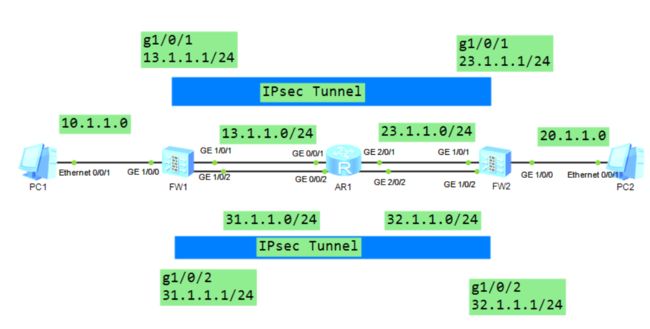
【eNSP】链路冗余技术课后配置
链路冗余2:1
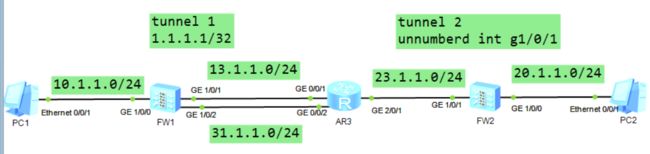
[FW1]interface Tunnel 1
[FW1-Tunnel1]tunnel-protocol ipsec
[FW1-Tunnel1]ip address 1.1.1.1 32
加此口加入到安全区域
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
add interface Tunnel1
[FW2]interface Tunnel 1
[FW2-Tunnel2]tunnel-protocol ipsec
[FW2-Tunnel2]ip address unnumbered interface GigabitEthernet 1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Tunnel2
路由
FW1
[FW1]rip 1
[FW1-rip-1]version 2
[FW1-rip-1]undo summary
[FW1-rip-1]network 13.0.0.0
[FW1-rip-1]network 31.0.0.0
[FW1-rip-1]network 1.0.0.0
AR3
[AR3]rip 1
[AR3-rip-1]version 2
[AR3-rip-1]undo summary
[AR3-rip-1]network 13.0.0.0
[AR3-rip-1]network 31.0.0.0
[AR3-rip-1]network 23.0.0.0
FW2
[FW2]RIP 1
[FW2-rip-1]version 2
[FW2-rip-1]undo summary
[FW2-rip-1]network 23.0.0.0
查询
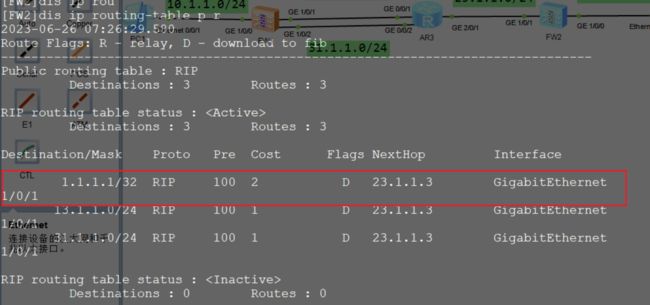
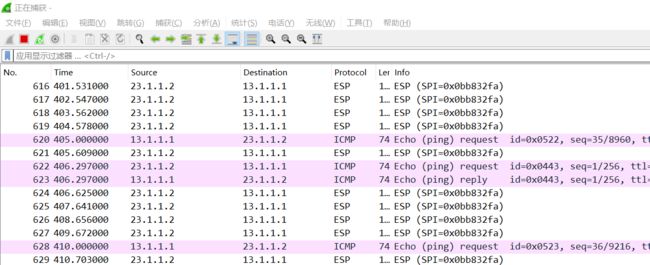
FW2没有学习到tunnel 那个口,是因为它还没有两个Up

FW1(负载均衡)

通过rip的操控,使其不是负载均衡
[AR3]interface GigabitEthernet 0/0/2
[AR3-GigabitEthernet0/0/2]rip metricout 2
[AR3-GigabitEthernet0/0/2]dis this
interface GigabitEthernet0/0/2
ip address 31.1.1.3 255.255.255.0
rip metricout 2 #将度量值改大,就会自动给学习小的
ipsec
FW1
[FW1]ip route-static 20.1.1.0 24 Tunnel 1
[FW1]acl 3000
[FW1-acl-adv-3000]rule 05 permit ip source 10.1.1.0 0.0.0.255 destination 20.1.1.0 0.0.0.255
[FW1]ike peer S01_TO_S02
[FW1-ike-peer-S01_TO_S02]pre-shared-key Huawei@123
[FW1-ike-peer-S01_TO_S02]ike-proposal 10
[FW1]ipsec policy-template S01_TEMP 1
[FW1-ipsec-policy-templet-S01_TEMP-1]security acl 3000
[FW1-ipsec-policy-templet-S01_TEMP-1]proposal 10
[FW1-ipsec-policy-templet-S01_TEMP-1]ike-peer S01_TO_S02
[FW1]ipsec policy S01 1 isakmp template S01_TEMP
[FW1]interface Tunnel 1
[FW1-Tunnel1]ipsec policy S01
[FW1]security-policy
[FW1-policy-security]default action permit
[FW2]ip route-static 10.1.1.0 24 Tunnel 2
[FW2]acl 3000
[FW2-acl-adv-3000]rule 05 permit ip source 20.1.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[FW2]ike proposal 10
[FW2]ike peer S02_TO_S01
[FW2-ike-peer-S02_TO_S01]pre-shared-key Huawei@123
