- 如何在 Ubuntu 22.04 上使用 LEMP 安装 WordPress 教程
vvw&
技术文章Linux开源项目推荐ubuntulinux运维服务器wordpressLEMPphp
简介:本教程旨在指导你如何在Ubuntu22.04上使用LEMP栈安装WordPress。WordPress是一个用PHP编写的开源内容管理系统。LEMP栈是Linux,NGINX,MySQL和PHP的缩写。WordPress非常用户友好,并提供了多种选项,例如不同的插件和具有精美设计的各种主题,使其成为用户最可定制的CMS。以下段落将介绍安装WordPress之前LEMP安装的所有步骤。在Ubu
- 想转行网络安全,可以先看看过来人的建议
孤独的汤姆
web安全安全
在当前就业形势下,不少朋友面临转行的困境。网络安全作为一个热门领域,自然也吸引了许多人的目光。本文将就转行网络安全这一话题,提供一些切实可行的建议。网络安全行业概况网络安全涵盖了从基础的脚本编写到高级的漏洞研究等多个层面。该领域包括但不限于:渗透测试、漏洞评估、恶意软件分析、入侵检测、信息安全管理等。这些内容的复杂性不一,从基础的安全监控到复杂的安全架构设计都涉及其中。这就意味着,尽管有些领域可能
- 仓颉编程语言:从入门到精通
为啥要瞅瞅仓颉这玩意儿?有一说一,现在的编程语言多得跟米一样,对吧?那一门新语言想火,没点绝活儿肯定不行。仓颉(Cangjie)这哥们儿,是华为搞出来的新玩意儿,静态编译的,主打的就是一个现代化、性能炸裂、安全感满满,而且天生就会搞并发。就凭这几点,已经有不少大佬开始关注了。这篇博客呢,就是你的“老司机”指南,带你把仓颉这车开得明明白白。不管你是刚上路的小白,还是开惯了Rust、Go、Java、N
- Linux 中的 .bashrc 是什么?配置详解
vvw&
技术文章Linuxlinuxchrome运维服务器ubuntu后端centos
如果你使用过Linux终端,那么你很可能接触过.bashrc文件。这个功能强大的脚本是个性化命令行环境并使其更高效运行的关键。在本文中,我们将向你介绍这个文件是什么,在哪里可以找到它,以及如何安全地编辑它。你还将学到一些实用技能,如创建省时的命令别名、编写强大的shell函数,以及自定义终端提示的外观。最后,我们还将介绍基本的最佳实践和常见错误,帮助你建立更高效、更强大的命令行工作流程。准备强烈简
- 常见的网络攻击方式及防御措施
神的孩子都在歌唱
计算机网络原理网络运维服务器
常见的网络攻击方式及防御措施:全面解析网络安全威胁前言肝文不易,点个免费的赞和关注,有错误的地方请指出,看个人主页有惊喜。作者:神的孩子都在歌唱在信息化高速发展的今天,网络安全威胁无处不在,不论是个人用户、企业组织,甚至是政府部门,都面临着各种形式的网络攻击。今天,神唱就来带大家一起深入了解常见的网络攻击方式以及如何有效防御这些攻击。一.网络攻击的基本概念1.1什么是网络攻击?网络攻击是指攻击者通
- 微信小程序--顶部轮播图
wendyNo
小程序小程序
效果图市面是手机尺寸有很多,那如何让我们的轮播图根据手机来进行自适应呢?常见的手机尺寸:wxmlWXSS.banneritem{width:100%;}.banneritemimage{width:100%;}JSconstapp=getApp();varpage=1;Page({data:{bannerUrls:[//轮播图的图片{url:'/images/banner1.jpeg',linkU
- PHP Laravel 如何查询字段类型为json的数据-WhereJsonContains、orWhereJsonContains
创建表CREATETABLE`suppliers`(`id`bigintunsignedNOTNULLAUTO_INCREMENT,`supplier_name`varchar(255)CHARACTERSETutf8mb4COLLATEutf8mb4_unicode_ciDEFAULTNULLCOMMENT'供应商名称',`address`jsonDEFAULTNULLCOMMENT'地址:数据
