- 【微知】如何将Centos8的yum镜像更换为阿里云的镜像?(/etc/yum.repos.d/CentOS-Base.repo, yum clean all, yum makecache)
北冥的备忘录
Linux命令centosMellanox
背景Centos官方镜像使用yum安装软件经常网络不可达,比如报错:[root@localhostegypt-1.10]#yuminstallcpanCentOSStream8-AppStream0.0B/s|0B00:00Errorsduringdownloadingmetadataforrepository‘appstream’:-Curlerror(6):Couldn’tresolvehos
- tomcat 服务
狂踹瘸子那条好腿!
tomcatjava
任务描述:采用Tomcat搭建动态网站。这个先做(3)配置linux3和linux4为tomcat服务器,网站默认首页内容分别为“tomcatA”和“tomcatB”,仅使用域名访问80端口http和443端口https;证书路径均为/etc/ssl/skills.jks。[root@linux3~]#tar-zxvfapache-tomcat-10.0.2.tar.gz[root@linux3~
- Tomcat 8 安装包下载
m0_74825409
面试学习路线阿里巴巴tomcatjava
Tomcat8安装包下载【下载地址】Tomcat8安装包下载本仓库提供了一个包含Windows和Linux版本的Tomcat8安装包,方便用户快速下载并部署Tomcat8服务器[这里是图片001]项目地址:https://gitcode.com/open-source-toolkit/fda7c简介本仓库提供了一个包含Windows和Linux版本的Tomcat8安装包,方便用户快速下载并部署To
- Linux 服務器上部署 DeepSeek
蠟筆小新工程師
linux
要在Linux服務器上部署DeepSeek,可以按照以下步驟進行:1.**安裝Ollama工具**:-下載並安裝Ollama工具,這是一個開源大模型服務工具,用於簡化在本地運行大模型。-執行以下命令來安裝Ollama:```bashcurl-fsSLhttps://ollama.com/install.sh|sh```-安裝完成後,驗證安裝:```bashollama--version```2.*
- Linux中的查看命令
L耀早睡
linux运维服务器
路径分为相对路径(行相对当前工作目录开始的路径)和绝对路径(不管是)#:命令提示符,从这个位置可以开始输入命令,另一个提示符为$,如果是root,则提示为#;如果是普通用户,则提示$。~:当前用户的主目录cd..:返回上一级目录cdetc==è用鼠标双击etc这个文件(1).为当前目录(2)..为上一级目录创建文件和文件夹:touch命令:创建一个空文件。ex:toucha.txtmkdir创建一
- 实战C++手写线程池
GeniusAng丶
C/C++编程c++OOP线程池
课程总目录文章目录一、项目必备基础概念1.1并发和并行1.2多线程的优势1.3线程的消耗1.4线程池的优势1.5线程池的两种模式:fixed模式和cached模式1.6线程同步之线程互斥1.7线程同步之线程通信1.7.1条件变量1.7.2信号量1.8项目设计图浏览二、线程池代码展示三、线程池资源回收死锁问题分析四、线程资源回收策略修改优化五、Linux平台编译线程池动态库六、packaged_ta
- 小结:BGP协议
flying robot
HCIA/HCIP笔记
BGP(BorderGatewayProtocol,边界网关协议)在华为路由器上的使用BGP是互联网的核心路由协议,主要用于自治系统(AS,AutonomousSystem)之间的路由选择,即外部网关协议(EGP)。华为路由器支持BGP,可用于企业级网络、多运营商网络、跨AS路由控制等场景。1.BGP关键特性✅BGP主要特点路径向量协议(PathVectorProtocol):使用AS-PATH避
- linux开启samba共享文件夹
linux运维samba
