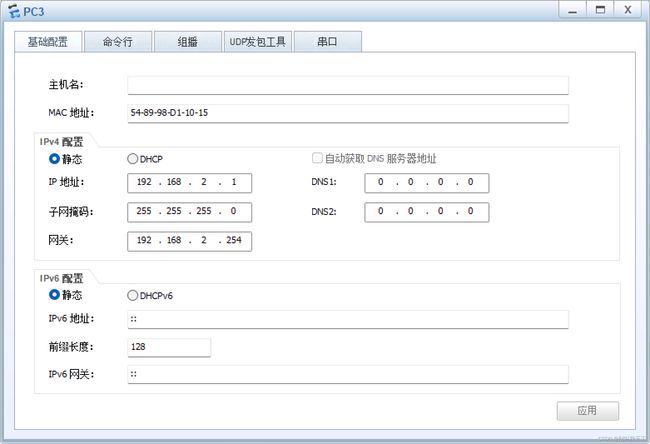
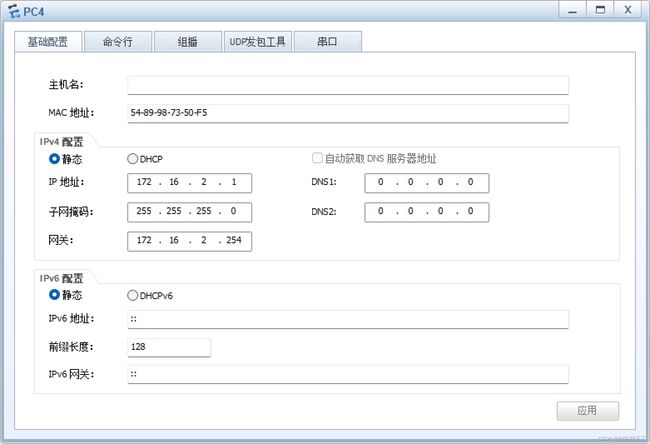
(1)如图所示配置IP地址
PC1的配置
PC2的配置
AR1的配置
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR1
[AR1]interface g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 192.168.1.254 24
[AR1-GigabitEthernet0/0/0]quit
[AR1]interface g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 172.16.1.254 24
[AR1-GigabitEthernet0/0/1]quit
[AR1]interface g0/0/2
[AR1-GigabitEthernet0/0/2]ip address 12.1.1.1 24
[AR1-GigabitEthernet0/0/2]quit
R2的配置
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR2
[AR2]interface g0/0/2
[AR2-GigabitEthernet0/0/2]ip address 12.1.1.2 24
[AR2-GigabitEthernet0/0/2]quit
[AR2]interface g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 23.1.1.2 24
[AR2-GigabitEthernet0/0/0]quit
[AR2]interface LoopBack 0
[AR2-LoopBack0]ip address 2.2.2.2 32
[AR2-LoopBack0]quit
R3的配置
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR3
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 23.1.1.3 24
[AR3-GigabitEthernet0/0/0]quit
[AR3]interface g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 192.168.2.254 24
[AR3-GigabitEthernet0/0/1]quit
[AR3]interface g0/0/2
[AR3-GigabitEthernet0/0/2]ip address 172.16.2.254 24
[AR3-GigabitEthernet0/0/2]quit
PC3的配置
PC4的配置
(2)配置网络连通性
AR1的配置
[AR1]ip route-static 0.0.0.0 0.0.0.0 12.1.1.2
AR3的配置
[AR3]ip route-static 0.0.0.0 0.0.0.0 23.1.1.2
(3)配置IPSEC VPN
第一步:定义感兴趣的流量
AR1的配置
[AR1]acl 3000
[AR1-acl-adv-3000]rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
[AR1-acl-adv-3000]quit
AR3的配置
[AR3]acl 3000
[AR3-acl-adv-3000]rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[AR3-acl-adv-3000]quit
第二步:设置提议
AR1的配置
[AR1]ipsec proposal 1
[AR1-ipsec-proposal-1]quit
AR3的配置
[AR3]ipsec proposal 1
[AR3-ipsec-proposal-1]quit
在AR1上查看提议
[AR1]display ipsec proposal //查看IPSEC VPN 提议
Number of proposals: 1 //编号为1
IPSec proposal name: 1 //名字为1
Encapsulation mode: Tunnel //封装模式为隧道
Transform : esp-new //封装为ESP
ESP protocol : Authentication MD5-HMAC-96 //认证模式为MD5
Encryption DES //加密用DES
第三步:设置安全策略
AR1的配置
[AR1]ipsec policy hcip 1 manual