- Kerberos 漏洞
IT 青年
0o漏洞
前言Kerberos漏洞涉及多个关键安全缺陷,主要包括MS14-068提权漏洞、CVE-2024-43639远程代码执行漏洞,以及CVE-2025系列新披露漏洞。一、MS14-068提权漏洞(CVE-2014-6324)漏洞影响受影响系统:WindowsServer2003、2008、2008R2、2012、2012R2。漏洞类型:权限提升漏洞,允许普通域用户提升至域管理员权限。CVSS评分:未公
- 排序的艺术:Spring Data JPA 如何玩转关联实体排序 (. 运算符的奥秘) ✨
小丁学Java
SpringDataJPAjpa
这次我们来深入探讨SpringDataJPA分页排序中一个非常实用但又容易混淆的技巧:如何优雅地对关联实体(或嵌套属性)进行排序。排序的艺术:SpringDataJPA如何玩转关联实体排序(.运算符的奥秘)你好,我是坚持哥!在构建Web应用时,分页查询是家常便饭。SpringDataJPA(JavaPersistenceAPI)提供了强大的Pageable接口,让分页和排序变得异常简单。但当你的排
- FreeRTOS 可重入
✅一、FreeRTOS是“可重入”的吗?FreeRTOS本身是设计为可重入的RTOS内核,但它的可重入性依赖于你使用的API和上下文环境(任务、ISR、中断嵌套等)。我们分情况来看:二、不同上下文下的可重入性分析1.FreeRTOS内核API(任务管理、调度器等)内核是多任务安全的(即线程安全/可重入)。大多数API内部使用了临界区保护(关中断/禁止调度),确保操作的原子性。✅可重入2.FreeR
- linux环境下tomcat安装
M.za
linuxtomcat运维服务器
Tomcat一、什么是Tomcat?1.1、Tomcat介绍Tomcat又叫ApacheTomcat最早是sun公司开发的,1999年捐献给apache基金会,隶属于雅加达项目,现在已经独立成一个顶级项目,因为tomcat技术先进,性能稳定,又是一个开源的web应用服务器,所以很多企业都在使用,很多Java开发者也在使用,开发调试jsp的首选,被更多企业用于Java容器。Tomcat官网:http
- 基于单片机的住宅防火防盗报警系统设计
启初科技
51单片机毕业设计单片机毕业设计单片机嵌入式硬件
文章目录一、系统概述二、项目内容和功能介绍三、效果图四、资料获取一、系统概述基于单片机的住宅防火防盗报警系统设计介绍一、系统设计背景与意义随着城市化进程的加快和居民生活水平的提高,住宅安全已成为人们关注的焦点。火灾和盗窃是威胁住宅安全的两大主要因素,传统的人工巡查和简单的安防设备已难以满足现代住宅的安全需求。基于单片机的住宅防火防盗报警系统集成了传感器技术、单片机控制技术和无线通信技术,能够实时监
- 蓝牙协议栈低功耗之安全管理协议层(SMP)
写代码的无赖的猴子
BLE低功耗蓝牙协议栈网络信息与通信物联网
逻辑链路控制和适配协议层L2CAPSMP层阶段一阶段二Legacyparing安全连接交换公匙鉴权阶段1鉴权阶段2阶段三LElegacypairing:LESecureConnections交叉密匙特性配对PDU类型Hello,我是无赖的猴子,一个蓝牙爱好者,分享蓝牙相关的知识,关注我,学习蓝牙:蓝牙文章链接直达:1.profile层(待更新)2.属性协议层(ATT)(待更新)3.安全管理协议层(
- 在实训云平台上配置云主机
酒城译痴无心剑
Spark基础学习笔记(2)实训云云主机远程连接
文章目录零、学习目标一、实训云升级二、实训云登录(一)登录实训云(二)切换界面语言(三)规划云主机实例三、创建网络三、创建路由器四、连接子网五、创建虚拟网卡六、管理安全组规则七、创建云主机(一)云主机规划(二)创建ied云主机(三)创建其它云主机八、本机利用FinalShell连接虚拟机(一)连接ied云主机(二)连接其它云主机九、配置云主机(一)配置ied云主机1、查看IP地址2、配置主机名3、