一:安装samba#检查是否安装sambarpm-qisamba #如未安装,使用命令安装yuminstallsamba二:系统用户配置#添加系统用户useraddyouboshare#设置系统用户登陆密码passwdyouboshare#添加共享文件夹的用户(youboshare为要共享的用户)smbpasswd-ayouboshare三:配置共享文件夹1:添加共享文件夹并设置权限#创建共享文件
- Ubuntu系统下交叉编译bzip2
linux运维交叉编译
一、交叉编译bzip21.下载libpng源码下载bzip2:https://sourceware.org/bzip2/downloads.html下载并解压源码。tar-xvzfbzip2-1.0.8.tar.gzcdbzip2-1.0.82.设置环境变量设置交叉编译工具链的环境变量:exportPATH=/home/yoyo/360Downloads/toolchains/arm-linux-
- MySQL限制登陆失败次数配置
泠然一梦
mysqladb数据库linux服务器运维windows
目录一、限制登陆策略1、Windows2、Linux一、限制登陆策略1、Windows1)安装插件登录MySQL数据库mysql-uroot-p执行命令安装插件#限制登陆失败次数插件installpluginCONNECTION_CONTROLsoname'connection_control.dll';installpluginCONNECTION_CONTROL_FAILED_LOGIN_AT
- 前端进阶题(面试必看)
Caleb-niu
面试指南前端面试职场和发展
网络&安全❓输入URL地址后发生了什么事情?DNS域名解析,从URL地址中获取域名地址,通过DNS服务器解析为IP地址。先本地缓存(浏览器、操作系统)》ISP网络服务商》根服务器(根域、一级域、二级域、三级域)建立TCP连接,HTTP协议是基于TCP协议的,浏览器与服务端通过三次握手建立TCP连接(如果是HTTPS则是四次握手,多了因此SSL握手)。下载数据,向服务端发送请求报文(header+b
- tcp处理
rc_ll
网络TCP
进入包的处理(net/ipv4/tcp_input.c):接收的段都由tcp_v4_do_rcv处理,该函数根据不同的状态交由不同的函数处理。LISTEN状态且已建立半连接的处理函数为tcp_v4_hnd_req,其他状态为tcp_rcv_state_processtcp_rcv_established处理从一个建立的连接进入的tcp包,是处理tcp包的唯一入口点。Linux有两种方法处理tc
- CIDR转IP段:原理&Java实现
伏羲栈
Javatcp/ipjava网络协议
博主简介:CSDN博客专家,历代文学网(PC端可以访问:https://literature.sinhy.com/#/?__c=1000,移动端可微信小程序搜索“历代文学”)总架构师,15年工作经验,精通Java编程,高并发设计,Springboot和微服务,熟悉Linux,ESXI虚拟化以及云原生Docker和K8s,热衷于探索科技的边界,并将理论知识转化为实际应用。保持对新技术的好奇心,乐于分
- 安装Windows和Ubuntu双系统 (Legacy + MBR)
kentrl
操作系统windowslinuxubuntu系统安装mbr
首先搞清楚Legacy引导和UEFI引导的区别传统BIOS中Legacy引导的主板只能使用MBR磁盘安装操作系统;UEFI引导的主板能在GPT和MBR磁盘上安装64位操作系统。传统Legacy仅支持mbr,若使用gpt会导致找不到启动盘(Legacy引导读取不到gpt类型的分区表)名称Legacy引导UEFI引导图形界面不支持图形界面支持图形界面分区表类型只能支持MBR类型的磁盘安装系统支持GPT
- Kubernetes-v1.26.3(kubeadm)部署
wxwopt
kubelet
1.k8s基础系统环境配置1.1.环境准备CentOSLinuxrelease7.9.2009(Core)IPHOSTNAME操作系统192.168.10.131k8s-master01CentOS7.9192.168.10.132k8s-master02CentOS7.9192.168.10.133k8s-node01CentOS7.9注意:集群安装时会涉及到三个网段:宿主机网段:就是安装k8s
- 进程基本概念和通信方式