[FW2-ike-peer-S02_TO_S01]ike-proposal 10
[FW2-ike-peer-S02_TO_S01]remote-address 1.1.1.1
[FW2]ipsec policy S02 1 isakmp
[FW2-ipsec-policy-isakmp-S02-1]proposal 10
[FW2-ipsec-policy-isakmp-S02-1]ike-peer S02_TO_S01
[FW2-ipsec-policy-isakmp-S02-1]security acl 3000
[FW2]interface Tunnel 2
[FW2-Tunnel2]IPSE
[FW2-Tunnel2]ipsec policy S02
[FW2]security-policy
[FW2-policy-security]default action permit
链路冗余2:2
interface GigabitEthernet1/0/0
ip address 10.1.1.1 255.255.255.0
interface GigabitEthernet1/0/1
ip address 13.1.1.1 255.255.255.0
interface GigabitEthernet1/0/2
ip address 31.1.1.1 255.255.255.0
firewall zone trust
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
AR1
interface GigabitEthernet0/0/1
ip address 13.1.1.3 255.255.255.0
interface GigabitEthernet0/0/2
ip address 31.1.1.3 255.255.255.0
interface GigabitEthernet2/0/1
ip address 23.1.1.3 255.255.255.0
interface GigabitEthernet2/0/2
ip address 32.1.1.3 255.255.255.0
FW2
interface GigabitEthernet1/0/0
ip address 20.1.1.1 255.255.255.0
interface GigabitEthernet1/0/1
ip address 23.1.1.1 255.255.255.0
interface GigabitEthernet1/0/2
ip address 32.1.1.1 255.255.255.0
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
[FW1]rip 1
[FW1-rip-1]version 2
[FW1-rip-1]un summary
[FW1-rip-1]network 13.0.0.0
[FW1]rip 2
[FW1-rip-2]version 2
[FW1-rip-2]un summary
[FW1-rip-2]network 31.0.0.0
AR1
[AR1]rip 1
[AR1-rip-1]version 2
[AR1-rip-1]un summary
[AR1-rip-1]network 13.0.0.0
[AR1-rip-1]network 23.0.0.0
[AR1]rip 2
[AR1-rip-2]version 2
[AR1-rip-2]un summary
[AR1-rip-2]network 31.0.0.0
[AR1-rip-2]network 32.0.0.0
FW2
[FW2]rip 1
[FW2-rip-1]version 2
[FW2-rip-1]un summary
[FW2-rip-1]network 23.0.0.0
[FW2]rip 2
[FW2-rip-2]version 2
[FW2-rip-2]un summary
[FW2-rip-2]network 32.0.0.0
ip-link
FW1
[FW1]ip-link check enable
[FW1]ip-link name MASTER
[FW1-iplink-MASTER]destination 23.1.1.2 interface GigabitEthernet 1/0/1 mode icm
p next-hop 13.1.1.3
#提示信息为down ,需要在对端FW2开启PING
[FW1-iplink-MASTER]
Jun 20 2023 11:23:45 FW1 %%01HEALTHCHECK/4/DOWN(l)[1]:Detect changed status to d
own (Protocol=icmp,DestinationIp=23.1.1.2,DestinationPort=0).