- MCP协议采用客户端-服务器架构的深层逻辑与架构对比分析
一、架构选择的核心动因1.功能解耦与安全边界的强制性要求MCP采用客户端-服务器(C/S)架构的核心动因源于AI系统与真实世界交互的特殊性:权限分层控制:主机(Host)作为协调层,严格划分客户端(Client)与服务端(Server)的操作权限。例如医疗场景中,诊断模型(Client)仅能通过医院授权的主机访问脱敏病历服务器,无法直接接触原始数据。沙箱隔离需求:每个MCP服务器运行在独立容器中(
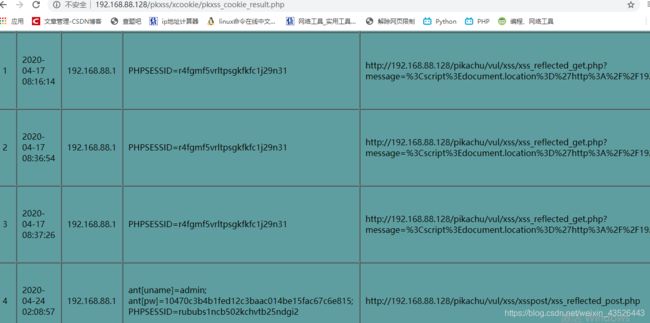
- 从0到1:SQL注入与XSS攻防实战——数据库安全加固全攻略
小张在编程
sqlxss数据库
引言2023年某电商平台用户数据泄露事件中,黑客仅用一行username='OR'1'='1的登录输入,就拖走了百万用户信息;另一家社交网站更离谱,用户在评论区输入alert('xss'),竟让千万级用户的浏览器成了“提线木偶”。这些看似简单的攻击,为何能撕开企业安全防线?今天我们就来拆解SQL注入与XSS的“作案手法”,并给出一套可落地的数据库安全加固方案——毕竟,防住这两类攻击,能解决80%的
- 内网环境部署Deepseek+Dify,构建企业私有化AI应用
我是鲁阿姨
0.简介#公司为生产安全和保密,内部的服务器不可连接外部网络,为了可以在内网环境下部署,采用的方案为ollama(Docker)+Dify(DockerCompose),方便内网环境下迁移和备份,下文将介绍部署的全部过程。1.镜像拉取#镜像拉取为准备工作,因服务器在内网环境,需要先在可以连接外网的电脑上拉取相关镜像或文件。由于公司笔记本的Windows系统屏蔽了MicrosoftStore,导致D
- 从实验到文化 - “混沌日”与持续混沌
weixin_42587823
混沌数据库混沌
从实验到文化-“混沌日”与持续混沌第一部分:锻炼团队的“免疫系统”-混沌日(GameDay)什么是“混沌日”?混沌日是一场有计划、有组织的演习活动。在活动中,团队成员们齐聚一堂(无论是线上还是线下),在一个受控的环境中(理想情况是生产环境,但从预生产环境开始是更安全的选择),主动触发一次模拟的真实故障场景。它就像一次针对技术团队和系统的消防演习。它的价值何在?混沌实验不仅仅测试机器,它同样也测试人
- Web端版本更新提示--前端处理
扶我起来还能学_
前端javascriptvue.js前端框架
Web端版本更新提示–前端处理原理:webpack每次打包jshash值不同import{MessageBox}from'element-ui'letlastScripts=[]//最新一次js文件src名constDURATION=5*60*1000//设置5分钟检查更新一次//提取html中的script标签的src属性asyncfunctionextractNewScripts(htmlSt
- 网络工具Fing Network Tools v12.10.2专业版,WiFi设备扫描神器
米豆学社
网络工具
[软件名称]:网络工具FingNetworkTools[软件大小]:49.2MB[下载通道]:夸克盘|迅雷盘软件介绍《FingNetworkTools》v12.10.2专业版|WiFi安全卫士,一键检测所有联网设备✨核心功能设备扫描–实时发现WiFi网络中的所有连接设备,识别陌生入侵者⚡网络诊断–速度测试+延迟分析,找出Netflix卡顿真凶️安全防护–入侵检测+防火墙功能,守护家庭网络安全高级工
- spring-data-jpa+spring+hibernate+druid配置
参考链接:http://doc.okbase.net/liuyitian/archive/109276.htmlhttp://my.oschina.net/u/1859292/blog/312188最新公司的web项目需要用到spring-data-jpa作为JPA的实现框架,同时使用阿里巴巴的开源数据库连接池druid。关于这两种框架的介绍我在这里就不多赘述。直接进入配置页面:spring的配置