Chasing追~
操作系统websocket信息与通信
进程基本概念-进程和子进程程序是计算机指令的集合,它以文件的形式存储在磁盘上,而**进程通常被定义为一个正在运行的程序的实例,是一个程序在其自身的地址空间中的一次执行活动.**一个程序可以对应多个进程.进程是资源申请,高度和独立运行的单位,因此,它使用系统中的运行资源,而程序不能申请系统资源,不能被系统高度也不能作为独立运行的单位,因此它不占系统运行资源.进程组成:操作系统用来管理进行的内核对象内
- Kubernetes kubelet inotify
summer_west_fish
#容器云Kuberneteskuberneteskubeletjava
在Kubernetes中,kubelet是运行在每个节点上的关键组件,负责管理Pod和容器的生命周期。kubelet使用多种机制来监控和管理容器的文件系统事件,其中一种机制是利用Linux的inotify接口。1.什么是inotify?inotify是一个Linux内核子系统,用于监控文件系统事件。它允许应用程序注册对特定文件或目录的监控,并在这些文件或目录发生变化时接收通知。inotify是一种
- Linux上用C++和GCC开发程序实现两个不同PostgreSQL实例下单个数据库中多个Schema稳定高效的数据迁移到其它PostgreSQL实例
weixin_30777913
c++数据库开发语言postgresql服务器
设计一个在Linux上运行的GCCC++程序,同时连接三个不同的PostgreSQL实例,其中两个实例中分别有两个数据库中多个Schema的表结构分别与第三实例中两个数据库中多个Schema个结构完全相同,同时复制两个实例中两个数据库中多个Schema里的所有表的数据到第三个实例中两个数据库中多个Schema里,使用以下快速高效的方法,加入异常处理,支持每隔固定时间重试一定次数,每张表的复制运行状
- 控制服务和守护进程
上邪o_O
RedhatLinux知识点linux
守护进程(Daemon)是什么?列举一些常见的守护进程。守护进程(Daemon)是在Linux系统中一种长期运行在后台的进程,它通常在系统启动时被启动,并且在系统关闭前一直保持运行状态。守护进程不与特定的终端关联,因此不会受到用户登录或注销的影响,其主要目的是为系统或用户提供特定的服务。httpd:用于提供Web服务,当用户在浏览器中访问网站时,httpd守护进程负责处理HTTP请求并返回相应的网
- Android构建系统 - 03 编译执行流程
Mr.pyZhang
构建系统androidlinux
文章目录执行编译Linux内核编译make编译系统选择编译命令makem..makemmmmma...其他命令代码搜索导航指令makeclean/update-apiMakefile分类解析过程树根节点droid`/Makefile``main.mk``droid`droidcore节点.imgfilesmodules_to_install`INSTALLED_ANDROID_INFO_TXT_T
- FLASH与RAM
AARON_MJT
STM32单片机javascript嵌入式硬件
STM32内的FLASH与RAMFLASH1、什么是FLASH?FLASH的作用是什么?2、NandFlash&NorFlashRAM1、什么是RAM?RAM的作用?内存分区1、四区分配2、单片机的程序存储3、STM32有两部分内存空间4、为什么会有RAM1和RAM2?5、怎样将变量存储在CMM内存中?6、将实时操作系统的数据存放在CCM单片机的flash和RAM,相当于电脑的硬盘和内存条FLAS
- ram与flash你知道多少?
华维单片机编程
单片机ramflash内存分配与c语言变量的存储位置
一电脑程序运行过程与单片机的区别我们平常使用的电脑的程序是存储在磁盘中的,由于磁盘的读取速度很慢,所以为了避免程序阻塞,电脑在程序执行之前,会把整个代码复制到内存中,CPU从内存中读取指令,然后去运行。为了合理利用和规划内存资源,除了操作系统的内存管理外,最重要的是内存的分段。对每一个进程,操作系统都会为其分配一片内存,同时将其分段为代码段、数据段、堆栈段等等,不同的段具有不同的属性。电脑的运行模
- 《ArkTS鸿蒙应用开发入门到实战》—新手小白学习鸿蒙的推荐工具书!
