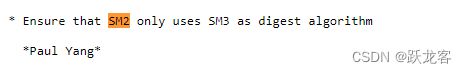openssl3.1.1国密支持的验证笔记
openssl3.1.1国密支持的验证笔记
openssl的版本差异日志
openssl虽然有3个大分支,我们就以3.1大分支查看关于国密的差异日志。
Changes between 1.1.0i and 1.1.1 [11 Sep 2018]
Changes between 1.1.1b and 1.1.1c [28 May 2019]
Changes between 1.1.1k and 1.1.1l [24 Aug 2021]
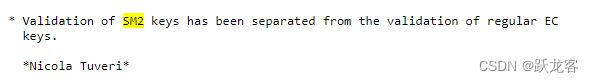
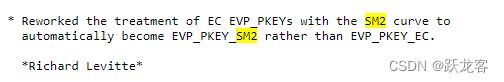
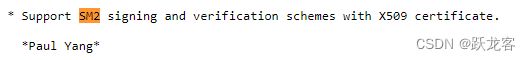
Changes between 1.1.1 and 3.0.0 [7 sep 2021]
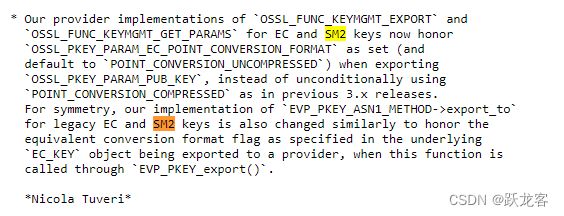
Changes between 3.0.7 and 3.0.8 [7 Feb 2023]
差异日志分析
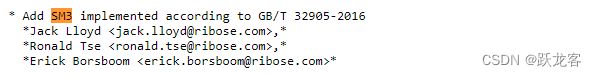
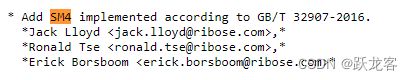
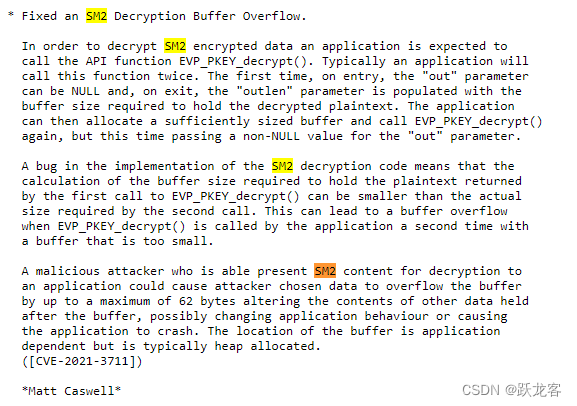
openssl在1.1.1版本已经添加了国密算法的支持,
openssl在3.0.0版本已经支持了国标签名和验签的支持
最有一次相关修改在3.0.8版本。
所以测试环境需要3.0.8以及更高版本。本人习惯使用最新版本,目前的最新版本为3.1.1版本,开始测试一波。
openssl编译(openssl-3.1.1)
编译流程
直接上终端日志
第一次想当然了,没有看官方说明,搞砸了,
错误示范:
: 1690424002:0;tar -zxvf openssl-3.1.1.tar.gz
: 1690424010:0;cd openssl-3.1.1
: 1690424039:0;./Configure
: 1690424067:0;make -j4
: 1690424109:0;chmod a+x util/shlib_wrap.sh
: 1690424114:0;chmod a+x util/wrap.pl
: 1690424116:0;make -j4
: 1690424156:0;make -j1
: 1690435099:0;cd ..
: 1690435105:0;rm -r openssl-3.1.1
正确示范:
: 1690435110:0;tar -zxvf openssl-3.1.1.tar.gz
: 1690435115:0;cd openssl-3.1.1
: 1690435138:0;./config --prefix=/opt/openssl-3.1.1
: 1690435176:0;make
: 1690436282:0;make install
: 1690438167:0;cd /opt/openssl-3.1.1/bin
由于没有安装到系统路径上,配一下动态库搜索路径,才能执行
# root @ ubuntu in /opt/openssl-3.1.1/bin [6:37:47]
$ find .. -name "*.so"
../lib64/engines-3/loader_attic.so
../lib64/engines-3/capi.so
../lib64/engines-3/padlock.so
../lib64/engines-3/afalg.so
../lib64/libssl.so
../lib64/ossl-modules/legacy.so
../lib64/libcrypto.so
# root @ ubuntu in /opt/openssl-3.1.1/bin [6:38:04]
$ export LD_LIBRARY_PATH=/opt/openssl-3.1.1/lib64:$LD_LIBRARY_PATH
# root @ ubuntu in /opt/openssl-3.1.1/bin [6:38:14]
$ ./openssl version
OpenSSL 3.1.1 30 May 2023 (Library: OpenSSL 3.1.1 30 May 2023)
国密支持测试
非对称算法支持(结论:支持SM2)
# root @ ubuntu in ~/SMx_test [7:39:52]
$ /opt/openssl-3.1.1/bin/openssl list -public-key-algorithms
Legacy:
Name: OpenSSL RSA method
Type: Builtin Algorithm
OID: rsaEncryption
PEM string: RSA
Name: rsa
Alias for: rsaEncryption
Name: OpenSSL PKCS#3 DH method
Type: Builtin Algorithm
OID: dhKeyAgreement
PEM string: DH
Name: dsaWithSHA
Alias for: dsaEncryption
Name: dsaEncryption-old
Alias for: dsaEncryption
Name: dsaWithSHA1-old
Alias for: dsaEncryption
Name: dsaWithSHA1
Alias for: dsaEncryption
Name: OpenSSL DSA method
Type: Builtin Algorithm
OID: dsaEncryption
PEM string: DSA
Name: OpenSSL EC algorithm
Type: Builtin Algorithm
OID: id-ecPublicKey
PEM string: EC
Name: OpenSSL RSA-PSS method
Type: Builtin Algorithm
OID: rsassaPss
PEM string: RSA-PSS
Name: OpenSSL X9.42 DH method
Type: Builtin Algorithm
OID: X9.42 DH
PEM string: X9.42 DH
Name: OpenSSL X25519 algorithm
Type: Builtin Algorithm
OID: X25519
PEM string: X25519
Name: OpenSSL X448 algorithm
Type: Builtin Algorithm
OID: X448
PEM string: X448
Name: OpenSSL ED25519 algorithm
Type: Builtin Algorithm
OID: ED25519
PEM string: ED25519
Name: OpenSSL ED448 algorithm
Type: Builtin Algorithm
OID: ED448
PEM string: ED448
Name: sm2
Alias for: id-ecPublicKey
Provided:
Key Managers:
Name: OpenSSL RSA implementation
Type: Provider Algorithm
IDs: { 1.2.840.113549.1.1.1, 2.5.8.1.1, RSA, rsaEncryption } @ default
Name: OpenSSL PKCS#3 DH implementation
Type: Provider Algorithm
IDs: { 1.2.840.113549.1.3.1, DH, dhKeyAgreement } @ default
Name: OpenSSL DSA implementation
Type: Provider Algorithm
IDs: { 1.2.840.10040.4.1, 1.2.840.10040.4.3, 1.3.14.3.2.12, 1.3.14.3.2.13, 1.3.14.3.2.27, DSA, DSA-old, DSA-SHA, DSA-SHA1, DSA-SHA1-old, dsaEncryption, dsaEncryption-old, dsaWithSHA, dsaWithSHA1, dsaWithSHA1-old } @ default
Name: OpenSSL EC implementation
Type: Provider Algorithm
IDs: { 1.2.840.10045.2.1, EC, id-ecPublicKey } @ default
Name: OpenSSL RSA-PSS implementation
Type: Provider Algorithm
IDs: { 1.2.840.113549.1.1.10, RSA-PSS, RSASSA-PSS, rsassaPss } @ default
Name: OpenSSL X9.42 DH implementation
Type: Provider Algorithm
IDs: { 1.2.840.10046.2.1, dhpublicnumber, DHX, X9.42 DH } @ default
Name: OpenSSL X25519 implementation
Type: Provider Algorithm
IDs: { 1.3.101.110, X25519 } @ default
Name: OpenSSL X448 implementation
Type: Provider Algorithm
IDs: { 1.3.101.111, X448 } @ default
Name: OpenSSL ED25519 implementation
Type: Provider Algorithm
IDs: { 1.3.101.112, ED25519 } @ default
Name: OpenSSL ED448 implementation
Type: Provider Algorithm
IDs: { 1.3.101.113, ED448 } @ default
Name: OpenSSL SM2 implementation
Type: Provider Algorithm
IDs: { 1.2.156.10197.1.301, SM2 } @ default
Name: OpenSSL TLS1_PRF via EVP_PKEY implementation
Type: Provider Algorithm
IDs: TLS1-PRF @ default
Name: OpenSSL HKDF via EVP_PKEY implementation
Type: Provider Algorithm
IDs: HKDF @ default
Name: OpenSSL SCRYPT via EVP_PKEY implementation
Type: Provider Algorithm
IDs: { 1.3.6.1.4.1.11591.4.11, id-scrypt, SCRYPT } @ default
Name: OpenSSL HMAC via EVP_PKEY implementation
Type: Provider Algorithm
IDs: HMAC @ default
Name: OpenSSL SIPHASH via EVP_PKEY implementation
Type: Provider Algorithm
IDs: SIPHASH @ default
Name: OpenSSL POLY1305 via EVP_PKEY implementation
Type: Provider Algorithm
IDs: POLY1305 @ default
Name: OpenSSL CMAC via EVP_PKEY implementation
Type: Provider Algorithm
IDs: CMAC @ default