- MCP Streamable HTTP 样例(qbit)
pythonagent
前言模型上下文协议(ModelContextProtocol,MCP),是由Anthropic推出的开源协议,旨在实现大语言模型与外部数据源和工具的集成,用来在大模型和数据源之间建立安全双向的连接。本文代码技术栈Python3.11.8FastMCP2.10.3MCP的传输机制StandardInput/Output(stdio)StreamableHTTPServer-SentEvents(SS
- 2025 轻松部署 ERPNext
linux
在数字化转型浪潮不断推进的2025年,企业对高效、灵活的企业资源计划(ERP)系统需求日益增长。作为一款开源且功能全面的ERP系统,ERPNext以其模块化、易用性和强大的自定义能力,受到越来越多中小企业的青睐。然而,部署ERPNext仍然是许多企业信息化过程中的一大挑战。本文将介绍如何借助云平台实现快速、轻松、安全地部署ERPNext系统。什么是ERPNext?ERPNext是一个开源的ERP系
- 从实践到自动化:现代运维管理的转型与挑战
运维
从实践到自动化:现代运维管理的转型与挑战在信息化快速发展的今天,企业IT系统的稳定性、可用性和安全性已成为衡量公司竞争力的重要因素之一。运维(IT运维)管理作为确保企业IT系统健康、稳定运行的关键职能,一直是企业技术团队关注的重点。然而,随着业务的复杂化、用户需求的变化以及技术的不断创新,传统的运维方式已逐渐无法满足企业对于高效、高可用、高安全的需求。如何提升运维效率、减少人为错误、提高运维系统的
- JavaScript中的系统对话框:alert、confirm、prompt
JavaScript中的系统对话框:alert、confirm、prompt在Web开发的世界里,JavaScript始终扮演着“桥梁”的角色——它连接用户与网页,让静态的页面焕发活力。而在这座桥梁上,系统对话框(SystemDialogs)是最基础却最实用的工具之一。它们像是一位贴心的助手,在用户需要确认、提示或输入时,悄然出现,又在任务完成后无声退场。今天,我们就来聊聊JavaScript中三
- 5种使用USB数据线将文件从安卓设备传输到电脑的方法
Digitally
数据管理android
当你想通过无线方式将安卓设备中的数据复制到电脑时,是否遇到过困难?不用担心,只要按照正确的步骤操作,这个过程其实非常简单。本指南将为你提供使用USB数据线将文件从安卓设备传输到电脑的必要步骤。我们将介绍如何连接设备、查找文件并确保安全传输。有了这些指导,你会发现这是一个任何人都可以轻松掌握的简单操作。#1:通过文件资源管理器使用USB数据线将文件从安卓设备传输到电脑文件资源管理器是使用USB数据线
- 深入剖析开源AI阅读器项目Saga Reader基于大模型的文本转换与富文本渲染优化方案
魑魅丶小鬼
人工智能
引言AI阅读器作为一种新型的内容消费工具,正在改变人们获取和处理信息的方式。本文将介绍SagaReader项目中如何利用大型语言模型(LLM)进行网页内容抓取、智能优化和富文本渲染,特别是如何通过精心设计的提示词(prompt)引导LLM生成样式丰富的HTML内容,提升用户阅读体验。关于SagaReader基于Tauri开发的著名开源AI驱动的智库式阅读器(前端部分使用Web框架),能根据用户指定
- 如何学习智能体搭建
如何学习智能体搭建前言随着人工智能的发展,智能体(Agent)成为自动化、交互式应用和自主决策系统中的核心角色。本书将从零基础出发,系统讲解智能体的基本原理、常见框架、实战搭建与进阶技巧,帮助你快速上手并应用于实际项目。目录智能体基础认知智能体的核心组成主流智能体开发框架本地智能体与云端智能体选型智能体的任务自动化与插件集成智能体的知识检索与上下文管理智能体的多模态扩展智能体安全与可控性智能体实战
- 全栈运维的“诅咒”与“荣光”:为什么“万金油”工程师是项目成功的隐藏MVP?