心态还需努力呀
HarmonyOSharmonyos华为鸿蒙应用开发入门到实战ArkTS
《ArkTS鸿蒙应用开发入门到实战》—新手小白学习鸿蒙的推荐工具书!在科技日新月异的今天,鸿蒙操作系统(HarmonyOS)作为华为推出的全新操作系统,正迅速进入越来越多的智能设备,成为物联网和智能硬件领域的重要平台。如果你是鸿蒙开发的新手,面对众多的学习资源和技术文档,可能会感到无从下手。别担心,《ArkTS鸿蒙应用开发入门到实战》这本书,正是为你提供的一本最佳入门工具书,帮助你轻松踏入鸿蒙应用
- 多个python打包成exe_多个py文件生成一个可运行exe文件
演绎完美身材
多个python打包成exe
一、概述目前有一个python脚本,需要在别的电脑中运行,安装python环境太麻烦,封装成exe文件,运行比较方便。二、演示环境说明python版本:3.7.9操作系统:windows10安装模块pip3installerpyinstaller封装新建目录test,目录结构如下:./├──conf.py└──test.pyconf.py#!/usr/bin/python3#-*-coding:u
- BIOS和BMC的介绍
缘来是你68
硬件服务器
以BIOS为核心的固件产业,是信创产业链的重要组成部分,可被誉为信创产业的“山海关”。在计算机体系中,BIOS有着比操作系统更为底层和基础性的作用,是机器点亮后第一个被激活的系统程序,主要负责检测、访问与调试底层硬件资源,并分配给操作系统,以保障整个机器顺利安全运转。目前,全球X86授权BIOS厂商共计4家,它们分别是AMI、Phoenix、Insyde和百敖,而百敖(卓易信息旗下)又是境内唯一一
- 启用WSL后,使用ssh通道连接ubuntu
铁皮盒子
LinuxWin32sshubuntu运维wsl
EnjoyWSL目的启用wsl后,使用windows自带的powershell、cmd操作linux还是不太好使。以下介绍开启ssh通道,并保证能在ssh通道下,也能正常使用wsl中的win命令行,以及正常打开gui应用。离线更新WSL,请跳转链接:离线更新WSL打开ssh通道删除ubuntu自带的openssh,在wsl环境下,无法正常启动sudoaptremoveopenssh-servers
- Linux:简单理解文件系统内附Linux内核设计与实现PDF下载地址
℃绝心恋
Linuxlinux
简单理解文件系统文件系统ext2文件系统文件的存储文件的获取文件系统文件存储的方式有线性存储和离散存储两种,线性存储可能会导致磁盘的利用率降低,产生磁盘碎片,离散存储方式会提高程序对磁盘的利用率,以下是Linux内核简设计与实现中关于文系统的一段话的一部分:文件通过目录组织起来。文件目录好比一个文件目录好比一个文件夹,用来容纳相关文件。因为目录也可以包含其他目录,及子目录,所以目录可以层层嵌套,形
- PHP到底是如何和服务器各个硬件进行交互的?使用场景是什么?底层原理是什么?