# root @ ubuntu in ~/SMx_test [7:46:34]
$ /opt/openssl-3.1.1/bin/openssl list -public-key-methods
Legacy:
rsaEncryption
Type: External Algorithm
dhKeyAgreement
Type: Builtin Algorithm
dsaEncryption
Type: External Algorithm
id-ecPublicKey
Type: Builtin Algorithm
rsassaPss
Type: External Algorithm
X9.42 DH
Type: Builtin Algorithm
X25519
Type: Builtin Algorithm
X448
Type: Builtin Algorithm
ED25519
Type: Builtin Algorithm
ED448
Type: Builtin Algorithm
Provided:
Encryption:
{ 1.2.840.113549.1.1.1, 2.5.8.1.1, RSA, rsaEncryption } @ default
{ 1.2.156.10197.1.301, SM2 } @ default
Key Exchange:
{ 1.2.840.113549.1.3.1, DH, dhKeyAgreement } @ default
{ 1.3.101.110, X25519 } @ default
{ 1.3.101.111, X448 } @ default
ECDH @ default
TLS1-PRF @ default
HKDF @ default
{ 1.3.6.1.4.1.11591.4.11, id-scrypt, SCRYPT } @ default
Signatures:
{ 1.2.840.113549.1.1.1, 2.5.8.1.1, RSA, rsaEncryption } @ default
{ 1.2.840.10040.4.1, 1.2.840.10040.4.3, 1.3.14.3.2.12, 1.3.14.3.2.13, 1.3.14.3.2.27, DSA, DSA-old, DSA-SHA, DSA-SHA1, DSA-SHA1-old, dsaEncryption, dsaEncryption-old, dsaWithSHA, dsaWithSHA1, dsaWithSHA1-old } @ default
{ 1.3.101.112, ED25519 } @ default
{ 1.3.101.113, ED448 } @ default
{ 1.2.156.10197.1.301, SM2 } @ default
ECDSA @ default
HMAC @ default
SIPHASH @ default
POLY1305 @ default
CMAC @ default
Key encapsulation:
{ 1.2.840.113549.1.1.1, 2.5.8.1.1, RSA, rsaEncryption } @ default
摘要算法,哈希算法,杂凑算法(结论:支持SM3)
# root @ ubuntu in ~/SMx_test [7:52:15]
$ /opt/openssl-3.1.1/bin/openssl list -digest-algorithms
Legacy:
RSA-MD4 => MD4
RSA-MD5 => MD5
RSA-MDC2 => MDC2
RSA-RIPEMD160 => RIPEMD160
RSA-SHA1 => SHA1
RSA-SHA1-2 => RSA-SHA1
RSA-SHA224 => SHA224
RSA-SHA256 => SHA256
RSA-SHA3-224 => SHA3-224
RSA-SHA3-256 => SHA3-256
RSA-SHA3-384 => SHA3-384
RSA-SHA3-512 => SHA3-512
RSA-SHA384 => SHA384
RSA-SHA512 => SHA512
RSA-SHA512/224 => SHA512-224
RSA-SHA512/256 => SHA512-256
RSA-SM3 => SM3
BLAKE2b512
BLAKE2s256
id-rsassa-pkcs1-v1_5-with-sha3-224 => SHA3-224
id-rsassa-pkcs1-v1_5-with-sha3-256 => SHA3-256
id-rsassa-pkcs1-v1_5-with-sha3-384 => SHA3-384
id-rsassa-pkcs1-v1_5-with-sha3-512 => SHA3-512
MD4
md4WithRSAEncryption => MD4
MD5
MD5-SHA1
md5WithRSAEncryption => MD5
MDC2
mdc2WithRSA => MDC2
ripemd => RIPEMD160
RIPEMD160
ripemd160WithRSA => RIPEMD160
rmd160 => RIPEMD160
SHA1
sha1WithRSAEncryption => SHA1
SHA224
sha224WithRSAEncryption => SHA224
SHA256
sha256WithRSAEncryption => SHA256
SHA3-224
SHA3-256
SHA3-384
SHA3-512
SHA384
sha384WithRSAEncryption => SHA384
SHA512
SHA512-224
sha512-224WithRSAEncryption => SHA512-224
SHA512-256
sha512-256WithRSAEncryption => SHA512-256
sha512WithRSAEncryption => SHA512
SHAKE128
SHAKE256
SM3
sm3WithRSAEncryption => SM3
ssl3-md5 => MD5
ssl3-sha1 => SHA1
whirlpool
Provided:
{ 2.16.840.1.101.3.4.2.10, SHA3-512 } @ default
{ 2.16.840.1.101.3.4.2.6, SHA-512/256, SHA2-512/256, SHA512-256 } @ default
{ 2.16.840.1.101.3.4.2.4, SHA-224, SHA2-224, SHA224 } @ default
{ 1.3.14.3.2.26, SHA-1, SHA1, SSL3-SHA1 } @ default
{ 2.16.840.1.101.3.4.2.7, SHA3-224 } @ default
{ 2.16.840.1.101.3.4.2.9, SHA3-384 } @ default
{ 1.3.36.3.2.1, RIPEMD, RIPEMD-160, RIPEMD160, RMD160 } @ default
{ 2.16.840.1.101.3.4.2.3, SHA-512, SHA2-512, SHA512 } @ default
{ 2.16.840.1.101.3.4.2.5, SHA-512/224, SHA2-512/224, SHA512-224 } @ default
{ 2.16.840.1.101.3.4.2.12, SHAKE-256, SHAKE256 } @ default
{ 2.16.840.1.101.3.4.2.2, SHA-384, SHA2-384, SHA384 } @ default
{ 1.2.156.10197.1.401, SM3 } @ default
{ 2.16.840.1.101.3.4.2.8, SHA3-256 } @ default
{ 1.2.840.113549.2.5, MD5, SSL3-MD5 } @ default
{ 1.3.6.1.4.1.1722.12.2.2.8, BLAKE2S-256, BLAKE2s256 } @ default
{ 2.16.840.1.101.3.4.2.1, SHA-256, SHA2-256, SHA256 } @ default
{ 1.3.6.1.4.1.1722.12.2.1.16, BLAKE2B-512, BLAKE2b512 } @ default
MD5-SHA1 @ default
{ 2.16.840.1.101.3.4.2.11, SHAKE-128, SHAKE128 } @ default
{ KECCAK-KMAC-128, KECCAK-KMAC128 } @ default
{ KECCAK-KMAC-256, KECCAK-KMAC256 } @ default
NULL @ default
对称算法支持(结论:支持SM4)
# root @ ubuntu in ~/SMx_test [7:55:07] C:130
$ /opt/openssl-3.1.1/bin/openssl list -cipher-algorithms
Legacy:
AES-128-CBC
AES-128-CBC-HMAC-SHA1
AES-128-CBC-HMAC-SHA256
id-aes128-CCM
AES-128-CFB
AES-128-CFB1
AES-128-CFB8
AES-128-CTR
AES-128-ECB
id-aes128-GCM
AES-128-OCB
AES-128-OFB
AES-128-XTS
AES-192-CBC
id-aes192-CCM
AES-192-CFB
AES-192-CFB1
AES-192-CFB8
AES-192-CTR
AES-192-ECB
id-aes192-GCM
AES-192-OCB
AES-192-OFB
AES-256-CBC
AES-256-CBC-HMAC-SHA1
AES-256-CBC-HMAC-SHA256
id-aes256-CCM
AES-256-CFB
AES-256-CFB1
AES-256-CFB8
AES-256-CTR
AES-256-ECB
id-aes256-GCM
AES-256-OCB
AES-256-OFB
AES-256-XTS
aes128 => AES-128-CBC
aes128-wrap => id-aes128-wrap
aes192 => AES-192-CBC
aes192-wrap => id-aes192-wrap
aes256 => AES-256-CBC
aes256-wrap => id-aes256-wrap
ARIA-128-CBC
ARIA-128-CCM
ARIA-128-CFB
ARIA-128-CFB1
ARIA-128-CFB8
ARIA-128-CTR
ARIA-128-ECB
ARIA-128-GCM
ARIA-128-OFB
ARIA-192-CBC
ARIA-192-CCM
ARIA-192-CFB
ARIA-192-CFB1
ARIA-192-CFB8
ARIA-192-CTR
ARIA-192-ECB
ARIA-192-GCM
ARIA-192-OFB
ARIA-256-CBC
ARIA-256-CCM
ARIA-256-CFB
ARIA-256-CFB1
ARIA-256-CFB8
ARIA-256-CTR
ARIA-256-ECB
ARIA-256-GCM
ARIA-256-OFB
aria128 => ARIA-128-CBC
aria192 => ARIA-192-CBC
aria256 => ARIA-256-CBC
bf => BF-CBC
BF-CBC
BF-CFB
BF-ECB
BF-OFB
blowfish => BF-CBC
CAMELLIA-128-CBC
CAMELLIA-128-CFB
CAMELLIA-128-CFB1
CAMELLIA-128-CFB8
CAMELLIA-128-CTR
CAMELLIA-128-ECB
CAMELLIA-128-OFB
CAMELLIA-192-CBC
CAMELLIA-192-CFB
CAMELLIA-192-CFB1
CAMELLIA-192-CFB8
CAMELLIA-192-CTR