云原生水神
职业发展系统运维运维
大家好,今天,我们来聊一个特殊且至关重要的群体:运维工程师。特别是那些在项目制中,以一己之力扛起一个或多个产品生死的“全能战士”。你是否就是其中一员?你的技能树上点亮了:操作系统、网络协议、mysql与Redis中间件、Docker与K8s容器化、Ansible与Terraform自动化、Go/Python工具开发、Prometheus监控体系、opentelemetry可视化,甚至要负责信息安全
- Nginx中如何配置WebSocket代理?
m0_74824025
面试学习路线阿里巴巴nginxwebsocket运维
Nginx可以配置为WebSocket代理,将WebSocket连接从客户端转发到后端服务器。以下是如何在Nginx中配置WebSocket代理的详细步骤和示例配置。1.安装Nginx确保你已经安装了Nginx。如果没有安装,可以使用以下命令进行安装:sudoapt-getupdatesudoapt-getinstallnginx2.配置WebSocket代理编辑Nginx配置文件,通常位于/et
- PHP如何实现二维数组排序?
IT独行者
二维数组PHP排序
二维数组在PHP开发中经常遇到,但是他的排序就不如一维数组那样用内置函数来的方便了,(一维数组排序可以参考本站另一篇文章【PHP中数组排序函数详解汇总】)。二维数组的排序需要我们自己写函数处理了,这里UncleToo给大家分享一个PHP二维数组排序的函数:
代码:
functionarray_sort($arr,$keys,$type='asc'){
$keysvalue= $new_arr
- 【Hadoop十七】HDFS HA配置
bit1129
hadoop
基于Zookeeper的HDFS HA配置主要涉及两个文件,core-site和hdfs-site.xml。
测试环境有三台
hadoop.master
hadoop.slave1
hadoop.slave2
hadoop.master包含的组件NameNode, JournalNode, Zookeeper,DFSZKFailoverController
- 由wsdl生成的java vo类不适合做普通java vo
darrenzhu
VOwsdlwebservicerpc
开发java webservice项目时,如果我们通过SOAP协议来输入输出,我们会利用工具从wsdl文件生成webservice的client端类,但是这里面生成的java data model类却不适合做为项目中的普通java vo类来使用,当然有一中情况例外,如果这个自动生成的类里面的properties都是基本数据类型,就没问题,但是如果有集合类,就不行。原因如下:
1)使用了集合如Li
- JAVA海量数据处理之二(BitMap)
周凡杨
java算法bitmapbitset数据
路漫漫其修远兮,吾将上下而求索。想要更快,就要深入挖掘 JAVA 基础的数据结构,从来分析出所编写的 JAVA 代码为什么把内存耗尽,思考有什么办法可以节省内存呢? 啊哈!算法。这里采用了 BitMap 思想。
首先来看一个实验:
指定 VM 参数大小: -Xms256m -Xmx540m
- java类型与数据库类型
g21121
java
很多时候我们用hibernate的时候往往并不是十分关心数据库类型和java类型的对应关心,因为大多数hbm文件是自动生成的,但有些时候诸如:数据库设计、没有生成工具、使用原始JDBC、使用mybatis(ibatIS)等等情况,就会手动的去对应数据库与java的数据类型关心,当然比较简单的数据类型即使配置错了也会很快发现问题,但有些数据类型却并不是十分常见,这就给程序员带来了很多麻烦。
&nb
- Linux命令
510888780
linux命令
系统信息
arch 显示机器的处理器架构(1)
uname -m 显示机器的处理器架构(2)
uname -r 显示正在使用的内核版本
dmidecode -q 显示硬件系统部件 - (SMBIOS / DMI)
hdparm -i /dev/hda 罗列一个磁盘的架构特性
hdparm -tT /dev/sda 在磁盘上执行测试性读取操作
cat /proc/cpuinfo 显示C
- java常用JVM参数
墙头上一根草
javajvm参数
-Xms:初始堆大小,默认为物理内存的1/64(<1GB);默认(MinHeapFreeRatio参数可以调整)空余堆内存小于40%时,JVM就会增大堆直到-Xmx的最大限制
-Xmx:最大堆大小,默认(MaxHeapFreeRatio参数可以调整)空余堆内存大于70%时,JVM会减少堆直到 -Xms的最小限制
-Xmn:新生代的内存空间大小,注意:此处的大小是(eden+ 2
- 我的spring学习笔记9-Spring使用工厂方法实例化Bean的注意点
aijuans
Spring 3
方法一:
<bean id="musicBox" class="onlyfun.caterpillar.factory.MusicBoxFactory"
factory-method="createMusicBoxStatic"></bean>
方法二:
- mysql查询性能优化之二
annan211
UNIONmysql查询优化索引优化