快点好好学习吧
PHPphp
PHP是一种服务器端脚本语言,主要用于Web开发。它通过与服务器硬件和操作系统交互来完成各种任务。1.PHP如何与服务器硬件进行交互?(1)通过操作系统PHP本身并不直接与硬件交互,而是通过操作系统的接口(如系统调用、API)间接访问硬件资源。操作系统负责管理硬件资源(如CPU、内存、硬盘、网络设备),PHP通过调用操作系统的功能来使用这些资源。(2)通过扩展模块PHP提供了大量的扩展模块(如My
- 深度对比Linux软链接和Windows快捷方式
秋の水
linuxwindows
以下从8个维度对Linux软链接和Windows快捷方式进行深度对比:一、核心特性对比特性Linux软链接Windows快捷方式文件类型特殊文件类型(symboliclink).lnk扩展名文件存储内容纯文本路径二进制结构(含GUID等元数据)文件大小路径长度决定(约100B)固定约1KB系统识别内核级支持Shell解析二、路径解析机制Linux软链接:采用相对路径时基于链接文件所在目录解析示例:
- CentOS vs Ubuntu - 常用命令深度对比及最佳实践指南20250302
Narutolxy
技术干货分享centosubuntulinux
CentOSvsUbuntu-常用命令深度对比及最佳实践指南引言在Linux服务器操作系统领域,CentOS和Ubuntu是广泛采用的发行版。它们在命令集、默认工具链及生态系统方面各有特点。本文深入剖析CentOS与Ubuntu在常用命令层面的异同,并结合实践案例,帮助读者理解两者的特性,从而根据业务需求做出精准选型。1.环境配置管理1.1用户账户管理创建用户CentOSuseraddpyapp#
- web报表工具FineReport常见的数据集报错错误代码和解释
老A不折腾
web报表finereport代码可视化工具
在使用finereport制作报表,若预览发生错误,很多朋友便手忙脚乱不知所措了,其实没什么,只要看懂报错代码和含义,可以很快的排除错误,这里我就分享一下finereport的数据集报错错误代码和解释,如果有说的不准确的地方,也请各位小伙伴纠正一下。
NS-war-remote=错误代码\:1117 压缩部署不支持远程设计
NS_LayerReport_MultiDs=错误代码
- Java的WeakReference与WeakHashMap
bylijinnan
java弱引用
首先看看 WeakReference
wiki 上 Weak reference 的一个例子:
public class ReferenceTest {
public static void main(String[] args) throws InterruptedException {
WeakReference r = new Wea
- Linux——(hostname)主机名与ip的映射
eksliang
linuxhostname
一、 什么是主机名
无论在局域网还是INTERNET上,每台主机都有一个IP地址,是为了区分此台主机和彼台主机,也就是说IP地址就是主机的门牌号。但IP地址不方便记忆,所以又有了域名。域名只是在公网(INtERNET)中存在,每个域名都对应一个IP地址,但一个IP地址可有对应多个域名。域名类型 linuxsir.org 这样的;
主机名是用于什么的呢?
答:在一个局域网中,每台机器都有一个主
- oracle 常用技巧
18289753290
oracle常用技巧 ①复制表结构和数据 create table temp_clientloginUser as select distinct userid from tbusrtloginlog ②仅复制数据 如果表结构一样 insert into mytable select * &nb
- 使用c3p0数据库连接池时出现com.mchange.v2.resourcepool.TimeoutException
酷的飞上天空
exception
有一个线上环境使用的是c3p0数据库,为外部提供接口服务。最近访问压力增大后台tomcat的日志里面频繁出现
com.mchange.v2.resourcepool.TimeoutException: A client timed out while waiting to acquire a resource from com.mchange.v2.resourcepool.BasicResou
- IT系统分析师如何学习大数据
蓝儿唯美
大数据
我是一名从事大数据项目的IT系统分析师。在深入这个项目前需要了解些什么呢?学习大数据的最佳方法就是先从了解信息系统是如何工作着手,尤其是数据库和基础设施。同样在开始前还需要了解大数据工具,如Cloudera、Hadoop、Spark、Hive、Pig、Flume、Sqoop与Mesos。系 统分析师需要明白如何组织、管理和保护数据。在市面上有几十款数据管理产品可以用于管理数据。你的大数据数据库可能
- spring学习——简介
a-john
spring
Spring是一个开源框架,是为了解决企业应用开发的复杂性而创建的。Spring使用基本的JavaBean来完成以前只能由EJB完成的事情。然而Spring的用途不仅限于服务器端的开发,从简单性,可测试性和松耦合的角度而言,任何Java应用都可以从Spring中受益。其主要特征是依赖注入、AOP、持久化、事务、SpringMVC以及Acegi Security
为了降低Java开发的复杂性,
- 自定义颜色的xml文件
aijuans
xml
<?xml version="1.0" encoding="utf-8"?> <resources> <color name="white">#FFFFFF</color> <color name="black">#000000</color> &
- 运营到底是做什么的?
aoyouzi
运营到底是做什么的?