CAMELLIA-192-ECB
CAMELLIA-192-OFB
CAMELLIA-256-CBC
CAMELLIA-256-CFB
CAMELLIA-256-CFB1
CAMELLIA-256-CFB8
CAMELLIA-256-CTR
CAMELLIA-256-ECB
CAMELLIA-256-OFB
camellia128 => CAMELLIA-128-CBC
camellia192 => CAMELLIA-192-CBC
camellia256 => CAMELLIA-256-CBC
cast => CAST5-CBC
cast-cbc => CAST5-CBC
CAST5-CBC
CAST5-CFB
CAST5-ECB
CAST5-OFB
ChaCha20
ChaCha20-Poly1305
des => DES-CBC
DES-CBC
DES-CFB
DES-CFB1
DES-CFB8
DES-ECB
DES-EDE
DES-EDE-CBC
DES-EDE-CFB
des-ede-ecb => DES-EDE
DES-EDE-OFB
DES-EDE3
DES-EDE3-CBC
DES-EDE3-CFB
DES-EDE3-CFB1
DES-EDE3-CFB8
des-ede3-ecb => DES-EDE3
DES-EDE3-OFB
DES-OFB
des3 => DES-EDE3-CBC
des3-wrap => id-smime-alg-CMS3DESwrap
desx => DESX-CBC
DESX-CBC
id-aes128-CCM
id-aes128-GCM
id-aes128-wrap
id-aes128-wrap-pad
id-aes192-CCM
id-aes192-GCM
id-aes192-wrap
id-aes192-wrap-pad
id-aes256-CCM
id-aes256-GCM
id-aes256-wrap
id-aes256-wrap-pad
id-smime-alg-CMS3DESwrap
idea => IDEA-CBC
IDEA-CBC
IDEA-CFB
IDEA-ECB
IDEA-OFB
rc2 => RC2-CBC
rc2-128 => RC2-CBC
rc2-40 => RC2-40-CBC
RC2-40-CBC
rc2-64 => RC2-64-CBC
RC2-64-CBC
RC2-CBC
RC2-CFB
RC2-ECB
RC2-OFB
RC4
RC4-40
RC4-HMAC-MD5
seed => SEED-CBC
SEED-CBC
SEED-CFB
SEED-ECB
SEED-OFB
sm4 => SM4-CBC
SM4-CBC
SM4-CFB
SM4-CTR
SM4-ECB
SM4-OFB
Provided:
{ 2.16.840.1.101.3.4.1.22, AES-192-CBC, AES192 } @ default
{ 1.2.410.200046.1.1.12, ARIA-256-CBC, ARIA256 } @ default
{ 2.16.840.1.101.3.4.1.4, AES-128-CFB } @ default
{ 1.2.410.200046.1.1.38, ARIA-192-CCM } @ default
{ 1.2.410.200046.1.1.1, ARIA-128-ECB } @ default
{ 2.16.840.1.101.3.4.1.2, AES-128-CBC, AES128 } @ default
{ 2.16.840.1.101.3.4.1.24, AES-192-CFB } @ default
{ 1.2.392.200011.61.1.1.1.2, CAMELLIA-128-CBC, CAMELLIA128 } @ default
{ 1.2.392.200011.61.1.1.1.4, CAMELLIA-256-CBC, CAMELLIA256 } @ default
{ 1.2.410.200046.1.1.35, ARIA-192-GCM } @ default
{ 2.16.840.1.101.3.4.1.42, AES-256-CBC, AES256 } @ default
{ 1.2.410.200046.1.1.36, ARIA-256-GCM } @ default
{ 1.3.111.2.1619.0.1.2, AES-256-XTS } @ default
{ 1.2.840.113549.1.9.16.3.6, DES3-WRAP, id-smime-alg-CMS3DESwrap } @ default
{ 2.16.840.1.101.3.4.1.48, AES-256-WRAP-PAD, AES256-WRAP-PAD, id-aes256-wrap-pad } @ default
{ 1.2.156.10197.1.104.3, SM4-OFB, SM4-OFB128 } @ default
{ 2.16.840.1.101.3.4.1.25, AES-192-WRAP, AES192-WRAP, id-aes192-wrap } @ default
{ 2.16.840.1.101.3.4.1.41, AES-256-ECB } @ default
{ 0.3.4401.5.3.1.9.49, CAMELLIA-256-CTR } @ default
{ 1.2.410.200046.1.1.2, ARIA-128-CBC, ARIA128 } @ default
{ 2.16.840.1.101.3.4.1.6, aes-128-gcm, id-aes128-GCM } @ default
{ 0.3.4401.5.3.1.9.41, CAMELLIA-256-ECB } @ default
{ 2.16.840.1.101.3.4.1.44, AES-256-CFB } @ default
{ 2.16.840.1.101.3.4.1.8, AES-128-WRAP-PAD, AES128-WRAP-PAD, id-aes128-wrap-pad } @ default
{ 1.2.156.10197.1.104.4, SM4-CFB, SM4-CFB128 } @ default
{ 0.3.4401.5.3.1.9.4, CAMELLIA-128-CFB } @ default
{ 1.2.410.200046.1.1.39, ARIA-256-CCM } @ default
{ 1.2.410.200046.1.1.14, ARIA-256-OFB } @ default
{ 2.16.840.1.101.3.4.1.46, aes-256-gcm, id-aes256-GCM } @ default
{ 0.3.4401.5.3.1.9.9, CAMELLIA-128-CTR } @ default
{ 2.16.840.1.101.3.4.1.23, AES-192-OFB } @ default
{ 1.2.156.10197.1.104.1, SM4-ECB } @ default
{ 2.16.840.1.101.3.4.1.7, aes-128-ccm, id-aes128-CCM } @ default
{ 2.16.840.1.101.3.4.1.47, aes-256-ccm, id-aes256-CCM } @ default
{ 1.2.410.200046.1.1.7, ARIA-192-CBC, ARIA192 } @ default
{ 2.16.840.1.101.3.4.1.45, AES-256-WRAP, AES256-WRAP, id-aes256-wrap } @ default
{ 1.2.410.200046.1.1.15, ARIA-256-CTR } @ default
{ 1.2.410.200046.1.1.3, ARIA-128-CFB } @ default
{ 1.2.410.200046.1.1.34, ARIA-128-GCM } @ default
{ 1.2.410.200046.1.1.6, ARIA-192-ECB } @ default
{ 2.16.840.1.101.3.4.1.26, aes-192-gcm, id-aes192-GCM } @ default
{ 0.3.4401.5.3.1.9.29, CAMELLIA-192-CTR } @ default
{ 0.3.4401.5.3.1.9.43, CAMELLIA-256-OFB } @ default
{ 1.2.156.10197.1.104.2, SM4, SM4-CBC } @ default
{ 1.2.410.200046.1.1.37, ARIA-128-CCM } @ default
{ 2.16.840.1.101.3.4.1.27, aes-192-ccm, id-aes192-CCM } @ default
{ 1.3.14.3.2.17, DES-EDE, DES-EDE-ECB } @ default
{ 1.2.410.200046.1.1.11, ARIA-256-ECB } @ default
{ 1.3.111.2.1619.0.1.1, AES-128-XTS } @ default
{ 2.16.840.1.101.3.4.1.5, AES-128-WRAP, AES128-WRAP, id-aes128-wrap } @ default
{ 2.16.840.1.101.3.4.1.3, AES-128-OFB } @ default
{ 0.3.4401.5.3.1.9.3, CAMELLIA-128-OFB } @ default
{ 0.3.4401.5.3.1.9.1, CAMELLIA-128-ECB } @ default
{ 1.2.840.113549.3.7, DES-EDE3-CBC, DES3 } @ default
{ 0.3.4401.5.3.1.9.44, CAMELLIA-256-CFB } @ default
{ 1.2.410.200046.1.1.10, ARIA-192-CTR } @ default
{ 0.3.4401.5.3.1.9.23, CAMELLIA-192-OFB } @ default
{ 0.3.4401.5.3.1.9.24, CAMELLIA-192-CFB } @ default
{ 1.2.410.200046.1.1.9, ARIA-192-OFB } @ default
{ 1.2.410.200046.1.1.13, ARIA-256-CFB } @ default
{ 2.16.840.1.101.3.4.1.1, AES-128-ECB } @ default
{ 2.16.840.1.101.3.4.1.28, AES-192-WRAP-PAD, AES192-WRAP-PAD, id-aes192-wrap-pad } @ default
{ 1.2.410.200046.1.1.8, ARIA-192-CFB } @ default
{ 1.2.156.10197.1.104.7, SM4-CTR } @ default
{ 2.16.840.1.101.3.4.1.43, AES-256-OFB } @ default
{ 1.2.410.200046.1.1.4, ARIA-128-OFB } @ default
{ 1.2.392.200011.61.1.1.1.3, CAMELLIA-192-CBC, CAMELLIA192 } @ default
{ 0.3.4401.5.3.1.9.21, CAMELLIA-192-ECB } @ default
{ 1.2.410.200046.1.1.5, ARIA-128-CTR } @ default
{ 2.16.840.1.101.3.4.1.21, AES-192-ECB } @ default
NULL @ default
AES-128-CBC-CTS @ default
AES-192-CBC-CTS @ default
AES-256-CBC-CTS @ default
AES-256-CFB1 @ default
AES-192-CFB1 @ default
AES-128-CFB1 @ default
AES-256-CFB8 @ default