Jun 20 2023 11:23:45 FW1 %%01HEALTHCHECK/3/DOWN(l)[2]:IP-Link MASTER changed sta
tus to down (Protocol=icmp,DestinationIp=23.1.1.2,DestinationPort=0).
Jun 20 2023 11:23:45 FW1 HEALTHCHECK/2/DOWN:OID 1.3.6.1.4.1.2011.6.122.45.2.2 IP
-link MASTER changes status to down.
#开启ping功能才能up
[FW2]interface g1/0/1
[FW2-GigabitEthernet1/0/1]service-manage ping permit
[FW1-iplink-MASTER]dis ip-link
2023-06-20 11:24:54.740
Current Total Ip-link Number : 1
Name Member State Up/Down/Init
MASTER 1 down 0 1 0
[FW1]
Jun 20 2023 11:45:14 FW1 HEALTHCHECK/6/UP:OID 1.3.6.1.4.1.2011.6.122.45.2.1 IP-l
ink MASTER changes status to up.
[FW1]dis ip-link
2023-06-20 11:45:48.760
Current Total Ip-link Number : 1
Name Member State Up/Down/Init
MASTER 1 up 1 0 0
FW2
[FW2]ip-link check enable
[FW2]ip-link name MASTER
[FW2-iplink-MASTER]destination 13.1.1.1 interface GigabitEthernet 1/0/1 mode icm
p next-hop 23.1.1.3
Jun 20 2023 11:50:47 FW2 %%01HEALTHCHECK/4/DOWN(l)[4]:Detect changed status to d
own (Protocol=icmp,DestinationIp=13.1.1.1,DestinationPort=0).
Jun 20 2023 11:50:47 FW2 %%01HEALTHCHECK/3/DOWN(l)[5]:IP-Link MASTER changed sta
tus to down (Protocol=icmp,DestinationIp=13.1.1.1,DestinationPort=0).
Jun 20 2023 11:50:47 FW2 HEALTHCHECK/2/DOWN:OID 1.3.6.1.4.1.2011.6.122.45.2.2 IP
-link MASTER changes status to down.
[FW2-iplink-MASTER]q
[FW2]dis ip-l
[FW2]dis ip-link
2023-06-20 11:54:41.540
Current Total Ip-link Number : 1
Name Member State Up/Down/Init
MASTER 1 down 0 1 0
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]service-manage ping permit
[FW2]
Jun 20 2023 11:56:21 FW2 HEALTHCHECK/6/UP:OID 1.3.6.1.4.1.2011.6.122.45.2.1 IP-l
ink MASTER changes status to up.