文章来源:夏叔叔(微信号:woshixiashushu),欢迎大家关注!很久没有动笔写点东西,近些日子,由于爱狗团产品上线,不断面试,经常会被问道一个问题。问:爱狗团的运营主要做什么?答:带着用户一起嗨。为什么是带着用户玩起来呢?究竟什么是运营?运营到底是做什么的?那么,我们先来回答一个更简单的问题——互联网公司对运营考核什么?以爱狗团为例,绝大部分的移动互联网公司,对运营部门的考核分为三块——用
- js面向对象类和对象
百合不是茶
js面向对象函数创建类和对象
接触js已经有几个月了,但是对js的面向对象的一些概念根本就是模糊的,js是一种面向对象的语言 但又不像java一样有class,js不是严格的面向对象语言 ,js在java web开发的地位和java不相上下 ,其中web的数据的反馈现在主流的使用json,json的语法和js的类和属性的创建相似
下面介绍一些js的类和对象的创建的技术
一:类和对
- web.xml之资源管理对象配置 resource-env-ref
bijian1013
javaweb.xmlservlet
resource-env-ref元素来指定对管理对象的servlet引用的声明,该对象与servlet环境中的资源相关联
<resource-env-ref>
<resource-env-ref-name>资源名</resource-env-ref-name>
<resource-env-ref-type>查找资源时返回的资源类
- Create a composite component with a custom namespace
sunjing
https://weblogs.java.net/blog/mriem/archive/2013/11/22/jsf-tip-45-create-composite-component-custom-namespace
When you developed a composite component the namespace you would be seeing would
- 【MongoDB学习笔记十二】Mongo副本集服务器角色之Arbiter
bit1129
mongodb
一、复本集为什么要加入Arbiter这个角色 回答这个问题,要从复本集的存活条件和Aribter服务器的特性两方面来说。 什么是Artiber? An arbiter does
not have a copy of data set and
cannot become a primary. Replica sets may have arbiters to add a
- Javascript开发笔记
白糖_
JavaScript
获取iframe内的元素
通常我们使用window.frames["frameId"].document.getElementById("divId").innerHTML这样的形式来获取iframe内的元素,这种写法在IE、safari、chrome下都是通过的,唯独在fireforx下不通过。其实jquery的contents方法提供了对if
- Web浏览器Chrome打开一段时间后,运行alert无效
bozch
Webchormealert无效
今天在开发的时候,突然间发现alert在chrome浏览器就没法弹出了,很是怪异。
试了试其他浏览器,发现都是没有问题的。
开始想以为是chorme浏览器有啥机制导致的,就开始尝试各种代码让alert出来。尝试结果是仍然没有显示出来。
这样开发的结果,如果客户在使用的时候没有提示,那会带来致命的体验。哎,没啥办法了 就关闭浏览器重启。
结果就好了,这也太怪异了。难道是cho
- 编程之美-高效地安排会议 图着色问题 贪心算法
bylijinnan
编程之美
import java.util.ArrayList;
import java.util.Collections;
import java.util.List;
import java.util.Random;
public class GraphColoringProblem {
/**编程之美 高效地安排会议 图着色问题 贪心算法
* 假设要用很多个教室对一组
- 机器学习相关概念和开发工具
chenbowen00
算法matlab机器学习
基本概念:
机器学习(Machine Learning, ML)是一门多领域交叉学科,涉及概率论、统计学、逼近论、凸分析、算法复杂度理论等多门学科。专门研究计算机怎样模拟或实现人类的学习行为,以获取新的知识或技能,重新组织已有的知识结构使之不断改善自身的性能。
它是人工智能的核心,是使计算机具有智能的根本途径,其应用遍及人工智能的各个领域,它主要使用归纳、综合而不是演绎。
开发工具
M
- [宇宙经济学]关于在太空建立永久定居点的可能性
comsci
经济
大家都知道,地球上的房地产都比较昂贵,而且土地证经常会因为新的政府的意志而变幻文本格式........