AES-192-CFB8 @ default
AES-128-CFB8 @ default
AES-256-CTR @ default
AES-192-CTR @ default
AES-128-CTR @ default
AES-256-OCB @ default
AES-192-OCB @ default
AES-128-OCB @ default
AES-128-SIV @ default
AES-192-SIV @ default
AES-256-SIV @ default
{ AES-256-WRAP-INV, AES256-WRAP-INV } @ default
{ AES-192-WRAP-INV, AES192-WRAP-INV } @ default
{ AES-128-WRAP-INV, AES128-WRAP-INV } @ default
{ AES-256-WRAP-PAD-INV, AES256-WRAP-PAD-INV } @ default
{ AES-192-WRAP-PAD-INV, AES192-WRAP-PAD-INV } @ default
{ AES-128-WRAP-PAD-INV, AES128-WRAP-PAD-INV } @ default
AES-128-CBC-HMAC-SHA1 @ default
AES-256-CBC-HMAC-SHA1 @ default
AES-128-CBC-HMAC-SHA256 @ default
AES-256-CBC-HMAC-SHA256 @ default
ARIA-256-CFB1 @ default
ARIA-192-CFB1 @ default
ARIA-128-CFB1 @ default
ARIA-256-CFB8 @ default
ARIA-192-CFB8 @ default
ARIA-128-CFB8 @ default
CAMELLIA-128-CBC-CTS @ default
CAMELLIA-192-CBC-CTS @ default
CAMELLIA-256-CBC-CTS @ default
CAMELLIA-256-CFB1 @ default
CAMELLIA-192-CFB1 @ default
CAMELLIA-128-CFB1 @ default
CAMELLIA-256-CFB8 @ default
CAMELLIA-192-CFB8 @ default
CAMELLIA-128-CFB8 @ default
{ DES-EDE3, DES-EDE3-ECB } @ default
DES-EDE3-OFB @ default
DES-EDE3-CFB @ default
DES-EDE3-CFB8 @ default
DES-EDE3-CFB1 @ default
DES-EDE-CBC @ default
DES-EDE-OFB @ default
DES-EDE-CFB @ default
{ 1.2.156.10197.1.104.8, SM4-GCM } @ default
{ 1.2.156.10197.1.104.9, SM4-CCM } @ default
ChaCha20 @ default
ChaCha20-Poly1305 @ default
国密测试
生成CA根证书国密SM2私钥
# root @ ubuntu in ~/SMx_test [7:55:45]
$ /opt/openssl-3.1.1/bin/openssl ecparam -list_curves
secp112r1 : SECG/WTLS curve over a 112 bit prime field
secp112r2 : SECG curve over a 112 bit prime field
secp128r1 : SECG curve over a 128 bit prime field
secp128r2 : SECG curve over a 128 bit prime field
secp160k1 : SECG curve over a 160 bit prime field
secp160r1 : SECG curve over a 160 bit prime field
secp160r2 : SECG/WTLS curve over a 160 bit prime field
secp192k1 : SECG curve over a 192 bit prime field
secp224k1 : SECG curve over a 224 bit prime field
secp224r1 : NIST/SECG curve over a 224 bit prime field
secp256k1 : SECG curve over a 256 bit prime field
secp384r1 : NIST/SECG curve over a 384 bit prime field
secp521r1 : NIST/SECG curve over a 521 bit prime field
prime192v1: NIST/X9.62/SECG curve over a 192 bit prime field
prime192v2: X9.62 curve over a 192 bit prime field
prime192v3: X9.62 curve over a 192 bit prime field
prime239v1: X9.62 curve over a 239 bit prime field
prime239v2: X9.62 curve over a 239 bit prime field
prime239v3: X9.62 curve over a 239 bit prime field
prime256v1: X9.62/SECG curve over a 256 bit prime field
sect113r1 : SECG curve over a 113 bit binary field
sect113r2 : SECG curve over a 113 bit binary field
sect131r1 : SECG/WTLS curve over a 131 bit binary field
sect131r2 : SECG curve over a 131 bit binary field
sect163k1 : NIST/SECG/WTLS curve over a 163 bit binary field
sect163r1 : SECG curve over a 163 bit binary field
sect163r2 : NIST/SECG curve over a 163 bit binary field
sect193r1 : SECG curve over a 193 bit binary field
sect193r2 : SECG curve over a 193 bit binary field
sect233k1 : NIST/SECG/WTLS curve over a 233 bit binary field
sect233r1 : NIST/SECG/WTLS curve over a 233 bit binary field
sect239k1 : SECG curve over a 239 bit binary field
sect283k1 : NIST/SECG curve over a 283 bit binary field
sect283r1 : NIST/SECG curve over a 283 bit binary field
sect409k1 : NIST/SECG curve over a 409 bit binary field
sect409r1 : NIST/SECG curve over a 409 bit binary field
sect571k1 : NIST/SECG curve over a 571 bit binary field
sect571r1 : NIST/SECG curve over a 571 bit binary field
c2pnb163v1: X9.62 curve over a 163 bit binary field
c2pnb163v2: X9.62 curve over a 163 bit binary field
c2pnb163v3: X9.62 curve over a 163 bit binary field
c2pnb176v1: X9.62 curve over a 176 bit binary field
c2tnb191v1: X9.62 curve over a 191 bit binary field
c2tnb191v2: X9.62 curve over a 191 bit binary field
c2tnb191v3: X9.62 curve over a 191 bit binary field
c2pnb208w1: X9.62 curve over a 208 bit binary field
c2tnb239v1: X9.62 curve over a 239 bit binary field
c2tnb239v2: X9.62 curve over a 239 bit binary field
c2tnb239v3: X9.62 curve over a 239 bit binary field
c2pnb272w1: X9.62 curve over a 272 bit binary field
c2pnb304w1: X9.62 curve over a 304 bit binary field
c2tnb359v1: X9.62 curve over a 359 bit binary field
c2pnb368w1: X9.62 curve over a 368 bit binary field
c2tnb431r1: X9.62 curve over a 431 bit binary field
wap-wsg-idm-ecid-wtls1: WTLS curve over a 113 bit binary field
wap-wsg-idm-ecid-wtls3: NIST/SECG/WTLS curve over a 163 bit binary field
wap-wsg-idm-ecid-wtls4: SECG curve over a 113 bit binary field
wap-wsg-idm-ecid-wtls5: X9.62 curve over a 163 bit binary field
wap-wsg-idm-ecid-wtls6: SECG/WTLS curve over a 112 bit prime field
wap-wsg-idm-ecid-wtls7: SECG/WTLS curve over a 160 bit prime field
wap-wsg-idm-ecid-wtls8: WTLS curve over a 112 bit prime field
wap-wsg-idm-ecid-wtls9: WTLS curve over a 160 bit prime field
wap-wsg-idm-ecid-wtls10: NIST/SECG/WTLS curve over a 233 bit binary field
wap-wsg-idm-ecid-wtls11: NIST/SECG/WTLS curve over a 233 bit binary field
wap-wsg-idm-ecid-wtls12: WTLS curve over a 224 bit prime field
Oakley-EC2N-3:
IPSec/IKE/Oakley curve #3 over a 155 bit binary field.
Not suitable for ECDSA.
Questionable extension field!
Oakley-EC2N-4:
IPSec/IKE/Oakley curve #4 over a 185 bit binary field.
Not suitable for ECDSA.