1 union的限制
有时mysql无法将限制条件从外层下推到内层,这使得原本能够限制部分返回结果的条件无法应用到内层
查询的优化上。
如果希望union的各个子句能够根据limit只取部分结果集,或者希望能够先排好序在
合并结果集的话,就需要在union的各个子句中分别使用这些子句。
例如 想将两个子查询结果联合起来,然后再取前20条记录,那么mys
- 数据的备份与恢复
百合不是茶
oraclesql数据恢复数据备份
数据的备份与恢复的方式有: 表,方案 ,数据库;
数据的备份:
导出到的常见命令;
参数 说明
USERID 确定执行导出实用程序的用户名和口令
BUFFER 确定导出数据时所使用的缓冲区大小,其大小用字节表示
FILE 指定导出的二进制文
- 线程组
bijian1013
java多线程threadjava多线程线程组
有些程序包含了相当数量的线程。这时,如果按照线程的功能将他们分成不同的类别将很有用。
线程组可以用来同时对一组线程进行操作。
创建线程组:ThreadGroup g = new ThreadGroup(groupName);
&nbs
- top命令找到占用CPU最高的java线程
bijian1013
javalinuxtop
上次分析系统中占用CPU高的问题,得到一些使用Java自身调试工具的经验,与大家分享。 (1)使用top命令找出占用cpu最高的JAVA进程PID:28174 (2)如下命令找出占用cpu最高的线程
top -Hp 28174 -d 1 -n 1
32694 root 20 0 3249m 2.0g 11m S 2 6.4 3:31.12 java
- 【持久化框架MyBatis3四】MyBatis3一对一关联查询
bit1129
Mybatis3
当两个实体具有1对1的对应关系时,可以使用One-To-One的进行映射关联查询
One-To-One示例数据
以学生表Student和地址信息表为例,每个学生都有都有1个唯一的地址(现实中,这种对应关系是不合适的,因为人和地址是多对一的关系),这里只是演示目的
学生表
CREATE TABLE STUDENTS
(
- C/C++图片或文件的读写
bitcarter
写图片
先看代码:
/*strTmpResult是文件或图片字符串
* filePath文件需要写入的地址或路径
*/
int writeFile(std::string &strTmpResult,std::string &filePath)
{
int i,len = strTmpResult.length();
unsigned cha
- nginx自定义指定加载配置
ronin47
进入 /usr/local/nginx/conf/include 目录,创建 nginx.node.conf 文件,在里面输入如下代码:
upstream nodejs {
server 127.0.0.1:3000;
#server 127.0.0.1:3001;
keepalive 64;
}
server {
liste
- java-71-数值的整数次方.实现函数double Power(double base, int exponent),求base的exponent次方
bylijinnan
double
public class Power {
/**
*Q71-数值的整数次方
*实现函数double Power(double base, int exponent),求base的exponent次方。不需要考虑溢出。
*/
private static boolean InvalidInput=false;
public static void main(
- Android四大组件的理解
Cb123456
android四大组件的理解
分享一下,今天在Android开发文档-开发者指南中看到的:
App components are the essential building blocks of an Android
- [宇宙与计算]涡旋场计算与拓扑分析
comsci
计算
怎么阐述我这个理论呢? 。。。。。。。。。
首先: 宇宙是一个非线性的拓扑结构与涡旋轨道时空的统一体。。。。
我们要在宇宙中寻找到一个适合人类居住的行星,时间非常重要,早一个刻度和晚一个刻度,这颗行星的
- 同一个Tomcat不同Web应用之间共享会话Session
cwqcwqmax9
session
实现两个WEB之间通过session 共享数据
查看tomcat 关于 HTTP Connector 中有个emptySessionPath 其解释如下:
If set to true, all paths for session cookies will be set to /. This can be useful for portlet specification impleme
- springmvc Spring3 MVC,ajax,乱码
dashuaifu
springjquerymvcAjax
springmvc Spring3 MVC @ResponseBody返回,jquery ajax调用中文乱码问题解决