所以,在地球议会尚不具有在太空行使法律和权力的力量之前,我们外太阳系统的友好联盟可以考虑在地月系的某些引力平衡点上面,修建规模较大的定居点
- oracle 11g database control 证书错误
daizj
oracle证书错误oracle 11G 安装
oracle 11g database control 证书错误
win7 安装完oracle11后打开 Database control 后,会打开em管理页面,提示证书错误,点“继续浏览此网站”,还是会继续停留在证书错误页面
解决办法:
是 KB2661254 这个更新补丁引起的,它限制了 RSA 密钥位长度少于 1024 位的证书的使用。具体可以看微软官方公告:
- Java I/O之用FilenameFilter实现根据文件扩展名删除文件
游其是你
FilenameFilter
在Java中,你可以通过实现FilenameFilter类并重写accept(File dir, String name) 方法实现文件过滤功能。
在这个例子中,我们向你展示在“c:\\folder”路径下列出所有“.txt”格式的文件并删除。 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
- C语言数组的简单以及一维数组的简单排序算法示例,二维数组简单示例
dcj3sjt126com
carray
# include <stdio.h>
int main(void)
{
int a[5] = {1, 2, 3, 4, 5};
//a 是数组的名字 5是表示数组元素的个数,并且这五个元素分别用a[0], a[1]...a[4]
int i;
for (i=0; i<5; ++i)
printf("%d\n",
- PRIMARY, INDEX, UNIQUE 这3种是一类 PRIMARY 主键。 就是 唯一 且 不能为空。 INDEX 索引,普通的 UNIQUE 唯一索引
dcj3sjt126com
primary
PRIMARY, INDEX, UNIQUE 这3种是一类PRIMARY 主键。 就是 唯一 且 不能为空。INDEX 索引,普通的UNIQUE 唯一索引。 不允许有重复。FULLTEXT 是全文索引,用于在一篇文章中,检索文本信息的。举个例子来说,比如你在为某商场做一个会员卡的系统。这个系统有一个会员表有下列字段:会员编号 INT会员姓名
- java集合辅助类 Collections、Arrays
shuizhaosi888
CollectionsArraysHashCode
Arrays、Collections
1 )数组集合之间转换
public static <T> List<T> asList(T... a) {
return new ArrayList<>(a);
}
a)Arrays.asL
- Spring Security(10)——退出登录logout
234390216
logoutSpring Security退出登录logout-urlLogoutFilter
要实现退出登录的功能我们需要在http元素下定义logout元素,这样Spring Security将自动为我们添加用于处理退出登录的过滤器LogoutFilter到FilterChain。当我们指定了http元素的auto-config属性为true时logout定义是会自动配置的,此时我们默认退出登录的URL为“/j_spring_secu