Questionable extension field!
brainpoolP160r1: RFC 5639 curve over a 160 bit prime field
brainpoolP160t1: RFC 5639 curve over a 160 bit prime field
brainpoolP192r1: RFC 5639 curve over a 192 bit prime field
brainpoolP192t1: RFC 5639 curve over a 192 bit prime field
brainpoolP224r1: RFC 5639 curve over a 224 bit prime field
brainpoolP224t1: RFC 5639 curve over a 224 bit prime field
brainpoolP256r1: RFC 5639 curve over a 256 bit prime field
brainpoolP256t1: RFC 5639 curve over a 256 bit prime field
brainpoolP320r1: RFC 5639 curve over a 320 bit prime field
brainpoolP320t1: RFC 5639 curve over a 320 bit prime field
brainpoolP384r1: RFC 5639 curve over a 384 bit prime field
brainpoolP384t1: RFC 5639 curve over a 384 bit prime field
brainpoolP512r1: RFC 5639 curve over a 512 bit prime field
brainpoolP512t1: RFC 5639 curve over a 512 bit prime field
SM2 : SM2 curve over a 256 bit prime field
# root @ ubuntu in ~/SMx_test [9:06:38] C:130
$ /opt/openssl-3.1.1/bin/openssl ecparam -genkey -name SM2 -out root.key
# root @ ubuntu in ~/SMx_test [9:08:12]
$ cat root.key
-----BEGIN SM2 PARAMETERS-----
BggqgRzPVQGCLQ==
-----END SM2 PARAMETERS-----
-----BEGIN PRIVATE KEY-----
MIGIAgEAMBQGCCqBHM9VAYItBggqgRzPVQGCLQRtMGsCAQEEIMseXRorRdHJe5ab
2J4iSjWmBGQOlHIIJR38mqk9h1VroUQDQgAERa17YaXohsIanVDRoJJRhkPTpIZf
U+DcVcUDaUHjPXKZcbTnNjf2boiD4oORZ1CV5VMbnWYSew37SPn1Anbiqg==
-----END PRIVATE KEY-----
# root @ ubuntu in ~/SMx_test [9:08:17]
$ /opt/openssl-3.1.1/bin/openssl ecparam -text -noout -in root.key
Could not read params of EC parameters from root.key
C091F8D0AC7F0000:error:1E08010C:DECODER routines:OSSL_DECODER_from_bio:unsupported:crypto/encode_decode/decoder_lib.c:102:No supported data to decode. Input type: PEM
C091F8D0AC7F0000:error:1608010C:STORE routines:ossl_store_handle_load_result:unsupported:crypto/store/store_result.c:151:
# root @ ubuntu in ~/SMx_test [9:08:26] C:1
$ /opt/openssl-3.1.1/bin/openssl ec -text -noout -in root.key
read EC key
Private-Key: (256 bit)
priv:
cb:1e:5d:1a:2b:45:d1:c9:7b:96:9b:d8:9e:22:4a:
35:a6:04:64:0e:94:72:08:25:1d:fc:9a:a9:3d:87:
55:6b
pub:
04:45:ad:7b:61:a5:e8:86:c2:1a:9d:50:d1:a0:92:
51:86:43:d3:a4:86:5f:53:e0:dc:55:c5:03:69:41:
e3:3d:72:99:71:b4:e7:36:37:f6:6e:88:83:e2:83:
91:67:50:95:e5:53:1b:9d:66:12:7b:0d:fb:48:f9:
f5:02:76:e2:aa
ASN1 OID: SM2
看着好像是没有问题。
生成CA根证书国密SM2公钥
# root @ ubuntu in ~/SMx_test [9:26:12] C:1
$ /opt/openssl-3.1.1/bin/openssl ec -in root.key -text -noout
read EC key
Private-Key: (256 bit)
priv:
29:9a:da:8d:84:60:6e:cf:ee:9b:ed:16:33:7d:43:
f1:a8:b1:cb:2c:1c:81:87:5e:56:93:4f:9c:3a:56:
8b:01
pub:
04:1c:92:71:8c:d5:bd:42:75:34:59:53:de:97:11:
07:9c:4b:bf:d6:13:97:e1:99:b3:ec:71:57:84:24:
e4:3c:5d:26:f8:06:f8:c2:e9:db:de:cc:e2:e8:10:
27:eb:8d:73:fc:06:89:c8:14:b5:a3:d5:a0:b1:ce:
13:50:d1:c2:b1
ASN1 OID: SM2
# root @ ubuntu in ~/SMx_test [9:19:55]
$ /opt/openssl-3.1.1/bin/openssl ec -pubout -in root.key -out root_pub.key
read EC key
writing EC key
# root @ ubuntu in ~/SMx_test [9:20:03]
$ ls
root.key root_pub.key
# root @ ubuntu in ~/SMx_test [9:20:09]
$ cat root_pub.key
-----BEGIN PUBLIC KEY-----
MFowFAYIKoEcz1UBgi0GCCqBHM9VAYItA0IABByScYzVvUJ1NFlT3pcRB5xLv9YT
l+GZs+xxV4Qk5DxdJvgG+MLp297M4ugQJ+uNc/wGicgUtaPVoLHOE1DRwrE=
-----END PUBLIC KEY-----
# root @ ubuntu in ~/SMx_test [9:23:51] C:1
$ /opt/openssl-3.1.1/bin/openssl ec -pubin -in root_pub.key -text -noout
read EC key
Public-Key: (256 bit)
pub:
04:1c:92:71:8c:d5:bd:42:75:34:59:53:de:97:11:
07:9c:4b:bf:d6:13:97:e1:99:b3:ec:71:57:84:24:
e4:3c:5d:26:f8:06:f8:c2:e9:db:de:cc:e2:e8:10:
27:eb:8d:73:fc:06:89:c8:14:b5:a3:d5:a0:b1:ce:
13:50:d1:c2:b1
ASN1 OID: SM2
生成CA根证书
# root @ ubuntu in ~/SMx_test [9:33:34]
$ /opt/openssl-3.1.1/bin/openssl req -new -x509 -key root.key -out root.crt
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:HN
Locality Name (eg, city) []:ZZ
Organization Name (eg, company) [Internet Widgits Pty Ltd]:JL
Organizational Unit Name (eg, section) []:HW
Common Name (e.g. server FQDN or YOUR name) []:liuyuelong.com
Email Address []:[email protected]
# root @ ubuntu in ~/SMx_test [9:35:16]
$ ls
root.crt root.key root_pub.key
# root @ ubuntu in ~/SMx_test [9:35:19]
$ cat root.crt
-----BEGIN CERTIFICATE-----
MIICTjCCAfSgAwIBAgIUDHdnZH56/dBiHojqqNzfhoDDIUwwCgYIKoEcz1UBg3Uw
fDELMAkGA1UEBhMCQ04xCzAJBgNVBAgMAkhOMQswCQYDVQQHDAJaWjELMAkGA1UE
CgwCSkwxCzAJBgNVBAsMAkhXMRcwFQYDVQQDDA5saXV5dWVsb25nLmNvbTEgMB4G
CSqGSIb3DQEJARYReWpraHRkZHhAc2luYS5jb20wHhcNMjMwNzI3MDkzNTE2WhcN
MjMwODI2MDkzNTE2WjB8MQswCQYDVQQGEwJDTjELMAkGA1UECAwCSE4xCzAJBgNV
BAcMAlpaMQswCQYDVQQKDAJKTDELMAkGA1UECwwCSFcxFzAVBgNVBAMMDmxpdXl1
ZWxvbmcuY29tMSAwHgYJKoZIhvcNAQkBFhF5amtodGRkeEBzaW5hLmNvbTBaMBQG
CCqBHM9VAYItBggqgRzPVQGCLQNCAAQcknGM1b1CdTRZU96XEQecS7/WE5fhmbPs
cVeEJOQ8XSb4BvjC6dvezOLoECfrjXP8BonIFLWj1aCxzhNQ0cKxo1MwUTAdBgNV
HQ4EFgQUuT7GISEAApZf7WL7sjR2DDZM62IwHwYDVR0jBBgwFoAUuT7GISEAApZf
7WL7sjR2DDZM62IwDwYDVR0TAQH/BAUwAwEB/zAKBggqgRzPVQGDdQNIADBFAiEA
3ggGkI7OL8pR21OPYt/ogyXTQz8pdjs5BwHwf1+NVnMCIHyXJO05Fe0BGAxG4bhC
N5fiGR1dwR6StS/LnriuW0aT
-----END CERTIFICATE-----
# root @ ubuntu in ~/SMx_test [9:35:49]
$ /opt/openssl-3.1.1/bin/openssl x509 -in root.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
0c:77:67:64:7e:7a:fd:d0:62:1e:88:ea:a8:dc:df:86:80:c3:21:4c
Signature Algorithm: SM2-with-SM3
Issuer: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = liuyuelong.com, emailAddress = [email protected]
Validity
Not Before: Jul 27 09:35:16 2023 GMT
Not After : Aug 26 09:35:16 2023 GMT
Subject: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = liuyuelong.com, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: sm2
Public-Key: (256 bit)
pub:
04:1c:92:71:8c:d5:bd:42:75:34:59:53:de:97:11:
07:9c:4b:bf:d6:13:97:e1:99:b3:ec:71:57:84:24:
e4:3c:5d:26:f8:06:f8:c2:e9:db:de:cc:e2:e8:10:
27:eb:8d:73:fc:06:89:c8:14:b5:a3:d5:a0:b1:ce:
13:50:d1:c2:b1
ASN1 OID: SM2
X509v3 extensions:
X509v3 Subject Key Identifier:
B9:3E:C6:21:21:00:02:96:5F:ED:62:FB:B2:34:76:0C:36:4C:EB:62
X509v3 Authority Key Identifier:
B9:3E:C6:21:21:00:02:96:5F:ED:62:FB:B2:34:76:0C:36:4C:EB:62
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: SM2-with-SM3
Signature Value:
30:45:02:21:00:de:08:06:90:8e:ce:2f:ca:51:db:53:8f:62:
df:e8:83:25:d3:43:3f:29:76:3b:39:07:01:f0:7f:5f:8d:56:
73:02:20:7c:97:24:ed:39:15:ed:01:18:0c:46:e1:b8:42:37:
97:e2:19:1d:5d:c1:1e:92:b5:2f:cb:9e:b8:ae:5b:46:93
SM2算法的私钥,openssl自动选择SM2-with-SM3签名算法,牛B。
给使用CA根证书给CA根证书验签
正常使用应该没有这种使用场景,但是验一下也无妨嘛。
# root @ ubuntu in ~/SMx_test [9:36:45]
$ /opt/openssl-3.1.1/bin/openssl verify -CAfile root.crt root.crt
root.crt: OK
肯定是没有问题的嘛,自己给自己验签怎么会有问题呢!