Spring3.0 MVC @ResponseBody 的作用是把返回值直接写到HTTP response body里。具体实现AnnotationMethodHandlerAdapter类handleResponseBody方法,具体实
- 搭建WAMP环境
dcj3sjt126com
wamp
这里先解释一下WAMP是什么意思。W:windows,A:Apache,M:MYSQL,P:PHP。也就是说本文说明的是在windows系统下搭建以apache做服务器、MYSQL为数据库的PHP开发环境。
工欲善其事,必须先利其器。因为笔者的系统是WinXP,所以下文指的系统均为此系统。笔者所使用的Apache版本为apache_2.2.11-
- yii2 使用raw http request
dcj3sjt126com
http
Parses a raw HTTP request using yii\helpers\Json::decode()
To enable parsing for JSON requests you can configure yii\web\Request::$parsers using this class:
'request' =&g
- Quartz-1.8.6 理论部分
eksliang
quartz
转载请出自出处:http://eksliang.iteye.com/blog/2207691 一.概述
基于Quartz-1.8.6进行学习,因为Quartz2.0以后的API发生的非常大的变化,统一采用了build模式进行构建;
什么是quartz?
答:简单的说他是一个开源的java作业调度框架,为在 Java 应用程序中进行作业调度提供了简单却强大的机制。并且还能和Sp
- 什么是POJO?
gupeng_ie
javaPOJO框架Hibernate
POJO--Plain Old Java Objects(简单的java对象)
POJO是一个简单的、正规Java对象,它不包含业务逻辑处理或持久化逻辑等,也不是JavaBean、EntityBean等,不具有任何特殊角色和不继承或不实现任何其它Java框架的类或接口。
POJO对象有时也被称为Data对象,大量应用于表现现实中的对象。如果项目中使用了Hiber
- jQuery网站顶部定时折叠广告
ini
JavaScripthtmljqueryWebcss
效果体验:http://hovertree.com/texiao/jquery/4.htmHTML文件代码:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>网页顶部定时收起广告jQuery特效 - HoverTree<
- Spring boot内嵌的tomcat启动失败
kane_xie
spring boot
根据这篇guide创建了一个简单的spring boot应用,能运行且成功的访问。但移植到现有项目(基于hbase)中的时候,却报出以下错误:
SEVERE: A child container failed during start
java.util.concurrent.ExecutionException: org.apache.catalina.Lif
- leetcode: sort list
michelle_0916
Algorithmlinked listsort
Sort a linked list in O(n log n) time using constant space complexity.
====analysis=======
mergeSort for singly-linked list
====code======= /**
* Definition for sin
- nginx的安装与配置,中途遇到问题的解决
qifeifei
nginx
我使用的是ubuntu13.04系统,在安装nginx的时候遇到如下几个问题,然后找思路解决的,nginx 的下载与安装
wget http://nginx.org/download/nginx-1.0.11.tar.gz
tar zxvf nginx-1.0.11.tar.gz
./configure
make
make install
安装的时候出现
- 用枚举来处理java自定义异常
tcrct
javaenumexception
在系统开发过程中,总少不免要自己处理一些异常信息,然后将异常信息变成友好的提示返回到客户端的这样一个过程,之前都是new一个自定义的异常,当然这个所谓的自定义异常也是继承RuntimeException的,但这样往往会造成异常信息说明不一致的情况,所以就想到了用枚举来解决的办法。
1,先创建一个接口,里面有两个方法,一个是getCode, 一个是getMessage
public
- erlang supervisor分析
wudixiaotie
erlang
当我们给supervisor指定需要创建的子进程的时候,会指定M,F,A,如果是simple_one_for_one的策略的话,启动子进程的方式是supervisor:start_child(SupName, OtherArgs),这种方式可以根据调用者的需求传不同的参数给需要启动的子进程的方法。和最初的参数合并成一个数组,A ++ OtherArgs。那么这个时候就有个问题了,既然参数不一致,那