[FW2]dis ip-link
2023-06-20 11:56:30.940
Current Total Ip-link Number : 1
Name Member State Up/Down/Init
MASTER 1 up 1 0 0
静态路由
FW1
#(主的路由)
[FW1]ip route-static 20.1.1.0 24 GigabitEthernet 1/0/1 13.1.1.3 preference 10 track ip-link MASTER
#静态路由的存在主要依据GigabitEthernet 1/0/1和 ip-link MASTER(直接去对端防火墙接口关闭ping功能),倘若两者都down,路由表中就不会存在静态路由
#(备的路由)
[FW1]ip route-static 20.1.1.0 24 GigabitEthernet 1/0/2 31.1.1.3 preference 20
[FW1]dis ip routing-table protocol static
2023-06-20 12:07:37.720
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : Static
Destinations : 1 Routes : 2 Configured Routes : 2
Static routing table status : <Active>
Destinations : 1 Routes : 1
Destination/Mask Proto Pre Cost Flags NextHop Interface
20.1.1.0/24 Static 10 0 D 13.1.1.3 GigabitEthernet
1/0/1
Static routing table status : <Inactive>
Destinations : 1 Routes : 1
Destination/Mask Proto Pre Cost Flags NextHop Interface
20.1.1.0/24 Static 20 0 31.1.1.3 GigabitEthernet
1/0/2
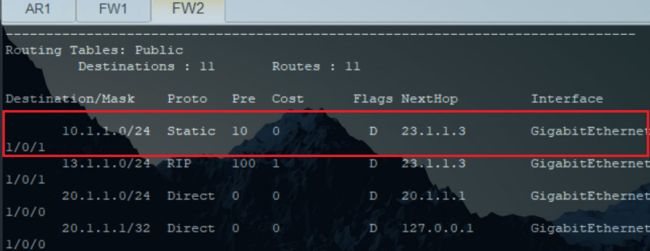
FW2
[FW2]ip route-static 10.1.1.0 24 GigabitEthernet 1/0/1 23.1.1.3 preference 10 track ip-link MASTER
[FW2]IP route-static 20.1.1.0 24 GigabitEthernet 1/0/2 32.1.1.3 preference 20
[FW2]dis ip routing-table protocol static
2023-06-20 12:12:52.880
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : Static
Destinations : 2 Routes : 2 Configured Routes : 2
Static routing table status : <Active>
Destinations : 1 Routes : 1
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.1.1.0/24 Static 10 0 D 23.1.1.3 GigabitEthernet
1/0/1
Static routing table status : <Inactive>
Destinations : 1 Routes : 1
Destination/Mask Proto Pre Cost Flags NextHop Interface
20.1.1.0/24 Static 20 0 32.1.1.3 GigabitEthernet
1/0/2
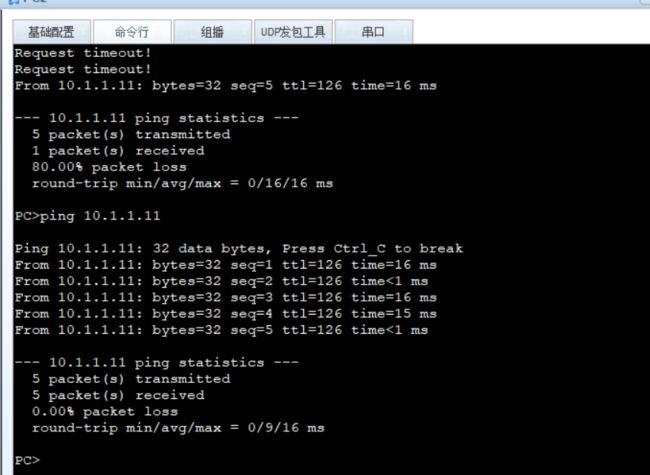
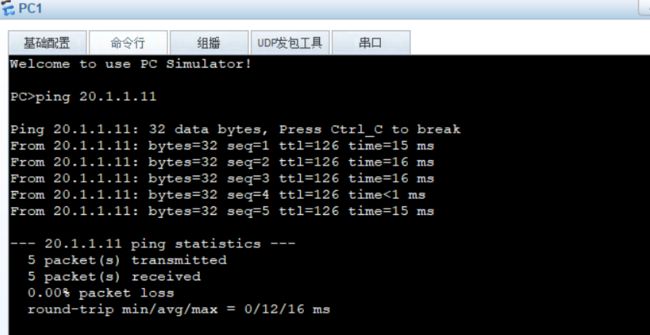
建立ipsec
FW1
[FW1]acl 3000
[FW1-acl-adv-3000]rule 05 permit ip source 10.1.1.0 0.0.0.255 destination 20.1.1
[FW1]ike peer MASTER
[FW1-ike-peer-MASTER]undo version 2
[FW1-ike-peer-MASTER]pre-shared-key Huawei@123
[FW1-ike-peer-MASTER]ike-proposal 10