生成服务器密钥对
# root @ ubuntu in ~/SMx_test [1:08:49]
$ /opt/openssl-3.1.1/bin/openssl ecparam -genkey -name SM2 -out server.key
# root @ ubuntu in ~/SMx_test [1:09:21]
$ cat server.key
-----BEGIN SM2 PARAMETERS-----
BggqgRzPVQGCLQ==
-----END SM2 PARAMETERS-----
-----BEGIN PRIVATE KEY-----
MIGIAgEAMBQGCCqBHM9VAYItBggqgRzPVQGCLQRtMGsCAQEEIHjB95D+zU84Ybgg
0iAwogycqDM1yjQeK1iPX0xwwZXioUQDQgAEj6Fi8BEulmmcHish9fsI6gZEgjSA
ORDpOEaZ2LrmsBhzm059n2z0UDWvEGHPPC55miwSpfQUhA8WuE4avYk6Ag==
-----END PRIVATE KEY-----
# root @ ubuntu in ~/SMx_test [1:09:25]
$ /opt/openssl-3.1.1/bin/openssl ec -text -noout -in server.key
read EC key
Private-Key: (256 bit)
priv:
78:c1:f7:90:fe:cd:4f:38:61:b8:20:d2:20:30:a2:
0c:9c:a8:33:35:ca:34:1e:2b:58:8f:5f:4c:70:c1:
95:e2
pub:
04:8f:a1:62:f0:11:2e:96:69:9c:1e:2b:21:f5:fb:
08:ea:06:44:82:34:80:39:10:e9:38:46:99:d8:ba:
e6:b0:18:73:9b:4e:7d:9f:6c:f4:50:35:af:10:61:
cf:3c:2e:79:9a:2c:12:a5:f4:14:84:0f:16:b8:4e:
1a:bd:89:3a:02
ASN1 OID: SM2
# root @ ubuntu in ~/SMx_test [1:10:06] C:127
$ /opt/openssl-3.1.1/bin/openssl ec -pubout -in server.key -out server_pub.key
read EC key
writing EC key
# root @ ubuntu in ~/SMx_test [1:10:23]
$ cat server_pub.key
-----BEGIN PUBLIC KEY-----
MFowFAYIKoEcz1UBgi0GCCqBHM9VAYItA0IABI+hYvARLpZpnB4rIfX7COoGRII0
gDkQ6ThGmdi65rAYc5tOfZ9s9FA1rxBhzzwueZosEqX0FIQPFrhOGr2JOgI=
-----END PUBLIC KEY-----
# root @ ubuntu in ~/SMx_test [1:10:36]
$ /opt/openssl-3.1.1/bin/openssl ec -pubin -in server_pub.key -text -noout
read EC key
Public-Key: (256 bit)
pub:
04:8f:a1:62:f0:11:2e:96:69:9c:1e:2b:21:f5:fb:
08:ea:06:44:82:34:80:39:10:e9:38:46:99:d8:ba:
e6:b0:18:73:9b:4e:7d:9f:6c:f4:50:35:af:10:61:
cf:3c:2e:79:9a:2c:12:a5:f4:14:84:0f:16:b8:4e:
1a:bd:89:3a:02
ASN1 OID: SM2
生成服务器证书请求文件
# root @ ubuntu in ~/SMx_test [1:11:30] C:130
$ /opt/openssl-3.1.1/bin/openssl req -new -key server.key -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:HN
Locality Name (eg, city) []:ZZ
Organization Name (eg, company) [Internet Widgits Pty Ltd]:JL
Organizational Unit Name (eg, section) []:HW
Common Name (e.g. server FQDN or YOUR name) []:*.liuyunuo.cn
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# root @ ubuntu in ~/SMx_test [1:18:27]
$ cat server.csr
-----BEGIN CERTIFICATE REQUEST-----
MIIBNzCB3gIBADB7MQswCQYDVQQGEwJDTjELMAkGA1UECAwCSE4xCzAJBgNVBAcM
AlpaMQswCQYDVQQKDAJKTDELMAkGA1UECwwCSFcxFjAUBgNVBAMMDSoubGl1eXVu
dW8uY24xIDAeBgkqhkiG9w0BCQEWEXlqa2h0ZGR4QHNpbmEuY29tMFowFAYIKoEc
z1UBgi0GCCqBHM9VAYItA0IABI+hYvARLpZpnB4rIfX7COoGRII0gDkQ6ThGmdi6
5rAYc5tOfZ9s9FA1rxBhzzwueZosEqX0FIQPFrhOGr2JOgKgADAKBggqgRzPVQGD
dQNIADBFAiBMd/NcRzTelVCtjhQL8mU7qb0BY2T3VH+jn2DYdBsnTgIhAKBX0qFb
IAudJ9D2O2uTf66i9CRncxWpD22/1m2ORz/s
-----END CERTIFICATE REQUEST-----
# root @ ubuntu in ~/SMx_test [1:18:38]
$ /opt/openssl-3.1.1/bin/openssl req -text -noout -in server.csr
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: sm2
Public-Key: (256 bit)
pub:
04:8f:a1:62:f0:11:2e:96:69:9c:1e:2b:21:f5:fb:
08:ea:06:44:82:34:80:39:10:e9:38:46:99:d8:ba:
e6:b0:18:73:9b:4e:7d:9f:6c:f4:50:35:af:10:61:
cf:3c:2e:79:9a:2c:12:a5:f4:14:84:0f:16:b8:4e:
1a:bd:89:3a:02
ASN1 OID: SM2
Attributes:
(none)
Requested Extensions:
Signature Algorithm: SM2-with-SM3
Signature Value:
30:45:02:20:4c:77:f3:5c:47:34:de:95:50:ad:8e:14:0b:f2:
65:3b:a9:bd:01:63:64:f7:54:7f:a3:9f:60:d8:74:1b:27:4e:
02:21:00:a0:57:d2:a1:5b:20:0b:9d:27:d0:f6:3b:6b:93:7f:
ae:a2:f4:24:67:73:15:a9:0f:6d:bf:d6:6d:8e:47:3f:ec
CA私钥通过服务器证书请求为服务器生成证书(错误)
# root @ ubuntu in ~/SMx_test [1:38:58] C:1
$ /opt/openssl-3.1.1/bin/openssl x509 -req -in server.csr -signkey root.key -out server.crt
Certificate request self-signature ok
subject=C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
# root @ ubuntu in ~/SMx_test [1:39:12]
$ cat server.crt
-----BEGIN CERTIFICATE-----
MIIB8zCCAZgCFHhSrlWiLFM3tN9+SSeErM9SRrAaMAoGCCqBHM9VAYN1MHsxCzAJ
BgNVBAYTAkNOMQswCQYDVQQIDAJITjELMAkGA1UEBwwCWloxCzAJBgNVBAoMAkpM
MQswCQYDVQQLDAJIVzEWMBQGA1UEAwwNKi5saXV5dW51by5jbjEgMB4GCSqGSIb3
DQEJARYReWpraHRkZHhAc2luYS5jb20wHhcNMjMwNzI4MDEzOTEyWhcNMjMwODI3
MDEzOTEyWjB7MQswCQYDVQQGEwJDTjELMAkGA1UECAwCSE4xCzAJBgNVBAcMAlpa
MQswCQYDVQQKDAJKTDELMAkGA1UECwwCSFcxFjAUBgNVBAMMDSoubGl1eXVudW8u
Y24xIDAeBgkqhkiG9w0BCQEWEXlqa2h0ZGR4QHNpbmEuY29tMFowFAYIKoEcz1UB
gi0GCCqBHM9VAYItA0IABByScYzVvUJ1NFlT3pcRB5xLv9YTl+GZs+xxV4Qk5Dxd
JvgG+MLp297M4ugQJ+uNc/wGicgUtaPVoLHOE1DRwrEwCgYIKoEcz1UBg3UDSQAw
RgIhAPLtgPAFtxEFXxzCJFxRYBa5m9kKlD+RCf/2N56Q+Of3AiEAktIMixCUkOUY