- 透过源码学前端 之 Backbone 三 Model
逐行分析JS源代码
backbone源码分析js学习
Backbone 分析第三部分 Model
概述: Model 提供了数据存储,将数据以JSON的形式保存在 Model的 attributes里,
但重点功能在于其提供了一套功能强大,使用简单的存、取、删、改数据方法,并在不同的操作里加了相应的监听事件,
如每次修改添加里都会触发 change,这在据模型变动来修改视图时很常用,并且与collection建立了关联。
- SpringMVC源码总结(七)mvc:annotation-driven中的HttpMessageConverter
乒乓狂魔
springMVC
这一篇文章主要介绍下HttpMessageConverter整个注册过程包含自定义的HttpMessageConverter,然后对一些HttpMessageConverter进行具体介绍。
HttpMessageConverter接口介绍:
public interface HttpMessageConverter<T> {
/**
* Indicate
- 分布式基础知识和算法理论
bluky999
算法zookeeper分布式一致性哈希paxos
分布式基础知识和算法理论
BY NODEXY@2014.8.12
本文永久链接:http://nodex.iteye.com/blog/2103218
在大数据的背景下,不管是做存储,做搜索,做数据分析,或者做产品或服务本身,面向互联网和移动互联网用户,已经不可避免地要面对分布式环境。笔者在此收录一些分布式相关的基础知识和算法理论介绍,在完善自我知识体系的同
- Android Studio的.gitignore以及gitignore无效的解决
bell0901
androidgitignore
github上.gitignore模板合集,里面有各种.gitignore : https://github.com/github/gitignore
自己用的Android Studio下项目的.gitignore文件,对github上的android.gitignore添加了
# OSX files //mac os下 .DS_Store
- 成为高级程序员的10个步骤
tomcat_oracle
编程
What
软件工程师的职业生涯要历经以下几个阶段:初级、中级,最后才是高级。这篇文章主要是讲如何通过 10 个步骤助你成为一名高级软件工程师。
Why
得到更多的报酬!因为你的薪水会随着你水平的提高而增加
提升你的职业生涯。成为了高级软件工程师之后,就可以朝着架构师、团队负责人、CTO 等职位前进
历经更大的挑战。随着你的成长,各种影响力也会提高。
- mongdb在linux下的安装
xtuhcy
mongodblinux
一、查询linux版本号:
lsb_release -a
LSB Version: :base-4.0-amd64:base-4.0-noarch:core-4.0-amd64:core-4.0-noarch:graphics-4.0-amd64:graphics-4.0-noarch:printing-4.0-amd64:printing-4.0-noa
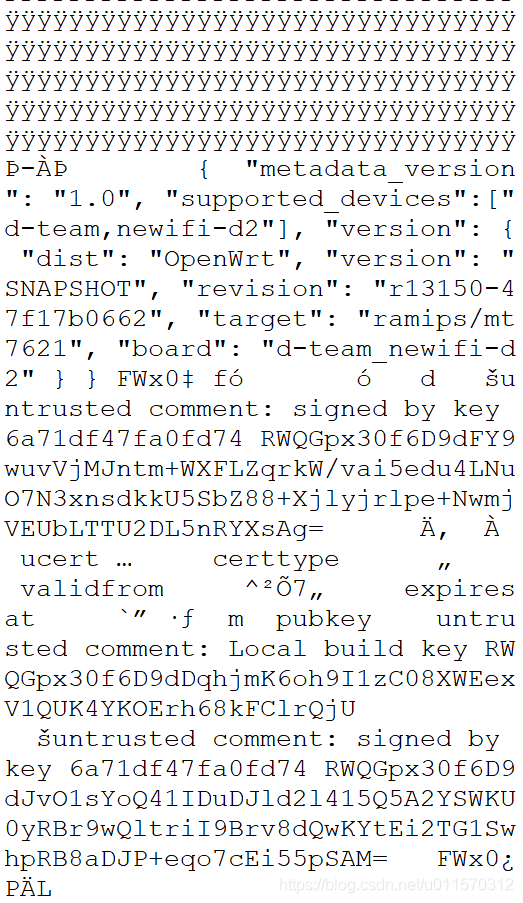 官方固件结尾
官方固件结尾
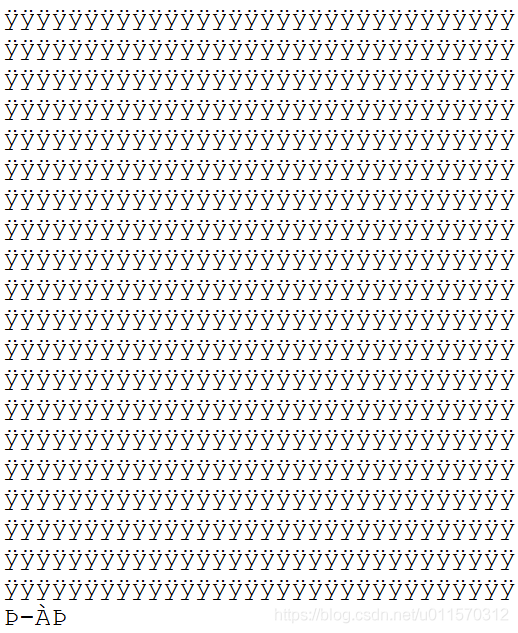 修改后结尾丢失
修改后结尾丢失