[AR1-ipsec-policy-manual-hcip-1]security acl 3000
[AR1-ipsec-policy-manual-hcip-1]proposal 1
[AR1-ipsec-policy-manual-hcip-1]tunnel local 12.1.1.1
[AR1-ipsec-policy-manual-hcip-1]tunnel remote 23.1.1.3
[AR1-ipsec-policy-manual-hcip-1]sa spi outbound esp 1234
[AR1-ipsec-policy-manual-hcip-1]sa spi inbound esp 4321
[AR1-ipsec-policy-manual-hcip-1]sa string-key inbound esp simple lwljh
[AR1-ipsec-policy-manual-hcip-1]sa string-key outbound esp simple lwljh
AR3的配置
[AR3]ipsec policy hcip 1 manual
[AR3-ipsec-policy-manual-hcip-1]security acl 3000
[AR3-ipsec-policy-manual-hcip-1]proposal 1
[AR3-ipsec-policy-manual-hcip-1]tunnel local 23.1.1.3
[AR3-ipsec-policy-manual-hcip-1]tunnel remote 12.1.1.1
[AR3-ipsec-policy-manual-hcip-1]sa spi outbound esp 4321
[AR3-ipsec-policy-manual-hcip-1]sa spi inbound esp 1234
[AR3-ipsec-policy-manual-hcip-1]sa string-key inbound esp simple lwljh
[AR3-ipsec-policy-manual-hcip-1]sa string-key outbound esp simple lwljh
[AR3-ipsec-policy-manual-hcip-1]quit
查看策略
[AR1]display ipsec policy //查看IPSEC的策略
===========================================
IPSec policy group: "hcip"
Using interface:
===========================================
Sequence number: 1
Security data flow: 3000
Tunnel local address: 12.1.1.1
Tunnel remote address: 23.1.1.3
Qos pre-classify: Disable
Proposal name:1
Inbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Inbound ESP setting:
ESP SPI: 4321 (0x10e1)
ESP string-key: lwljh
ESP encryption hex key:
ESP authentication hex key:
Outbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Outbound ESP setting:
ESP SPI: 1234 (0x4d2)
ESP string-key: lwljh
ESP encryption hex key:
ESP authentication hex key:
第四步:在接口下调用
AR1的配置
[AR1]interface g0/0/2
[AR1-GigabitEthernet0/0/2]ipsec policy hcip
[AR1-GigabitEthernet0/0/2]quit
AR2的配置
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ipsec policy hcip
[AR3-GigabitEthernet0/0/0]quit
- 实验调试
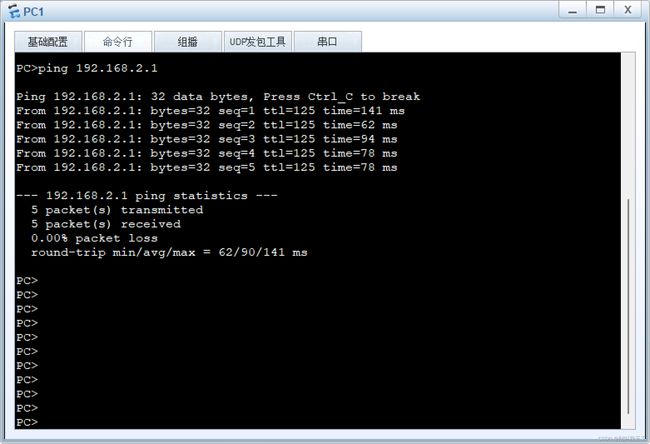
(1)在PC1访问PC3
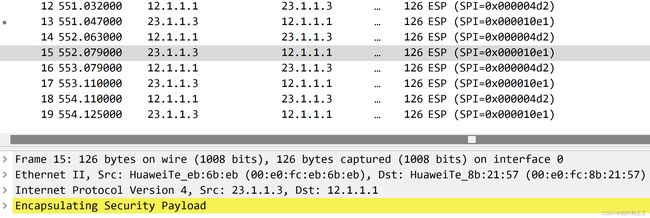
(2)在AR1的g0/0/2抓包
抓包截图如图12-10所示:
通过以上输出可以看到,数据都加密了。
想要华为数通配套实验拓扑和配置笔记的朋友们点赞+关注,评论区留下邮箱发给你