olV8UX/WWiypi+BTIIKCsjLaprYWBlE=
-----END CERTIFICATE-----
# root @ ubuntu in ~/SMx_test [1:39:21]
$ /opt/openssl-3.1.1/bin/openssl x509 -in server.crt -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
78:52:ae:55:a2:2c:53:37:b4:df:7e:49:27:84:ac:cf:52:46:b0:1a
Signature Algorithm: SM2-with-SM3
Issuer: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
Validity
Not Before: Jul 28 01:39:12 2023 GMT
Not After : Aug 27 01:39:12 2023 GMT
Subject: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: sm2
Public-Key: (256 bit)
pub:
04:1c:92:71:8c:d5:bd:42:75:34:59:53:de:97:11:
07:9c:4b:bf:d6:13:97:e1:99:b3:ec:71:57:84:24:
e4:3c:5d:26:f8:06:f8:c2:e9:db:de:cc:e2:e8:10:
27:eb:8d:73:fc:06:89:c8:14:b5:a3:d5:a0:b1:ce:
13:50:d1:c2:b1
ASN1 OID: SM2
Signature Algorithm: SM2-with-SM3
Signature Value:
30:46:02:21:00:f2:ed:80:f0:05:b7:11:05:5f:1c:c2:24:5c:
51:60:16:b9:9b:d9:0a:94:3f:91:09:ff:f6:37:9e:90:f8:e7:
f7:02:21:00:92:d2:0c:8b:10:94:90:e5:18:a2:55:7c:51:7f:
d6:5a:2c:a9:8b:e0:53:20:82:82:b2:32:da:a6:b6:16:06:51
使用CA证书对服务器证书进行验签(错误)
# root @ ubuntu in ~/SMx_test [1:40:15]
$ /opt/openssl-3.1.1/bin/openssl verify -CAfile root.crt server.crt
C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
error 18 at 0 depth lookup: self-signed certificate
error server.crt: verification failed
生成服务器证书并验签
# root @ ubuntu in ~/SMx_test [3:10:56]
$ /opt/openssl-3.1.1/bin/openssl x509 -req -in server.csr -CA root.crt -CAkey root.key -CAcreateserial -out server1.crt
Certificate request self-signature ok
subject=C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
# root @ ubuntu in ~/SMx_test [3:11:57]
$ /opt/openssl-3.1.1/bin/openssl x509 -in server1.crt -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
2f:c5:e1:c5:52:f4:5a:29:b9:c1:fc:06:c1:51:1e:51:36:71:56:85
Signature Algorithm: SM2-with-SM3
Issuer: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = liuyuelong.com, emailAddress = [email protected]
Validity
Not Before: Jul 28 03:11:57 2023 GMT
Not After : Aug 27 03:11:57 2023 GMT
Subject: C = CN, ST = HN, L = ZZ, O = JL, OU = HW, CN = *.liuyunuo.cn, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: sm2
Public-Key: (256 bit)
pub:
04:8f:a1:62:f0:11:2e:96:69:9c:1e:2b:21:f5:fb:
08:ea:06:44:82:34:80:39:10:e9:38:46:99:d8:ba:
e6:b0:18:73:9b:4e:7d:9f:6c:f4:50:35:af:10:61:
cf:3c:2e:79:9a:2c:12:a5:f4:14:84:0f:16:b8:4e:
1a:bd:89:3a:02
ASN1 OID: SM2
Signature Algorithm: SM2-with-SM3
Signature Value:
30:44:02:20:17:4a:fc:9d:75:b5:e7:ef:2a:53:11:11:ee:d4:
96:db:c6:03:1f:b3:df:f6:3a:be:44:b1:5c:7c:8f:c2:3e:96:
02:20:1b:87:40:96:95:61:54:12:c1:10:df:98:50:c8:cf:d5:
15:fc:66:0b:16:57:5d:02:37:61:36:27:3b:fb:de:e4
# root @ ubuntu in ~/SMx_test [3:12:08]
$ /opt/openssl-3.1.1/bin/openssl verify -CAfile root.crt server1.crt
server1.crt: OK
GA/T0015相关测试
给第三方生成的证书请求文件生成证书
# root @ ubuntu in ~/SMx_test [5:57:16]
$ /opt/openssl-3.1.1/bin/openssl req -text -noout -in gbs_req_cert_a77d169.pem
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = CN, ST = HN, L = ZZ, O = JL, OU = LiveGBS, CN = 34020000002000000001, serialNumber = a77d1691d30cdc6eec2e9fb0acd4a4f4
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:01:28:3c:50:26:d1:73:0d:e4:db:f8:14:62:bb:
1a:74:39:fc:b4:c5:9a:9b:82:6e:11:1a:4c:59:7d:
fb:97:31:8d:8c:7d:9b:cb:a9:35:36:f1:41:53:cf:
31:41:a7:91:bf:ef:a9:c9:5d:7d:63:38:62:46:70:
a6:2e:9d:76:12
ASN1 OID: SM2
Attributes:
Requested Extensions:
X509v3 Subject Alternative Name:
email:[email protected]
Signature Algorithm: SM2-with-SM3
Signature Value:
30:46:02:21:00:8f:f1:4c:5e:56:8a:8b:b8:d5:b2:9d:0b:05:
a4:72:ec:91:67:01:d0:84:b0:30:6a:ba:c1:10:f0:b2:ba:12:
8d:02:21:00:bd:01:a7:fe:03:35:ba:ad:2f:35:8d:f8:fe:b1:
1e:1e:7e:f7:5b:4e:f3:aa:22:d3:0a:2e:79:05:f2:17:e3:59
# root @ ubuntu in ~/SMx_test [6:14:35] C:1
$ /opt/openssl-3.1.1/bin/openssl x509 -req -in gbs_req_cert_a77d169.pem -CA root.crt -CAkey root.key -CAcreateserial -out livsGBS.crt
Certificate request self-signature did not match the contents
C001EC05457F0000:error:06880006:asn1 encoding routines:ASN1_item_verify_ctx:EVP lib:crypto/asn1/a_verify.c:217:
# root @ ubuntu in ~/SMx_test [6:15:07] C:1
$ /opt/openssl-3.1.1/bin/openssl x509 -req -in gbs_req_cert_a77d169.pem -CA root.crt -CAkey root.key -out livsGBS.crt
Certificate request self-signature did not match the contents
C0A13EE8427F0000:error:06880006:asn1 encoding routines:ASN1_item_verify_ctx:EVP lib:crypto/asn1/a_verify.c:217:
提示证书请求文件的公钥对签名进行验签没有过,扯淡了,已和第三方玩,就不行了。咋搞?