[FW1-ike-peer-MASTER]remote-address 23.1.1.2
[FW1]ike peer BACKUP
[FW1-ike-peer-BACKUP]UNDO VERS
[FW1-ike-peer-BACKUP]UNDO version 2
[FW1-ike-peer-BACKUP]pre-shared-key Huawei@123
[FW1-ike-peer-BACKUP]ike-proposal 10
[FW1-ike-peer-BACKUP]remote-address 32.1.1.2
[FW1]ipsec proposal10
[FW1]ipsec policy S01_MASTER 1 isakmp
[FW1-ipsec-policy-isakmp-S01_MASTER-1]security acl 3000
[FW1-ipsec-policy-isakmp-S01_MASTER-1]proposal 10
[FW1-ipsec-policy-isakmp-S01_MASTER-1]ike-peer MASTER
[FW1]ipsec policy S01_BACKUP 1 isakmp
[FW1-ipsec-policy-isakmp-S01_BACKUP-1]security acl 3000
[FW1-ipsec-policy-isakmp-S01_BACKUP-1]proposal 10
[FW1-ipsec-policy-isakmp-S01_BACKUP-1]ike-peer BACKUP
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]ipsec policy S01_MASTER
[FW1]interface GigabitEthernet 1/0/2
[FW1-GigabitEthernet1/0/2]ipsec policy S01_BACKUP
FW2
[FW2]acl 3000
[FW2-acl-adv-3000]rule 05 permit ip source 20.1.1.0 0.0.0.255 destination 10.1.1
.0 0.0.0.255
[FW2]ike proposal 10
[FW2-ike-peer-MASTER]UNDO version 2
[FW2-ike-peer-MASTER]pre-shared-key Huawei@123
[FW2-ike-peer-MASTER]ike-proposal 10
[FW2-ike-peer-MASTER]remote-address 13.1.1.1
[FW2]ike peer BACKUP
[FW2-ike-peer-BACKUP]UNDO version 2
[FW2-ike-peer-BACKUP]pre-shared-key Huawei@123
[FW2-ike-peer-BACKUP]ike-proposal 10
[FW2-ike-peer-BACKUP]remote-address 31.1.1.1
[FW2]ipsec proposal 10
[FW2]ipsec policy S02_MASTER 1 isakmp
[FW2-ipsec-policy-isakmp-S02_MASTER-1]security acl 3000
[FW2-ipsec-policy-isakmp-S02_MASTER-1]proposal 10
[FW2-ipsec-policy-isakmp-S02_MASTER-1]ike-peer MASTER
[FW2]ipsec policy S02_BACKUP 1 isakmp
[FW2-ipsec-policy-isakmp-S02_BACKUP-1]security acl 3000
[FW2-ipsec-policy-isakmp-S02_BACKUP-1]proposal 10
[FW2-ipsec-policy-isakmp-S02_BACKUP-1]ike-peer BACKUP
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]ipsec policy S02_MASTER
[FW2]interface GigabitEthernet 1/0/2
[FW2-GigabitEthernet1/0/2]ipsec policy S02_BACKUP
安全策略(FW1和FW2)
[FW1]security-policy
[FW1-policy-security]default action permit
[FW2]security-policy
[FW2-policy-security]default action permit