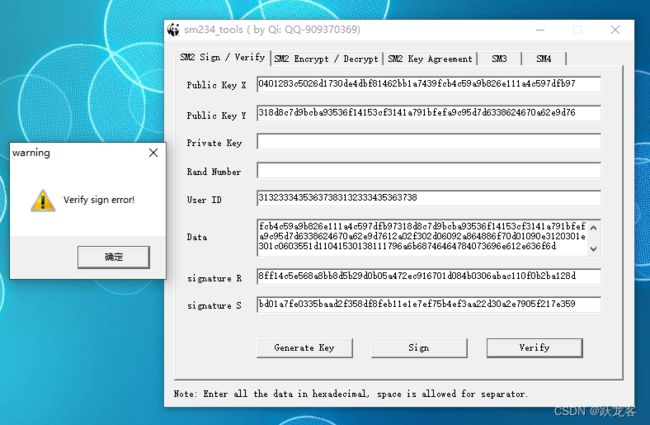
手工解析工具验签测试 (错误)
原始数据
3082017d
30820122020100308190310b300906035504061302434e310b300906035504081302484e310b3009060355040713025a5a310b3009060355040a13024a4c3110300e060355040b13074c697665474253311d301b060355040313143334303230303030303032303030303030303031312930270603550405132061373764313639316433306364633665656332653966623061636434613466343059301306072a8648ce3d020106082a811ccf5501822d0342000401283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb97318d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612a02f302d06092a864886f70d01090e3120301e301c0603551d11041530138111796a6b68746464784073696e612e636f6d[签名内容]
300a06082a811ccf55018375
03490030460221008ff14c5e568a8bb8d5b29d0b05a472ec916701d084b0306abac110f0b2ba128d022100bd01a7fe0335baad2f358df8feb11e1e7ef75b4ef3aa22d30a2e7905f217e35968[签名]
手工解析数据 (错误)
3082017d[SEQUENCE]
30820122[SEQUENCE]
020100[INTERGER:Version:1(0x00)]
308190[SEQUENCE:Subject]
310b[SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550406
1302[PrintableString(2)]
434e[CN:中国]
310b [SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550408[ID:stateOrProvinceName]
1302[PrintableString(2)]
484e[HN:河南]
310b [SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550407[ID:localityName]
1302[PrintableString(2)]
5a5a[ZZ:郑州]
310b [SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
55040a[ID:organizationName]
1302[PrintableString(2)]
4a4c[JL:巨龙]
3110[SET]
300e[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
55040b[ID:organizationalUnitName]
1307[PrintableString(7)]
4c697665474253[liveGBS]
311d[SET]
301b[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550403[ID:commonName]
1314[PrintableString(20)]
3334303230303030303032303030303030303031[34020000002000000001]
3129[SET]
3027[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550405[ID:serialNumber]
13201314[PrintableString(32)]
6137376431363931643330636463366565633265396662306163643461346634[a77d1691d30cdc6eec2e9fb0acd4a4f4]
3059[SEQUENCE]
3013[SEQUENCE]
0607[OBJECT IDENTIFIER(7)]
2a8648ce3d0201[ID:ecPublicKey]
0608[OBJECT IDENTIFIER(8)]
2a811ccf5501822d[ID:Unknow]
0342[BIT STRING(66)]
00[BIT STRING 忽略字节]
0401283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb97318d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612[公钥:65byte]
a02f[Context]
302d[SEQUENCE]
0609[OBJECT IDENTIFIER(9)]
2a864886f70d01090e
3120[SET]
301e[SEQUENCE]
301c[SEQUENCE]
0603[OBJECT IDENTIFIER(9)]
551d11[ID:subjectAltName]
0415[OCTET STRING]
3013[SEQUENCE]
8111[UnknowType]
796a6b68746464784073696e612e636f6d[[email protected]]
300a[SEQUENCE]
0608[OBJECT IDENTIFIER(7)]
2a811ccf55018375[ID:Unknow]
034900[BIT STRING]
3046[SEQUENCE]
0221[UnknowType]
00[BIT STRING 忽略字节]
8ff14c5e568a8bb8d5b29d0b05a472ec916701d084b0306abac110f0b2ba128d[signature R]
0221[UnknowType]
00[BIT STRING 忽略字节]
bd01a7fe0335baad2f358df8feb11e1e7ef75b4ef3aa22d30a2e7905f217e359[signature S]
68[UNknow]
验签测试 (错误)
[public Key X]
0401283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb97
[public Key Y]
318d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d76
[UserID]
31323334353637383132333435363738
[MessageData]
30820122020100308190310b300906035504061302434e310b300906035504081302484e310b3009060355040713025a5a310b3009060355040a13024a4c3110300e060355040b13074c697665474253311d301b060355040313143334303230303030303032303030303030303031312930270603550405132061373764313639316433306364633665656332653966623061636434613466343059301306072a8648ce3d020106082a811ccf5501822d0342000401283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb97318d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612a02f302d06092a864886f70d01090e3120301e301c0603551d11041530138111796a6b68746464784073696e612e636f6d
[signature R]
8ff14c5e568a8bb8d5b29d0b05a472ec916701d084b0306abac110f0b2ba128d
[signature S]
bd01a7fe0335baad2f358df8feb11e1e7ef75b4ef3aa22d30a2e7905f217e359
也不太会,大概解析一下证书结构。
手工解析工具验签测试(正确)
摇人帮忙,得到一下信息,原来公钥用错了。
在 SM2 公钥信息中,如果你提到的是前缀为 “00 04” 的公钥格式,它表示 SM2 公钥的非压缩格式。
具体地说,SM2 的非压缩公钥格式由以下部分组成:
“00”:表示这是非压缩格式,而不是压缩格式(压缩格式通常是以 “02” 或 “03” 开头)。
“04”:表示后续的数据是 x 和 y 坐标的完整表示。
后续的数据:固定长度为 64 字节,其中前 32 字节表示 x 坐标,后 32 字节表示 y 坐标,共同构成了 SM2 椭圆曲线上的公钥点。
因此,“00 04” 前缀指示了 SM2 公钥是以非压缩格式表示的,并且随后的 64 字节是完整的 x 和 y 坐标值,用于描述椭圆曲线上的公钥点。
原始数据
3082017d
30820122020100308190310b300906035504061302434e310b300906035504081302484e310b3009060355040713025a5a310b3009060355040a13024a4c3110300e060355040b13074c697665474253311d301b060355040313143334303230303030303032303030303030303031312930270603550405132061373764313639316433306364633665656332653966623061636434613466343059301306072a8648ce3d020106082a811ccf5501822d0342000401283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb97318d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612a02f302d06092a864886f70d01090e3120301e301c0603551d11041530138111796a6b68746464784073696e612e636f6d[签名内容]
300a06082a811ccf55018375
03490030460221008ff14c5e568a8bb8d5b29d0b05a472ec916701d084b0306abac110f0b2ba128d022100bd01a7fe0335baad2f358df8feb11e1e7ef75b4ef3aa22d30a2e7905f217e35968[签名]
手工解析数据
3082017d[SEQUENCE]
30820122[SEQUENCE]
020100[INTERGER:Version:1(0x00)]
308190[SEQUENCE:Subject]
310b[SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550406
1302[PrintableString(2)]
434e[CN:中国]
310b [SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550408[ID:stateOrProvinceName]
1302[PrintableString(2)]
484e[HN:河南]
310b [SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550407[ID:localityName]
1302[PrintableString(2)]
5a5a[ZZ:郑州]
310b [SET]
3009[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
55040a[ID:organizationName]
1302[PrintableString(2)]
4a4c[JL:巨龙]
3110[SET]
300e[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
55040b[ID:organizationalUnitName]
1307[PrintableString(7)]
4c697665474253[liveGBS]
311d[SET]
301b[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550403[ID:commonName]
1314[PrintableString(20)]
3334303230303030303032303030303030303031[34020000002000000001]
3129[SET]
3027[SEQUENCE]
0603[OBJECT IDENTIFIER(3)]
550405[ID:serialNumber]
13201314[PrintableString(32)]
6137376431363931643330636463366565633265396662306163643461346634[a77d1691d30cdc6eec2e9fb0acd4a4f4]
3059[SEQUENCE]
3013[SEQUENCE]
0607[OBJECT IDENTIFIER(7)]
2a8648ce3d0201[ID:ecPublicKey]
0608[OBJECT IDENTIFIER(8)]
2a811ccf5501822d[ID:Unknow]
0342[BIT STRING(66)]
0004[前缀,非压缩]
01283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb9731[public Key Y:32byte]
8d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612[public Key Y:32byte]
a02f[Context]
302d[SEQUENCE]
0609[OBJECT IDENTIFIER(9)]
2a864886f70d01090e
3120[SET]
301e[SEQUENCE]
301c[SEQUENCE]
0603[OBJECT IDENTIFIER(9)]
551d11[ID:subjectAltName]
0415[OCTET STRING]
3013[SEQUENCE]
8111[UnknowType]
796a6b68746464784073696e612e636f6d[[email protected]]
300a[SEQUENCE]
0608[OBJECT IDENTIFIER(7)]
2a811ccf55018375[ID:Unknow]
034900[BIT STRING]
3046[SEQUENCE]
0221[UnknowType]
00[BIT STRING 忽略字节]
8ff14c5e568a8bb8d5b29d0b05a472ec916701d084b0306abac110f0b2ba128d[signature R]
0221[UnknowType]
00[BIT STRING 忽略字节]
bd01a7fe0335baad2f358df8feb11e1e7ef75b4ef3aa22d30a2e7905f217e359[signature S]
68[UNknow]
验签测试
[public Key X]
01283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb9731
[public Key Y]
8d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612
[UserID]
31323334353637383132333435363738
[MessageData]
30820122020100308190310b300906035504061302434e310b300906035504081302484e310b3009060355040713025a5a310b3009060355040a13024a4c3110300e060355040b13074c697665474253311d301b060355040313143334303230303030303032303030303030303031312930270603550405132061373764313639316433306364633665656332653966623061636434613466343059301306072a8648ce3d020106082a811ccf5501822d0342000401283c5026d1730de4dbf81462bb1a7439fcb4c59a9b826e111a4c597dfb97318d8c7d9bcba93536f14153cf3141a791bfefa9c95d7d6338624670a62e9d7612a02f302d06092a864886f70d01090e3120301e301c0603551d11041530138111796a6b68746464784073696e612e636f6d
[signature R]
8ff14c5e568a8bb8d5b29d0b05a472ec916701d084b0306abac110f0b2ba128d
[signature S]
bd01a7fe0335baad2f358df8feb11e1e7ef75b4ef3aa22d30a2e7905f217e359
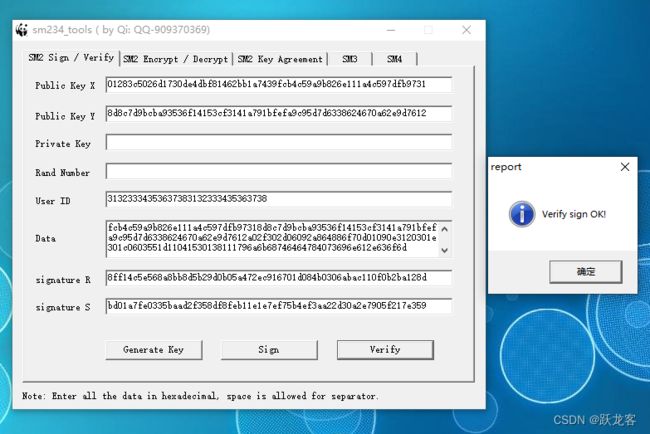
呵呵,那现在的问题就改为为什么openssl认为签名不对的问题。
暂时放弃好了
试试GMSSL好了